Revisiting LDPC Rate Matching in IEEE 802.11 for Improved Performance
The document discusses revisiting LDPC rate matching in IEEE 802.11, focusing on issues such as performance loss compared to previous standards, power consumption in LDPC decoding/encoding, and over puncturing. It covers preliminary concepts, packet size distribution in various devices like laptops
2 views • 17 slides
Virtualized Evolved Packet Core Market
Explore $19.87 billion Virtualized Evolved Packet Core Market: Get exclusive insights on key market trends, segments, geographical analysis, & competitive analysis!\nDownload Sample Report Here @ \/\/ \/download-sample-report\/cp_id=5201
3 views • 6 slides
Virtualized Evolved Packet Core Market Projected to Reach $19.87 Billion by 2031
Explore $19.87 billion Virtualized Evolved Packet Core Market: Get exclusive insights on key market trends, segments, geographical analysis, & competitive analysis!\n
1 views • 4 slides
Introduction to IEEE 802.11-20 EHT PPE Thresholds Field
IEEE 802.11-20 standard defines the Nominal Packet Padding values and Pre-FEC Padding Factors for PE fields in 11ax. The selection of Nominal Packet Padding values is crucial and can be determined using specific methods, including PPE Thresholds Present subfield. The PPE Thresholds field contains in
0 views • 14 slides
Understanding IMIX in Networking and Testing Tools
IMIX, or Internet Mix, refers to a mixture of packet sizes used to simulate real-world network conditions for testing networking devices. Various tools and methods, such as Genome Reporting, Moongen, T-Rex, and Spirent TestCenter, implement IMIX with specific packet size distributions and characteri
1 views • 8 slides
Insights on Global Governance and Multistakeholderism for Activists
This educational packet provides valuable insights for activists focused on understanding the governance context surrounding UN organizations. It discusses the impact of multistakeholderism on global governance, challenges to multilateralism, and the need for a more equitable system. The packet incl
0 views • 11 slides
Enhancing Network Performance with RoCE Technology
Remote Direct Memory Access (RDMA) benefits, RoCEv2 packet format, resilient RoCE feature progression, optimizing network performance with QoS, and RoCE congestion control convergence analysis are discussed in this proposal. RoCE technology offers low latency, high throughput, and efficient CPU usag
0 views • 19 slides
IEEE 802.11-19/1575r0 Multi-Link BA Operation Overview
Presentation slides from September 2019 discussing the Multi-Link Operation (MLO) in IEEE 802.11-19/1575r0 standard. The slides cover topics such as the benefits of MLO, synchronized/asynchronized rules, terminology, architecture, and common BA sessions. The proposal aims to define an architecture s
0 views • 25 slides
Understanding Sound Card Digital Operation on Winlink Express
Explore the capabilities of utilizing a sound card interface for digital operations on Winlink Express, offering flexibility and performance for various modes, including Packet, ARDOP, Vara HF, and Vara FM. Learn about the benefits of sound card interfaces, sound card operation, and the modes suppor
0 views • 39 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Explore Cisco Packet Tracer for Network Simulation
Discover Cisco Packet Tracer, a powerful network simulation program used for hands-on LAN configuration and managing large-scale distributed systems. Learn about its availability to Networking Academy users and how to download the software for free through Academy Connection.
0 views • 8 slides
Understanding Programmable Traffic Management for Network Optimization
Programmable Traffic Management involves packet scheduling, traffic shaping, policing, drop policies, packet buffering, replication, and classification to optimize network performance. It is used in integrated switch architectures and is crucial for addressing diverse traffic characteristics and req
0 views • 66 slides
Understanding Checksums in Packet Headers
Checksums play a crucial role in validating the integrity of packet headers in various protocols. This tutorial explores the concept of checksums, the use of algorithms like CRC, and the process of recalculating checksums to ensure data integrity in network communications.
0 views • 11 slides
Eastlake High School Athletics Visitor Facilities Information Packet 2024 - 2025
Welcome to Eastlake High School! This informational packet provides details on visitor facilities, contact information for key administration and athletic personnel, the importance of sportsmanship, and a list of head coaches for various sports teams. The emphasis is on prioritizing student athlete
2 views • 17 slides
Understanding Packet Radio: A Comprehensive Guide
Packet radio, utilizing VHF FM technology, is a digital mode allowing keyboard-to-keyboard communication, messaging, mailboxes, bulletins, and more. It uses the AX.25 protocol and operates at varying data rates on VHF and HF bands. The system comprises basic stations and automated nodes, each requir
0 views • 20 slides
Understanding Router Routing Tables in Computer Networks
Router routing tables are crucial for directing packets to their destination networks. These tables contain information on directly connected and remote networks, as well as default routes. Routers use this information to determine the best path for packet forwarding based on network/next hop associ
0 views • 48 slides
Understanding WAN Technologies and Routing in Large Networks
WAN technologies enable communication over large geographic distances, connecting multiple sites efficiently. Packet switches play a crucial role in forwarding packets, with modern WAN architecture focusing on interconnecting switches using LAN technology and leased digital circuits. Store and forwa
1 views • 17 slides
Enhancing Network Debugging with CherryPick in Software-Defined Datacenter Networks
Explore CherryPick, a technique for tracing packet trajectory in software-defined datacenter networks. It helps in debugging by ensuring data plane conforms with control plane policies, localizing network problems, and enabling packet trajectory tracing challenges like non-shortest paths. CherryPick
0 views • 14 slides
Programmable Parser and Header Definitions at University of South Carolina
Programmable parsers and custom header definitions play a crucial role in network packet processing. This presentation by Jorge Crichigno at the University of South Carolina covers topics such as parser operation, predefined states, and header formats. The content delves into the capabilities of pro
1 views • 22 slides
Understanding Internet Architecture and Networking Principles
The content explores the architecture and goals of the Internet, focusing on its original objectives, survivability in the face of failure, and evolving requirements. It delves into how networks function, describing behaviors and packet handling. Additionally, it discusses the framework for describi
0 views • 15 slides
Understanding the Impact of 1% Packet Loss on TCP and the Cubic Congestion Avoidance Algorithm
Delve into the surprising effects of even 1% packet loss on network flows, the methods TCP uses to mitigate loss, and how the CUBIC congestion avoidance algorithm works. Explore the researched but not quantified problem of packet loss and learn about a test methodology using Ubuntu hosts to measure
0 views • 24 slides
Honors Human Anatomy and Physiology Summer Introduction Packet
Welcome to Honors Human Anatomy and Physiology at Col. Z. Magruder High School! Dr. Newman provides an overview of the course, including anatomical positions, body planes, regional terms, and tables for reference. The packet sets the foundation for studying the structure and function of the human bo
0 views • 7 slides
FY25 Title III Consortium Packet Overview
FY25 Title III Consortium Packet provides information on English Language Proficiency allocations, consortium formation, grant management, board approval requirements, and responsibilities of the lead fiscal agent. English Learner counts determine funding eligibility, with consortiums formed to reac
0 views • 15 slides
Bandwidth and Packet Type Detection Schemes for 40-50GHz Millimeter Wave Communication Systems
The document discusses bandwidth and packet type detection schemes for 40-50GHz millimeter wave communication systems in IEEE 802.11aj specifications. It proposes a preamble design for auto-detection of bandwidth and packet type to improve channel estimation and decoding efficiency. By utilizing dif
0 views • 27 slides
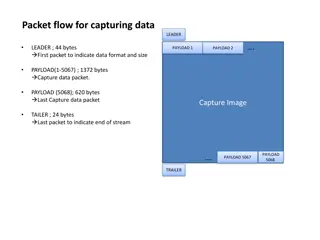
Wireshark Data Capture and UDP Analysis
Capturing data flow through packets in Wireshark reveals a series of fragmented payloads, starting with a leader packet of 44 bytes and ending with a trailer of 24 bytes. The UDP data payloads range from 44 to 1372 bytes, with specific lengths for different payloads and packets. Analysis includes UD
0 views • 4 slides
Dictionary Compression and Deep Packet Inspection (DPI) Overview
This content discusses Decompression-Free Inspection (DPI) for shared dictionary compression over HTTP, the challenges and solutions in deep packet inspection (DPI), compressed HTTP methods, examples of intra-response and inter-response compression, and current operations of Network Intrusion Detect
0 views • 33 slides
Enhancing Network Security Using Snort Virtual Network Function with DPI Service
Deep Packet Inspection (DPI) as a service is explored in this work, aiming to improve performance, innovation, and security in network operations. By extracting DPI from middleboxes and offering it as a shared service, the paper suggests benefits such as optimized packet scanning, enhanced functiona
0 views • 55 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Advancements in Network and Database Integration
This presentation discusses the convergence of network advancements and database technologies, highlighting key challenges such as packet processing at increasing line rates and latency issues. It explores the current landscape of databases from a research perspective and proposes solutions for opti
0 views • 13 slides
Understanding Undefined Behaviours in P4 Programs
Explore the implications of undefined behaviours in P4 programs, discover how to identify and address them, or even leverage them to your advantage. Delve into the world of P4 programming, where you can manipulate packet processing sequences, match-action tables, and packet transformations within a
0 views • 66 slides
PacketGuardian: A Tool for Static Detection of Packet Injection Vulnerabilities
This research paper introduces PacketGuardian, an effective static analysis tool designed to evaluate the robustness of protocol implementations against packet injection attacks. This tool supports precise context, flow, field-sensitive taint analysis, implicit flow analysis, and employs a summary-b
0 views • 23 slides
Exploring the Evolution of Data Communications: A Brief Overview
Delve into the progression of data communications from Morse code to modern radio email systems like Winlink. Discover the history of protocols, technologies, and the impact of the internet on amateur packet radio. Unravel the development of ARQ data protocols, X.25 packet switching, and the transit
0 views • 51 slides
Issues and Tests in Data Analysis at IHEP Experimental Center
Data analysis issues and tests were found by Tingxuan Zeng at the TDAQ Group within the Experimental Center at IHEP. Various issues were identified during the last data taking session, including discrepancies in GEMDC packet counts, incorrect packet lengths, and buffer pile-up. Analysis and testing
0 views • 4 slides
Understanding Haskell Types, Classes, Functions, and Polymorphism
In Haskell, types are collections of related values, ensuring type safety through compile-time type inference. Type errors occur when functions are applied to arguments of the wrong type. Annotations help define types, and Haskell offers basic types like Bool, Char, String, Int, Integer, Float, and
0 views • 30 slides
Understanding the Basics of Packet Radio for Amateur Communication
Explore the world of packet radio, a digital mode used by amateur radio operators to build wireless computer networks. Learn about its benefits, how it works using the AX.25 protocol, making connections, advantages such as error checking, and building a packet station with the necessary components.
0 views • 19 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Enhancing Data Center Network Performance through Packet Scheduling and ECN
Explore the advancements in data center network performance improvement through techniques like packet scheduling, Explicit Congestion Notification (ECN), and strict priority for different types of flows. The research discusses the requirements of low latency for short messages and high throughput f
0 views • 48 slides
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of disp
0 views • 17 slides
Considerations on PHY Padding and Packet Extension in 11ax
The document discusses the proposed PHY padding and packet extension for IEEE 802.11ax, focusing on considerations for processing data within SIFS duration and relaxation of LDPC decoding processing time. It outlines the overview of the proposed padding scheme, considerations for LDPC implementation
0 views • 15 slides
Innovative Application Packet for ACE Solutions - Explore the Visual Journey
Dive into the visually captivating world of ACE Solutions with their cutting-edge application packet. From stunning visuals to advanced functionality, this packet showcases the power and versatility of ACE Solutions for modern applications. Discover the seamless navigation, engaging content, and ric
0 views • 59 slides