Seat Belts
How seat belts work in a crash and the importance of wearing them to protect yourself during a collision.
1 views • 14 slides
Line Segment Intersection
Geometric intersections play a crucial role in computational geometry for tasks such as solid modeling, collision detection in robotics, and overlaying subdivisions in geographic information systems. The problem of line segment intersection involves finding all intersection points between a set of c
0 views • 17 slides
Autonomous Conjunction Assessment Methodology Among Satellites
Methodology for Collision Avoidance (CA) among constellations of autonomously-controlled satellites is crucial for protecting assets in space. From straightforward protection against dead satellites to active coordination for maneuverable payloads, the range of primary-secondary CA possibilities is
1 views • 12 slides
Understanding 2D Collision Detection in Game Development
Explore the intricacies of 2D collision detection in game development through methods like distance checks, bounding shapes, and optimizing collision tests. Dive into concepts like sprite speed assumptions, square-square collisions, and rectangle testing complexities. Learn about useful Rectangle me
5 views • 29 slides
How Do I Change My Name on an Allegiant Air Flight Ticket
Allegiant Air usually charges nothing for small Changes, but not for full name changes. With the correct documentation, full name changes are achievable for reasons like marriage or legal changes. On the policy of Allegiant Airline Name Change Policy There are fees associated with modifications, dep
5 views • 5 slides
Can I Change my Name on a Southwest Airlines Ticket?
Name updates on tickets for minor edits or legal name changes are usually permitted by Southwest Airlines. Generally speaking, though, they prohibit transfers to another individual. To legally alter your name, get in touch with Southwest Airlines Name Change Policy customer care and provide them wit
20 views • 5 slides
How do I change my name on a Southwest Airlines ticket?
If a passenger's name on a ticket is misspelled and the adjustment doesn't change who they are, Southwest Airlines will correct it for free. Fees might be charged, though, if the name change entails making a major modification or giving the ticket to someone else. Southwest Airlines Name Change Poli
4 views • 5 slides
Chemical Kinetics: Understanding Reaction Rates and Factors
Chemical kinetics is a branch of physical chemistry that explores the velocity and factors influencing chemical reactions. It studies how reactants transform into products, considering conditions like temperature, pressure, and reactant concentrations. Factors affecting reaction rates include the na
7 views • 24 slides
Automotive Sensing Systems & Radar Technology Overview
Explore the world of automotive sensing systems and radar technology including radar speed guns. Learn about the sensors used in cars for various applications such as radar cruise control, collision detection, and more. Discover the characteristics of these sensors and how they can be augmented or r
0 views • 7 slides
How Can I Change my Name on a Southwest Airlines Ticket
Get in touch with Southwest Airlines customer support right away if you believe you spelled your name incorrectly when making a reservation. They allow little changes, like typo repairs, without needing cancellation and rescheduling. Southwest Airlines Name Change Policy They can be contacted via ph
8 views • 5 slides
What is Allegiant Air’s Name Change Policy?
Allegiant Air\u2019s name change policy allows for corrections of minor spelling errors or typos in the passenger's name. For more significant changes or if the ticket needs to be transferred to another person, Allegiant typically charges a fee. The exact fee and process can vary, so it\u2019s best
0 views • 5 slides
Quick & Reliable Towing Near Me Gastonia NC
In the world of automobiles, unforeseen circumstances can arise at any moment. Whether it's a flat tire, engine trouble, or an unfortunate collision, finding yourself stranded on the side of the road can be a stressful experience.
2 views • 5 slides
How Do I Change My Passenger Names on Spirit Airlines?
To change the name on your Spirit Airlines flight reservation, follow the Spirit Airlines Name Change Policy. Here's a general guide on how to go about it:\nContact Spirit Airlines: Reach out to Spirit Airlines customer service through phone or online channels.\nExplain the Situation: Clearly explai
4 views • 6 slides
Safety and Responsibility: Transitioning to Secondary School
As students transition to secondary school, they are granted more freedom which comes with added responsibility. This period brings significant changes, including traveling to school independently, using public transport, walking, or cycling. However, there are risks involved, with statistics showin
0 views • 28 slides
Understanding Sediment Provenance in Geology
Sediment provenance in geology involves reconstructing the origin of sediments through compositional analyses to determine erosion history and geographical origins. It helps characterize the journey of sediments from source to sink, providing insights into tectonic and paleoclimatic histories. Prove
2 views • 11 slides
Spectrum Sensing for Enhanced Channel Access in Wireless Networks
This document presents a proposal for Spectrum Sensing Based Deferral (SSBD) to improve channel access in wireless networks. SSBD incorporates spectrum sensing with transmission deferral in a time-bound manner to enhance performance, reliability, and latency control. The proposed solution safeguards
1 views • 11 slides
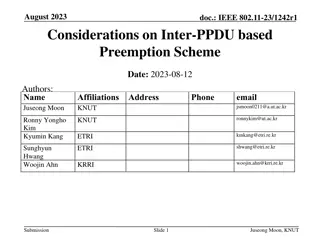
Considerations on Inter-PPDU Based Preemption Scheme in IEEE 802.11-23
In this document, considerations are presented for a preemption scheme in IEEE 802.11-23, focusing on issues such as coordination, ACK transmission timing, and channel access fairness. The proposed inter-PPDU based preemption scheme aims to improve the transmission of low latency traffics within the
1 views • 12 slides
Mechanism Proposal to Avoid IRM Conflicts in IEEE 802.11 Networks
This document presents a proposal to tackle IRM collision and conflict issues in IEEE 802.11 networks, particularly focusing on addressing scenarios where multiple non-AP STAs select the same IRM. The document outlines the importance of avoiding IRM conflicts, introduces the concept of IRM Recap, an
0 views • 12 slides
Understanding Generic Drugs and Brand Name Medications
Generic drugs are identical copies of brand-name medications in dosage, strength, quality, and intended use. They contain the same active ingredients but are sold under their chemical name. This article explores the basic differences between generic and brand-name drugs, when generic drugs are marke
0 views • 20 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Autonomous Obstacle Avoidance Robot Using ROS, Lidar, and Raspberry Pi with Matlab Path Planning
Obstacle avoidance in robotics has evolved from basic collision avoidance to autonomous path planning with the use of Lidar and ROS. This project involves mapping the environment using Lidar scans and implementing a path planning algorithm in Matlab to navigate around obstacles. By utilizing a Raspb
0 views • 15 slides
Advanced Emergency Braking System (AEBS) Definition and Activation Guidelines
The provided content outlines the definition and activation requirements of the Advanced Emergency Braking System (AEBS). It covers the phases involved, including Collision Warning and Emergency Braking, as well as the speed limitations for activation. The system aims to automatically detect potenti
0 views • 12 slides
Physics Collision Problems Explained
Explore various collision scenarios involving bullets, blocks, cars, and people in this physics problem set. Calculate velocities, masses, and recoils to understand the dynamics of collisions and their effects on different objects involved.
0 views • 15 slides
The Story of How a PC Got Its Name
A PC on a network without a name sends out a DHCP request to get a unique name. The message is duplicated by a switch and reaches the DHCP server, which assigns the PC a new name: 10.0.0.3. The server also provides information about the network setup and offers to forward messages to the outside wor
0 views • 26 slides
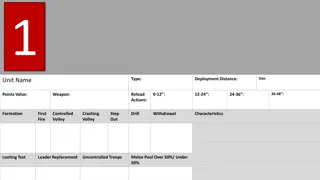
Unit Name Details and Specifications
Explore the details and specifications of various units including deployment distance, size, weapon details, actions, and characteristics for Unit Name 1, Unit Name 2, Unit Name 3, and Unit Name 4. Each unit has its own unique attributes and is depicted with an image for reference.
0 views • 8 slides
Understanding Botanical Names and Common Plant Names
Botanical names consist of a generic name and a specific name, with the first letter of the generic name capitalized and the specific name in lowercase. These names should be underlined or italicized when in prints. Plants also have common and vernacular names that vary by locality, culture, and tri
0 views • 162 slides
Understanding the Dynamics of Collision: Bug vs. Windshield
Explore the intriguing physics behind a bug hitting a windshield, delving into concepts like Newton's third law, momentum conservation, and the differences in force, time of impact, and change in velocity. Discover why a bug goes splat while a windshield remains intact in a collision scenario, with
0 views • 19 slides
Drone Collision Avoidance Simulator for Autonomous Maneuvering
Our project focuses on developing a drone collision avoidance simulator using NEAT and Deep Reinforcement Learning techniques. We aim to create a model that can maneuver obstacles in a 2D environment, enhancing performance and survivability. Previous attempts utilizing non-machine learning solutions
0 views • 28 slides
Advanced Techniques in Collider Physics for Enhanced Luminosity
Explore cutting-edge research on beam-beam effects, crab waist colliders, and luminosity optimization in collider physics. Discover how innovative strategies like crab waist technology and bunch crabbing mitigation are revolutionizing particle collision studies. Dive into the complexities of achievi
0 views • 10 slides
Understanding the Relationship between Decisional Second-Preimage Resistance and Preimage Resistance in Cryptographic Hash Functions
This work delves into the subtle question of when Decisional Second-Preimage Resistance (SPR) implies Preimage Resistance (PRE) in hash functions. It presents a tool for enabling tight security proofs for hash-based signatures by exploring the success probability of adversaries against collision res
0 views • 25 slides
Foundations of Cryptography: Digital Signatures and Collision-Resistant Hash Functions
Foundations of Cryptography explores the construction of digital signature schemes and collision-resistant hash function families using one-way functions and safe primes. The content delves into the concept of collision-resistant hash functions and their construction from the discrete logarithm prob
0 views • 31 slides
Foundations of Cryptography: Lecture 12 - Digital Signatures and Collision-Resistant Hash Functions
The lecture covers the construction of collision-resistant hash functions from discrete log, the security behind it, and the implications for digital signature schemes. It delves into the theoretical foundations of cryptography, showcasing the interplay between one-way functions, hash functions, and
0 views • 25 slides
Comprehensive Overview of CSE 373 Data Structures and Algorithms Course - Autumn 2018
This document provides detailed information about the CSE 373 Data Structures and Algorithms course in Autumn 2018, presented by Shrirang (Shri) Mare. It covers topics such as hashing, collision strategies, hash tables, design decisions, testing, and more. The content includes announcements, midterm
0 views • 25 slides
Privacy Address Requirements for Wireless Personal Area Networks
This document discusses the privacy address requirements for IEEE P802.15 Working Group's TG4ab standard for Wireless Personal Area Networks (WPANs). It covers the need for 48-bit addresses with collision resistance, the use of different privacy addresses for each frame, and the adequacy of 12-bit c
0 views • 8 slides
Understanding TCAS - Traffic Collision Avoidance System
A Traffic Collision Avoidance System (TCAS) is a vital aircraft collision avoidance technology that helps reduce mid-air collisions by monitoring the airspace around an aircraft. TCAS operates independently of ground-based equipment and advises pilots on potential conflicting aircraft. Mandated by t
0 views • 13 slides
Vehicle Safety Protocols: Handling Tire Blows, Brake Failure, and More
Learn essential actions for handling emergencies like tire blowouts, brake failure, stuck accelerator, and steering failure. Additionally, understand off-road recovery, minimizing damage due to potholes, and escaping from a sinking vehicle. Discover collision avoidance techniques and steps to take i
0 views • 9 slides
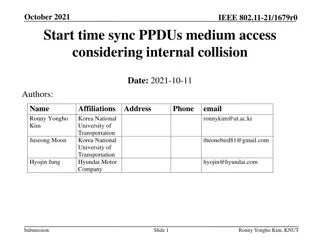
Understanding Start Time Sync Procedures in IEEE 802.11-21/1679r0
In the document authored by Ronny Yongho Kim et al., the focus is on start time sync PPDU medium access considering internal collision in IEEE 802.11-21/1679r0. It discusses the importance of defining a clear rule to resolve internal collision cases during medium access procedures. Specific attentio
0 views • 9 slides
Understanding Hash Tables and Hashing Concepts in Computer Algorithms
This content delves into the concept of Hash Tables, covering topics such as the support for dictionary operations, achieving constant time through direct address tables, case studies in web server maintenance, and an exploration of hashing functions and collision avoidance. It also touches upon key
0 views • 40 slides
MitM Attack by Name Collision: Implications and Vulnerability Assessment
In this research study, the authors delve into the risks and vulnerabilities associated with Man-in-the-Middle (MitM) attacks exploiting name collision in the era of new generic Top-Level Domains (gTLDs). The study highlights how attackers can intercept web traffic by manipulating vulnerable domains
0 views • 25 slides
Name Badge Maker by BadgeMachine
Design your own name badges maker with your name, title and logo. Choose the desired colour, shape and size for your name tag, Easy to design name badge. Contact us on 03 9793 6260 for custom name badges.
1 views • 8 slides