Understanding Vulnerability: Meaning, Types, and Factors affecting Vulnerability
This article explores the concept of vulnerability, including its meaning, types (physical and social), and factors that contribute to vulnerability. It discusses the impact of hazardous events on communities, infrastructure, and the environment, and highlights the importance of awareness and prepar
26 views • 31 slides
TIBCO TCP-TM Exam Overview & TCP BusinessEvents Exam Questions
Start here---https:\/\/bit.ly\/42Mp9mW---Get complete detail on TCP-TM exam guide to crack Professional. You can collect all information on TCP-TM tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Professional and get ready to crack TCP-TM certifica
3 views • 14 slides
TIBCO TCP-BE Exam Success: Key Concepts and Practice Sessions
Begin your journey here---https:\/\/bit.ly\/3UUOF7y---Discover comprehensive details on the TCP-BE exam guide to excel as a Professional. Gather all the essential information on TCP-BE tutorials, practice tests, books, study materials, exam questions, and syllabus. Strengthen your expertise in Profe
3 views • 14 slides
Understanding Risk Management in Environmental Geography and Disaster Management
Risk management in environmental geography and disaster management involves assessing the potential losses from hazards, evaluating vulnerability and exposure, and implementing strategies to mitigate risks. It includes calculating risk, dealing with risk through acceptance, avoidance, reduction, or
1 views • 10 slides
Comprehensive Guide to Vulnerability Mapping in Election Planning
Explore the significance of Vulnerability Mapping (VM) in empowering vulnerable voters, understand the concept, role of DEO/RO, and the objective of identifying and addressing voter vulnerability. The presentation emphasizes pre-poll and post-poll actions, remedial measures, and timelines, providing
3 views • 42 slides
Vulnerability Mapping (VM).Guidance Plan
Vulnerability Mapping (VM) is crucial in empowering vulnerable voters by identifying and addressing potential threats to their exercise of franchise. This guide explains the concept of vulnerability mapping, its role in ensuring free and fair elections, and the responsibilities of election officials
2 views • 42 slides
Understanding Telecom Security Testing: Vulnerability Assessment & Remediation
Telecom security testing is crucial for safeguarding infrastructure against hacks. Learn about vulnerability assessment, common weaknesses, types of vulnerabilities, severity scoring, and automated tools like Nessus and Nexpose. Explore network, web application, and host-based vulnerability testing
0 views • 18 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
Understanding the Vulnerability Index for Small Island Developing States
This article discusses the concept of vulnerability in the context of countries, focusing on Small Island Developing States (SIDS). It explores the differences between vulnerability and poverty, the history of vulnerability index development from SIDS to Least Developed Countries (LDCs), and critiqu
8 views • 44 slides
Understanding TCP/IP Networking Fundamentals
Explore the basics of TCP/IP networking, including protocols like IP, UDP, RTP, and more. Learn about the structure of the Internet, the role of routers, OSI network model, TCP/IP network model, and packet encapsulation in data transmission. Gain insights into the layers of the OSI model and the TCP
1 views • 36 slides
Understanding OSI Model and TCP/IP Protocol Suite
Explore the concept of layering in data communication, comparing the OSI model and TCP/IP protocol suite. Learn about protocol layers, protocol hierarchies, and the functionality of each layer in these models. Discover the interrelationships between layers and the evolution from OSI to TCP/IP.
5 views • 57 slides
Understanding TCP Congestion Control in Operating Systems
TCP congestion control is crucial for maintaining stability and efficient data transmission in computer networks. This article delves into the history and development of congestion control algorithms, highlighting key components such as additive-increase, multiplicative-decrease, and slow-start reac
0 views • 12 slides
Understanding Mobile Computing and TCP/IP Protocol Suite
Mobile computing is crucial for continuous internet connectivity regardless of physical location. The TCP/IP protocol suite, consisting of Transmission Control Protocol (TCP) and Internet Protocol (IP), forms the backbone of internet infrastructure. IP addressing and mobility challenges are addresse
1 views • 51 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding OSI Model and TCP/IP Protocol Suite in Computer Networking
This chapter explores the OSI model and TCP/IP protocol suite, delving into protocol layers, addressing mechanisms, and network components. It highlights the interface between layers, functions of each layer in the OSI model, and compares TCP/IP protocol suite layers with OSI model layers. The discu
0 views • 30 slides
TCP Manager Module Orientation Overview
The TCP Manager Module Orientation provides an in-depth look at the TimeClock Plus (TCP) system, including employee setup, time tracking, leave requests, and clocking rules. The system allows for seamless management of staff time and schedules, with features such as automatic time adjustments, accru
0 views • 14 slides
Enhancing TCP Performance: Understanding Maximum Window Size
Explore the concept of increasing the maximum window size of TCP to improve performance. Delve into discussions on the current limitations, proposals for enhancement, and the importance of understanding TCP sequencing. Discover insights on why the maximum window size must be less than 2^30 and wheth
0 views • 8 slides
Gender Considerations in Climate Vulnerability and Risk Assessments for Agriculture
This training workshop explores the intersection of gender, climate vulnerability, and risk assessments in adaptation planning for the agriculture sectors. It delves into how women and men may experience climate change effects differently and discusses ways to ensure gender considerations are includ
0 views • 6 slides
Understanding TCP and UDP in Computer Network Interoperability
The Transport Layer in computer networks facilitates logical communication between application processes on different hosts. Two key transport protocols, UDP and TCP, provide distinct services - UDP offers unreliable and unordered delivery, while TCP ensures reliable and ordered delivery with featur
1 views • 9 slides
Regulations on 1,2,3-Trichloropropane (1,2,3-TCP) Contaminant Levels
State Water Board conducted a public hearing regarding the regulations on 1,2,3-TCP, a carcinogenic chemical found in groundwater. The proposed regulations aim to set Maximum Contaminant Levels (MCL) and other safety measures to protect public health. Stakeholder meetings and public workshops were h
1 views • 21 slides
Understanding TCP Protocol and Reliability in Networking
This content covers key concepts related to the TCP protocol in networking, including TCP header fields, sequence and acknowledgement numbers, the 3-way handshake, and reliability mechanisms such as error detection, feedback, and retransmission. It also discusses potential issues in TCP communicatio
8 views • 41 slides
Understanding TCP: Evolution, Features, and Operation
The lecture covers the Transport Layer focusing on Transmission Control Protocol (TCP). It discusses TCP's reliability, bi-directional byte streams, congestion control, flow control, connection setup, three-way handshake, connection tear-down, sequence number space, and bidirectional communication.
0 views • 48 slides
Communication Setup for Modbus TCP in Do-more Technical Training
Explore the configuration and setup of Modbus TCP communication in Do-more devices, including the use of built-in Ethernet ports and ECOM100 modules for both server and client roles. Understand the parameters, limitations, and expandable ranges for communication with Modbus TCP devices as slaves and
0 views • 28 slides
Coastal Vulnerability Assessment of Curacao, Netherlands Antilles
Conduct a comprehensive Coastal Vulnerability Audit of Curacao, Netherlands Antilles, using the Coastal Vulnerability Audit Tool (CVAT) to assess physical, human, and engineering infrastructure systems, as well as vulnerability, planning, and resiliency action plans. Consider factors such as climati
0 views • 10 slides
Understanding Socket Programming in Java
Exploring the essentials of socket programming with Java, covering topics such as network sockets, socket lifecycle, communication protocols (UDP and TCP), and considerations for client/server applications using UDP and TCP. TCP is highlighted as suitable for services like remote login and file tran
0 views • 18 slides
Understanding Sockets: A Comprehensive Overview
Sockets provide a standard interface for network protocols like TCP/IP, enabling connections between machines to send and receive data. The TCP protocol, part of the TCP/IP suite, is crucial for internet communications. Learn about the logical structure of sockets and how to create socket connection
0 views • 37 slides
TCP Data Plane Performance Diagnosis Research
Researchers from Princeton University and Duke University delve into diagnosing performance issues in TCP data planes within public clouds. They address challenges related to monitoring, identifying poor TCP performance sources, and diagnosing problems at the edge, proposing solutions for efficient
0 views • 20 slides
The Evolution of TCP and Internet Traffic Trends
The Internet landscape has seen significant changes with over 90% of traffic using encrypted payloads, a majority originating from cloud servers, and a notable shift towards QUIC protocol. The role of TCP as a reliable transport protocol is explored, highlighting its adaptive streaming capabilities
0 views • 38 slides
Understanding TCP Round-Trip Time Measurement
This presentation delves into the importance of measuring TCP round-trip time in the data plane, highlighting key reasons such as security against BGP hijacks and IP spoofing, performance enhancements, and improving user Quality of Experience. It explores monitoring at a vantage point, TCP sequence
0 views • 12 slides
Understanding TCP Flow Control and Congestion Control Variants
The text delves into TCP flow control and congestion control mechanisms, focusing on TCP Tahoe and Reno variants. It explains the sender-side congestion control algorithms, such as AIMD, slow start, and fast recovery. Details of TCP variants like BIC and CUBIC are also discussed, highlighting their
0 views • 29 slides
Enhancing TCP Fairness Using P4-Programmable Data Planes
This study presents a solution to improve TCP fairness in non-programmable networks by utilizing P4-programmable data planes. It addresses unfair bandwidth distribution issues in TCP traffic and proposes a system that leverages P4 switches for passive traffic monitoring and RTT computation.
0 views • 24 slides
Understanding TCP Sequence Numbers and Attacks
Explore the fundamental concepts of TCP sequence numbers and inference attacks, along with the design, implementation, and impact analysis of TCP attacks. Delve into the significance of TCP fields, the three-way handshake process, as well as sequence and acknowledgment numbers to gain a comprehensiv
0 views • 35 slides
Understanding Mobile Transport Layer and TCP Mechanisms
Mobile communications require efficient transport protocols like TCP for reliable data transmission in wireless and mobile networks. This involves addressing challenges such as packet loss, network congestion, and performance degradation. Key topics include TCP mechanisms, congestion control, and op
1 views • 15 slides
Understanding OSI Model and TCP/IP Protocol Suite in Computer Networking
This content delves into the OSI model and TCP/IP protocol suite, highlighting the protocol layers, addressing mechanisms, and communication scenarios. It explores the functions of each layer, the interface between layers, and compares the TCP/IP layers with the OSI model. Through examples and illus
0 views • 46 slides
Understanding Cellular Traffic Accounting and TCP Retransmissions
Delve into the complexities of cellular traffic accounting, focusing on the impact of TCP retransmissions on network data billing. Explore the challenges faced by cellular providers in accurately charging subscribers for data usage amidst increasing traffic volumes. Consider the implications of TCP
0 views • 31 slides
Understanding Vulnerability in Research Populations
Vulnerability in research populations refers to being exposed to harm without the ability to protect oneself adequately. Factors contributing to vulnerability include intrinsic limitations like decision-making capacity and situational influences such as political or economic circumstances. Different
0 views • 22 slides
Understanding Network Protocols: TCP, UDP, DHCP, DNS
Explore the fundamentals of key network protocols including TCP, UDP, DHCP, and DNS. Learn about IPv4 and IPv6 addresses, IP address classes, and the roles of these protocols in the TCP/IP suite. Understand the differences between TCP and UDP in terms of connection setup and reliability. Discover th
0 views • 13 slides
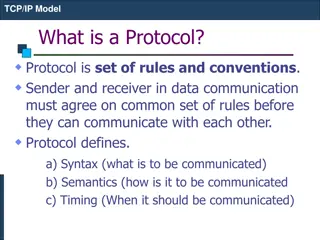
Understanding TCP/IP Protocol Suite
TCP/IP, a fundamental protocol suite, defines rules and conventions essential for data communication. It consists of layers like Network Access, Internet, and Host-to-Host, each serving specific functions. The suite ensures proper syntax, semantics, and timing for effective data exchange between sen
0 views • 53 slides
Exploring Vulnerability and Power Dynamics in Imperial Rome: Phaedrus' Perspective
Delve into the intricate relationship between constructions of vulnerability in imperial Latin texts and the material reality of vulnerability in ancient Rome. Discover how cultural perceptions of male citizen invulnerability rely on affirming vulnerability in others. Uncover the strengths of vulner
0 views • 10 slides
Understanding TCP Congestion Control Mechanisms
Delve into the world of TCP congestion control through advanced concepts such as slow start, congestion avoidance, feedback mechanisms, and various TCP variations like New Reno and Vegas. Explore the intricate algorithms and behaviors that govern network throughput and delay management.
0 views • 34 slides