Computational Physics (Lecture 18)
Neural networks explained with the example of feedforward vs. recurrent networks. Feedforward networks propagate data, while recurrent models allow loops for cascade effects. Recurrent networks are less influential but closer to the brain's function. Introduction to handwritten digit classification
0 views • 55 slides
Evolution and Potential of 5G Technology
Explore the evolving landscape of 5G technology, from enhanced mobile broadband to groundbreaking use cases and standalone networks. Learn how supportive regulations and spectrum allocation are vital for unlocking 5G's full potential. Discover the transformative impact of Standalone 5G networks on i
8 views • 10 slides
Insights into 5G NSA Deployment and Performance in Rome
Explore the transition from 4G to 5G, specifically focusing on the deployment and performance of 5G Non-Standalone (NSA) networks in Rome, Italy. Detailed analysis includes coverage, application performance, and empirical data from large-scale measurement campaigns conducted by four Mobile Network O
2 views • 29 slides
Understanding Computer Networks: Types and Characteristics
In the realm of computer networks, nodes share resources through digital telecommunications networks. These networks enable lightning-fast data exchange and boast attributes like speed, accuracy, diligence, versatility, and vast storage capabilities. Additionally, various types of networks exist tod
9 views • 12 slides
Graph Neural Networks
Graph Neural Networks (GNNs) are a versatile form of neural networks that encompass various network architectures like NNs, CNNs, and RNNs, as well as unsupervised learning models such as RBM and DBNs. They find applications in diverse fields such as object detection, machine translation, and drug d
2 views • 48 slides
Understanding SHA-256 Algorithm and History
SHA-256 is a secure hashing algorithm that produces 256-bit hash values and is more secure than MD5, SHA-0, and SHA-1 due to fewer collisions. Created in 2001 by the NSA, it is widely used in various applications like cryptocurrency, SSL certificates, and blockchain. This summary provides insights i
0 views • 17 slides
Understanding AES Encryption Algorithm and Its Implementation
Learn about the Advanced Encryption Standard (AES) algorithm - a NSA-approved NIST standard encryption method. Explore how AES works, its key rounds, SubBytes, ShiftRows, MixColumns operations, and its optimization for embedded systems and small memory devices. Discover the importance of secure cryp
0 views • 14 slides
Understanding Artificial Neural Networks From Scratch
Learn how to build artificial neural networks from scratch, focusing on multi-level feedforward networks like multi-level perceptrons. Discover how neural networks function, including training large networks in parallel and distributed systems, and grasp concepts such as learning non-linear function
1 views • 33 slides
Understanding Back-Propagation Algorithm in Neural Networks
Artificial Neural Networks aim to mimic brain processing. Back-propagation is a key method to train these networks, optimizing weights to minimize loss. Multi-layer networks enable learning complex patterns by creating internal representations. Historical background traces the development from early
1 views • 24 slides
Exploring Samsung SmartThings Hub and Zigbee/Zwave Networks
The Samsung SmartThings hub is a versatile device connecting Zigbee and Zwave networks, offering secure access to SkySpark via HTTPS. Zigbee and Zwave networks operate on distinct frequencies, enabling efficient communication without interference with WiFi. These networks support various devices for
0 views • 19 slides
Understanding Wireless Wide Area Networks (WWAN) and Cellular Network Principles
Wireless Wide Area Networks (WWAN) utilize cellular network technology like GSM to facilitate seamless communication for mobile users by creating cells in a geographic service area. Cellular networks are structured with backbone networks, base stations, and mobile stations, allowing for growth and c
2 views • 17 slides
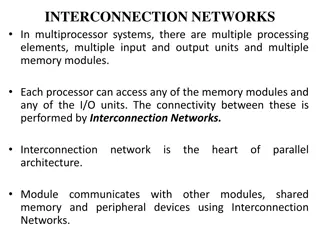
Understanding Interconnection Networks in Multiprocessor Systems
Interconnection networks are essential in multiprocessor systems, linking processing elements, memory modules, and I/O units. They enable data exchange between processors and memory units, determining system performance. Fully connected interconnection networks offer high reliability but require ext
1 views • 19 slides
Understanding Computer Networks in BCA VI Semester
Computer networks are vital for sharing resources, exchanging files, and enabling electronic communications. This content explores the basics of computer networks, the components involved, advantages like file sharing and resource sharing, and different network computing models such as centralized a
1 views • 96 slides
Support and Development Initiatives for Netball in South Africa
The presentation discusses the support provided by the Department to Netball South Africa (NSA), including financial aid and assistance to reposition and enhance the sport. It highlights initiatives such as the Federation Intensive Support Programme and the Netball World Cup Legacy Programme, focusi
0 views • 8 slides
Understanding Computer Communication Networks at Anjuman College
This course focuses on computer communication networks at Anjuman College of Engineering and Technology in Tirupati, covering topics such as basic concepts, network layers, IP addressing, hardware aspects, LAN standards, security, and administration. Students will learn about theoretical and practic
0 views • 72 slides
Introduction to Neural Networks in IBM SPSS Modeler 14.2
This presentation provides an introduction to neural networks in IBM SPSS Modeler 14.2. It covers the concepts of directed data mining using neural networks, the structure of neural networks, terms associated with neural networks, and the process of inputs and outputs in neural network models. The d
0 views • 18 slides
Enhancing Agriculture Through Global Knowledge Networks and Information Management Systems
Global and regional knowledge networks play a vital role in agriculture by facilitating information sharing, collaboration, capacity building, and coordination among stakeholders. These networks improve access to information, foster collaboration, enhance capacity building, and strengthen coordinati
0 views • 5 slides
Understanding Router Routing Tables in Computer Networks
Router routing tables are crucial for directing packets to their destination networks. These tables contain information on directly connected and remote networks, as well as default routes. Routers use this information to determine the best path for packet forwarding based on network/next hop associ
0 views • 48 slides
P-Rank: A Comprehensive Structural Similarity Measure over Information Networks
Analyzing the concept of structural similarity within Information Networks (INs), the study introduces P-Rank as a more advanced alternative to SimRank. By addressing the limitations of SimRank and offering a more efficient computational approach, P-Rank aims to provide a comprehensive measure of si
0 views • 17 slides
Implementing Technology in Census Data Management
Utilizing technology in census data management can greatly enhance accuracy, project completion times, timeliness, and cost-effectiveness. The NSA has successfully implemented Computer-Assisted Personal Interviews (CAPI) for various surveys, leading to improved data collection efficiency. Considerat
0 views • 24 slides
Understanding Advanced Classifiers and Neural Networks
This content explores the concept of advanced classifiers like Neural Networks which compose complex relationships through combining perceptrons. It delves into the workings of the classic perceptron and how modern neural networks use more complex decision functions. The visuals provided offer a cle
0 views • 26 slides
Implications of President's NSA Review Group - Conway-Walker Lecture
In the Conway-Walker Lecture at Cornell, the implications of the President's NSA Review Group were discussed, focusing on themes like declining half-life of secrets, multiple equities in one Internet, and the role of IT professionals. The lecture delved into the creation of the review group followin
0 views • 32 slides
3GPP TSG-RAN-WG4#95-e Meeting Summary: Power Class Requirements and Way Forward Decisions
During the 3GPP TSG-RAN-WG4#95-e meeting, discussions were held on power class requirements, UL MIMO, and other related topics. The meeting covered various options for setting up TxD requirements, focusing on Release 16 independence, UL MIMO emission requirements for R15, NSA NR power class clarific
0 views • 6 slides
Understanding Relational Bayesian Networks in Statistical Inference
Relational Bayesian networks play a crucial role in predicting ground facts and frequencies in complex relational data. Through first-order and ground probabilities, these networks provide insights into individual cases and categories. Learning Bayesian networks for such data involves exploring diff
0 views • 46 slides
Innovative Approaches to Cyber Operations Capstone Course
Explore innovative pedagogical methods implemented in a Cyber Operations Capstone Laboratory Course, covering topics like flipping the classroom, live exercises, and balancing offense and defense strategies. Students work on practical applications like Kali, Metasploit, and web applications security
0 views • 17 slides
Understanding Overlay Networks and Distributed Hash Tables
Overlay networks are logical networks built on top of lower-layer networks, allowing for efficient data lookup and reliable communication. They come in unstructured and structured forms, with examples like Gnutella and BitTorrent. Distributed Hash Tables (DHTs) are used in real-world applications li
0 views • 45 slides
Understanding Networks: An Introduction to the World of Connections
Networks define the structure of interactions between agents, portraying relationships as ties or links. Various examples such as the 9/11 terrorists network, international trade network, biological networks, and historical marriage alliances in Florence illustrate the power dynamics within differen
0 views • 46 slides
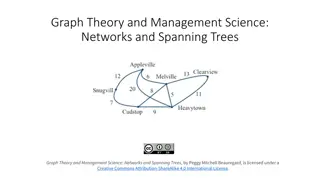
Understanding Graph Theory and Networks: Concepts and Applications
Explore the concepts of graph theory and management science, focusing on networks, spanning trees, and their practical applications. Learn about the difference between a snowplow tracing streets, a traveler visiting cities, and connecting towns with cables. Discover how networks like Facebook evolve
0 views • 15 slides
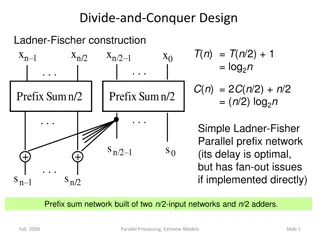
Parallel Prefix Networks in Divide-and-Conquer Algorithms
Explore the construction and comparisons of various parallel prefix networks in divide-and-conquer algorithms, such as Ladner-Fischer, Brent-Kung, and Kogge-Stone. These networks optimize computation efficiency through parallel processing, showcasing different levels of latency, cell complexity, and
1 views • 21 slides
The Evolution of Virtual Certification in NSA Perspective
The journey towards virtual certification, as seen through the lens of an NSA, involves navigating expensive, time-limited, and location-limited processes. The classic process involves safety demonstrations, risk analysis, and virtual simulations, highlighting the advantages and drawbacks of testing
0 views • 11 slides
Diverse Social Entities Mining from Linked Data in Social Networks
This research focuses on mining diverse social entities from linked data in social networks using a DF-tree structure and DF-growth mining algorithm. The study explores the extraction of important linked data in social networks and the mining of various social entities such as friends. Prominence va
0 views • 13 slides
The Enigmatic Kryptos Sculpture by Jim Sanborn at CIA Headquarters
The Kryptos sculpture created by artist Jim Sanborn in 1990 stands on the grounds of the CIA headquarters in Langley, Virginia. It features a metal wall adorned with encrypted text, benches, a fish pond, and other intriguing elements. Collaborating with NSA cryptographer Ed Scheidt, Sanborn incorpor
0 views • 56 slides
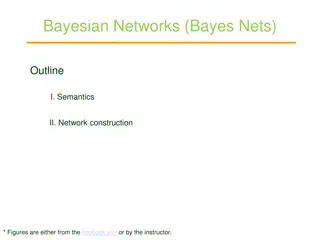
Understanding Bayesian Networks: A Comprehensive Overview
Bayesian networks, also known as Bayes nets, provide a powerful tool for modeling uncertainty in complex domains by representing conditional independence relationships among variables. This outline covers the semantics, construction, and application of Bayesian networks, illustrating how they offer
0 views • 17 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
The Edward Snowden Incident: Government, Politics, and Ethics in the Internet Age
Explore the Edward Snowden incident, where the former NSA employee leaked classified information revealing the U.S. government's surveillance activities. Delve into the ethical implications, the timeline of events, and the impact on government and society in the internet age.
0 views • 26 slides
Evolution of Networking: Embracing Software-Defined Networks
Embrace the future of networking by transitioning to Software-Defined Networks (SDN), overcoming drawbacks of current paradigms. Explore SDN's motivation, OpenFlow API, challenges, and use-cases. Compare the complexities of today's distributed, error-prone networks with the simplicity and efficiency
0 views • 36 slides
Rally Against Mass Surveillance - StopWatching.Us Event Summary
Edward Snowden's revelations exposed government surveillance on citizens, sparking a rally against mass surveillance on October 26, 2013. The ACLU supports Snowden as a whistleblower, while NSA officials criticize him. The event highlights concerns over privacy, government overreach, and the collect
0 views • 18 slides
Understanding EternalBlue Exploit: History, Vulnerabilities, and Impact
EternalBlue is a notorious exploit developed by the NSA and leaked by the Shadow Brokers hacker group. It has been used in significant cyberattacks like WannaCry and NotPetya, targeting Windows systems through SMB protocol vulnerabilities. This exploit's impact and the various attacks it has been ut
0 views • 17 slides
Understanding Interconnection Networks in Embedded Computer Architecture
Explore the intricacies of interconnection networks in embedded computer architecture, covering topics such as connecting multiple processors, topologies, routing, deadlock, switching, and performance considerations. Learn about parallel computer systems, cache interconnections, network-on-chip, sha
0 views • 43 slides
Understanding Deep Generative Bayesian Networks in Machine Learning
Exploring the differences between Neural Networks and Bayesian Neural Networks, the advantages of the latter including robustness and adaptation capabilities, the Bayesian theory behind these networks, and insights into the comparison with regular neural network theory. Dive into the complexities, u
0 views • 22 slides