Adaptive Tree-based Convergecast Protocol
Adaptive tree-based protocol for managing overlay networks in heterogeneous networks. It proposes improvements to the existing Tree-Based Convergecast Routing (TBCR) protocol by considering additional parameters such as RTT, power consumption, link stability, and link mobility to optimize routing de
31 views • 12 slides
Case Studies on Successful Revenue Technology Implementations in Cargo Services (1)
In the fast-paced world of cargo services, optimizing pricing strategies remains a pivotal challenge for businesses aiming to boost profitability and maintain competitive advantage. Revenue technology, specifically tools that enable dynamic and cargo pricing, has revolutionized how companies approac
2 views • 5 slides
Understanding OSI Model and TCP/IP Protocol Suite
Explore the concept of layering in data communication, comparing the OSI model and TCP/IP protocol suite. Learn about protocol layers, protocol hierarchies, and the functionality of each layer in these models. Discover the interrelationships between layers and the evolution from OSI to TCP/IP.
5 views • 57 slides
London Homeless Coalition (LHC) Death Communication Protocol
In 2014, the Memorial Committee of the London Homeless Coalition (LHC) established the Death Communication Protocol to acknowledge, share, and address the loss of individuals experiencing homelessness. The protocol aims to inform partnering organizations of confirmed or unconfirmed deaths, support g
0 views • 12 slides
Understanding Mobile Computing and TCP/IP Protocol Suite
Mobile computing is crucial for continuous internet connectivity regardless of physical location. The TCP/IP protocol suite, consisting of Transmission Control Protocol (TCP) and Internet Protocol (IP), forms the backbone of internet infrastructure. IP addressing and mobility challenges are addresse
1 views • 51 slides
STM32WB BLE SW Application Sequencer Architecture Overview
The STM32WB BLE SW Application Sequencer is a specialized framework that optimizes while loop bare-metal implementations to avoid race conditions, especially in low power modes. It is not intended to compete with standard operating systems but rather with bare-metal implementations. The sequencer al
2 views • 14 slides
Understanding TCP/IP Protocol Software Interface in Client-Server Communication
Explore the loosely specified protocol software interface in TCP/IP for client-server communication. Delve into the advantages and disadvantages of the interface, allowing flexibility and diverse implementations while maintaining compatibility across various systems.
1 views • 20 slides
Understanding Synthetic Aperture Radar (SAR) Modes and Implementations
Explore the world of Synthetic Aperture Radar (SAR) through various modes and implementations, covering topics such as SAR coordinate systems, pulse compression, range-Doppler algorithms, Born approximation, SAR scene simulation, and more. Dive into the distinctions between unfocused SAR and focused
0 views • 18 slides
Understanding OSI Model and TCP/IP Protocol Suite in Computer Networking
This chapter explores the OSI model and TCP/IP protocol suite, delving into protocol layers, addressing mechanisms, and network components. It highlights the interface between layers, functions of each layer in the OSI model, and compares TCP/IP protocol suite layers with OSI model layers. The discu
0 views • 30 slides
MAAP Protocol Overview in IEEE 1722: Address Acquisition and Message Format
The MAAP (Multicast Address Acquisition Protocol) is defined in IEEE 1722 for time-sensitive applications in bridged local area networks. It involves acquiring multicast addresses through claiming, probing, and defending messages. MAAP enables dynamic allocation of addresses and defending against co
0 views • 8 slides
IEEE 802.11-20/1761r1 Ranging Protocol for 11bd
This document outlines the ranging protocol proposed for IEEE 802.11-20/1761r1, focusing on RTT-based ranging leveraging multi-channel operation. By integrating the 11az ranging protocol, it enables flexible and low-overhead application in 11bd for improved accuracy in ITS bands. The protocol includ
1 views • 13 slides
Understanding EIGRP: A Comprehensive Overview
Enhanced Interior Gateway Routing Protocol (EIGRP) is a dynamic routing protocol providing various advantages to network administrators. It is a classless routing protocol supporting VLSM and is considered an Interior Gateway Protocol (IGP). EIGRP uses advanced distance vector routing and is known f
1 views • 5 slides
Understanding SFTP Server Functionality with ACS 5.x by Mohammad Azharuddin AAA Team
SFTP (SSH File Transfer Protocol) is a secure network protocol for file access, transfer, and management over reliable data streams. It enhances security by extending the SSH protocol and can be implemented using a reliable 8-bit byte stream protocol. SFTP commands are sent as 4 ASCII letters follow
4 views • 23 slides
Enhanced Family Court Police Disclosure Protocol for 2024
The 2024 Family Court Police Disclosure Protocol addresses key issues identified in the 2013 protocol, emphasizing timely and proportionate requests for material. Changes include a new checklist for the judiciary, guidance notes, and revised processes for litigants in person. The protocol provides c
1 views • 19 slides
Understanding Priority Queues and Heap Data Structures
Priority queues play a key role in computer science algorithms by managing data based on priority levels. The use of heap data structures enhances the efficiency of priority queue operations. This tutorial covers the basics of priority queues, their applications, different implementations such as li
0 views • 30 slides
Priority Queues in Java: Implementation and Use Cases
Explore the concept of priority queues in Java, covering implementations using unsorted and sorted linked lists, as well as heaps. Learn about the differences between a queue and a priority queue through reading quizzes and discover various priority queue implementation options. Dive into priority q
1 views • 42 slides
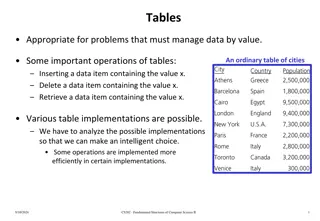
Implementations and Operations of Tables for Managing Data
An analysis of different table implementations for managing data by value, discussing operations like insertion, deletion, and retrieval. The post explores various linear and nonlinear implementations such as sorted arrays, linked lists, and binary search trees, highlighting the importance of select
0 views • 54 slides
Priority Queues: Operations and Implementations
Priority queues are data structures that allow efficient insertion, deletion, and retrieval of elements based on their priority. This information-rich content covers various aspects of priority queues, including ideal times, binomial queues, Dijkstra's algorithm for single-source shortest paths, and
0 views • 11 slides
Essential Elements of Clinical Trial Protocols
Understanding the key components of a clinical trial research protocol is essential for conducting successful studies. This includes identifying session objectives, discussing trial protocol contents, exploring observational study elements, and learning about reporting guidelines. Study objectives f
1 views • 25 slides
Understanding Priority Queues and Heaps in CSE 373 Lecture
Today's lecture in CSE 373 covers the Priority Queue Abstract Data Type (ADT), the properties of heaps, and their implementations. Key topics include the completeness property of heaps, different priority queue implementations such as the binary search tree for faster insert and find operations, and
0 views • 21 slides
Enhancing 3DIC Implementations with Mix-and-Match Die Stacking
This study by Kwangsoo Han, Andrew B. Kahng, and Jiajia Li delves into the improved performance of 3DIC implementations through the mix-and-match die stacking technique. By integrating slow and fast tiers, they aim to enhance parametric yield and optimize design-stage processes for a more efficient
0 views • 19 slides
Understanding Queues in Computer Science: Principles and Implementations
Explore the concept of queues in computer science, focusing on ordered collections of data following the FIFO principle. Learn about queue ADTs, implementations in Python, and delve into a simulation of a Printer Queue problem. Discover how to model printing tasks as random events and analyze the im
0 views • 15 slides
Understanding DNS Flag Day and EDNS: A Comprehensive Overview
DNS Flag Day marks a coordinated effort to remove workarounds in DNS implementations, impacting domains in various ccTLDs like .CL, .CZ, .SE, .NU, and .NZ. Enhanced DNS (EDNS) provides a mechanism for supporting new options, but issues arise from poor DNS implementations causing delays and hindering
0 views • 20 slides
Understanding ADT List Operations and Implementations
In this detailed content, you will learn about the specifications and operations involved in working with an ADT list. The structure, domain operations, and user instructions are clearly outlined for efficient implementation. The content also delves into the representation and implementation aspects
0 views • 30 slides
Efficient Snapshot Implementations in Distributed Systems
This content discusses various snapshot implementations in distributed systems, focusing on achieving faster and sub-linear snapshot complexity. It covers topics such as multi-writer registers, tree structures, polylogarithmic snapshots, and the challenges of ensuring consistency across processes. T
0 views • 16 slides
PacketGuardian: A Tool for Static Detection of Packet Injection Vulnerabilities
This research paper introduces PacketGuardian, an effective static analysis tool designed to evaluate the robustness of protocol implementations against packet injection attacks. This tool supports precise context, flow, field-sensitive taint analysis, implicit flow analysis, and employs a summary-b
0 views • 23 slides
Practical Implementations of Arithmetic Coding
Explore the practical implementations, advantages, and disadvantages of arithmetic coding in this informative guide. Learn about the basic algorithm, dynamic interval expansion, integer arithmetic coding, and methods to improve the speed of arithmetic coding. Dive deep into encoding algorithms, exam
0 views • 78 slides
Understanding Queues: Operations, Implementations, and Applications
Explore the world of queues, a fundamental data structure with operations like enqueue and dequeue, and implementations using arrays or linked lists. Dive into the applications of queues and their significance in various scenarios. Uncover the basics of queue operations and their practical implicati
0 views • 30 slides
Sync HotStuff: Practical Synchronous State Machine Replication
Sync HotStuff is a practical synchronous protocol that tolerates Byzantine replicas and handles weaker synchrony models. It overcomes issues of requiring a large number of rounds and lock-step execution. The protocol ensures safety by committing blocks and guarantees liveness by continuing to commit
0 views • 15 slides
AI-Based Compression and Understanding of Industrial Data (MPAI-CUI) - Company Performance Prediction Use Case
AI-based Compression and Understanding of Industrial Data (MPAI-CUI) is a standard developed by the MPEG standards group. This standard focuses on transforming data into a more suitable format for applications. The presentation will cover the introduction to MPAI, applications, a demo for anonymous
0 views • 25 slides
Understanding ADTs: Lists, Stacks, and Queues - Implementation and Operations
Explore the world of Abstract Data Types (ADTs) - Lists, Stacks, and Queues, focusing on their operations like adding, removing, and accessing elements. Learn the differences between array and linked list implementations, along with insights on how to manipulate data structure implementations. Dive
0 views • 18 slides
High Performance User-Level Sockets over Gigabit Ethernet
Presentation overview of the design challenges, performance enhancement techniques, and results related to implementing high-performance user-level sockets over Gigabit Ethernet networks. The background and motivation discuss the limitations of traditional kernel-based implementations and the need f
1 views • 34 slides
Overview of HERDOS TES and SNiPER TES
HERDOS TES and SNiPER TES are discussed in detail, outlining their implementations and distinctive features. The discussion includes insights on TES requirements, concrete implementations, DataBuffer usage, HERD TES reliance on podio, and the migration plan to podio
0 views • 10 slides
Understanding Protocol Deviations in Clinical Trials
Protocol deviations are expected occurrences in clinical trials that may arise from site or participant actions. It is crucial for research teams to identify, report, and learn from these deviations to ensure the integrity and safety of the study. Mechanisms for identifying and reporting deviations,
0 views • 16 slides
Understanding OSI Model and TCP/IP Protocol Suite in Computer Networking
This content delves into the OSI model and TCP/IP protocol suite, highlighting the protocol layers, addressing mechanisms, and communication scenarios. It explores the functions of each layer, the interface between layers, and compares the TCP/IP layers with the OSI model. Through examples and illus
0 views • 46 slides
Exploring Web Services at IRIS: Implementations and Coordination
Discover the world of web services at IRIS through a detailed exploration of implementations, international coordination efforts, and the team behind these endeavors. Learn about the definition of web services, practical examples, and the various data and processing services offered by IRIS to suppo
0 views • 24 slides
Understanding Noise*: A Verified Secure Channel Protocol Library
Explore Noise*, a library of high-performance secure channel protocol implementations that have been verified for correctness. The Noise protocol examples, such as IKpsk2, showcase key exchange patterns used in applications like WhatsApp and Wireguard VPN. Discover the importance of verified impleme
0 views • 18 slides
Coverage-Directed Differential Testing of JVM Implementations
The paper discusses the importance of coverage-directed differential testing for Java Virtual Machine (JVM) implementations. It covers challenges in identifying JVM defects, solutions using test oracles, and examples of JVM behavior discrepancies. The study emphasizes the need for obtaining test cla
0 views • 45 slides
Seeking a General-Purpose CCSDS Link Layer Protocol: Next-Generation Data Link Protocol (NGDLP)
This document discusses the proposed Universal Frame Format for a next-generation data link protocol, focusing on major questions about transfer frames, Protocol Link Transmission Unit (PLTU), and Universal Transfer Frame Structure. It explores topics such as frame formats, telemetry transfer frames
0 views • 24 slides
NT Awake Proning Protocol for Non-Intubated Patients
This protocol outlines the benefits and procedure for prone positioning in non-intubated patients experiencing mild to moderate hypoxemia. It highlights patient eligibility criteria, equipment required, and considerations for nursing care. The protocol emphasizes improving oxygenation by promoting a
0 views • 11 slides