Welcome to the Coding Adventure, where students thrive through development
Hey there, fellow code enthusiasts! \ud83d\ude80 Ready to embark on a journey of building something truly amazing with Java Full Stack Projects? Whether you\u2019re a seasoned developer or just dipping your toes into the coding world, get ready for an exciting adventure! \n\n \n\"Ever dreamt of crea
1 views • 2 slides
Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
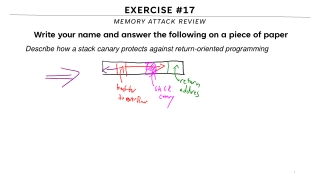
Memory Attack Review Overview
This content provides insights on memory attacks, particularly focusing on return-oriented programming and stack canary protection. It explores how stack canaries safeguard against return-oriented programming by detecting buffer overflows and preventing the alteration of return addresses. With a vis
1 views • 32 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
Principles for ESS Time Schedule & VDER Usecase.
Exploring the principles and key components of the VDER program, including ESS time scheduling and value stack compensation. The VDER components such as E-value, LSRV, DRV, Energy Value, and ICAP are discussed alongside the MCOS studies that assess marginal system cost reductions due to distributed
1 views • 8 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
Progress on Global Monitoring of Safely Managed Sanitation Services
Presentation on the progress of safely managed sanitation services globally, highlighting the off-track status towards meeting SDG targets. It covers the distribution of on-site and sewered sanitation, wastewater treatment, and challenges in safe management. The project includes pilots in Bangladesh
2 views • 18 slides
Unlock Your Coding Superpowers with Mastering in Full Stack Web Development in Java
Full stack web development is a process of developing web applications which includes front-end and back-end. Encompasses data, business layers, and presentation ones to provide a smooth user experience.
9 views • 3 slides
Unlock Your Coding Superpowers with Mastering in Full Stack Web Development in Java
Full stack web development is a process of developing web applications which includes front-end and back-end. Encompasses data, business layers, and presentation ones to provide a smooth user experience. Java is a highly popular object-oriented language that is chosen by various businesses because o
10 views • 3 slides
A Safety Expert’s Guide: How to Stack Pallets Safely
In the bustling world of warehouses, logistics, and manufacturing, the proper stacking of pallets is a critical aspect of maintaining a safe and organized workspace. As a safety expert, I\u2019ve seen firsthand the importance of implementing best practices to ensure the secure stacking of pallets. I
13 views • 2 slides
full stack React developers company
Binary Informatics is one of the global leaders in full-stack development with React, having an unmatched experience when it comes to the development of strong and easily scalable applications. Binary Informatics is recognized for its team of experienced developers, proficient in both front- and bac
0 views • 7 slides
Design Your Journey Enroll in the Best Full Stack Java Developer Course in Pune
Java is an extremely adaptable and robust programming language in the wide technology area. Ambitious developers can benefit greatly from having this ability due to its versatility and broad use across other disciplines. Pune has various options to launch your career if you're hoping to enter the fi
0 views • 3 slides
Design Your Journey Enroll in the Best Full Stack Java Developer Course in Pune
Java is an extremely adaptable and robust programming language in the wide technology area. Ambitious developers can benefit greatly from having this ability due to its versatility and broad use across other disciplines. Pune has various options to launch your career if you're hoping to enter the fi
1 views • 3 slides
full stack React development services
They can handle server-side logic, databases, and the integration of APIs with the power of React to bring responsive and interactive user interfaces. At Binary Informatics, we focus on modern development practices and agile methodologies to create scalable, maintainable, and efficient applications
0 views • 7 slides
MERN-Stack-Development
The approach to development is very agile, meaning the created software is flexible enough to make changes at a much faster rate by the dynamically changing needs of markets. Binary Informatics focuses on efficiency and quality, which helps businesses innovate faster with MERN stack-based solutions,
0 views • 8 slides
Piezoelectric Stack Actuator Market Analysis, Size, Share, Growth, Trends Foreca
The Global Piezoelectric Stack Actuator market stands at the forefront of technological driving advancements in various industries through its dynamic applications. These actuator systems harness the unique properties of piezoelectric materials, providing precision and versatility in a range of mech
0 views • 8 slides
Best Pallet Repair in North St Marys
Are you looking for the Best Pallet Repair in North St Marys? Then contact The Pallet People. They offer a wide range of pallets, both new and second-hand. They also provide a professional timber pallet repair service. Their team is passionate about providing the best quality pallets and services to
0 views • 6 slides
Essential Tips for Warehouse Safety: Protecting Employees from Common Hazards
Warehouse safety is (or at least, should be) a top priority for any organization dealing with storage and distribution. Warehouses are, by their very nature, fast-paced and bustling environments, with forklifts zooming around, pallets stacked high, and workers constantly on the move \u2013 and with
1 views • 4 slides
Efficient Stack Emission Monitoring Procedure for Air Quality Control
Stack emission monitoring is crucial for industries to assess and reduce pollutants in exhaust air. This procedure involves tasks like measurement, testing, and analysis of flue gases. Sampling sites are selected strategically for accurate readings, and molecular weight and gas velocity are determin
1 views • 11 slides
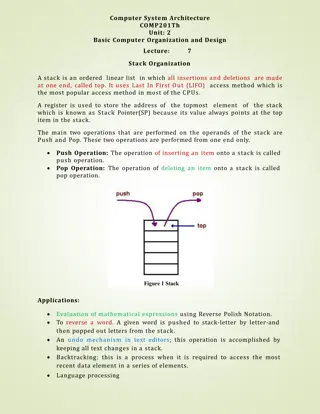
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
Understanding The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
Full Stack Skills for Digital Era Technology Architect
Specialized in full stack web & app development, with expertise in back-end technologies, cloud fundamentals, and security protocols. Proficient in programming languages like Java, NodeJS, Python, and frameworks like ReactJS and Angular. Emphasizes continuous learning, agility, and adaptability in t
2 views • 7 slides
Open Source PMCI Stack Implementation for Add-In Card Manageability by Sumanth Bhat
Sumanth Bhat, a BMC Firmware Engineer at Intel, presented an initiative on open-source PMCI stack implementation for managing add-in cards. The agenda covered an overview of platform architecture with Add-In Card management, existing mechanisms, PMCI architecture overview, and external interfaces li
3 views • 18 slides
Understanding Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Understanding Stacks: Fundamentals and Applications
Stacks are linear data structures where all operations happen at one end — the top. They follow the Last-In, First-Out (LIFO) principle. This text delves into stack operations like push and pop, stack data management, and various applications such as infix to postfix conversion. Detailed methods a
0 views • 14 slides
Neural Shift-Reduce Dependency Parsing in Natural Language Processing
This content explores the concept of Shift-Reduce Dependency Parsing in the context of Natural Language Processing. It describes how a Shift-Reduce Parser incrementally builds a parse without backtracking, maintaining a buffer of input words and a stack of constructed constituents. The process invol
0 views • 34 slides
The Ultimate Guide to Becoming a Full Stack Developer: What You Need to Know
In the dynamic world of web development, the role of a full stack developer is highly sought after. These versatile professionals are capable of handling both the front-end and back-end aspects of web applications, making them invaluable assets to an
0 views • 1 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Understanding Software Weaknesses and Exploits
Discover the vulnerabilities present in software such as buffer overflows and format string vulnerabilities, and how these weaknesses can be exploited to cause security issues. Learn about the technical aspects of weaknesses, stack frames, memory organization, and the potential consequences of stack
0 views • 57 slides
Understanding Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Overview of Material Handling Equipment and Containers
This chapter covers various types of containers used for the movement and storage of loose items, including pallets, skid boxes, and tote pans. It explains the significance of unitizing devices like pallets and unitizers in optimizing load efficiency. Additionally, the role of unitizers in assemblin
0 views • 32 slides