BCA 601(N): Computer Network Security
Explore various aspects of computer network security including cryptography, IP security, web security, and system security. Learn about authentication, encryption, key management, and network management security. Real-world examples and best practices covered.
0 views • 23 slides
Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Understanding Tax Expenditures and Their Impact on Government Revenue
Tax expenditures are provisions in the U.S. federal tax laws that result in revenue losses by allowing exclusions, exemptions, deductions, credits, preferential tax rates, and deferrals. This concept is crucial as it affects government revenue, and there are challenges in reporting these expenditure
3 views • 18 slides
Enhancing Security Definitions for Functional Encryption
This study delves into the realm of functional encryption (FE) against probabilistic queries, highlighting the necessity for improved security definitions to address existing limitations such as counter-intuitive examples and impossibility results. The exploration leads to proposing a new security n
4 views • 20 slides
Quick Course on Setting up Fund Accounting in QuickBooks Pro for Municipalities
Discover how to set up fund accounting in QuickBooks Pro for municipalities using class tracking features. Learn to define funds, track balances for revenues and expenditures, and create new revenue accounts. Explore examples of recording revenue and managing expenditures effectively.
0 views • 19 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Overview of Food Price Trends and Consumer Expenditures in the US
The presentation highlights the consumer spending on food, food price trends over time, 2021 food prices, and forecasts for 2022 in a historical context. It emphasizes that U.S. consumers spent 12% of their expenditures on food in 2020, aligning with historical averages. Food price inflation remaine
0 views • 21 slides
Overview of Ontario's Expenditures and Revenues
Ontario's projected expenditures for 2018-2019 are around $158 billion, with 30 ministries grouped into six major sectors. The top spending sectors include Health, Education, Other Programs, and Interest on Debt. Revenue sources for the same fiscal year are projected to be approximately $152 billion
7 views • 16 slides
Provincial Treasury Process for Dealing with Irregular Expenditures
The Provincial Treasury outlines the process for handling irregular expenditures, including the definition of irregular expenditure, regulations introduced, legal opinions, and duties of Accounting Officers (AOs) and Authorized Officials (AAs) to prevent and address irregularities. Various steps and
0 views • 12 slides
Colorado Expenditures on the Medically Indigent Presentation
The presentation focuses on Colorado's expenditures for the medically indigent, conducted by Yondorf & Associates. It outlines the background of the expenditures project, preliminary findings, and possible policy implications. The project aims to estimate current spending on Coloradans who cannot af
0 views • 12 slides
Evaluation Process for AAU Membership and Indicators
AAU evaluates universities for membership based on research and education profiles. Non-member universities exceeding standards may be invited to join, while current members falling below may face review. The process involves membership and phase 1 indicators, federal R&D expenditures, and expenditu
0 views • 12 slides
Missouri HealthNet Pharmacy Program and Budget Update Summary
The Missouri HealthNet Pharmacy Program and Budget Update for July 2023 provides detailed insights into the enrollees, expenditures, and services covered. It highlights the distribution of enrollees among different categories such as children, custodial parents, pregnant women, elderly, and disabled
0 views • 9 slides
Musculoskeletal Disorders in Norway: Statistics and Analysis
This information provides an in-depth look at musculoskeletal disorders in Norway, including disease categories, public expenditures, burden of disease, DALYs by ICD10 chapters, health expenditures, productivity loss, deaths, and YLDs in 2013. The data sheds light on the prevalence, impact, and dist
0 views • 9 slides
UC Merced Entertainment Policy Overview for Catering Recharges
University of California, Merced's entertainment policy (BUS-79) outlines expenditures for business meetings, entertainment, and other occasions, including guidelines for catering recharges. The policy covers purposes, maximum rates, general limitations, approval of expenditures, exceptions, busines
0 views • 17 slides
Litchfield Elementary School District Bond Update June 30, 2021
Litchfield Elementary School District provides an update on the 2014 Bond Authorization as of June 30, 2021. The District has issued bonds totaling $35 million with expenditures and available cash detailed. Expenditures include school remodeling, new construction projects, operational expenses, and
0 views • 11 slides
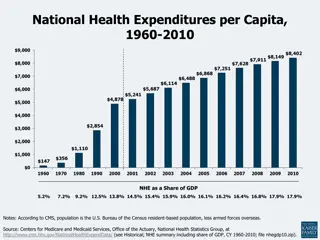
Trends in National Health Expenditures and Care Costs, 1960-2010
National health expenditures per capita and as a share of GDP from 1960 to 2010, along with average annual growth rates, show the evolving landscape of healthcare spending in the U.S. The data reveals changing patterns in healthcare expenditure and outlines the concentration of health care spending
0 views • 20 slides
Audit Report on Adult Corrections Expenditures
Adult corrections expenditures report from the Legislative Audit Bureau highlights trends in inmate population, operating expenditures, employee wages, turnover rates, vacancy rates, and inmate health care management issues. The report identifies areas of growth in corrections spending and offers re
0 views • 14 slides
Essential Guidelines for Documenting University Expenditures during Emergency
Guidelines for documenting essential expenditures at the university during emergencies, emphasizing the categories of essential activities to be maintained such as protecting life, preserving university property, supporting critical services, ensuring continuity of operations, education, student ser
0 views • 17 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
Medicaid Program Expenditure Analysis August 2022
Analysis of Medicaid program expenditures in August 2022 reveals interesting insights. Total enrollees in August 2022 were 1,358,275 with total expenditures amounting to $304,664,691.2. The report delves into expenditure distribution across various services, top drug classes per fiscal year, and Med
0 views • 12 slides
Chowan County Manager's Recommended Budget 2021-2022 Overview
The Chowan County Manager, Kevin Howard, has recommended a budget for FY 2021-2022 with details on property tax information, general fund revenues, revenue sources, and fund expenditures. The proposed budget includes information on assessed tax values, tax rates, revenue sources, and expenditures by
2 views • 7 slides
Public Housing Capital Fund Management Guidelines
Public Housing Capital Fund Management Guidelines provide detailed instructions for Public Housing Authorities (PHAs) regarding the proper utilization of capital funds, including obligations, expenditures, and modernization projects. PHAs are required to follow HUD regulations, maintain fiscal respo
0 views • 21 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
0 views • 41 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
Impact of MGNREGA on Private Coaching in West Bengal, India
This study explores the impact of the Mahatma Gandhi National Rural Employment Guarantee Act (MGNREGA) on private coaching expenditures in West Bengal, focusing on how participation and earnings under MGNREGA influence decisions related to private tutoring. More than half of households involved in M
0 views • 21 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Insights on Intergovernmental Funding of Surface Transportation
The interconnected nature of surface transportation funding system is highlighted, showing a decline in overall spending across federal, state, and local governments. Challenges in funding call for dialogue among all levels of government. The data reflects expenditures, funding sources, and the vary
2 views • 11 slides
Understanding HTTP Security Headers for Web Apps
Explore the importance of HTTP security headers on web applications through a detailed breakdown of headers like HSTS, XFO, XSS, CSP, CTO, RH, and FP. Learn how these headers enhance security by instructing browsers on handling website content, preventing various attacks. Gain insights on configurin
0 views • 68 slides
Understanding Obligations and Expenditures in Grant Management
Explore the definition and characteristics of obligations in grant management, including the importance of tracking and managing funds responsibly to avoid overages. Learn how purchase orders create obligations and how to report expenditures effectively within the period of availability of funds.
0 views • 28 slides
Financial Policy Recommendations for Accumulated Surplus Management
The council policy recommends retaining an accumulated surplus up to 4% of operating expenditures, with any excess transferred to the Capital Works Reserve. The rationale behind this policy includes ensuring cash flow, setting aside funds for future expenditures, maintaining a rainy day fund, and pr
0 views • 14 slides
2020 Impact Fee Summary Report
The 2020 Impact Fee Annual Report, Traffic Impact Fee Summary, and Park Impact Fee Summary outline the eligible project expenditures, impact fee balances, spending requirements, and more for the year. Key highlights include significant project expenditures, balance allocations, and future spending p
0 views • 6 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
0 views • 15 slides
Revolutionizing Security Testing with BDD-Security
Explore the innovative approach of Continuous and Visible Security Testing with BDD-Security by Stephen de Vries. Gain insights into how security testing can be integrated seamlessly into modern development practices, shifting the focus from reactive to proactive measures. Learn about the importance
0 views • 33 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Understanding Security Testing and Architecture
Explore the fundamentals of security testing, computer security goals, software security approach, and security architecture. Learn about securing computer assets, verifying trustworthiness of security mechanisms, and validating security architecture through threat modeling. Enhance your knowledge o
0 views • 57 slides