Budget Execution Challenges in Somalia's Social Sectors
Addressing malnutrition in Somalia is hindered by low budget execution rates in the health and education sectors. Only a small portion of Official Development Assistance (ODA) is channeled through government systems, impacting service delivery and development financing. Donor-supported budgets for h
0 views • 32 slides
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Memory-unsafe languages like C and C++ are prone to Use-After-Free (UAF) vulnerabilities. PUMM introduces execution unit partitioning to efficiently tackle this issue. By segregating and managing execution units, PUMM aims to prevent UAF exploits and enhance software security.
0 views • 31 slides
Topic : Distinction between Modern and Traditional Logic.
Logic, as a normative study, focuses on distinguishing correct reasoning from incorrect. Traditional logic, based on Aristotle's work, emphasized syllogistic reasoning, while modern logic, pioneered by figures like Leibnitz and Russell, employs mathematical methods and symbolic logic for a more adva
2 views • 10 slides
COMPUTER ORGANISATION Register Transfer Language
Register Transfer Language is a symbolic notation used to describe the micro-operations transferring data among registers in computer organisation. It signifies the availability of hardware logic circuits to perform specified micro-operations and transfer results between registers. Register Transfer
6 views • 7 slides
Symbolic Execution Tree for a Program
Generate the complete symbolic execution tree for a given program by annotating nodes with path constraints and line numbers, aiding in understanding program execution flow.
0 views • 26 slides
Explore the Rich Cultural Heritage of the Haida People
Delve into the fascinating world of the Haida, a Native American group from the Pacific Northwest Coast known for their intricate art, symbolic designs, and rich mythological heritage. Discover how Haida symbols capture important events in their history, explore their unique tattooing traditions, an
0 views • 8 slides
Exploring Symbolic Equations with Deep Learning by Shirley Ho at ACM Learning Event
Join Shirley Ho at the ACM Learning event to delve into the world of symbolic equations with deep learning. Discover insights on leveraging deep learning for symbolic equations and engage in a knowledge-packed session tailored for scientists, programmers, designers, and managers.
0 views • 5 slides
Decoding Symbolic Thinking: Exploring the Power of Symbols in Learning and Perception
Delve into the world of symbolic thinking through the eyes of renowned artist René Magritte and explore how symbols shape our perception and understanding of the world. From dissecting Magritte's iconic painting to unraveling the intricacies of language as a symbolic system, journey through the int
2 views • 15 slides
Understanding the Neglected Provisions of Order XXI CPC, 1908
Explore the overlooked aspects of Order XXI CPC, 1908, focusing on the definitions, types of decrees, modes of execution, procedures for executing decrees, reasons for neglect, impact, recommendations, and conclusion. Learn about neglected provisions like summary execution, execution against legal r
0 views • 14 slides
Understanding Software Testing: Test Cases, Selection, and Execution
Software testing plays a crucial role in identifying and resolving issues within software products. Test cases, selection, and execution are fundamental aspects of the testing process. Test cases define conditions for testing software functionality, with a focus on repeatability and data specificity
2 views • 36 slides
Understanding Symbolic Interactionism in Sociology
Symbolic Interactionism is a school of thought in sociology that focuses on how individuals interact with each other through symbols, shaping social structures. It highlights the role of symbols in defining actions and meanings in social interactions. The concept explores how different socializing e
0 views • 18 slides
Symbolic Meanings of Twelve Chinese Zodiac Pairs Explained
Explore the symbolic meanings of the twelve Chinese zodiac pairs, highlighting the complementary personalities represented by each pair. From wisdom and diligence to bravery and care, the intricate relationships between these zodiac signs offer valuable insights into Chinese culture and values.
1 views • 8 slides
Understanding Sociological Perspectives
Sociologists employ three primary theoretical perspectives to explain how society influences young people and vice versa: the symbolic interactionist perspective, the functionalist perspective, and the conflict perspective. Symbolic interactionism focuses on symbols and face-to-face interactions, wh
1 views • 18 slides
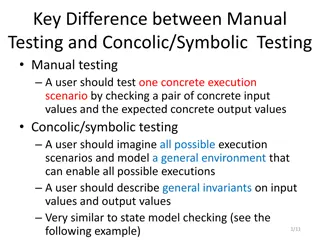
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Understanding Symbolic Logic: A Modern Approach
Delve into the world of symbolic logic where traditional and modern approaches differ. Learn how symbolic languages help overcome challenges with natural languages, leading to a clearer understanding of deductive reasoning through the analysis of premises, conclusions, compound statements, and logic
1 views • 32 slides
Understanding Propositional Logic at Kwame Nkrumah University
Dive into the world of symbolic logic and compound statements with a focus on Propositional Logic at Kwame Nkrumah University in Ghana. Explore the concepts of connectives, simple and compound statements, truth values, and more. Enhance your logical reasoning skills through a tutorial on symbolic lo
0 views • 57 slides
Ensuring Security in Persistent Key-Value Stores using Shielded Execution
This content discusses the challenges and solutions for securing LSM-based Key-Value stores in untrusted computing environments using Shielded Execution. It addresses the need for confidentiality, integrity, and freshness of data in persistent storage systems. The research explores Trusted Execution
0 views • 32 slides
Introduction to Symbolic Logic: Understanding Logical Inferences
Logic is the study of reasoning methods to distinguish between correct and incorrect arguments. Symbolic Logic involves representing logic symbolically for easier understanding and manipulation. Logical inferences help in making decisions based on reasoning chains. The content discusses the use of l
1 views • 28 slides
Modes of Execution of Decree in Civil Law
The lecture discusses the various modes of execution of decree in civil law, such as execution against a person through arrest and detention, and execution against property. It explains the procedures involved in arrest and detention, including the conditions for release, restrictions on arrest, and
0 views • 9 slides
Understanding Java Memory Management
Explore how memory is managed in Java programs, including memory allocation for code, objects, and execution stack. Learn about memory areas like the execution stack and heap, and understand the concept of activation records in method execution.
0 views • 27 slides
Exploring Instruction Level Parallel Architectures in Embedded Computer Architecture
Delve into the intricacies of Instruction Level Parallel Architectures, including topics such as Out-Of-Order execution, Hardware speculation, Branch prediction, and more. Understand the concept of Speculation in Hardware-based execution and the role of Reorder Buffer in managing instruction results
0 views • 51 slides
Evolution of Execution Methods in Modern Society
Explore the historical and modern methods of execution, from hanging to lethal injection, and the transition towards more civilized approaches. Learn about the contributions of prominent figures like Elbridge Gerry in advocating for humane execution methods. Delve into the commercial rivalry between
0 views • 13 slides
Secure and Efficient Multi-Variant Execution in Distributed Settings
This paper discusses dMVX, a system for secure multi-variant execution in distributed settings to mitigate memory errors and protect against attacks. Using leader and follower variants, diversified program variants run in lockstep to ensure security. The system monitors and replicates I/O results, e
0 views • 35 slides
Ceremonial Possession Practices in Europe's New World Conquest
Patricia Seed's book explores how European nations utilized ceremonial practices to claim ownership of the New World between 1492-1640. Each nation employed symbolic gestures to legitimize their rule, leading to conflicts over territory. Critics such as Las Casas, Van Der Donck, and Williams challen
0 views • 11 slides
Exploring the Archetypal Symbolism of the Whale in Moby-Dick
The concept of the whale as an archetype, deeply rooted in human consciousness, is examined through the lens of Moby-Dick. The symbolic significance of the whale, drawing on mythology and literature, captures universal themes of fear, awe, and nature's power. Delving into the literary analysis of Mo
0 views • 4 slides
Understanding Symbolic Logic and Rules of Inference
Explore the realm of symbolic logic and rules of inference through Modus Ponens, Well Formed Formulas (WFFs), truth tables, and more. Discover how logic is topic-neutral and test arguments for validity using truth tables. Dive into the world of logical equivalence and consistency with practical exam
0 views • 15 slides
Enhancing Online Service Security through Symbolic Transaction Certification
The research discusses securing multiparty online services through the certification of symbolic transactions, addressing logic flaws and the importance of program verification. The Certification of Symbolic Transaction (CST) approach is presented as an effective way to verify system-wide properties
0 views • 22 slides
Symbolic Communication in African Literary Arts: Proverbs and Visual Symbols
Exploring the use of African proverbs and symbols as forms of communication in literature, particularly in Nigeria. The incorporation of Adinkra patterns, Akan symbols, and visual representations of proverbs in fiction writing and cultural traditions is highlighted, showcasing the rich symbolic heri
0 views • 13 slides
Understanding Code Execution Graphs and Superblocks in Software Analysis
Explore the concepts of Static Execution Graphs, Dynamic Execution Graphs, Superblocks, hot-path detection, and memory arithmetic in software analysis. Learn about the grouping of blocks, violation tracking, control dependencies, and code behaviors across time through these graphical representations
0 views • 9 slides
Understanding Culture: Definition, Components, and Variations
Culture encompasses the entire way of life for a group of people, comprising material and symbolic elements passed down through generations. Categories include material and symbolic culture, with aspects like beliefs, customs, gestures, language, norms, and artifacts shaping cultural identity. Langu
0 views • 15 slides
Exploring Human-Animal Relationships Through Social Science Research: A 25-Year Review
Delve into the intricate world of human-animal interactions with a comprehensive examination of 25 years of social science research. Discover thought-provoking studies that explore the symbolic, cultural, and emotional dynamics shaping our relationships with animals. From the moral universes of cock
0 views • 27 slides
Understanding Processes in Operating Systems - ECE344 Lecture 3 Summary
This lecture delves into the essential concepts of processes, threads, and synchronization in operating systems. Key topics covered include units of execution, representation of units of execution in the OS, process execution states, and state transitions. Users, programs, and the role of processes
0 views • 45 slides
InvisiSpec: Making Speculative Execution Invisible
InvisiSpec presents a novel defense mechanism to address speculative execution attacks in the cache hierarchy. By making speculative execution invisible to potential attackers, this holistic approach aims to mitigate the risks associated with exploiting side effects on incorrect paths, such as Spect
0 views • 18 slides
Multicycle Datapath and Execution Steps Overview
This content provides a detailed explanation of a multicycle datapath and the execution steps involved in processing instructions. It covers key elements such as instruction fetching, decoding, memory referencing, ALU operations, branch and jump instructions, as well as memory access for read and wr
0 views • 11 slides
Understanding Symbolic Execution and Directed Automated Random Testing
Symbolic Execution is a method used for analyzing programs to determine inputs causing each part to execute, vital in program testing. However, limitations arise in cases without code availability, hindering definitive path conditions. Directed Automated Random Testing (DART) overcomes this through
0 views • 20 slides
Secure Cloud Applications with Intel SGX - OSDI 2014 Presentation Summary
This presentation discusses the challenges of trusting cloud environments and proposes solutions utilizing Intel SGX technology. It explores the need for secure execution of applications on untrusted cloud platforms, presents existing solutions, and introduces the concept of Haven for private execut
0 views • 33 slides
Rethinking Processes with Threads in Operating Systems
Processes in operating systems traditionally include various resources and execution states, leading to inefficiencies in communication and parallel program execution. By separating the concept of a process from its execution state, modern OSes like Mac, Windows, and Unix introduce threads as lightw
0 views • 29 slides
Python Programming Essentials: Basics, Operators, Expressions, and Control Flow
This segment delves into the fundamentals of Python programming with a focus on essential concepts such as comments, numbers, strings, variables, arithmetic operators, logical operators, order of execution, expressions, and control flow statements like conditional execution and looping. Learn about
0 views • 12 slides
Understanding Predicate Logic and Quantifiers for Symbolic Proofs
Dive into the realm of predicate logic and quantifiers, exploring the nuances of symbolic proofs and evaluating logical statements. Learn about bound variables, domain considerations, and strategies for constructing iron-clad proofs using quantifiers.
0 views • 36 slides
Understanding Operating System Concepts: Multiprogramming, Multiprocessing, Multitasking, and Multithreading
In the realm of operating systems, terms like multiprogramming, multiprocessing, multitasking, and multithreading can often be confusing due to their similar appearance but distinct meanings. These concepts play a crucial role in efficiently managing resources in a computing system, particularly in
0 views • 6 slides