Mastering Subnetting: A Comprehensive Overview
Delve into the world of subnetting with Tengku Khairil Ahsyar's course outline covering IP address conversion, subnet mask calculation, and more. Learn about binary, octal, decimal, and hexadecimal number systems along with conversion techniques. Understand the significance of subnetting for efficie
1 views • 25 slides
Medical Terminology Health Science 20
Medical terminology is a specialized language used in healthcare to describe medical concepts concisely. It consists of prefixes, root words, and suffixes, which can be broken down to define complex terms. Utilizing proper medical terminology enhances communication among healthcare professionals and
3 views • 16 slides
Caterpillar Cat 336D2 and 336D2 L Excavator (Prefix FAR) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 30 slides
Caterpillar Cat 12H NA Motor Grader (Prefix 2WR) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 33 slides
Caterpillar Cat 120G MOTOR GRADER (Prefix 87V) Service Repair Manual Instant Download 1
Please open the website below to get the complete manual\n\n\/\/
0 views • 31 slides
Caterpillar Cat 120G Motor Grader (Prefix 87V) Service Repair Manual Instant Download 3
Please open the website below to get the complete manual\n\n\/\/
0 views • 29 slides
Caterpillar Cat 120G MOTOR GRADER (Prefix 87V) Service Repair Manual Instant Download 11
Please open the website below to get the complete manual\n\n\/\/
0 views • 27 slides
Caterpillar Cat 120G MOTOR GRADER (Prefix 87V) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 28 slides
Caterpillar Cat 120M Motor Grader (Prefix D9W) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 30 slides
Caterpillar Cat 120M Motor Grader (Prefix R9A) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 29 slides
Caterpillar Cat 120M Motor Grader (Prefix R9C) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 30 slides
Caterpillar Cat 120M Series 2 Motor Grader (Prefix M9C) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 31 slides
Understanding Network Security Fundamentals and Common Web Application Attacks
Learn about the basics of network security, including common web application attacks such as Cross-Site Scripting (XSS), SQL Injection, and Session Hijacking. Explore important concepts like cookies, markup languages, and ways to enhance security to protect against cyber threats.
0 views • 11 slides
Understanding Network Security: Hijacking, Denial of Service, and IDS
This content delves into the concepts of spying and hijacking in network security, covering topics such as eavesdropping on packets, injecting packets into streams, denial of service attacks, and defense mechanisms like firewalls and IDS. It explores low-level attacks and defenses, including ARP cac
1 views • 81 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
Understanding Control Hijacking Attacks and Defenses
Control hijacking attacks pose a significant threat by allowing malicious actors to manipulate data and control flow within a system. This article explores common attack methods like stack smashing and heap spraying, along with defenses such as fixing bugs, implementing platform defenses, and markin
1 views • 36 slides
Enhancing Chapel Compiler with Interfaces and Semantic Changes
Explore the evolution of Chapel compiler with the integration of interfaces, semantic modifications, and improvements in error messages. Delve into the concepts of constrained generics, function call hijacking prevention, and the impact on compiler efficiency.
0 views • 30 slides
Introduction to Huffman Coding for Data Compression
Understand the principles of encoding in information systems through topics such as Binary, Morse Code, Prefix Property, Code Optimization, and Huffman Coding. Explore the efficient representation of symbols with varying frequencies using Huffman coding, ensuring a prefix-free code for data compress
0 views • 16 slides
Exploring Words with the Prefix "bi-" for Children
This educational content focuses on introducing and understanding the prefix "bi-" meaning two. Children are encouraged to think of words starting with "bi-" and create new words by adding the prefix to existing ones. The lesson includes interactive activities, spelling exercises, and independent ta
0 views • 7 slides
IPv6 Networking Considerations in xDSL Networks
Practical insights and challenges in implementing IPv6 networking in xDSL networks, discussing rotating prefixes, privacy implications, management of multiple prefixes, prefix size considerations, and strategies for DHCP and L2TP termination. The content also covers security measures, prefix rotatio
0 views • 11 slides
Summary of MAC Address Policy Contribution to IEEE 802.11
This document outlines the contribution of MAC address policy to IEEE 802.11, focusing on defining ANQP and Beacon elements to convey information about addressing types supported by the network. It details how specific bits in the ANQP element represent support for various MAC address types includin
0 views • 5 slides
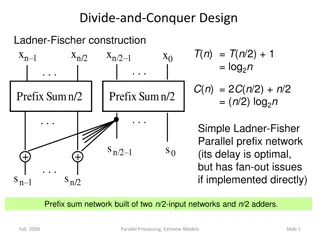
Parallel Prefix Networks in Divide-and-Conquer Algorithms
Explore the construction and comparisons of various parallel prefix networks in divide-and-conquer algorithms, such as Ladner-Fischer, Brent-Kung, and Kogge-Stone. These networks optimize computation efficiency through parallel processing, showcasing different levels of latency, cell complexity, and
1 views • 21 slides
Web Security Threats and Vulnerabilities: An Overview
Understanding the risks associated with web security, including issues like IP hijacking, cache poisoning, and transparent proxies. Explore how existing approaches fall short in protecting against malicious attacks and potential exploits, with observed vulnerabilities highlighting the importance of
0 views • 17 slides
Enhancing Interdomain Routing Security with RPKI
This content explores the deployment and security aspects of Resource Public Key Infrastructure (RPKI), a system that maps IP prefixes to their owning organizations to prevent prefix/subprefix hijacks. It delves into prefix and subprefix hijacking scenarios, certifying ownership with RPKI, and how R
0 views • 29 slides
Unit Testing Legacy Code: Hijacking Singletons for Testing
Enabling unit testing of legacy code requires making changes without altering existing calling code. Singleton pattern poses challenges for testing, but strategies such as hijacking can be employed for effective unit testing. David Benson shares insights on legacy code attributes and unit testing ap
0 views • 39 slides
Transparent and Efficient CFI Enforcement with Intel Processor Trace
This research discusses Control Flow Integrity (CFI) enforcement to combat control flow hijacking attacks. It explores methods for runtime CFI enforcement, including instrumented checking and transparent monitoring. The study delves into trace mechanisms, buffer management strategies, and when to tr
0 views • 32 slides
Understanding Cocaine's Neural Mechanism and Reward Learning Circuit
Cocaine affects the brain's reward circuit by blocking dopamine transporters, leading users to associate the drug with a rewarding feeling. Prolonged use can result in internalization of dopamine receptors. By hijacking reward-learning mechanisms, cocaine becomes one of the most harmful and addictiv
0 views • 13 slides
Understanding DLL Hijacking in Windows
Dynamic-Link Libraries (DLLs) are a mechanism in Windows for sharing code and data, making it easier to design and build applications. By loading DLLs either statically at compile time or dynamically at runtime, programs can enhance memory management and user experience. However, DLL hijacking, a co
0 views • 13 slides
Understanding Software Security Fundamentals
This review delves into essential concepts of software security, covering topics such as basic execution models, parameter areas, control flow hijacking, channeling vulnerabilities, buffer overflows, and format strings. It explores stack diagrams and analysis, elucidating critical mechanisms like co
0 views • 17 slides
RPKI Deployment and Security Overview
Explore the key concepts of RPKI deployment and security, including preventing prefix/subprefix hijacks, certifying ownership with RPKI, and how RPKI can prevent prefix hijacks. Learn about challenges in deployment and the importance of route origin validation. Understand the risks of insecure deplo
0 views • 24 slides
Evolved Addressing and Forwarding in Information-Centric Networks
The content discusses Evolved Addressing and Forwarding in Information-Centric Networks, focusing on an accountable Internet protocol (AIP) that addresses vulnerabilities at the IP level, such as source spoofing, DoS attacks, and route hijacking. AIP utilizes a hierarchy of self-certifying addresses
0 views • 16 slides
Understanding Network Security Fundamentals in Computer Networks
Explore the importance of network security in Computer Networks, focusing on key aspects like confidentiality, integrity, authentication, and non-repudiation. Learn about common threats, such as eavesdropping, impersonation, hijacking, and denial of service attacks, and the role of cryptography in e
0 views • 28 slides
Understanding Malware: Types, Risks, and Removal Methods
Explore the world of malware, including its various types and how it infiltrates systems. Discover the dangers it poses, such as data theft and system hijacking, and learn about manual removal techniques using tools like MBAM. Dive into hands-on labs to analyze, detect, and eliminate malware for a s
0 views • 15 slides
Understanding Control Hijacking Attacks in Computer Systems
Explore the concept of control hijacking attacks in computer systems, including buffer overflows, format string vulnerabilities, and use-after-free exploits. Learn about the attacker's goal, examples of attacks, and the importance of understanding C functions, the stack, and the heap. Delve into sys
0 views • 39 slides
Understanding Routing Issues in Information-Centric Networks
This section delves into the routing issues within Information-Centric Networks, highlighting vulnerabilities such as misconfigured routers, prefix hijacking, and impersonation. It emphasizes the importance of validating routes and proposes improvements to address security concerns associated with B
0 views • 15 slides
Comprehensive Guide on XSS Attacks and Defense Strategies
Explore the intricate details of Cross-Site Scripting attacks, the anatomy of XSS attacks, safe ways to represent dangerous characters in web pages, defense mechanisms based on data types and contexts, and the significance of encoding and output handling. Learn how attackers misuse XSS to hijack ses
0 views • 32 slides
Cyber Security Engineering: Understanding the Importance and Examples
Cyber security is crucial due to the uncontrollable nature of digital devices and the potential for unauthorized access and manipulation, leading to severe consequences like data leakage, information distortion, and unauthorized access. Two examples illustrate the real-world implications of cyber th
0 views • 20 slides
Virtual Meeting Security Best Practices
Ensure the security of your virtual meetings by following best practices to mitigate threats like teleconference hijacking. Consider tools like Zoom, Skype, Webex, and others to host secure meetings. Avoid making meetings public, manage screen-sharing options, use waiting rooms, validate participant
0 views • 23 slides
Understanding Router Design and Longest Prefix Matching in Computer Networks
Explore concepts like control plane processors, route lookup, and IP block reallocation in computer networking. Learn about the basics of forwarding tables, scheduling, and buffer management crucial for network operations. Dive into routing algorithms and data plane processing for efficient packet d
0 views • 39 slides
Authenticated Firmware Loaders: Verification and Potential Vulnerabilities
This research paper explores the verification of authenticated firmware loaders presented by Sujit Kumar Muduli, Pramod Subramanyan, and Sayak Ray. It delves into the secure boot process to prevent malicious firmware compromise. The study also discusses trusted firmware updates for remote device sec
0 views • 29 slides