Budget Execution Challenges in Somalia's Social Sectors
Addressing malnutrition in Somalia is hindered by low budget execution rates in the health and education sectors. Only a small portion of Official Development Assistance (ODA) is channeled through government systems, impacting service delivery and development financing. Donor-supported budgets for h
0 views • 32 slides
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Memory-unsafe languages like C and C++ are prone to Use-After-Free (UAF) vulnerabilities. PUMM introduces execution unit partitioning to efficiently tackle this issue. By segregating and managing execution units, PUMM aims to prevent UAF exploits and enhance software security.
0 views • 31 slides
Understanding Taxation and Reporting of Futures and Options (F&O) Transactions
Explore the taxation aspects and reporting requirements related to Futures and Options (F&O) transactions. Learn about the types of F&O transactions, relevant heads of income for reporting income/loss, and the provisions of Section 43(5) of the Income Tax Act, 1961, defining speculative tran
1 views • 24 slides
Symbolic Execution Tree for a Program
Generate the complete symbolic execution tree for a given program by annotating nodes with path constraints and line numbers, aiding in understanding program execution flow.
0 views • 26 slides
Taxation of F&O Transactions under Indian Income Tax Law
This content discusses the taxation of Futures and Options (F&O) transactions in India under the Income Tax Act of 1961. It covers the types of F&O transactions, relevant heads of income for reporting income or loss, and the provisions of Section 43(5) related to speculative transactions. The articl
0 views • 24 slides
Understanding the Neglected Provisions of Order XXI CPC, 1908
Explore the overlooked aspects of Order XXI CPC, 1908, focusing on the definitions, types of decrees, modes of execution, procedures for executing decrees, reasons for neglect, impact, recommendations, and conclusion. Learn about neglected provisions like summary execution, execution against legal r
0 views • 14 slides
Understanding Software Testing: Test Cases, Selection, and Execution
Software testing plays a crucial role in identifying and resolving issues within software products. Test cases, selection, and execution are fundamental aspects of the testing process. Test cases define conditions for testing software functionality, with a focus on repeatability and data specificity
2 views • 36 slides
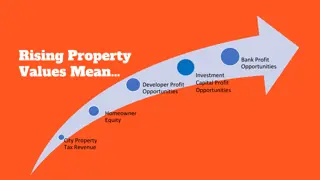
The Impact of Rising Property Values on Communities
Exploring the complex dynamics tied to increasing property values, this content delves into the implications for various stakeholders such as banks, developers, homeowners, and local politicians. It discusses the profit opportunities, equity issues, and challenges like increased rents, evictions, an
0 views • 8 slides
Understanding Case-Based Discussions for Effective Training
Case-Based Discussions (CBDs) are structured interviews exploring professional judgment in clinical cases. This method aims to enhance decision-making skills, prioritize options, and consider ethical implications. Key aspects include careful case selection, competency assessment, and avoiding specul
0 views • 15 slides
Understanding Futures Markets: Mechanism and Pricing Dynamics
Futures markets play a crucial role in price convergence between futures and spot prices of underlying assets. Traders can exploit arbitrage opportunities when the futures price deviates from the spot price during the delivery period. Settlement of futures contracts can be done through offsetting, d
3 views • 13 slides
Understanding Processor Speculation and Optimization
Dive into the world of processor speculation techniques and optimizations, including compiler and hardware support for speculative execution. Explore how speculation can enhance performance by guessing instruction outcomes and rolling back if needed. Learn about static and dynamic speculation, handl
0 views • 33 slides
Margaret Atwood's Analysis of "The Siren Song
Margaret Atwood, a renowned Canadian author, delves into the plight of humans through speculative fiction with elements of dystopia and science-fiction. She is an environmentalist who addresses issues like global warming in her works. Atwood's writing style includes free verse poetry with enjambment
16 views • 18 slides
Memory Consistency Models and Sequential Consistency in Computer Architecture
Memory consistency models play a crucial role in ensuring proper synchronization and ordering of memory references in computer systems. Sequential consistency, introduced by Lamport in 1979, treats processors as interleaved processes on a shared CPU and requires all references to fit into a global o
1 views • 64 slides
Enhancing Parallelization in Software Transactional Memory Systems
Explore how merge semantics in STMs enable speculative parallelization, addressing irregular parallelism challenges. The research covers connected components, parallel applications, and the utilization of speculation for optimized execution in diverse computing scenarios.
0 views • 43 slides
Understanding Robustness to Adversarial Examples in Machine Learning
Explore the vulnerability of machine learning models to adversarial examples, including speculative explanations and the importance of linear behavior. Learn about fast gradient sign methods, adversarial training of deep networks, and overcoming vulnerabilities. Discover how linear perturbations imp
0 views • 37 slides
Ensuring Security in Persistent Key-Value Stores using Shielded Execution
This content discusses the challenges and solutions for securing LSM-based Key-Value stores in untrusted computing environments using Shielded Execution. It addresses the need for confidentiality, integrity, and freshness of data in persistent storage systems. The research explores Trusted Execution
0 views • 32 slides
Modes of Execution of Decree in Civil Law
The lecture discusses the various modes of execution of decree in civil law, such as execution against a person through arrest and detention, and execution against property. It explains the procedures involved in arrest and detention, including the conditions for release, restrictions on arrest, and
0 views • 9 slides
Understanding Java Memory Management
Explore how memory is managed in Java programs, including memory allocation for code, objects, and execution stack. Learn about memory areas like the execution stack and heap, and understand the concept of activation records in method execution.
0 views • 27 slides
Energy-Efficient GPU Design with Spatio-Temporal Shared-Thread Speculative Adders
Explore the significance of GPUs in modern systems, with emphasis on their widespread adoption and performance improvements over the years. The focus is on the need for low-power adders in GPUs due to high arithmetic intensity in GPU workloads.
0 views • 46 slides
Exploring Instruction Level Parallel Architectures in Embedded Computer Architecture
Delve into the intricacies of Instruction Level Parallel Architectures, including topics such as Out-Of-Order execution, Hardware speculation, Branch prediction, and more. Understand the concept of Speculation in Hardware-based execution and the role of Reorder Buffer in managing instruction results
0 views • 51 slides
Evolution of Execution Methods in Modern Society
Explore the historical and modern methods of execution, from hanging to lethal injection, and the transition towards more civilized approaches. Learn about the contributions of prominent figures like Elbridge Gerry in advocating for humane execution methods. Delve into the commercial rivalry between
0 views • 13 slides
Secure and Efficient Multi-Variant Execution in Distributed Settings
This paper discusses dMVX, a system for secure multi-variant execution in distributed settings to mitigate memory errors and protect against attacks. Using leader and follower variants, diversified program variants run in lockstep to ensure security. The system monitors and replicates I/O results, e
0 views • 35 slides
Guide to Contacting Employers for Work Placements and Job Opportunities
Learn how to effectively contact employers for work placements and job opportunities by crafting speculative letters, covering letters, CVs, and application forms. Understand the purpose of each resource and gain insights into engaging with potential employers directly to enhance your chances of sec
0 views • 6 slides
Hardware-Assisted Task Scheduler for OS Intensive Applications
A hardware-assisted task scheduler called SchedTask is proposed to address the issue of instruction cache pollution in OS intensive applications. By utilizing SuperFunction characterization and a specialized scheduler, the system aims to optimize task execution on different cores for improved perfor
0 views • 28 slides
Exploring Modern AI Mythology and Science Fiction Interplay
The relationship between modern AI mythology and science fiction is examined through examples like Roko's Basilisk and "I Have No Mouth And I Must Scream." These narratives delve into the fears and possibilities surrounding artificial intelligence, blending speculative elements with ethical consider
0 views • 14 slides
Science Fiction Retrieval Practice: Short Stories Insights
Explore futuristic technologies, incongruity, and speculative fiction elements in science fiction short stories like "Robbie" and "There Will Come Soft Rains." Uncover the connections to historical events, like the Cold War, through literary analysis of these captivating narratives.
0 views • 16 slides
Humanity and Survival: Freezing Down (1969) by Anders Bodelsen
Novel explores themes of life vs. death, class division, loss of humanity, quest for perfection, and entrapment through a speculative fiction setting in 1973, 1995, and 2022. Central focus on the relationship between Bruno, Jenny, and Dr. Ackerman, as the Freezing Down process offers the possibility
0 views • 18 slides
Understanding Code Execution Graphs and Superblocks in Software Analysis
Explore the concepts of Static Execution Graphs, Dynamic Execution Graphs, Superblocks, hot-path detection, and memory arithmetic in software analysis. Learn about the grouping of blocks, violation tracking, control dependencies, and code behaviors across time through these graphical representations
0 views • 9 slides
Understanding Processes in Operating Systems - ECE344 Lecture 3 Summary
This lecture delves into the essential concepts of processes, threads, and synchronization in operating systems. Key topics covered include units of execution, representation of units of execution in the OS, process execution states, and state transitions. Users, programs, and the role of processes
0 views • 45 slides
InvisiSpec: Making Speculative Execution Invisible
InvisiSpec presents a novel defense mechanism to address speculative execution attacks in the cache hierarchy. By making speculative execution invisible to potential attackers, this holistic approach aims to mitigate the risks associated with exploiting side effects on incorrect paths, such as Spect
0 views • 18 slides
Multicycle Datapath and Execution Steps Overview
This content provides a detailed explanation of a multicycle datapath and the execution steps involved in processing instructions. It covers key elements such as instruction fetching, decoding, memory referencing, ALU operations, branch and jump instructions, as well as memory access for read and wr
0 views • 11 slides
Understanding Symbolic Execution and Directed Automated Random Testing
Symbolic Execution is a method used for analyzing programs to determine inputs causing each part to execute, vital in program testing. However, limitations arise in cases without code availability, hindering definitive path conditions. Directed Automated Random Testing (DART) overcomes this through
0 views • 20 slides
Speculative Region-based Memory Management for Big Data Systems
This research focuses on the challenges faced by big data systems, such as JVM crashes due to OutOfMemory errors and high management costs. It introduces a speculative region-based memory management technique to address these issues, aiming to optimize memory usage and improve system scalability. Th
0 views • 26 slides
Secure Cloud Applications with Intel SGX - OSDI 2014 Presentation Summary
This presentation discusses the challenges of trusting cloud environments and proposes solutions utilizing Intel SGX technology. It explores the need for secure execution of applications on untrusted cloud platforms, presents existing solutions, and introduces the concept of Haven for private execut
0 views • 33 slides
Rethinking Processes with Threads in Operating Systems
Processes in operating systems traditionally include various resources and execution states, leading to inefficiencies in communication and parallel program execution. By separating the concept of a process from its execution state, modern OSes like Mac, Windows, and Unix introduce threads as lightw
0 views • 29 slides
Python Programming Essentials: Basics, Operators, Expressions, and Control Flow
This segment delves into the fundamentals of Python programming with a focus on essential concepts such as comments, numbers, strings, variables, arithmetic operators, logical operators, order of execution, expressions, and control flow statements like conditional execution and looping. Learn about
0 views • 12 slides
Understanding Operating System Concepts: Multiprogramming, Multiprocessing, Multitasking, and Multithreading
In the realm of operating systems, terms like multiprogramming, multiprocessing, multitasking, and multithreading can often be confusing due to their similar appearance but distinct meanings. These concepts play a crucial role in efficiently managing resources in a computing system, particularly in
0 views • 6 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
Memory Allocation and Program Execution Overview
Understanding memory allocation is crucial for efficient program execution. This content delves into the importance of memory allocation, considerations for storing data during program execution, and the requirements for allocating memory efficiently. It also explores solutions for managing memory s
0 views • 35 slides
Understanding CPU Virtualization and Execution Control in Operating Systems
Explore the concepts of CPU virtualization, direct execution, and control mechanisms in operating systems illustrated through a series of descriptive images. Learn about efficient CPU virtualization techniques, managing restricted operations, system calls, and a limited direct execution protocol for
0 views • 18 slides