Public key encryption, Digital signature and authentication
Understand the concept of public key encryption, asymmetric encryption, and the widely used RSA algorithm. Explore how public key cryptography revolutionized the field of encryption and its applications in confidentiality, authentication, and key distribution.
4 views • 12 slides
Cooperative Governance and Urban Planning in Gauteng: Support to Municipal Public Accounts Committees
The Department of Cooperative Governance, Urban Planning, and Traditional Affairs (COGTA) in Gauteng provides support to Municipal Public Accounts Committees (MPACs) for clean audits, anti-corruption measures, and more. Upholding the RSA Constitution, the department aims to drive effective cooperati
0 views • 52 slides
Information Security – Theory vs. Reality
Exploring the concept of fault attacks in hardware security, this lecture delves into the various techniques used to compromise systems through non-nominal and nominal channels, as well as the potential risks introduced by trojan horses in the IT supply chain. The discussion includes differential fa
2 views • 37 slides
Batching Techniques for Accumulators: Applications to IOPs and Blockchains
This presentation discusses batching techniques for accumulators in the context of IOPs and blockchains. It covers challenges with UTXO sets, Merkle trees, and RSA accumulators, proposing solutions and improvements. The content explores problems with Merkle trees, benefits of RSA accumulators, and e
0 views • 27 slides
Empowering New Hampshire's Electricity Market Through Community Power
Empowerment of the electricity market in New Hampshire is highlighted through community power initiatives that aim to redesign governance, promote competitive retail markets, and enhance the role of distributed energy resources. The RSA 374:F of 1996 underlines the importance of competitive markets
4 views • 13 slides
Enhancing State Capacity Building in Education
Co-funded by OSEP and RSA, NTACT:C.NCSRC focuses on providing intensive technical assistance to states while engaging in strategic planning and action steps. With a wide range of resources and tools, virtual and in-person trainings, the center supports effective practices, data analysis, collaborati
0 views • 41 slides
Massey Ferguson MF 374 AQ CAB TRACTOR Parts Catalogue Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 27 slides
Massey Ferguson MF 374 S TRACTOR, - 300993 Parts Catalogue Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 28 slides
Massey Ferguson MF 374 VQ CAB TRACTOR, - 0295 Parts Catalogue Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 27 slides
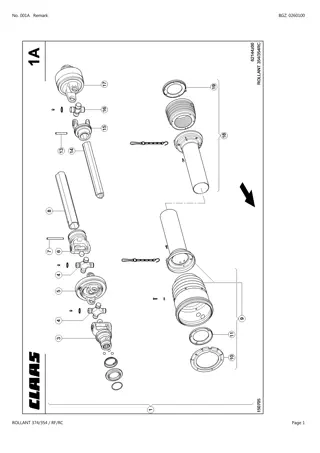
CLAAS ROLLANT 374 354 RF RC Baler Parts Catalogue Manual Instant Download (SN 76300011-76399999)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
Understanding Road Safety Audit and Inspection Concepts
Road Safety Audit (RSA) and Road Safety Inspection (RSI) play important roles in evaluating and improving road safety infrastructure. While RSA focuses on new road design and construction, RSI assesses existing roads periodically. This article discusses the differences between RSA and RSI, their pro
0 views • 32 slides
Introduction to Linux Shell for CSE 374 Course
Explore the Linux shell basics in CSE 374 course, covering topics like using Bash shell, executing commands, connecting to remote Linux servers, and interaction basics such as navigating command history. Get ready to dive into text-based interfaces and command-line operations in a Unix environment.
0 views • 14 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
2 views • 37 slides
Introduction to Computer Security and Number Theory
Explore the fundamental concepts of computer security, public key encryption, RSA encryption, and modular arithmetic in number theory. Understand properties of the modulo operator and learn how modular arithmetic exhibits specific mathematical properties.
0 views • 55 slides
Secure State Migration in the Data Plane Overview
The data plane synchronization protocol for secure state migration addresses the challenges of untrusted networks, ensuring completeness, low overhead, and integrity guarantee. P4Sync offers a solution by running in the data plane with minimal local control plane involvement, ensuring completeness,
2 views • 21 slides
Intermediate Concepts in C++ Inheritance - Lecture Participation Poll #24
Explore the advanced topic of C++ inheritance through Lecture Participation Poll #24 in CSE 374. Dive into the concepts with examples and code snippets covering class inheritance, virtual functions, and more. Don't miss out on this opportunity to enhance your understanding of intermediate programmin
0 views • 31 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Republic of South Africa (RSA): COSO Components 2 & 3 with 3 Lines of Defence Approach
The presentation delves into RSA's approach to the COSO components, focusing on Risk Assessment and Internal Controls. It discusses the legislative mandate, Treasury regulations, and the COSO Internal Control Integrated Framework. The Risk Assessment section covers levels, matrices, and key instrume
0 views • 13 slides
Exploring Cloud Cryptography for Secure Data Processing
Cloud cryptography is a vital aspect of data security in cloud computing, allowing data to be encrypted and processed securely. This presentation delves into the concepts of cloud cryptography, homomorphic encryption, and the two types of homomorphic encryption - hybrid and partial. It discusses the
8 views • 17 slides
Performance of Post-Quantum Signatures: Analysis and Comparison
Explore the performance and characteristics of various post-quantum signature schemes including Lattice-based Dilithium, QTesla, Falcon, Symmetric Sphincs+, Picnic, Multivariate GEMSS, Rainbow, and more. Understand the implications of using these schemes in TLS, code signing, firmware updates, signe
0 views • 29 slides
RSA Algorithm in Public-Key Cryptography
The RSA algorithm is a crucial public key cryptography method used for key exchange, digital signatures, and data encryption. It involves generating public-private key pairs using prime numbers, encryption with the public key, and decryption with the private key. The algorithm's strength lies in the
0 views • 5 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
Introduction to Cryptography and Its Applications in Computer Science
Cryptography is the study of methods for sending and receiving secret messages. In this lecture, we explore the design and application of cryptosystems, such as the RSA cryptosystem and Turing's Code. The goal is to securely encrypt and decrypt messages using number theory to protect communication f
1 views • 53 slides
Cryptography Concepts and Encryption Methods Overview
Exploring elementary cryptography concepts such as encryption, cryptanalysis, symmetric and asymmetric encryption algorithms like DES, AES, and RSA. Delve into key exchange protocols, digital signatures, cryptographic hash functions, and the process of encryption and decryption in a cryptosystem.
0 views • 23 slides
Exploring Long-Term Employment Outcomes of Vocational Rehabilitation Applicants
This study utilized linked administrative data to examine the outcomes of Vocational Rehabilitation (VR) applicants up to 7 years after program exit. Findings showed varied outcomes based on employment status at closure, with better results for those who closed with employment. The research linked R
0 views • 20 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computing utilizes the principles of quantum mechanics to process information exponentially faster than classical computers. This advancement poses a significant threat to current cryptographic systems, especially those reliant on factors like RSA and Diffie-Hellman key exchange. If large-sc
0 views • 25 slides
Understanding Prime Numbers and RSA Algorithm in Cryptography
Delve into the world of prime numbers and the RSA algorithm in cryptography. Learn about key generation, Bertrand's Postulate, the Miller-Rabin test for primality, and the Almost Miller-Rabin test. Discover how these concepts are crucial in ensuring secure communication and data encryption.
0 views • 20 slides
Key Exchange and Public-Key Cryptography Overview
Explore the challenges of key management, the use of trusted third parties in generating shared keys, the limitations of toy protocols in secure key exchange, and the evolution of public-key cryptography techniques like Merkle Puzzles, Diffie-Hellman, and RSA. Learn how to achieve secure key exchang
0 views • 36 slides
Understanding the RSA Algorithm - An Overview
Cryptography is the science of writing in secret code to protect information. The RSA algorithm, introduced by Rivest, Shamir, and Adleman in 1978, is a popular public key system. It involves the exchange of secure messages between senders and receivers to avoid code breaking. This algorithm uses bo
1 views • 31 slides
Marriage and Divorce Registration in RSA: Practices and Strategies
South Africa's marriage registration system has evolved post-1994 to align with democratic values, social justice, and human rights. The legal framework encompasses various acts and regulations, ensuring proper registration processes for both traditional and civil marriages. Strategies are in place
0 views • 10 slides
Understanding RSA Public-key Cryptography in Data Encryption
Exploring the foundational concepts of RSA public-key cryptography and its applications in data encryption. Learn how messages can be encoded, transmitted securely, and decoded using encryption and decryption functions. Discover the significance of picking large primes and understanding the bijectio
1 views • 12 slides
Understanding RSA Encryption for Secure Communication
Encryption plays a vital role in securing information, and RSA encryption, developed by Rivest, Shamir, and Adleman in 1977, uses public and private keys to safeguard data. Learn about the process, challenges with other encryption methods, prime numbers, and how RSA encryption works step by step.
0 views • 24 slides
Evaluation of Ed25519 Cryptography Performance in DNSSEC Validation
Edwards Curve Cryptography, specifically the Ed25519 algorithm, offers faster performance and high crypto density compared to other algorithms. This evaluation study compares key sizes, processing times, and validation support for Ed25519, ECDSA P-256, RSA-2048, and RSA-4096 in DNSSEC validation sce
0 views • 19 slides
Research Assessment Trends in RSA and Lesotho: Issues, Challenges, and Forward Strategies
Research assessment in RSA and Lesotho involves evaluating research quality, measuring inputs, outputs, and impacts using both qualitative and quantitative methodologies. The prevailing practices include assessing research productivity for progression and utilizing various assessment mechanisms to e
0 views • 7 slides
Legal Liability of Individuals in Corporate Entities
Explore the individual liability implications in claims against corporate entities, including insights on limited liability companies, dissolved LLCs, preincorporation transactions under the NH Business Corporation Act, and shareholder liability under RSA 293-A. Understand the concept of hostile wor
0 views • 23 slides
Intermediate Bash Scripting for Efficient Command Line Operations
Explore advanced Bash scripting techniques, including file redirection, file transfer methods, and script writing practices. Learn how to compress files, transfer data between local and remote hosts, and create executable Bash scripts for automated tasks in CSE 374.
0 views • 16 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Cryptology System Design Fundamentals - RSA Public Key System Analysis
The RSA public key system analysis involves determining suitable public and secret keys for users A and B, calculating distinct possible public keys, decrypting cryptograms, generating digital signatures, and discussing data ranges for secure communication. The solution covers the key generation pro
0 views • 16 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides