Rescue Drone: Increasing Autonomy and Implementing Computer Vision
Focuses on developing a rescue drone with increased autonomy and implementing computer vision for advanced object detection. The team, consisting of Cody Campbell (Hardware Engineer), Alexandra Borgesen (Computer Engineer), Halil Yonter (Team Leader), Shawn Cho (Software Engineer), Peter Burchell (M
78 views • 44 slides
The Top 10 Signs Your Router May Have Been Hacked
Explore the 10 unmistakable signs indicating your router's security might have been compromised. Learn how to identify potential breaches and safeguard your network from cyber threats.\n
4 views • 1 slides
Understanding Management, Leadership, and Organizational Success
The process of achieving organizational objectives through effective management and leadership is crucial for success. Management roles, such as top management, middle management, and supervisory management, each play a distinct role in implementing strategic plans and motivating employees. Skills l
9 views • 26 slides
FACILITY MANAGEMENT & SAFETY
Facility management and safety are interlinked disciplines crucial for optimizing workflow and ensuring a safe environment in various facilities. This includes managing space, infrastructure, resources, and staff effectively. Specific focus on laboratory facility management involves maintaining qual
3 views • 19 slides
adonai software
Adonai college Management System is a cloud-based ERP System that delivers various College and School Management Systems, College and School Management Software, College and School Management System ERP, College and School Management Software System, Online College and School Management Software Sys
3 views • 1 slides
Strategic Infrastructure Asset Management Plan (SIAMP) Overview
Strategic Infrastructure Asset Management Plan (SIAMP) Module 6 focuses on portfolio management principles for effective infrastructure asset management. Portfolio managers are guided on planning, managing work portfolios, and collaborating with other delivery management modules. The SIAMP outlines
6 views • 32 slides
National Radioactive Waste Management Plan Overview
Briefing the Select Committee on Land Reform, Environment, Mineral Resources, and Energy about the South African Radioactive Waste Management Programme and the legislative background governing radioactive waste management. The presentation outlines the framework, guiding elements, waste management p
4 views • 19 slides
Evolution of Management Theories: Classical Approach and Scientific Management
Explore the evolution of management theories focusing on the Classical Approach and Scientific Management. The Classical Approach emphasizes efficiency and specialization, while Scientific Management introduced systematic methods to increase productivity. Learn about key figures like Frederick Winsl
6 views • 31 slides
Comprehensive Property Management Services in Waterbury, CT by Idoni Management
Explore the comprehensive property management services offered by Idoni Management in Waterbury, CT. Our expert team provides tailored solutions for property owners, including tenant screening, rent collection, property maintenance, financial reporting, and lease management. Discover why we are the
1 views • 10 slides
Virtual Router Market Share, Opportunities, Trend, Revenue, Growth 2017-2027
At a compound annual growth rate of 22.3%, the size of the worldwide Virtual Router market is projected to reach US$ 614.6 Million in 2027.
0 views • 5 slides
Dynamic Buffer Sizing using Passive Measurements from P4 Switches
This study explores the dynamic modification of router buffer sizes by leveraging passive measurements from P4 switches. By dynamically adjusting buffer sizes based on factors like the number of long flows, average round-trip time, queueing delays, and packet loss rates, network performance can be o
3 views • 14 slides
Introduction to Organizational Behavior: Management Theories and Practices
Explore the evolution of organizational behavior from early management theories to contemporary practices. Understand the historical foundations and relevance of management theory in shaping workplace dynamics. Delve into key concepts like Scientific Management, Administrative Management, Bureaucrat
1 views • 28 slides
EGC Facility Management Pvt. Ltd.: Delivering Excellence in Property Management Services
EGC Facility Management Pvt. Ltd. is a leading organization in India offering a comprehensive service bouquet including property and asset management, maintenance services, consultancy, energy management, office support, and more. With a strong ethical foundation and a focus on client satisfaction,
0 views • 20 slides
Waste Management Priorities in Solomon Islands
The presentation by Debra Kereseka at the PACWASTEPLUS Steering Committee Meeting highlighted key waste management priorities in the Solomon Islands. Topics covered include the management of different waste streams, challenges faced, and clarifications for the project management unit. Priorities inc
0 views • 7 slides
Understanding Computer Network Components
Computer network components, including NIC, switch, hub, router, and modem, play vital roles in setting up networks. NIC (Network Interface Card) connects computers, hubs distribute data to multiple devices, switches provide direct connections, and routers connect LAN to the internet. Each component
1 views • 13 slides
Understanding Router Routing Tables in Computer Networks
Router routing tables are crucial for directing packets to their destination networks. These tables contain information on directly connected and remote networks, as well as default routes. Routers use this information to determine the best path for packet forwarding based on network/next hop associ
0 views • 48 slides
Unleashing Router Processing Power: A Revolutionary Approach
Delve into the realm of router processing power optimization with Marat Radan and Isaac Keslassy as they propose tapping into unutilized resources. Explore the innovative concept of redirecting packets to alleviate congestion and maximize efficiency in network operations.
1 views • 29 slides
Understanding Low-Intensity DoS Attacks on BGP Infrastructure
Low-intensity Denial of Service (DoS) attacks present a new challenge in cyber warfare, blending in with regular traffic to target communication channels like HTTP, SMTP, and DNS. These attacks require multiple participating hosts to flood the target with useless packets, gradually overloading serve
0 views • 25 slides
Risk Management & MPTF Portfolio Analysis at Programme Level for UN Somalia
This session delves into the world of risk management and portfolio analysis at the programme/project level, specifically focusing on the Risk Management Unit of the United Nations Somalia. It covers enterprise risk management standards, planned risk management actions, the role of RMU, joint risk m
0 views • 30 slides
Implementation of ATN/AMHS in Asia-Pacific Region: Strategies and Progress
Explore the progressive initiatives in implementing ATN/AMHS in the Asia-Pacific region as outlined by the International Civil Aviation Organization. The strategic adoption, communication ground-to-ground strategies, ATN over OSI and ATN over IPS conclusions, dual-stack protocols integration, and th
0 views • 20 slides
Manuherikia Catchment Management Plan Overview
An overview of the Manuherikia Catchment Plan presented to the Manuherikia Reference Group, emphasizing a holistic and values-based approach to flow management. The plan includes a flow management proposal with three management zones and a four-tiered approach for each zone. Site management tiers an
0 views • 14 slides
Apache Traffic Control Update Highlights
Apache Traffic Control provides insights into recent changes and upcoming developments, including Traffic Router updates, DNSSEC implementation, monitoring changes, and roadmap fixes. Stay informed about the project's progress and future plans.
0 views • 8 slides
Design Solutions for Routing under Constraints by Alexander Nadel
Alexander Nadel from Intel presents design solutions for routing under constraints, addressing challenges in formalization, scalability, decision strategies, conflict analysis, and violation resolution in industrial router design. The approach involves problem formalization, SAT encoding, net restar
0 views • 42 slides
Island-Based Fisheries Management in the U.S. Caribbean Region
The management of fisheries in the U.S. Caribbean region is undergoing a shift towards island-based management rather than species-based. This transition involves steps such as developing environmental assessments, initiating NEPA processes, and drafting new island-based Fishery Management Plans (FM
0 views • 7 slides
Understanding Network Layer Concepts in Router Design Lecture
This content delves into the fundamental concepts of network layer functions in router design, including data forwarding, control plane operations, and route processing. It explains the analogy of the postal system to address and locate network endpoints, and emphasizes the importance of route looku
0 views • 27 slides
Understanding Network Management Processes in Computer Networks
Network management processes play a vital role in maintaining the efficiency and security of computer networks. This includes fault management, configuration management, accounting management, performance management, and security management. Syslog, a standard for computer message logging, is utiliz
0 views • 78 slides
Innovations in Software-Defined Network Computing
The presentation explores the evolution of routers in the early 2000s, the limitations of hardware routers, and the need for more flexible and extensible software routers. It discusses the concept of the Click modular router and its architecture, emphasizing the benefits of a modular design approach
0 views • 35 slides
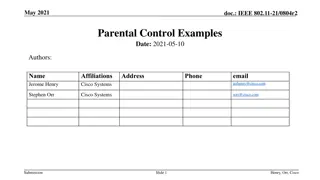
Parental Control Based on MAC Address in Wi-Fi Routers
The document discusses the implementation of parental control features based on MAC addresses in home-brand wireless routers and enterprise-class access points. It highlights real-world examples and market prevalence of this functionality, emphasizing its presence in various Wi-Fi router brands. The
0 views • 13 slides
Understanding Non-Optimal Routing and 32-Bit ASN Compatibility
Explore the challenges caused by the incompatibility of 32-bit ASN with old router software, leading to non-optimal routing issues. Learn about Autonomous Systems, AS Numbers, BGP asymmetric routing, and the importance of routing software supporting 32-bit ASN. Discover how outdated software replace
0 views • 8 slides
IT Infrastructure Updates and Deployments Overview
Deployment and upgrade progress of IT infrastructure at LBNL includes wireless network expansion, router replacements with 100G upgrade, 100G tapping evaluation for IDS, DTN deployment for data transfer automation, and video conferencing cart deployment. The updates range from network switches to ro
0 views • 7 slides
Overview of vRouter Implementation in Openstack Neutron
Virtual router (vRouter) is a crucial component in network virtualization, with applications in cloud environments like Openstack Neutron. This article delves into the concept of vRouter, its importance in IPv6 implementations, and the utilization of VM-based vRouters. It also explores the current s
0 views • 12 slides
Advanced Networking with Multiple Distributed Gateway Ports in OVN
Explores the latest advancements in networking technology with OVN by allowing the creation of multiple Distributed Gateway Ports per logical router. This feature enables connectivity to multiple external networks, supporting scenarios like shared services, NAT configurations, and load balancing. Di
0 views • 7 slides
Simplified Router Implementation for CSC458/2209 Course
You will be designing a simplified router for CSC458/2209 course with specific functionalities such as handling Ethernet frames, ICMP messages, ARP requests, IP packets, and more. The router will operate in an emulated network environment using Mininet and will need to route traffic between a client
0 views • 16 slides
Web Development Lecture Highlights & Tips
Explore key topics covered in a web development lecture, including routing, forms, API fetching, and web project assignments. Learn about bug fixes, stable code updates, React 16 features, layout design considerations, React Router philosophy, and various routing mechanisms. Enhance your understandi
0 views • 25 slides
Non-Interactive Anonymous Router with Quasi-Linear Computation
Explore the concept of a Non-Interactive Anonymous Router with Quasi-Linear Computation, Receiver Insider Protection (RIP), Sender Insider Protection (SIP), and Multi-Client Functional Encryption. The comparison of anonymity notions in NIAR and the motivation behind the non-interactive anonymous shu
0 views • 29 slides
Enhancing Tor Network Security and Performance with Tunable Path Selection
This presentation discusses the improvement of security and performance within the Tor network through tunable path selection. It covers Tor's design, proposed methods for bandwidth measurement, router selection algorithms, and the evaluation of different strategies to enhance the network's efficien
0 views • 29 slides
Innovative NoX Router: Transforming Low-Latency Router Techniques
Discover the groundbreaking NoX Router developed by Mitchell Hayenga and Mikko Lipasti from the Department of ECE. This router introduces a non-speculative control technique, enhancing efficiency by encoding and controlling traffic with XOR properties. By eliminating arbitration latency and dead cyc
0 views • 21 slides
Management Interventions' Long-Term Impact in Indian Firms
This study examines the lasting effects of management interventions in Indian textile firms over an 8-year period, revealing that while some improvements were reversed, treatment remained significant for management and performance. Factors like managerial turnover influenced the persistence of these
0 views • 38 slides
Understanding Router Design and Longest Prefix Matching in Computer Networks
Explore concepts like control plane processors, route lookup, and IP block reallocation in computer networking. Learn about the basics of forwarding tables, scheduling, and buffer management crucial for network operations. Dive into routing algorithms and data plane processing for efficient packet d
0 views • 39 slides
Network Configuration Complexity and Verification Tools
The content discusses the challenges of managing complex router configurations involving multiple routing protocols, metrics, and filters. It highlights the importance of using network verification tools to proactively detect errors and policy violations. Various tools such as Tiramisu, Minesweeper,
0 views • 26 slides