Modern Threat Modeling & Cloud Systems in OWASP Sacramento
Explore modern threat modeling techniques for cloud systems at OWASP Sacramento's June 2023 event. Agenda includes community topics and more. Membership at Granite City offers workspace perks and access to exclusive events. Learn about threat modeling history and methodologies like STRIDE and PASTA.
1 views • 14 slides
Comprehensive Review on Medical Separations and Direct Threat Assessments for Health Staff
This resource provides an extensive overview of medical separations and direct threat assessments relevant to Job Corps health and wellness staff and subcontractors. It covers topics such as the process of medical separations, reinstatement rights, disability accommodation, and when medical separati
1 views • 60 slides
India Alliance Clinical & Public Health fellowship in India
India Alliance Clinical & Public Health fellowship in India\n\nIndia Alliance Clinical and Public Health Research Fellowships are for Health researchers with an MD, MS, MPH, or an equivalent clinical or public health degree, who can apply for the DBT\/Wellcome Trust India Alliance Clinical and Publi
0 views • 5 slides
Introduction to Public Health Surveillance
Public health surveillance is essential in monitoring and analyzing health concerns that affect the entire nation. From infectious disease outbreaks to chronic illnesses and environmental disasters, public health aims to improve overall health and well-being. This presentation serves as an informati
0 views • 19 slides
Cyber Threat Detection and Network Security Strategies
Threat detection is crucial in analyzing security ecosystems to identify and neutralize malicious activities. Methods like leveraging threat intelligence, behavior analytics, setting intruder traps, and conducting threat hunts are essential for proactive security. Implementing security through obscu
1 views • 51 slides
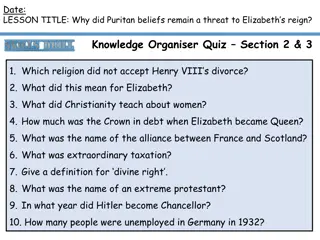
The Persistent Threat of Puritan Beliefs to Elizabeth's Reign
The Puritan belief system posed a significant threat to Queen Elizabeth I's reign, challenging the religious settlement she had put in place. Puritans disagreed with key aspects of the Church of England, such as the use of crucifixes and clergy vestments, leading to conflicts and resistance. Elizabe
0 views • 10 slides
Enhancing Public Health Workforce for COVID-19 Response Grant Program
This cooperative agreement aims to strengthen public health departments by expanding staff, hiring school nurses, and developing public health leaders. It includes major goals like creating a Public Health AmeriCorps and modernizing the public health workforce. The grant terms specify funding distri
1 views • 17 slides
Understanding Stereotype Threat and Teacher Response in Education
Stereotype Threat Theory explores the fear of confirming negative stereotypes and its impact on academic performance. Reduction of this threat can lead to improved learning outcomes. Teacher response plays a crucial role in shaping student writing, with various studies highlighting the importance of
0 views • 9 slides
Understanding Concepts in Public Health and Preventive Medicine
The evolution of nomenclature in public health, from hygiene to preventive medicine and social medicine, reflects the collective efforts to prevent disease, prolong life, and promote health. Key elements of modern public health include collective responsibility, state intervention, prevention emphas
0 views • 16 slides
Common Framework on Public Health Protection and Health Security in the UK
The Common Framework on Public Health Protection and Health Security in the UK is a structured approach towards ensuring health safety across geographical regions. Originating from EU regulations, the framework addresses infectious diseases, environmental hazards, and more. It involves collaboration
0 views • 5 slides
Induction Pack for New Registrars in Public Health - FPH August 2019
Welcome to the Specialty Training Scheme in Public Health! This induction pack introduces you to the Faculty of Public Health and outlines the key elements of the Training Programme. Learn about the strategic vision of FPH, membership benefits, and how to maximize effective public health action at d
3 views • 16 slides
Nursing Education in Public Health: A Collaborative Approach at Kent County Health Department
Joann Hoganson, MSN, RN, Director of Community Wellness at the Kent County Health Department, shares the importance of incorporating nursing students into public health initiatives. This collaboration benefits both the students and the agency by fostering professional commitment, recruiting exceptio
0 views • 9 slides
Behavioral Threat Assessment Tabletop Exercise - College First Year Analysis
Explore a comprehensive behavioral threat assessment tabletop exercise focused on analyzing a college first-year scenario. The exercise includes roles and responsibilities for players, facilitators, evaluators, and observers, guiding participants through phases to familiarize themselves with a stude
0 views • 19 slides
Understanding Cyber Threat Assessment and DBT Methodologies
Comprehensive information on methodologies and approaches useful for cyber threat assessment and Cyber DBT alongside classical DBT methodology as outlined in the NSS-10 document by S.K. Parulkar. The content discusses the importance of threat assessment, differences between physical and cyber threat
4 views • 17 slides
Challenges in Computer Systems Security
Understanding security in computer systems involves achieving goals in the presence of adversaries. However, this task is challenging due to the need to guarantee policies in the face of realistic and open-ended threat models. Issues can arise from problems with policy formulation, assumptions in th
0 views • 16 slides
Enhancing Incident Response Through Threat Intelligence
Explore the importance of threat intelligence in incident response, covering aspects such as understanding adversaries, assessing risks, evaluating threats, and leveraging strategic intelligence. Learn how organizations can benefit from a proactive approach to cybersecurity by utilizing threat intel
1 views • 18 slides
Understanding the Role of Public Health Practitioners in London's Workforce Development
Public Health Practitioners (PHPs) play a crucial role in implementing and delivering public health services, programs, and interventions. They focus on promoting health and wellbeing within communities, addressing health inequalities, and protecting the public from environmental hazards. Learn abou
0 views • 23 slides
Understanding Public Goods in Higher Education
This text delves into the concept of public goods in higher education, examining the distinctions between public and private forms, the economic and political dimensions, and the normative value of public goods. It discusses the economic definition of public goods, emphasizing their non-rivalrous an
1 views • 18 slides
Equity in Development Partners Support on Health Financing in Lao PDR P4H Meeting
The meeting focuses on addressing health indicators, inequities, and health financing challenges in Lao PDR. It analyzes the background of health indicators, inequities by socio-economic status and ethnic groups, and the current health financing situation in the country. The discussion delves into s
0 views • 23 slides
Comprehensive Training on Campus Threat Assessment Teams
Explore the advanced training curriculum developed by experts Marisa Randazzo, Ph.D., and Gene Deisinger, Ph.D., for Virginia Campus Threat Assessment Teams. The training covers areas like threat assessment processes, case management, legal updates, and challenges in team implementation. Participant
0 views • 92 slides
Mobile App Security Threat Modeling and Mitigation
Explore mobile app security threats, learn how to conduct threat modeling exercises, and implement mitigation strategies. Discover built-in security features, threat modeling technologies, and common threats like malware and code injection. Enhance your understanding of app security constraints and
0 views • 63 slides
Pennsylvania School Threat Assessment: Keeping Schools Safe
Pennsylvania schools have implemented a Threat Assessment Team to ensure the safety and security of students, staff, and community members. The team follows specific guidelines and procedures to assess and address threats, involving key stakeholders and promoting collaboration among multidisciplinar
0 views • 37 slides
Region IV Public Health Training Center Overview
The Region IV Public Health Training Center (PHTC) is dedicated to strengthening the competence of the public health workforce in HHS Region IV. It provides professional development opportunities for both current and future public health professionals through training programs, field placements, and
0 views • 33 slides
Understanding Stereotype Threat in Education
Stereotype threat is a phenomenon where individuals from marginalized groups experience anxiety due to negative stereotypes about their abilities. This can impact their performance and self-perception. Various groups, such as African-Americans, Latinos, females in STEM, elderly individuals, Roma, an
0 views • 42 slides
Threat Assessment Tabletop Exercise Overview
Conducting a tabletop exercise focused on threat assessment in a school setting. The exercise agenda includes welcome, introductions, exercise goals, objectives, participants' roles, exercise structure, and rules. The goals are to test preparedness for potential threats, coordinate plans effectively
0 views • 33 slides
Understanding Threat Modeling and Offensive Security
Threat modeling in offensive security involves determining potential threat scenarios that could compromise a system, understanding the system from an attacker's perspective, and devising defensive strategies. It helps confirm security implementations, identify gaps, monitor shortcomings, vulnerabil
0 views • 31 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Pennsylvania School Threat Assessment Procedures and Guidance
Ongoing concerns about school safety led to legislation in 2019, requiring schools in Pennsylvania to establish threat assessment teams. This presentation provides an overview of the statute, threat levels, team responsibilities, procedures, and resources for school staff, parents, and guardians to
0 views • 25 slides
Conducting Threat Assessments Through the Atrocity Prevention Lens
This module from the GLOBAL CENTRE FOR THE RESPONSIBILITY TO PROTECT focuses on conducting threat assessments through an atrocity prevention lens. It covers risk identification, situational awareness in field settings, information collection methods, addressing vulnerabilities of women and children,
0 views • 20 slides
Bomb Threat Preparedness Guidelines for Shifa International Hospital
The Shifa International Hospital emphasizes the importance of maintaining a secure environment for employees, patients, and visitors in the event of a bomb threat. This presentation covers the types of bomb threats, steps to follow in case of a bomb threat, and provides guidance on handling telephon
0 views • 14 slides
High School Students Behavioral Threat Assessment Tabletop Exercise Analysis
Conduct a tabletop exercise analyzing the behavioral threat assessment of two high school students. Explore roles and responsibilities, exercise itinerary, goal, and purpose to enhance threat assessment team preparedness and response. Utilize simulated scenarios to simulate real-world events for opt
0 views • 23 slides
Wisconsin Public Health Statutes Overview
Explore Wisconsin's public health history, statutes, and administrative rules, including the formation of the State Board of Health, consolidation of public health statutes in 1993, and the statutory duties of local boards of health. Learn about the chapters covering administration, communicable dis
0 views • 16 slides
Examining Stereotype Threat in Engineering Education
Exploring the experiences of female engineering students facing stereotype threat, this critical theoretical framework study sheds light on the challenges that impact their academic journey. Through narrative inquiry methodology, the research focuses on white female students to understand how stereo
0 views • 37 slides
Understanding Public Health Surveillance for Population Health
Public Health Surveillance is a vital process for systematically collecting, analyzing, and interpreting health data to inform public health practices. This crucial initiative, developed through the APTR in collaboration with the Brody School of Medicine at East Carolina University, focuses on enhan
0 views • 40 slides
Public Health Events in WHO Africa Region: Outbreaks Overview
Public health events in the WHO Africa Region pose a significant threat to global health security, with frequent outbreaks of diseases like Ebola, Yellow Fever, Polio, and cholera. In 2015, 105 public health events were reported, the majority being infectious diseases. Ongoing outbreaks in Angola, D
2 views • 30 slides
Scottish Public Health Observatory: Enhancing Health Information for Better Decision Making
The Scottish Public Health Observatory collaborates with NHS National Services Scotland to provide health information, intelligence, and statistical services supporting NHS in enhancing quality improvement in health care. They analyze national health data to improve population health and reduce heal
0 views • 16 slides
EU4Health Programme: Transforming Public Health in Europe
The EU's financial strategy and priorities in the health domain are highlighted through the EU4Health programme, aiming to enhance public health in Europe. The HaDEA is actively involved in improving health in the Union, protecting against cross-border health threats, ensuring availability of afford
0 views • 11 slides
School Safety and Threat Assessment Program Overview
Fact-based Threat Assessment for Safe and Supportive School Programs involves identifying, inquiring, assessing, and managing potentially dangerous situations. It aims to distinguish between those making threats and those posing real risks, without profiling or labeling individuals. Understanding th
0 views • 20 slides
Strengthening Strategic Partnerships for Public Health Intelligence
Promoting collaborative engagement between Public Health England (PHE) and local authorities is crucial for enhancing public health intelligence. PHE, as an arms-length body of the Department of Health, focuses on population health, prevention, and reducing health inequalities. Through initiatives l
0 views • 11 slides
Impact of Stereotypes on Perceived Facial Threat in Women Offenders
Facial expressions play a significant role in understanding emotions, but stereotypes can influence how people perceive facial affect. This study examines how reading tabloid articles about crimes committed by dark and light-skinned women offenders affects the perceived facial threat. Using a 2x2 fa
0 views • 9 slides