$PDF$/READ Soyuz: A Universal Spacecraft (Springer Praxis Books)
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/1852336579\n\nPDF\/READ Soyuz: A Universal Spacecraft (Springer Praxis Books) | Soyuz: A Universal Spacecraft (Springer Praxis Books)\n\"\n
1 views • 6 slides
Understanding Quantified Statements
Explore the logic of quantified statements, including universal instantiation, universal modus ponens, and examples illustrating the application of these concepts using variables, predicates, and symbols. Dive into the reasoning behind statements involving particular instances within a domain, and s
6 views • 22 slides
Universal Insurance
Universal Life Insurance has the dual advantage of life insurance as well as savings. Learn more about universal life insurance, including its types and benefits.
1 views • 7 slides
Understanding Universal Banking: Evolution, Definition, and Advantages
Universal banking combines commercial and investment banking services under one roof. This approach offers diverse financial services, promoting economies of scale and profitable diversification. The evolution of universal banking in India has been influenced by regulatory changes and the growing de
2 views • 26 slides
Critique of Universal and Differentiated Citizenship
Universal citizenship embodies equality of rights for all citizens, while differentiated citizenship focuses on special representation rights for oppressed groups. Iris Marion Young criticizes the universalism in citizenship, advocating for differentiated citizenship to address the needs of marginal
2 views • 10 slides
Secure Keyed Hashing on Programmable Switches
Explore the implementation challenges and opportunities for improved security, privacy, performance, and reliability in data plane applications using (Half)SipHash and CRC32 hashing techniques. Discover the vulnerabilities associated with CRC32 and the need for secure hashing solutions like SipID. L
0 views • 17 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Understanding Ethics, Values, and Universal Morality
Explore the concepts of ethics, universal values, and morality in a multicultural context through Education for Justice (E4J) Integrity and Ethics Module 2. Delve into topics such as the Universal Declaration on Human Rights, enacting universal values, moral relativism, and more. Gain insights on th
6 views • 14 slides
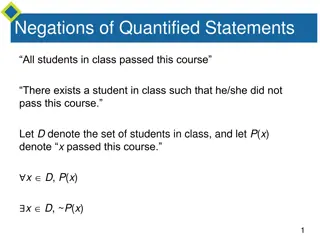
Understanding Negations in Quantified and Conditional Statements
Explore the concept of negations in quantified statements, where the negation of a universal statement equates to an existential statement, and vice versa. Discover the importance of negations in universal conditional statements and their relationship to logical equivalence. Dive into examples of ne
0 views • 15 slides
Understanding Scrypt: Maximally Memory-Hard Functions
Scrypt is a memory-hard function designed for password hashing and key derivation, aiming to thwart brute-force attacks by making evaluation moderately hard. It emphasizes the need for memory intensity over computation, hindering the advantages of special-purpose hardware, parallelism, and amortizat
0 views • 59 slides
Entity Resolution Problem in Customer Data Matching
The challenge of entity resolution, especially in the context of matching customer data between companies, is addressed in this content. The scenario involves accurately identifying which records correspond to the same individuals despite potential variations or errors in the data. Strategies such a
1 views • 56 slides
Braden River High School - Grad Bash 2019: Exclusive Universal Studios Experience
Join Braden River High School's Grad Bash on April 12th, 2019 for a thrilling experience at Universal Studios featuring private access to Islands of Adventure and Universal Studios Florida. Enjoy 26 attractions, live entertainment, and exclusive souvenir cups. Dress comfortably, meet seniors from ac
2 views • 6 slides
Comprehensive Overview of Binary Heaps, Heapsort, and Hashing
In this detailed review, you will gain a thorough understanding of binary heaps, including insertion and removal operations, heap utility functions, heapsort, and the efficient Horner's Rule for polynomial evaluation. The content also covers the representation of binary heaps, building initial heaps
0 views • 24 slides
CSE 373 - Hashing Concepts and Exam Preparation
Introduction to hashing in CSE 373, covering basic concepts, hash functions, collision resolution, and runtimes. Exam details for Friday's practice exam include topics on Stacks, Queues, BigO Notation, Heaps, Trees, Design Tradeoffs, and exam format with emphasis on theoretical understanding. Lectur
0 views • 38 slides
Understanding Locality Sensitive Hashing (LSH) for Nearest Neighbor Queries
Locality Sensitive Hashing (LSH) is a technique used to efficiently find nearest neighbors in high-dimensional spaces. By grouping similar points into the same hash bucket, LSH enables fast search for nearest neighbors, overcoming the curse of dimensionality. Variants include k-nearest neighbors and
0 views • 41 slides
Scaling Services and Key-Value Storage Techniques
This content delves into various aspects of scaling services, including partitioning, hashing, and key-value storage. It discusses vertical and horizontal scalability, the chaotic nature of horizontal scaling, techniques for partitioning data, and case studies like Amazon Dynamo. The importance of p
0 views • 48 slides
Exploring Universal Design in National Service and Disability Community
The presentation delves into Universal Design (UD) and its application in National Service and the disability community. It discusses ways to enhance program design beyond physical aspects, focusing on Universal Design for Learning and architecture. The content showcases how individuals use UD to cr
0 views • 55 slides
Move to Universal Credit Update Statistics 18/06/2024
The latest statistics on the Move to Universal Credit initiative show significant progress in the migration process. Over 824,000 individuals in 540,000 households have been sent migration notices, with many successfully transitioning to Universal Credit. The update also provides insights into condi
0 views • 10 slides
Overview of Ferndale, CA Solid Waste Regulations & Universal Collection Service
This content provides an overview of the solid waste regulations and universal collection service discussion in Ferndale, CA. It covers topics such as the need for universal collection, a solid waste franchise agreement, proposed service changes, regulatory drivers, and jurisdiction responsibilities
0 views • 14 slides
Understanding Consistent Hashing and Distributed Hash Table
Explore the concept of consistent hashing and distributed hash tables to efficiently store and retrieve web pages across multiple servers. Learn how hashing functions and algorithms can distribute data evenly, handle server additions smoothly, and minimize object relocations. Discover the benefits o
1 views • 36 slides
The Intriguing World of Language Evolution
In discussions encompassing universal grammar, pidgins, and creole languages, the fascinating exploration of language evolution unfolds. Chomsky's concept of universal grammar proposes inherent linguistic principles, sparking debate among scholars. Pidgins, emerging as makeshift jargons, highlight l
0 views • 18 slides
Overlay Networks and Consistent Hashing in Distributed Systems
Understanding the concept of overlay networks and consistent hashing in distributed systems is crucial for scalability and efficient data storage. Overlay networks like P2P DHT via KBR offer a decentralized approach for managing data while consistent hashing provides a balanced and deterministic way
0 views • 36 slides
Adapting Linear Hashing for Flash Memory Constrained Embedded Devices
This research explores the adaptation of linear hashing for improved data handling on flash memory-constrained embedded devices. Motivated by the increasing data collection by IoT devices, the study focuses on implementing database structures like a linear hash table for efficient data processing. T
0 views • 67 slides
Understanding Hash Functions in Data Structures
Hash functions are crucial in storing data efficiently by converting a sized amount of data into a single integer. They are used to generate hash values, hash codes, or hash sums, which serve as indexes in arrays. The hash function should be quick to compute and distribute hash addresses uniformly t
0 views • 200 slides
Enhancing MemC3: Compact and Concurrent MemCache for Improved Performance
MemC3 introduces a novel approach to compact and concurrent caching through dumber caching and smarter hashing techniques, addressing key issues faced by traditional memory caching systems. By implementing CLOCK-based LRU, approximate LRU, and utilizing Cuckoo Hashing, MemC3 achieves significant imp
0 views • 20 slides
Enhancing Key-Value Storage with MemC3 and Cuckoo Hashing
MemC3 is a specialized key-value store that combines CLOCK and Concurrent Cuckoo Hashing to improve performance and efficiency. Memcached, an established DRAM-based key-value store, is also discussed along with its LRU eviction strategy. The use of internal chaining hashtable and LRU caching in Memc
1 views • 23 slides
Universal Design and Accessibility Principles Overview
Learn about the importance of universal design and accessibility principles in creating technology that is usable by everyone, regardless of abilities. Discover the key principles such as equitable use, flexibility in use, simplicity, perceptibility, error tolerance, low physical effort, and appropr
0 views • 20 slides
Understanding Universal Instantiation in Deductive Reasoning
Universal instantiation is a crucial tool in deductive reasoning, allowing us to derive specific conclusions from general statements. By combining universal instantiation with modus ponens and modus tollens, we can construct valid arguments such as universal modus ponens and universal modus tollens.
0 views • 13 slides
Importance of Universal Precautions in Schools
Universal Precautions are practices that help protect employees and students in schools from exposure to potentially infectious materials like blood. By using protective barriers, washing hands thoroughly, and cleaning contaminated surfaces, the risk of spreading infections is reduced. It's crucial
0 views • 12 slides
Achieving Universal Health Coverage: Insights from Latin America
The Lancet Series on Universal Health Coverage in Latin America explores the importance of the Latin American nations' experience in the global context, addressing profound inequalities, policy experimentation, and the quest for Universal Health Coverage. The series delves into political and technic
0 views • 15 slides
Understanding Universal Credit Entitlements and Energy Standing Charges
Studying full-time while in education may make you eligible for Universal Credit if certain criteria are met, such as being under 21, having child responsibilities, or being disabled. Additionally, explore discounts available for Universal Credit recipients, including travel and energy bill savings.
0 views • 6 slides
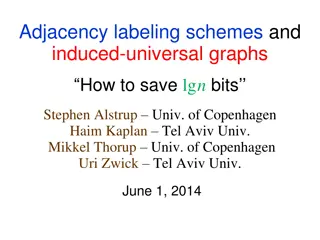
Adjacency Labeling Schemes and Induced-Universal Graphs
Adjacency labeling schemes involve assigning L-bit labels to vertices in a graph for efficient edge determination. The concept of induced-universal graphs is explored, where a graph is universal for a family F if all graphs in F are subgraphs of it. Theorems and lower bounds related to adjacency lab
0 views • 24 slides
Understanding Database Index Hashing Techniques
Hashing-based indexing in database systems is efficient for equality selections but not suitable for range searches. Both static and dynamic hashing methods exist, with static hashing involving fixed primary pages that are allocated sequentially. The process involves determining the bucket to which
0 views • 41 slides
Understanding Data Structures and Hashing in Java
Data structures play a crucial role in organizing, iterating, adding, deleting, and searching data efficiently. Hash tables, linked lists, trees, and more are explored in this overview, highlighting their strengths and trade-offs. Hashing, collision resolution strategies, and the importance of a wel
0 views • 19 slides
Understanding Hashing: Efficient Data Storage and Retrieval
Hashing is a powerful technique for achieving constant time complexity in finding and inserting data. It allows for quick access without the need for ordered elements. Direct addressing, limited hash operations, and efficient storage methods are discussed in this content to optimize data retrieval s
0 views • 100 slides
Understanding Sketching and Locality Sensitive Hashing in Data Mining
Explore the concepts of Jaccard Similarity and Cosine Similarity in data mining, along with their applications in recommendation systems and finding near-duplicates. Discover how Sketching and Locality Sensitive Hashing techniques help in efficiently identifying similar items and solving the Nearest
0 views • 63 slides
Universal Design in Disability Studies Programs: Bridging Theory and Practice
Explore the concept of Universal Design and its application in Disability Studies programs. Delve into the principles of Universal Instructional Design, challenges in implementation, and a case study of Disability Studies at CUNY SPS. Understand the importance of aligning academic discourse with the
0 views • 8 slides
Understanding Hash Tables and Hashing Concepts in Computer Algorithms
This content delves into the concept of Hash Tables, covering topics such as the support for dictionary operations, achieving constant time through direct address tables, case studies in web server maintenance, and an exploration of hashing functions and collision avoidance. It also touches upon key
0 views • 40 slides
Understanding Network Security Principles and Techniques
Explore the fundamental concepts of network security, including issues of confidentiality, integrity, and non-repudiability. Learn about the challenges of securing networks and the types of attacks that computer systems face. Dive into basic security techniques like hashing and symmetric key cryptog
0 views • 36 slides
Efficient Bucket Management in Extendible Hashing
In cases where a bucket (primary page) becomes full in extendible hashing, re-organizing the file by doubling the number of buckets can be costly in terms of resource utilization. An alternative approach involves using a directory of pointers to buckets and doubling the directory instead of all buck
0 views • 9 slides