Batching Techniques for Accumulators: Applications to IOPs and Blockchains
This presentation discusses batching techniques for accumulators in the context of IOPs and blockchains. It covers challenges with UTXO sets, Merkle trees, and RSA accumulators, proposing solutions and improvements. The content explores problems with Merkle trees, benefits of RSA accumulators, and e
0 views • 27 slides
Road Safety Audit and Inspection Concepts
Road Safety Audit (RSA) and Road Safety Inspection (RSI) play important roles in evaluating and improving road safety infrastructure. While RSA focuses on new road design and construction, RSI assesses existing roads periodically. This article discusses the differences between RSA and RSI, their pro
0 views • 32 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
4 views • 37 slides
Role of Constitution and Rules in Union Functionality: Speech by T.O. Ogunseye Esq
Constitution plays a crucial role in governing the affairs of a union like ASUP, ensuring rights protection, disciplinary actions, financial accountability, and more. The ASUP Constitution outlines objectives, member rights, disciplinary measures, subscription rules, election guidelines, and educati
0 views • 12 slides
Indian Constitution and Human Rights: A Comprehensive Overview
The Indian constitution embodies justice in social, economic, and political spheres, aiming for the full development of every individual. Rooted in democratic principles and socialism, the preamble emphasizes liberty, equality, and justice. Drawing wisdom from leaders like Dr. Ambedkar and Mahatma G
0 views • 10 slides
Constitution Day: History and Significance of September 17, 1787
Celebrate Constitution Day by learning about the signing of the United States Constitution on September 17, 1787. Discover the 39 delegates who signed the Constitution, the principles it upholds, and the seven articles that form the foundation of the American government.
2 views • 17 slides
Constitution of France: Salient Features of the Fifth Republic
The Constitution of France, in operation since 1958, aimed to bring stability after years of constitutional changes. It is rigid with complex amendment processes. France has a unitary constitution, a bicameral legislature, and a mix of presidential and parliamentary systems. The 5th Republic Constit
1 views • 25 slides
Key Features of the Constitution of India
The Constitution of India is the longest written constitution in the world, combining various constitutional features from different countries. It emphasizes popular sovereignty, parliamentary form of government, and special provisions for regional diversity. The document reflects a commitment to de
3 views • 5 slides
Features of China's 1982 Constitution
The 1982 Constitution of China, drafted after extensive discussions, adheres to socialist principles and emphasizes the socialist system as the foundation of the state. With a total of 138 Articles, it is a flexible document allowing for easy amendments and maintains a unitary system with centralize
2 views • 13 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Overview of United States Constitution Articles
The United States Constitution consists of several articles outlining the separation of powers among the branches of government. It establishes the legislative, executive, and judicial branches as well as the procedures for amending the Constitution and recognizing state laws.
0 views • 13 slides
Evolution of the Texas Constitution: From Independence to Modern Principles
Explore the journey of the Texas Constitution from the roots of rebellion and the Declaration of Independence to the principles outlined in the modern constitution. Learn about key events, changes in governance, and the process of amending the constitution over time.
0 views • 24 slides
Evolution of Somalia's Constitution: 1949-2012
The journey of Somalia's constitution from 1949 to 2012 is depicted through significant events such as the establishment of the military forces, involvement with Italy, and the formation of political and academic committees. Key figures and committees played vital roles in shaping the constitution d
0 views • 21 slides
Foundations of Georgia's Government and Constitution Structure
Explore the foundations of Georgia's government, including the structure of its state constitution, preamble, bill of rights, articles, and amendments. Learn about the relationship between the Georgia state constitution and the United States Constitution, and delve into the principles and intentions
0 views • 51 slides
Freedom of Speech Regulation in the Constitution of the Republic of Poland
The Constitution of the Republic of Poland guarantees freedom of speech and expression, ensuring the rights of individuals to hold opinions, seek, receive, and share information across various media. International agreements and laws further protect these rights, emphasizing the importance of respec
0 views • 7 slides
The Indian Federal System
The Indian federal system as defined by the Constitution of India establishes a unique structure where power is divided between the central government and the states. This system features characteristics such as governments at two levels, division of power, a written constitution, independent judici
2 views • 19 slides
Republic of South Africa (RSA): COSO Components 2 & 3 with 3 Lines of Defence Approach
The presentation delves into RSA's approach to the COSO components, focusing on Risk Assessment and Internal Controls. It discusses the legislative mandate, Treasury regulations, and the COSO Internal Control Integrated Framework. The Risk Assessment section covers levels, matrices, and key instrume
0 views • 13 slides
Amendment Process in the Indian Constitution: Overview and Procedure
Amending the Indian Constitution is a crucial process outlined in Article 368. It is designed to maintain the sanctity of the Constitution and prevent arbitrary power. The process involves introducing a Bill, passing it with required majorities in both Houses of Parliament, ratifying by state legisl
2 views • 7 slides
The Role of Education in South Africa's Constitution and Curriculum
The South African Constitution guarantees the right to education, including adult basic education and further education. The Revised National Curriculum Statement (RNCS) aligns with the Constitution, emphasizing social justice, human rights, and inclusivity. The curriculum aims to provide a learner-
0 views • 13 slides
RSA Algorithm in Public-Key Cryptography
The RSA algorithm is a crucial public key cryptography method used for key exchange, digital signatures, and data encryption. It involves generating public-private key pairs using prime numbers, encryption with the public key, and decryption with the private key. The algorithm's strength lies in the
0 views • 5 slides
The Signing of the United States Constitution in 1787
A group of men gathered at the Constitutional Convention in 1787 in Philadelphia to draft a constitution for the newly formed United States. Led by George Washington, they discussed, argued, and made key decisions in secret meetings. James Madison meticulously recorded the discussions while Benjamin
1 views • 17 slides
The Constitutional Convention of 1787 and the Birth of the American Constitution
The Constitutional Convention of 1787 was convened to address the weaknesses of the Articles of Confederation and create a stronger central government. Delegates like George Washington, James Madison, and Alexander Hamilton played key roles in drafting the Constitution, which required ratification b
0 views • 5 slides
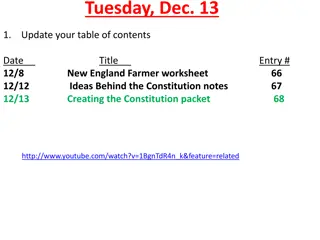
Analyzing the Creation of the Constitution
Delve into the historical events surrounding the formation of the United States Constitution through detailed notes, worksheets, and guided reading sections. Explore the key ideas behind the Constitution, the roles of various plans like the Virginia and New Jersey Plans, and the individuals involved
0 views • 22 slides
Celebrate Constitution Day: A Brief History of the U.S. Constitution
Learn about the significance of Constitution Day on September 17th and the journey that led to the creation of the U.S. Constitution. From the challenges posed by the Articles of Confederation to the final signing of the Constitution, delve into the key events and figures that shaped the foundation
0 views • 8 slides
Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
The Importance of a Constitution in Government
Exploring the significance of a constitution in governance, this content delves into the definition, origins, and key features of the UK constitution. It highlights the need for a constitution to establish rules for government institutions, regulate their relationships, define civil liberties, and p
0 views • 21 slides
A Comparison of US and Georgia Constitutions
A comparison between the US Constitution and the Georgia Constitution highlighting their preambles, articles, and amendment processes. The preamble of each constitution expresses the foundational values and goals of the people. The US Constitution outlines its legislative, executive, and judicial br
0 views • 7 slides
Overview of the Federal Structure in the Constitution of India
The Constitution of India showcases a quasi-federal system with a strong centralizing tendency, as discussed by scholars like Kenneth C. Wheare, Sir Ivor Jennings, and Dr. B. R. Ambedkar. The essential features of a federal constitution, such as division of power, supremacy of law, and distribution
0 views • 4 slides
The Evolution of the U.S. Constitution: From Jefferson and Madison to Amendment Processes
Jefferson and Madison held differing views on amending the Constitution, highlighting the balance between adaptability and stability. Despite enduring challenges like slavery, the Constitution remains the oldest written constitution. The rigorous amendment process, outlined in Article V, reflects th
0 views • 10 slides
Structure of the U.S. Constitution
The U.S. Constitution is divided into three main parts: the Preamble, the seven Articles that explain the government's plan, and the 27 Amendments which are written changes to the Constitution. The Preamble lists the goals of the Constitution, the Articles detail the powers and responsibilities of e
0 views • 37 slides
Study Guide: U.S. Constitution Flash Cards for Test Success
Explore flashcards covering key facts about the U.S. Constitution, including details about the Declaration of Independence, the Constitutional Convention, major political parties, the Preamble, goals of the Constitution, branches of government, and more. These visual aids will help you ace your test
0 views • 103 slides
Prime Numbers and RSA Algorithm in Cryptography
Delve into the world of prime numbers and the RSA algorithm in cryptography. Learn about key generation, Bertrand's Postulate, the Miller-Rabin test for primality, and the Almost Miller-Rabin test. Discover how these concepts are crucial in ensuring secure communication and data encryption.
0 views • 20 slides
RSA Algorithm - An Overview
Cryptography is the science of writing in secret code to protect information. The RSA algorithm, introduced by Rivest, Shamir, and Adleman in 1978, is a popular public key system. It involves the exchange of secure messages between senders and receivers to avoid code breaking. This algorithm uses bo
1 views • 31 slides
RSA Public-key Cryptography in Data Encryption
Exploring the foundational concepts of RSA public-key cryptography and its applications in data encryption. Learn how messages can be encoded, transmitted securely, and decoded using encryption and decryption functions. Discover the significance of picking large primes and understanding the bijectio
1 views • 12 slides
RSA Encryption for Secure Communication
Encryption plays a vital role in securing information, and RSA encryption, developed by Rivest, Shamir, and Adleman in 1977, uses public and private keys to safeguard data. Learn about the process, challenges with other encryption methods, prime numbers, and how RSA encryption works step by step.
0 views • 24 slides
Evaluation of Ed25519 Cryptography Performance in DNSSEC Validation
Edwards Curve Cryptography, specifically the Ed25519 algorithm, offers faster performance and high crypto density compared to other algorithms. This evaluation study compares key sizes, processing times, and validation support for Ed25519, ECDSA P-256, RSA-2048, and RSA-4096 in DNSSEC validation sce
0 views • 19 slides
Research Assessment Trends in RSA and Lesotho: Issues, Challenges, and Forward Strategies
Research assessment in RSA and Lesotho involves evaluating research quality, measuring inputs, outputs, and impacts using both qualitative and quantitative methodologies. The prevailing practices include assessing research productivity for progression and utilizing various assessment mechanisms to e
0 views • 7 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Cryptology System Design Fundamentals - RSA Public Key System Analysis
The RSA public key system analysis involves determining suitable public and secret keys for users A and B, calculating distinct possible public keys, decrypting cryptograms, generating digital signatures, and discussing data ranges for secure communication. The solution covers the key generation pro
0 views • 16 slides
Muddiest Point: Questions on RSA, DDoS Attacks, and Block Cipher Algorithms
In this collection of images, various concepts related to RSA encryption, DDoS attacks, block cipher algorithms like DES and AES, TCP protocols, and real-life applications of cryptography are explored. The images cover topics such as the Mirai-infected devices used in a DDoS attack on Dyn, differenc
0 views • 14 slides