Identity Theft Prevention Program
Ensure staff understand their responsibility to protect sensitive information and know the steps to prevent, detect, and respond to identity theft. This training is required as part of the Montana Tech Identity Theft Prevention Program.
1 views • 31 slides
Prevent Identity Theft: Tips and Actions
Understand identity theft, learn how to protect against it by safeguarding your information and spotting signs early on, and know the steps to take if it happens to you. Start a conversation and report any fraud promptly. Get informed at ftc.gov/PassItOn.
0 views • 10 slides
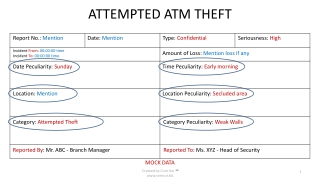
Attempted ATM Theft Incident Report
An attempted theft at an ATM located in a bank branch was unsuccessful but resulted in significant damage. Quick action by bank staff, including retrieving screenshots from backup, aided in the apprehension of the perpetrators. Recommendations were made to enhance security measures at ATM locations.
0 views • 4 slides
Understanding Cyber Crimes and Remedies in Gangtok by Himanshu Dhawan
Explore the world of cyber crimes and available remedies as presented by Advocate Himanshu Dhawan. Learn about different categories of cyber crimes, examples of financial and non-financial cyber crimes, data theft, and relevant sections of the IT Act, 2000. Gain insights into unauthorized access, da
1 views • 9 slides
Protecting Against Financial Scams: Insights & Prevention
Learn how to safeguard your finances from scams and identity theft. Discover the impact of scams on US citizens in 2019, the age group most affected by identity theft, the state with the highest identity theft reports, and the common delivery methods of scams. Gain valuable insights to protect yours
0 views • 27 slides
The Effectiveness of the Civil Rights Movement in Meeting the Needs of Black Americans up to 1968
Assessing the impact of the Civil Rights movement on Black Americans up to 1968 reveals significant progress in ending racial discrimination and segregation, securing voting rights, and advocating for social and economic equality. Despite achievements like the Civil Rights Act of 1964 and the Voting
0 views • 36 slides
Evolution of American Immigration Attitudes: 1918-1968
Attitudes towards immigration in the USA underwent significant shifts between 1918-1968 due to factors like isolationism, fear of revolution, prejudice, racism, social fears, and economic concerns. The influx of new immigrants from eastern and southern Europe challenged traditional American norms, l
1 views • 27 slides
Understanding White-Collar Crimes and Theft Offenses
Exploring the world of white-collar crimes and theft offenses, including common examples like embezzlement and fraud. Learn about larceny, robbery, burglary, and more, with insights on criminal acts, required state of mind, and motives behind such offenses.
0 views • 23 slides
Understanding the Red Flags Rule for Identity Theft Prevention
Learn how the Red Flags Rule aims to detect, prevent, and mitigate identity theft. Explore the goals of this training, identify red flags of potential fraud, and understand the application of the rule to financial institutions and creditors. Discover what covered accounts are and how to create unit-
2 views • 15 slides
Understanding Section 390 of the Indian Penal Code on Robbery
Section 390 of the Indian Penal Code discusses the concept of robbery and its elements of theft and extortion. It outlines that robbery involves imminent danger or the use of violence, and the offender voluntarily causes harm or induces fear to commit the crime. The section also provides explanation
0 views • 7 slides
Organizational and Managerial Issues in Logistics
This chapter delves into various organizational and managerial issues in logistics, covering topics such as organizational structure, productivity, quality, theft management, logistics social responsibility, reverse logistics, and programs to counter terrorism impact on logistics. Key terms and conc
0 views • 37 slides
If truly stolen crypto can be recovered in some way, can someone share the steps
1. Identify the Theft\n\nThe first step in recovering stolen cryptocurrency is to accurately identify and document the theft. This involves:\n\nNoticing unauthorized transactions in your wallet or exchange account.\nRecording all relevant transaction IDs, wallet addresses, and timestamps.\nCollectin
0 views • 15 slides
Protect Yourself from Identity Theft: Tips and Information
Learn about identity theft, how to spot it, major credit bureaus, keeping personal information secure, identity monitoring services, and ways to protect yourself from becoming a victim of identity theft.
0 views • 8 slides
Police Report: Theft of Amazing Robot
Mr. Silvester reported the theft of his 12-speed metallic blue Trek mountain bike, detailing the circumstances and security measures taken prior to the incident. The locked garage was found forced open with the missing bike bearing a security tag. The police investigation uncovered evidence suggesti
0 views • 10 slides
Holiday Season Safety Tips from Spring Valley Village Police Department
Spring Valley Village Police Department in Houston, TX, provides valuable safety tips for residents during the festive holiday season, focusing on securing homes, being mindful of theft risks, watching out for distraction crimes, and establishing a nightly security routine. Public Service Announceme
2 views • 8 slides
Understanding and Preventing Identity Theft in Daily Life
Learn how to safeguard your personal info and prevent identity theft with practical, everyday tips.\n
2 views • 5 slides
Challenges and Impact of Stock Theft in Kenya: Lessons and Future Directions
Agricultural crime, particularly stock theft in Kenya, poses significant challenges affecting rural communities and the national economy. Livestock theft, a prevalent form of agricultural crime, not only results in financial losses but also undermines rural livelihoods and community cohesion. Despit
2 views • 15 slides
Safeguarding Against Identity Theft: Prevention and Remediation
Identity theft is a serious threat where personal information is stolen for malicious purposes like setting up accounts or accessing funds in your name. This guide explains what identity theft is, why you should be concerned, how thieves obtain information, signs of being a victim, and preventive me
0 views • 22 slides
Protect Yourself: Identity Theft and Consumer Protection Insights
Explore the realms of identity theft, consumer protection laws, and fraud prevention strategies. Learn about consumer rights and responsibilities, ways to avoid financial scams, and agencies providing assistance. Discover the importance of safeguarding personal information to prevent fraud and ident
0 views • 21 slides
Understanding Section 3 Requirements in Housing and Urban Development Act of 1968
This content details the Section 3 requirements outlined in the Housing and Urban Development Act of 1968, focusing on providing economic opportunities to low- and very low-income workers, public housing residents, and businesses. It explains the definitions of Section 3 workers and businesses, high
0 views • 19 slides
Understanding the Extension of the Act of 5 December 1968 on Collective Labour Agreements
Exploring the extension of the Act of 5 December 1968 on collective labour agreements and joint committees, this workshop delves into its scope, importance of joint committees, and exceptions such as diplomatic missions. The Act applies to private sector employers, workers, and specified Belgian pub
0 views • 28 slides
The Cold War: Key Events up to 1968
West Berlin thrived while East Berlin suffered as the city became divided by a wall in 1961. The Vietnam War saw North and South Vietnam backed by different superpowers, leading to conflict until 1975. Cuba turned communist under Fidel Castro in 1959, prompting tensions with the US, notably during t
0 views • 9 slides
Understanding Theft Offences: Elements and Case Law
Theft offences, including theft and robbery, are defined under the Theft Act 1968. A person is guilty of theft if they dishonestly appropriate property belonging to another with the intention to permanently deprive them of it. The elements of theft involve actus reus (appropriation) and mens rea (di
0 views • 26 slides
Social Work Scotland Act 1968 and Its Impact: Reflections on Policy Intentions and Realization
The Social Work (Scotland) Act 1968 aimed to unify social work services and address the needs of vulnerable populations, particularly children. Despite its comprehensive provisions, the Act faced challenges in implementation, highlighting the gap between policy intentions and practical outcomes. Thi
0 views • 13 slides
Cold War Events Timeline - Key Moments from 1945 to 1968
Explore significant events of the Cold War era, from the Yalta Conference in 1945 to the Prague Spring in 1968. The timeline includes pivotal conferences, doctrines, conflicts, and speeches that shaped the geopolitical landscape of the time.
0 views • 26 slides
Kuken Co. Ltd.: Leading Provider of Specialized Tools Since 1968
Kuken Co. Ltd., established in March 1968 in Habikino-Shi, Osaka, is a reputable company specializing in fastening tools, sanding tools, polishing tools, drilling tools, grinding tools, cutting tools, and advanced torque control tools. Their innovative products include impact wrenches, oil pulse wre
0 views • 12 slides
Civil Rights Obligations in Federal Funding Programs
Federal funding programs require adherence to civil rights obligations, as enforced by the Office for Civil Rights. This includes upholding non-discrimination laws such as Title VI of the Civil Rights Act of 1964, the Omnibus Crime Control and Safe Streets Act of 1968, Section 504 of the Rehabilitat
0 views • 63 slides
Understanding Burglary Offences and Acts Reus in Property Crimes
Burglary is a serious property offence outlined in the Theft Act 1968, with distinct elements and penalties. The actus reus of burglary involves entry as a trespasser into a building with intent to steal, cause harm, or damage property. Differentiating between the offenses under section 9(1)(a) and
0 views • 11 slides
Understanding Robbery: Elements, Definition, and Distinctions
Robbery, defined under Section 8 of the Theft Act 1968, involves the act of stealing with the use of force or threat of force. This offense carries serious consequences, including a potential life imprisonment sentence. The key elements of robbery include the actus reus of theft and force, along wit
0 views • 11 slides
Protect Yourself from Identity Theft and Financial Crimes
Learn about identity theft, how it occurs, and steps you can take to protect yourself. Discover common methods used by fraudsters and the Equifax data breach incident. Find out what to do if you've been impacted by identity theft. Enroll in the TrustedID Premier credit monitoring service for free.
0 views • 23 slides
Addressing Vehicle Theft Crisis: Compulsory Engine Immobilisers in Queensland
Australia faces a significant vehicle theft issue, with Queensland being particularly affected. The societal and individual impacts are vast, highlighting the urgent need for implementing compulsory installation of engine immobilisers in passenger vehicles to combat theft, reduce crime rates, and pr
0 views • 21 slides
Understanding Wage Theft: A Closer Look at Violations and Consequences
Wage theft, a prevalent issue in the labor market, encompasses various violations such as not paying minimum wage, altering breaks, and misclassifying employees. The Fair Labor Standards Act of 1938 addresses these offenses with penalties, including imprisonment for repeat offenders. Studies indicat
0 views • 15 slides
Protect Yourself from Identity Theft: Tips and Actions to Take
Learn how to spot and respond to identity theft by checking your statements, credit reports, and taking immediate action if it happens. Protect your personal information and act swiftly to prevent further damage.
0 views • 11 slides
Understanding Identity Theft: Risks for Teens and How to Protect Yourself
Explore the world of identity theft and its potential impact on teenagers. Learn what identity theft entails, why teens are at risk, and the evolving tactics used by criminals. Discover how stolen identities are misused and ways to prevent falling victim to such crimes.
0 views • 41 slides
Frank Stella: Exhibition Highlights Through the Years
Explore the iconic artworks of Frank Stella showcased at renowned museums in New York City, Washington D.C., Los Angeles, and Hartford. The collection includes significant pieces like "Fez (2)" from 1964, "Empress of India" from 1965, "Harran II" from 1967, "Fortin de las Flores" from 1967, "Sinjerl
0 views • 10 slides
Effectiveness of the New Deal in Restoring Confidence and Addressing Economic Problems
In the context of the USA during 1918-1968, the New Deal implemented by President Franklin Roosevelt was aimed at addressing the devastating effects of the Great Depression. By restoring confidence in the banking system through measures like the Emergency Banking Act and engaging with the public thr
0 views • 18 slides
Combating and Preventing Organised Vehicle Crime in Belgium
The project in Belgium aims to combat and prevent organised vehicle crime through the development of a barrier model funded by the European Union. Despite a steady decline in motor vehicle theft in Belgium, challenges persist with the absence of specific expertise in law enforcement agencies and hot
4 views • 17 slides
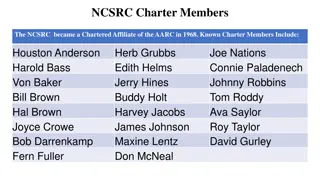
History of NCSRC: Charter Members and Significant Events
NCSRC, chartered affiliate of AARC since 1968, was founded by notable charter members. Key events include formation in 1965, split into NC and SC societies in 1968, and achievements like Sputum Bowl victories and legislations in subsequent years. The organization has evolved through advocacy, educat
0 views • 17 slides
Understanding Robbery: Elements and Distinctions
Robbery, as defined in Section 8 of the Theft Act 1968, involves the act of stealing accompanied by the use of force or the threat of force to instill fear in order to commit the theft. This offense is considered more serious than theft and can lead to a life imprisonment sentence. The key elements
0 views • 11 slides
History of the Pennsylvania General Assembly Before and After the 1968 Legislative Modernization Commission
The Pennsylvania General Assembly, America's largest full-time legislature, faced chronic deficits and partisan combat in 1968, leading to the creation of a bipartisan Commission on Legislative Modernization. The commission, comprising experienced leaders, aimed to improve legislative performance an
0 views • 22 slides