FACILITY MANAGEMENT & SAFETY
Facility management and safety are interlinked disciplines crucial for optimizing workflow and ensuring a safe environment in various facilities. This includes managing space, infrastructure, resources, and staff effectively. Specific focus on laboratory facility management involves maintaining qual
3 views • 19 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
Enhancing Safety: People Power SafetySTEP Refresher Training
Explore the comprehensive SafetySTEP Refresher Training program aimed at achieving safety through employee participation, engagement, and proactive safety measures. This training emphasizes creating a culture where safety is a core value, utilizing leading indicators to measure safety successes, and
0 views • 65 slides
Safety Initiatives at Utah State University
The safety committees at Utah State University are dedicated to fostering a culture of safety across the campus by identifying, preventing, and correcting safety concerns. They focus on areas such as promoting safety plans, ensuring chemical hygiene, and enhancing field safety and emergency response
0 views • 25 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Oklahoma School Safety Protocols Overview
Overview of the school safety protocols in Oklahoma, which define requirements based on COVID-19 alert levels per capita in each county. The protocols include instructions for different alert levels, mask recommendations, visitor limitations, and activity guidelines. Schools are expected to offer in
0 views • 9 slides
National Mine Safety Week 2023 - Vehicle Safety Guidelines
Explore the comprehensive safety guidelines for vehicle operation during National Mine Safety Week 2023. Learn about maintaining safety equipment, cabin safety systems, visibility safety systems, operational safety systems, emergency safety systems, other safety systems, training responsibilities, a
1 views • 10 slides
Understanding Post-Authorisation Safety Studies (PASS) in Pharmacovigilance
Post-Authorisation Safety Studies (PASS) are conducted after a medicinal product is authorized to gather more safety information or assess risk management effectiveness. These studies evaluate the safety and benefit-risk profile of the product, aiding regulatory decision-making. PASS aims to identif
0 views • 4 slides
Work Protocols and Safety Measures for Employees Returning to Work
In the wake of the COVID-19 pandemic, these work protocols emphasize roles, responsibilities, and mental wellbeing of employees. Pre-work precautions at home, personal measures, testing procedures, increasing awareness, and safe travel guidelines are highlighted to ensure a secure work environment.
0 views • 16 slides
Taking Chances: A Reflection on Personal Safety Commitment
Today's presentation prompts reflection on personal safety behavior, emphasizing the importance of upholding safety rules and commitments both at work and in daily life. It underlines the consequences of taking risks and breaking safety protocols, urging individuals to prioritize safety for themselv
0 views • 15 slides
Comprehensive Facility and Safety Management Programs at Shifa International Hospitals
Enhance safety at Shifa International Hospitals with robust facility and safety management programs covering emergency protocols for earthquakes, fire, and security incidents. Detailed procedures for risk assessment, color-coded emergency announcements, and staff training ensure a proactive approach
0 views • 19 slides
Comparative Analysis of Aviation Safety Management Systems: MSG-3 vs. SMS
The aviation industry continuously strives to enhance safety, leading to the development of Safety Management Systems (SMS) by ICAO and the longstanding Maintenance Steering Group (MSG-3) program. These systems focus on improving safety through different approaches, with MSG-3 emphasizing engineerin
1 views • 25 slides
Laboratory Safety Protocols and Pathogen Classification
Scientist must adhere to lab safety protocols including wearing safety gear, proper waste disposal, and handling chemicals carefully. The classification of pathogens varies by country based on WHO guidelines into four risk groups. Understanding these protocols and classifications is crucial for a sa
0 views • 17 slides
Safety Assessment and Accelerator Safety Envelope Review
Overview of the Safety Assessment Document (SAD) and Accelerator Safety Envelope (ASE) process for the 400 MeV Test Area (MTA) at Fermilab. The document details the shielding assessment, approval process by various committees, and updates made to the SAD chapters and the Accelerator Safety Envelope.
4 views • 8 slides
Proactive Safety Measures: PDO Safety Stand Down April 2024
A Safety Stand Down is a crucial activity to proactively discuss safety with employees, emphasizing risk awareness and injury prevention. The incident involving a fatal injury during Rig Move activities serves as a catalyst for reflection and improvement regarding safety procedures. This guide provi
1 views • 4 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Neutrino Platform Hall Access and Safety Guidelines
Guidelines for accessing and ensuring safety within the Neutrino Platform Hall at CERN, including registration, permissions, safety trainings, required equipment, online trainings, access points, and safety team responsibilities. Access is granted through registration at CERN, completion of safety t
1 views • 7 slides
Importance of Safety Education for Graduate and Undergraduate Students
Graduate and undergraduate students often lack safety knowledge and ethics, emphasizing the need for safety education over mere training. Safety education builds critical thinking, promotes safety ethics, and prepares individuals to handle future safety issues. Incorporating safety teachings through
3 views • 11 slides
Understanding ICF-IID Attic Fire Safety Requirements
The presentation, led by Donald Howard, a Health Insurance Specialist with CMS, focuses on the regulatory and life safety code requirements for attic fire safety in Intermediate Care Facilities for Individuals with Intellectual Disabilities (ICF-IID). It covers topics such as attic protection requir
0 views • 14 slides
NUSSC 57th Meeting - End of Term Report & Safety Standards Update
The 57th Meeting of the Nuclear Safety Standards Committee (NUSSC) concluded its 9th term with significant achievements including the approval and publication of multiple safety standards. Key highlights include the development of new standards such as SSG-3, SSG-88, SSG-89, and SSG-90 focusing on v
0 views • 8 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
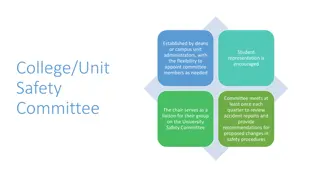
Established Campus Safety Protocols and Procedures
A comprehensive overview of safety measures within a university setting, including the formation of safety committees, roles of safety representatives, and the authority of the Environmental Health and Safety Division. The content emphasizes the importance of compliance with health and safety regula
0 views • 4 slides
Safety Practices and Reporting in Clinical Research
Safety practices and reporting in clinical research are crucial for ensuring the rights, safety, and well-being of trial subjects. This includes monitoring safety, reporting adverse events promptly, and following regulatory requirements. Investigators play a vital role in assuring subject safety and
0 views • 33 slides
Daly ES Re-Opening Plans and Safety Protocols
Get the latest updates on Daly ES re-opening plans, including hybrid learning start dates, school schedule changes, health and safety measures, classroom setups, and health room support protocols. Stay informed about important dates, health protocols, mask requirements, and more to ensure a smooth t
0 views • 11 slides
Safety Clearance Procedure for NA62: Overview and Recommendations
The conventional safety clearance procedure for NA62 involves checks by DGS-SEE (HSE) and obtaining radiological safety clearance from the DGS/RP group. Various safety checks are outlined in memorandums by Mark Hatch and Jonathan Gulley. Safety files for NA62 are noted to be in poor states, lacking
0 views • 8 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Exploring the Role of Safety Engineers in Ensuring Workplace Safety
Health and Safety Engineers play a crucial role in designing procedures and systems to keep people safe in various work environments. This Career Spotlight highlights the responsibilities of Safety Engineers, such as creating safety protocols and rules for workers to follow. Students are encouraged
0 views • 7 slides
Update on Safety Standards Implemented by TRANSSC
The 45th Transport Safety Standard Committee (TRANSSC) is making significant progress in endorsing and publishing safety standards for various transportation sectors. The scientific secretary, Dominique Delattre, reported on the status of endorsed safety standards, with several publications and ongo
1 views • 10 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Safety Rules and Guidelines for S-MODE 2021 Pilot Campaign
Providing health and safety regulations for fieldwork during the Fall 2021 S-MODE Pilot Campaign, this resource covers various safety plans, protocols, and emergency procedures, including COVID-19 mitigation strategies, emergency contact information, and general safety guidelines for personnel invol
0 views • 25 slides
Workplace Safety Guidelines and Objectives
This content provides comprehensive information on workplace safety, including general safety rules, evacuation routes, use of safety equipment, personal protective equipment, hazardous materials safety, and first aid principles. It emphasizes the importance of maintaining a safe work environment, i
0 views • 54 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides
Tritium Safety Protocols and Containment Procedures for Hall A Target Facility
This document outlines the safety protocols and containment procedures related to tritium handling at the Hall A Target Facility. It covers various aspects such as tritium containment, procedures development, access control, truck ramp protocols, and controlled access procedures. Detailed instructio
1 views • 45 slides