Neural quantum state tomography, improvements and applications
Advancements and potential applications of neural quantum state tomography, aiming to reduce the exponential classical memory required for expressing quantum states. It discusses the benefits of using machine learning techniques to process and analyze quantum data, such as cleaning up states, manipu
4 views • 26 slides
Cryptography,.Quantum-safe Cryptography& Quantum Cryptography
Dive into the world of cryptography, quantum-safe cryptography, and quantum technology as discussed in Maurizio D. Cina's presentation at CYBERDAYS in Prato. Topics include current cryptosystems, post-quantum cryptography, quantum key distribution, and future cryptosystems based on quantum algorithm
5 views • 17 slides
CERN Quantum Technologies Initiative Overview
The CERN Quantum Technologies Initiative (QTI) aims to explore the impact of quantum technology on CERN's physics programs. This phase involves identifying key areas for collaboration, conducting scientific investigations, and building quantum capacity. The strategy and roadmap were developed with i
6 views • 14 slides
Addressing The Quantum Threat: The Quantum Resistant Ledger
The Quantum Resistant Ledger (QRL) is a visionary blockchain and digital asset security solution designed to counter the emerging threat of quantum computing. With quantum technology advancing and traditional blockchains at risk, QRL offers an industrial-grade, quantum computer-resistant cryptocurre
2 views • 9 slides
Formal Verification of Quantum Cryptography by Dominique Unruh
Explore the significance of formal verification in quantum cryptography as discussed by Dominique Unruh from the University of Tartu. Understand the challenges, motivations, and current work in verifying quantum crypto protocols, and the potential impact of quantum computers on common encryption met
0 views • 25 slides
Introduction to Quantum Computing: Exploring the Future of Information Processing
Quantum computing revolutionizes information processing by leveraging quantum mechanics principles, enabling faster algorithms and secure code systems. Advancements in quantum information theory promise efficient distributed systems and combinatorial problem-solving. Discover the evolution of quantu
0 views • 68 slides
Near-Optimal Quantum Algorithms for String Problems - Summary and Insights
Near-Optimal Quantum Algorithms for String Problems by Ce Jin and Shyan Akmal presents groundbreaking research on string problem solutions using quantum algorithms. The study delves into various key topics such as Combinatorial Pattern Matching, Basic String Problems, Quantum Black-box Model, and mo
0 views • 25 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
Exploring Quantum Mechanics: Illusion or Reality?
Delve into the fascinating realm of quantum mechanics with Prof. D. M. Parshuramkar as he discusses the contrast between classical and quantum mechanics. Discover how classical mechanics fails to predict the behavior of electrons in atoms and molecules, leading to the development of quantum mechanic
1 views • 70 slides
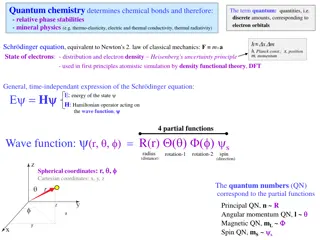
Understanding Quantum Chemistry and Electron Orbitals
Quantum chemistry plays a key role in determining chemical bonds, phase stabilities, and mineral physics through the study of electron orbitals, quantum numbers, and energy levels. This involves concepts such as the Schrödinger equation, quantum quantities, and the uncertainty principle. The arrang
0 views • 31 slides
Exploring Neural Quantum States and Symmetries in Quantum Mechanics
This article delves into the intricacies of anti-symmetrized neural quantum states and the application of neural networks in solving for the ground-state wave function of atomic nuclei. It discusses the setup using the Rayleigh-Ritz variational principle, neural quantum states (NQSs), variational pa
0 views • 15 slides
Exploring Cloud Cryptography for Secure Data Processing
Cloud cryptography is a vital aspect of data security in cloud computing, allowing data to be encrypted and processed securely. This presentation delves into the concepts of cloud cryptography, homomorphic encryption, and the two types of homomorphic encryption - hybrid and partial. It discusses the
8 views • 17 slides
Understanding Quantum Wires and Nanowires: Properties and Applications
Quantum wires, quantum dots, and nanowires are essential components in nanotechnology due to their unique properties and applications. Quantum wires are one-dimensional systems with restricted electron movement, while quantum dots are zero-dimensional, limiting electron movement in all dimensions. N
3 views • 12 slides
Performance of Post-Quantum Signatures: Analysis and Comparison
Explore the performance and characteristics of various post-quantum signature schemes including Lattice-based Dilithium, QTesla, Falcon, Symmetric Sphincs+, Picnic, Multivariate GEMSS, Rainbow, and more. Understand the implications of using these schemes in TLS, code signing, firmware updates, signe
0 views • 29 slides
Exploring the World of Quantum Money and Cryptography
Delve into the realm of quantum money, computation, and cryptography, understanding the intricacies of semi-quantum money, consensus problems, post-quantum cryptography, and unique concepts like certifiable randomness and tokenized digital signatures.
6 views • 30 slides
Overview of Basic Security Properties and Cryptography Fundamentals
This content provides an introduction to basic security properties such as confidentiality, authenticity, integrity, availability, non-repudiation, and access control. It also covers the fundamentals of cryptography, including symmetric and asymmetric encryption, public-key cryptography, and the imp
1 views • 41 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
Post-Quantum Cryptography Security Proofs and Models Overview
Explore the various aspects of post-quantum cryptography security, including evaluation criteria, building public key cryptography (PKC) systems, security proofs, digital signatures, and reduction problems. Dive into topics such as performance, cryptanalysis, provable security, standard models, exis
0 views • 42 slides
Foundations of Cryptography: MIT Course Overview and Key Concepts
Explore the MIT course "Foundations of Cryptography" offering insights on cryptography, key themes like adversarial thinking and computational hardness, historical context, and the significance of security proofs via reductions. Learn about the course staff, topics covered, and intellectual origins
1 views • 33 slides
Quantum Circuit Simulations and Electromagnetic Analyses in Quantum Photonics
Explore the world of quantum photonics with insights into two-qubit photon counters, jointed cavities, qubit pads, and quantum circuit simulations. Ansys simulations and experimental data by researchers Alessandro D'Elia and Claudio Gatti provide in-depth analysis of quantum phenomena. Discover the
0 views • 7 slides
Exploring Post-Quantum Cryptography and Constructive Reductions
Delve into the realm of post-quantum cryptography through an insightful journey of constructive reductions, rethinking cryptography assumptions, and the relationship between classical and post-quantum regimes. Discover the challenges, advancements, and goals in the quest for durable cryptographic al
1 views • 21 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Post-Quantum Cryptography in IEEE 802.11 - Current State and Future Concerns
Submission discusses the potential impact of post-quantum algorithms on IEEE 802.11 networks, highlighting the necessity to prepare for a post-quantum future. It explores the risks posed by quantum computing to existing cryptographic systems and emphasizes the importance of adopting post-quantum sol
0 views • 19 slides
New Perspectives on Computationally Binding Quantum Commitments
Exploring the concept of computationally binding quantum commitments through classical and new definitions focusing on collapsing hash functions, highlighting existing definitions, and proposing stronger definitions for post-quantum cryptography. The talk delves into the nuances of commitments, addr
0 views • 13 slides
Quantum Key Agreements and Random Oracles
This academic paper explores the impossibility of achieving key agreements using quantum random oracles, discussing the challenges and limitations in quantum communication, cryptographic protocols, quantum computation, and classical communication. The study delves into the implications of quantum ra
0 views • 29 slides
Quantum Computing: Achievable Reality or Unrealistic Dream Workshop
Explore the intriguing realm of quantum computing through insightful lectures by Prof. Gil Kalai and Prof. Nadav Katz at the American Physical Society workshop. Delve into the possibilities, failures, and advancements in quantum information science. Join the discussion on the state-of-the-art develo
0 views • 13 slides
Efficient Verified Cryptography in F* by Jean-Karim Zinzindohou
Explore the importance of cryptography verification in F* through Jean-Karim Zinzindohou's joint work with Karthik Bhargavan. Discover the significance of verifying crypto, static guarantees provided, and examples like elliptic curve cryptography. Delve into F* as a rich ML-like language for secure
0 views • 38 slides
Cache Attack on BLISS Lattice-Based Signature Scheme
Public-key cryptography, including the BLISS lattice-based signature scheme, is pervasive in digital security, from code signing to online communication. The looming threat of scalable quantum computers has led to the development of post-quantum cryptography, such as lattice-based cryptography, whic
0 views • 13 slides
Exploring Quantum Information through Polarization of Photons
Quantum information and photon polarization are explored in this detailed presentation featuring the ultimate quantum 2-state system. The content delves into the behavior of single photons at a quantum level, showcasing the intriguing properties and implications of quantum superposition in polarizat
1 views • 14 slides
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computing utilizes the principles of quantum mechanics to process information exponentially faster than classical computers. This advancement poses a significant threat to current cryptographic systems, especially those reliant on factors like RSA and Diffie-Hellman key exchange. If large-sc
0 views • 25 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Post-Quantum Cryptography: Safeguarding Secrets in the Digital Age
Delve into the realm of post-quantum cryptography and learn about the evolving landscape of secure communication. Explore topics such as Supersingular Isogeny Graphs, Ring-Learning With Errors, and the significance of key exchange in maintaining confidentiality. Discover the foundations of public ke
0 views • 39 slides
Understanding Quantum Computing: Quantum Gates, Bits, and Applications
Explore the world of quantum computing with this detailed guide covering quantum bits, gates, their applications, and the advancements made in the field. From classical bits to qubits, Bell states, and quantum gates, discover the fundamental principles that drive quantum computing forward.
0 views • 37 slides
Quantum Mechanics and Geometric Interpretations in Weyl Space
The discussion explores Weyl quantum mechanics, Bohm's interpretation of quantum potential, and geometric formulations in Euclidean-Weyl space. It delves into the implications of nonlocal quantum potentials and the nature of metric spaces in shaping quantum phenomena. Concluding with alternative vie
0 views • 30 slides
Overview of QuMA: A Microarchitecture for a Superconducting Quantum Processor
This paper introduces QuMA, a quantum microarchitecture that bridges the gap between high-level algorithms and the quantum physical layer. It defines a multi-layered system stack for quantum computers, focusing on compiler support, quantum error correction, and the need for a micro-architecture fram
0 views • 21 slides
Unveiling the Quantum World: Understanding Blackbody Radiation and Quantum Mechanics
Quantum Mechanics emerged between 1900 and 1930 as a revolutionary theory explaining the behavior of microscopic particles. This article delves into the need for Quantum Physics due to classical mechanics' limitations, focusing on Blackbody Radiation and laws governing it like Wiens Displacement Law
1 views • 30 slides
Introduction to Lattice-Based Cryptography and Linear Equations Solving
Explore the fundamentals of lattice-based cryptography and the significance of solving linear equations in cryptography. Learn about the exponential hardness and quantum resistance of lattice-based crypto, as well as the challenges and techniques involved in solving linear equations with various str
2 views • 29 slides
New Directions in Cryptography: Harta Dwijaksara, Yi Jae Park
Explore the world of cryptography through this comprehensive guide covering topics such as conventional cryptography, public key cryptography, one-way authentication, trap doors, computational complexity, and more. Learn about the importance of privacy in communications and the key principles behind
0 views • 20 slides
Quantum Error Correction and Fault Tolerance Overview
Quantum error correction and fault tolerance are essential for realizing quantum computers due to the challenge of decoherence. Various approaches, including concatenated quantum error correcting codes and topological codes like the surface code, are being studied for fault-tolerant quantum computin
0 views • 19 slides
Securing Communication in the Quantum Computing Era
Embracing Post-Quantum Cryptography (PQC) is essential to counter the threat posed by large-scale quantum computers to current public key cryptosystems. Russ Housley, a prominent figure in the field, highlights the urgency to deploy PQC algorithms before a quantum computing breakthrough occurs. The
0 views • 9 slides