Modern Threat Modeling & Cloud Systems in OWASP Sacramento
Explore modern threat modeling techniques for cloud systems at OWASP Sacramento's June 2023 event. Agenda includes community topics and more. Membership at Granite City offers workspace perks and access to exclusive events. Learn about threat modeling history and methodologies like STRIDE and PASTA.
1 views • 14 slides
Hunting as a green investment
The contentious issue of hunting as a green investment, analyzing its role in sustainability and conservation. Discusses the challenges and potential contributions of regulated hunting practices to the green economy, shedding light on the ethical, ecological, and economic perspectives. Addressing th
5 views • 8 slides
Cisco 300-220 Certification: All You Need to Know
Begin Your Journey Here--- https:\/\/bit.ly\/3PbovcW --- Access comprehensive details on the 300-220 exam guide to ace the Cisco Certified Specialist Threat Hunting and Defending certification. Gather all essential information on 300-220 tutorials, practice tests, books, study materials, exam questi
3 views • 17 slides
Comprehensive Bug Hunting Toolkit for Cybersecurity Enthusiasts
Explore a detailed guide on bug hunting tools, techniques, and resources by expert bug hunter Orwa Atyat from Jordan. Learn valuable tips on finding high/critical bugs, conducting basic recon, subdomain enumerations, collecting URLs/endpoints, and searching for backup files. Enhance your cybersecuri
2 views • 14 slides
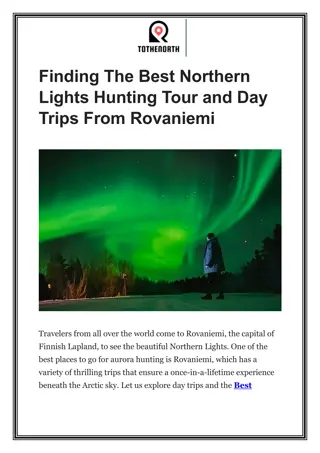
Finding The Best Northern Lights Hunting Tour and Day Trips From Rovaniemi
ToTheNorth\u2019s services come out to be an ideal result for your search of the day trips and Best Northern Lights Hunting Tour in Rovaniemi. Book your spot now to experience this tour. For more information and details, visit our website or contact us at al.korda89@gmail.com or 358414881706.
1 views • 4 slides
Benefits of the Best Northern Lights Hunting Tour in Rovaniemi
o increase your chances of seeing this breathtaking natural event, find the best Northern Lights hunting tour in Rovaniemi, such as from ToTheNorth. Your tour can become an incredible experience if you prioritize well-informed guides, remote viewing areas, and pleasant amenities.
3 views • 5 slides
Durable & High-Quality Backpacks & Rucksacks
We never underestimate the importance of a good-quality, weather resistant rucksack on an outdoor adventure. Survival Supplies Australia stocks only the best, high quality bushcraft, hunting, tactical, and hiking backpacks. Explore durable hiking backpacks, bushcraft backpacks, hunting backpacks and
0 views • 2 slides
Enhance Your Protection with MDR Cyber Security Services in Dallas
Do you wish to improve your security in Dallas against cyber threats? This is exactly where MDR Cyber Security services from Blackswan Cybersecurity can come in handy. While more complex forms of cyber threats and data breaches are becoming more popular, corporations need to acquire modern security
4 views • 8 slides
Durable & High-Quality Backpacks & Rucksacks
We never underestimate the importance of a good-quality, weather resistant rucksack on an outdoor adventure. Survival Supplies Australia stocks only the best, high quality bushcraft, hunting, tactical, and hiking backpacks. Explore durable hiking backpacks, bushcraft backpacks, hunting backpacks and
0 views • 1 slides
Knives High Quality Knives for Camping, Hunting & Bushcraft Survival
Fixed blade knives, hunting knives, and bushcraft survival knives are indispensable tools for outdoor enthusiasts, adventurers and bushcraft survivalists alike. With their sturdy construction and versatile designs, these knives are essential for various tasks such as cutting, chopping, and slicing,
1 views • 1 slides
Expert Tips from Recruitment Agencies in Kenya on Job Hunting
Job hunting can be a daunting task, especially in a competitive market like Kenya. However, with the right strategies and insights, you can navigate the job market successfully and land your dream job. Recruitment agencies Kenya, like Alliance Recrui
1 views • 9 slides
Exploring the Island: Lessons Learned and Plans Made
The boys explore the uninhabited island, learning about their surroundings and discussing survival strategies. Ralph believes his father will rescue them, while Jack focuses on hunting for food. The meeting dynamics change as rules are established, symbolized by the conch shell. Different characters
0 views • 13 slides
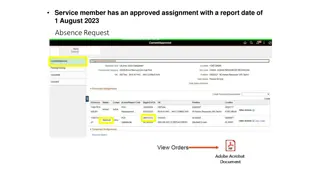
Absence Request Guidelines for Soldiers with Approved Assignments
Detailed instructions for submitting absence requests in conjunction with Permanent Change of Station (PCS) assignments. Users must follow specific steps for different absence scenarios, including absence with house hunting and without house hunting. The process involves entering chargeable days, ho
0 views • 7 slides
Cyber Threat Detection and Network Security Strategies
Threat detection is crucial in analyzing security ecosystems to identify and neutralize malicious activities. Methods like leveraging threat intelligence, behavior analytics, setting intruder traps, and conducting threat hunts are essential for proactive security. Implementing security through obscu
1 views • 51 slides
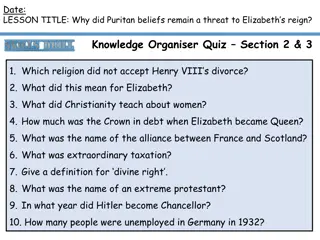
The Persistent Threat of Puritan Beliefs to Elizabeth's Reign
The Puritan belief system posed a significant threat to Queen Elizabeth I's reign, challenging the religious settlement she had put in place. Puritans disagreed with key aspects of the Church of England, such as the use of crucifixes and clergy vestments, leading to conflicts and resistance. Elizabe
0 views • 10 slides
Understanding Stereotype Threat and Teacher Response in Education
Stereotype Threat Theory explores the fear of confirming negative stereotypes and its impact on academic performance. Reduction of this threat can lead to improved learning outcomes. Teacher response plays a crucial role in shaping student writing, with various studies highlighting the importance of
0 views • 9 slides
Mastering Job Campaigns for Successful Employment
Discover the ins and outs of launching an effective employment campaign, from understanding the nature of job campaigns to exploring the history of job-hunting methods. Learn about important aspects like employer perspectives, job-hunting myths, and the significance of an active approach in job camp
0 views • 21 slides
Behavioral Threat Assessment Tabletop Exercise - College First Year Analysis
Explore a comprehensive behavioral threat assessment tabletop exercise focused on analyzing a college first-year scenario. The exercise includes roles and responsibilities for players, facilitators, evaluators, and observers, guiding participants through phases to familiarize themselves with a stude
0 views • 19 slides
The Legend of Sherwood Forest: From Royal Hunting Reserve to Nature Reserve
Sherwood Forest, once a royal hunting reserve in the 10th Century, is renowned for its association with the legendary figure Robin Hood. The forest provided cover for both hunting and outlaws, eventually becoming a nature reserve attracting millions of visitors annually. Despite its reduced size fro
0 views • 9 slides
Understanding Cyber Threat Assessment and DBT Methodologies
Comprehensive information on methodologies and approaches useful for cyber threat assessment and Cyber DBT alongside classical DBT methodology as outlined in the NSS-10 document by S.K. Parulkar. The content discusses the importance of threat assessment, differences between physical and cyber threat
4 views • 17 slides
Challenges in Computer Systems Security
Understanding security in computer systems involves achieving goals in the presence of adversaries. However, this task is challenging due to the need to guarantee policies in the face of realistic and open-ended threat models. Issues can arise from problems with policy formulation, assumptions in th
0 views • 16 slides
Enhancing Incident Response Through Threat Intelligence
Explore the importance of threat intelligence in incident response, covering aspects such as understanding adversaries, assessing risks, evaluating threats, and leveraging strategic intelligence. Learn how organizations can benefit from a proactive approach to cybersecurity by utilizing threat intel
1 views • 18 slides
Standing Rock Game & Fish Big Game Hunting Recommendations 2023
Standing Rock Sioux Tribe, under the guidance of Director Jeff Kelly and tribal biologists, presents the 2023 hunting recommendations. The report highlights observations, success rates, proposed tag reductions for deer, and conservation efforts due to environmental conditions. Additionally, the docu
0 views • 22 slides
Comprehensive Training on Campus Threat Assessment Teams
Explore the advanced training curriculum developed by experts Marisa Randazzo, Ph.D., and Gene Deisinger, Ph.D., for Virginia Campus Threat Assessment Teams. The training covers areas like threat assessment processes, case management, legal updates, and challenges in team implementation. Participant
0 views • 92 slides
Mobile App Security Threat Modeling and Mitigation
Explore mobile app security threats, learn how to conduct threat modeling exercises, and implement mitigation strategies. Discover built-in security features, threat modeling technologies, and common threats like malware and code injection. Enhance your understanding of app security constraints and
0 views • 63 slides
Unveiling Cyber Threats in IoT Environments
Explore the world of cyber threat hunting and intelligence in IoT environments through the eyes of Ali Dehghantanha. Discover myths, truths, and applied research projects in collaboration with EU LEAs and SMEs. Learn about the importance of threat intelligence, intrusion detection, and securing IoT/
0 views • 23 slides
Pennsylvania School Threat Assessment: Keeping Schools Safe
Pennsylvania schools have implemented a Threat Assessment Team to ensure the safety and security of students, staff, and community members. The team follows specific guidelines and procedures to assess and address threats, involving key stakeholders and promoting collaboration among multidisciplinar
0 views • 37 slides
New Member Safety Briefing & Orientation at Camp Blanding Rod & Gun Club
Camp Blanding Rod & Gun Club offers recreational benefits to active and retired members of the Florida Army and Air National Guard. The club supports various charities and provides exclusive hunting and fishing opportunities. Members must adhere to safety protocols, follow hunting and fishing regula
0 views • 12 slides
Understanding Stereotype Threat in Education
Stereotype threat is a phenomenon where individuals from marginalized groups experience anxiety due to negative stereotypes about their abilities. This can impact their performance and self-perception. Various groups, such as African-Americans, Latinos, females in STEM, elderly individuals, Roma, an
1 views • 42 slides
Threat Assessment Tabletop Exercise Overview
Conducting a tabletop exercise focused on threat assessment in a school setting. The exercise agenda includes welcome, introductions, exercise goals, objectives, participants' roles, exercise structure, and rules. The goals are to test preparedness for potential threats, coordinate plans effectively
0 views • 33 slides
Understanding Threat Modeling and Offensive Security
Threat modeling in offensive security involves determining potential threat scenarios that could compromise a system, understanding the system from an attacker's perspective, and devising defensive strategies. It helps confirm security implementations, identify gaps, monitor shortcomings, vulnerabil
0 views • 31 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Pennsylvania School Threat Assessment Procedures and Guidance
Ongoing concerns about school safety led to legislation in 2019, requiring schools in Pennsylvania to establish threat assessment teams. This presentation provides an overview of the statute, threat levels, team responsibilities, procedures, and resources for school staff, parents, and guardians to
0 views • 25 slides
Conducting Threat Assessments Through the Atrocity Prevention Lens
This module from the GLOBAL CENTRE FOR THE RESPONSIBILITY TO PROTECT focuses on conducting threat assessments through an atrocity prevention lens. It covers risk identification, situational awareness in field settings, information collection methods, addressing vulnerabilities of women and children,
0 views • 20 slides
Bomb Threat Preparedness Guidelines for Shifa International Hospital
The Shifa International Hospital emphasizes the importance of maintaining a secure environment for employees, patients, and visitors in the event of a bomb threat. This presentation covers the types of bomb threats, steps to follow in case of a bomb threat, and provides guidance on handling telephon
0 views • 14 slides
High School Students Behavioral Threat Assessment Tabletop Exercise Analysis
Conduct a tabletop exercise analyzing the behavioral threat assessment of two high school students. Explore roles and responsibilities, exercise itinerary, goal, and purpose to enhance threat assessment team preparedness and response. Utilize simulated scenarios to simulate real-world events for opt
0 views • 23 slides
Examining Stereotype Threat in Engineering Education
Exploring the experiences of female engineering students facing stereotype threat, this critical theoretical framework study sheds light on the challenges that impact their academic journey. Through narrative inquiry methodology, the research focuses on white female students to understand how stereo
0 views • 37 slides
2021 Mammal Hunting Regulations and Recommendations for Consideration
This collection of images and information details the 2021 mammal hunting regulations, recommendations for consideration, changes in hunter success rates, pronghorn numbers in Zone 3, and hunter success in Zone 3 likely tables in California. It discusses modifications to deer hunt seasons, tag quota
0 views • 10 slides
School Safety and Threat Assessment Program Overview
Fact-based Threat Assessment for Safe and Supportive School Programs involves identifying, inquiring, assessing, and managing potentially dangerous situations. It aims to distinguish between those making threats and those posing real risks, without profiling or labeling individuals. Understanding th
0 views • 20 slides
Impact of Stereotypes on Perceived Facial Threat in Women Offenders
Facial expressions play a significant role in understanding emotions, but stereotypes can influence how people perceive facial affect. This study examines how reading tabloid articles about crimes committed by dark and light-skinned women offenders affects the perceived facial threat. Using a 2x2 fa
0 views • 9 slides