Enhancing Transportation Performance Management through TSMO Collaboration
Advancements in technology and evolving customer needs are driving changes in transportation management. Transportation Systems Management and Operations (TSMO) offers strategies to optimize operational performance, complementing traditional capacity projects. Collaboration between TSMO and Transpor
1 views • 77 slides
Caterpillar Cat 329DL Excavator (Prefix TPM) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 27 slides
Lean Manufacturing: Improving Efficiency and Sustainability
Lean manufacturing principles such as 5S and Total Preventative Maintenance (TPM) focus on eliminating waste, optimizing processes, and ensuring sustainable improvements in production systems. Mistake-proofing, organization, cleanliness, and proactive equipment maintenance are key strategies discuss
0 views • 9 slides
Hardware Security and Trusted Platform Module Overview
This content discusses the importance of hardware security, distinguishing it from software security, and introduces the concept of Trusted Platform Module (TPM) as a trusted co-processor integrated into the platform to enhance security. It also highlights the role of the Trusted Computing Group (TC
0 views • 19 slides
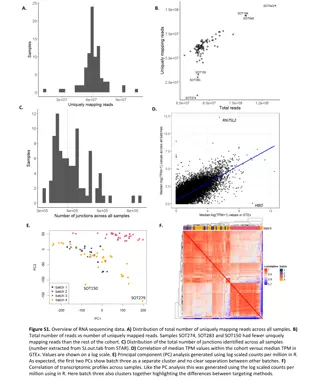
Overview of RNA Sequencing Data: Insights from Transcriptomic Profiling
This data set presents key findings from RNA sequencing analysis, including distribution of mapped reads, junction identification, TPM correlation, principal component analysis, and gene expression effects. Visual representations illustrate differences in gene expression profiles across samples, emp
0 views • 6 slides
Cloaking Malware with Trusted Platform Module in Secure Computing Environments
Exploring the concept of using Trusted Platform Modules (TPM) for cloaking malware to achieve secure and hidden computations. This research delves into leveraging hardware-based security features to execute and safeguard malicious code, highlighting the potential threats and implications within secu
0 views • 19 slides
Introduction to Lean Methodology and Tools for Process Improvement
Lean methodology focuses on identifying and eliminating waste in operations to improve efficiency. Key tools such as Kaizen, 5 Whys, Fishbone Diagram, and Spaghetti Diagram are utilized for continuous improvement. The building blocks of Lean include Kaizen, Pull/Kanban, TPM, 5S System, and more. Und
0 views • 8 slides