Chemistry of Natural Products - MPC-104T
Learn about the structural elucidation of camphor, a white crystalline substance derived from the wood of camphor laurel and other related trees. Discover its chemical properties, uses, and references for further study.
2 views • 7 slides
WHICH IS THE BEST JUNIOR COLLEGE IN VIZAG FOR INTERMEDIATE MPC
WHICH IS THE BEST COLLEGE IN VIZAG FOR INTERMEDIATE MPC?#bestcollege\n#vizageducation\n#mpccourses#trending\n\nAre you a student looking for the best college in Vizag to pursue Intermediate MPC? Look no further, Manasa Junior College is the top choice for aspiring students in Vizag. With a proven tr
4 views • 1 slides
Understanding ADER Offset and MPC/LPC Information
Explore the concept of ADER Offset and MPC/LPC information for energy resources, focusing on response capabilities, net power flow, and offset applications. Examples illustrate how the ADER is managed with and without offsets, alongside bid strategies in energy markets.
2 views • 6 slides
SRI SARASWATHI JUNIOR COLLEGE, BANJARA HILLS, HYDERABAD
At Sri Saraswathi Junior College, we strive to create a safe and nurturing environment where students can learn and grow. Our faculty members are highly qualified and experienced, and they are committed to providing our students with the best possible education.\n\nWe offer a wide range of programs,
1 views • 2 slides
Building a Macrostructural Standalone Model for North Macedonia: Model Overview and Features
This project focuses on building a macrostructural standalone model for the economy of North Macedonia. The model layout includes a system overview, theory, functional forms, and features of the MFMSA_MKD. It covers various aspects such as the National Income Account, Fiscal Account, External Accoun
2 views • 23 slides
NAMI Family Support Group Model Overview
This content provides an insightful introduction to the NAMI family support group model, emphasizing the importance of having a structured model to guide facilitators and participants in achieving successful support group interactions. It highlights the need for a model to prevent negative group dyn
6 views • 23 slides
RBI
Reserve Bank of India(RBI)\nThe Reserve Bank of India(RBI) is the Controlling Institution of all Banks in India. It is formed by an Act. It\u2019s owned by the Indian government\u2019s Finance Ministry and takes care of things like inflation, interest rates, lending, and ensuring the financial stab
1 views • 5 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Understanding Entity-Relationship Model in Database Systems
This article explores the Entity-Relationship (ER) model in database systems, covering topics like database design, ER model components, entities, attributes, key attributes, composite attributes, and multivalued attributes. The ER model provides a high-level data model to define data elements and r
0 views • 25 slides
Communication Models Overview
The Shannon-Weaver Model is based on the functioning of radio and telephone, with key parts being sender, channel, and receiver. It involves steps like information source, transmitter, channel, receiver, and destination. The model faces technical, semantic, and effectiveness problems. The Linear Mod
0 views • 8 slides
Enhancing Privacy in Crowdsourced Spectrum Allocation
This research focuses on protecting privacy in crowdsourced spectrum allocation, addressing the security challenges faced due to the presence of multiple entities and the sensitive information collected. By proposing potential ideas like Fully Homomorphic Encryption (FHE) and Secure Multi-Party Comp
0 views • 26 slides
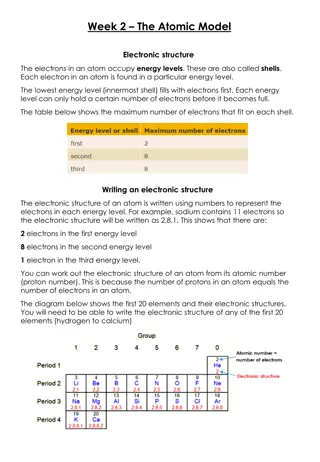
Understanding Atomic Structure: Electrons, Energy Levels, and Historical Models
The atomic model describes how electrons occupy energy levels or shells in an atom. These energy levels have specific capacities for electrons. The electronic structure of an atom is represented by numbers indicating electron distribution. Over time, scientists have developed atomic models based on
0 views • 5 slides
Understanding Fiscal Policy to Combat Recessions
Explore the role of fiscal policy in fighting recessions through stimulating aggregate demand, using government spending and tax cuts. Learn about the Keynesian multiplier effect, MPC, and different policy responses to economic fluctuations. Discover how government interventions can help stabilize t
0 views • 47 slides
Understanding Marginal Propensity to Consume and Save
Marginal Propensity to Consume (MPC) and Marginal Propensity to Save (MPS) measure the ratios of change in consumption and saving to change in disposable income respectively. The relationship between MPC and MPS shows that they equal 1 when combined, with the remainder being saved. The multiplier ef
7 views • 5 slides
Understanding ROC Curves and Operating Points in Model Evaluation
In this informative content, Geoff Hulten discusses the significance of ROC curves and operating points in model evaluation. It emphasizes the importance of choosing the right model based on the costs of mistakes like in disease screening and spam filtering. The content explains how logistical regre
7 views • 11 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
Understanding Keynesian Consumption and Savings Functions in Macroeconomics
Keynesian Consumption Function relates total consumption to national income, with stable characteristics like MPC and APC. Savings Function shows the relationship between savings and income, highlighting the Marginal Propensity to Save and Average Propensity to Save. Both functions are essential con
0 views • 6 slides
Understanding the OSI Model and Layered Tasks in Networking
The content highlights the OSI model and layered tasks in networking, explaining the functions of each layer in the OSI model such as Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. It also discusses the interaction between l
1 views • 41 slides
Regression Diagnostics for Model Evaluation
Regression diagnostics involve analyzing outlying observations, standardized residuals, model errors, and identifying influential cases to assess the quality of a regression model. This process helps in understanding the accuracy of the model predictions and identifying potential issues that may aff
1 views • 12 slides
Insights on Environmental Security and Ingenuity
In this tribute to Ran Canetti, insights are shared on environmental security, ingenuity, and secure multi-party computation (MPC). The discussion delves into the essence of ingenuity, addressing why some may misunderstand discoveries. Furthermore, the concept of environmental security and its pivot
0 views • 11 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
MFMSA_BIH Model Build Process Overview
This detailed process outlines the steps involved in preparing, building, and debugging a back-end programming model known as MFMSA_BIH. It covers activities such as data preparation, model building, equation estimation, assumption making, model compilation, and front-end adjustment. The iterative p
0 views • 10 slides
Efficient Multi-Party Computation Techniques
Explore the innovative approaches to Multi-Party Computation (MPC) such as MPC via Fully Homomorphic Encryption (FHE) and Multi-Key FHE. The focus is on minimizing round complexity and achieving secure distributed computations. Learn about key concepts, protocols, and advancements in the realm of MP
0 views • 17 slides
Proposal for Radio Controlled Model Aircraft Site Development
To establish a working relationship for the development of a site suitable for radio-controlled model aircraft use, the proposal suggests local land ownership with oversight from a responsible agency. Collins Model Aviators is proposed as the host club, offering site owner liability insurance throug
0 views • 20 slides
UBU Performance Oversight Engagement Framework Overview
Providing an overview of the UBU Logic Model within the UBU Performance Oversight Engagement Framework, this session covers topics such as what a logic model is, best practice principles, getting started, components of the logic model, evidence & monitoring components, and next steps. The framework
0 views • 33 slides
Massively Parallel Algorithm for Minimum Weight Vertex Cover
Massively Parallel Computation (MPC) model for solving the Minimum Weight Vertex Cover problem efficiently, including optimal round complexities and known approximation ratios. The algorithm is designed for graphs with vertices and edges, with each machine processing data synchronously in rounds. Va
0 views • 13 slides
Regression Model for Predicting Crew Size of Cruise Ships
A regression model was built to predict the number of crew members on cruise ships using potential predictor variables such as Age, Tonnage, Passenger Density, Cabins, and Length. The model showed high correlations among predictors, with Passengers and Cabins being particularly problematic. The full
0 views • 16 slides
Exact Byzantine Consensus on Undirected Graphs: Local Broadcast Model
This research focuses on achieving exact Byzantine consensus on undirected graphs under the local broadcast model, where communication is synchronous with known underlying graphs. The model reduces the power of Byzantine nodes and imposes connectivity requirements. The algorithm involves flooding va
0 views • 7 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
Calibration of Multi-Variable Rainfall-Runoff Model Using Snow Data in Alpine Catchments
Explore the calibration of a conceptual rainfall-runoff model in Alpine catchments, focusing on the importance of incorporating snow data. The study assesses the benefits of using multi-objective approaches and additional datasets for model performance. Various aspects such as snow cover, groundwate
0 views • 16 slides
Understanding Asp.Net Core MVC - Building Web Applications with Model-View-Controller Pattern
Asp.Net Core MVC is a framework for building web applications based on the Model-View-Controller pattern. The model manages application data and constraints, views present application state, and controllers handle requests and actions on the data model. Learn about the MVC structure, life cycle, mod
0 views • 22 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Foundations of Cryptography: Secure Multiparty Computation
Explore the foundations of cryptography with insights into secure multiparty computation, including the Secure 2PC from OT Theorem and the Two-Party Impossibility Theorem. Delve into the impossibility of 2-Party Secure MPC, claims, and exercises on extending to statistical security. Learn about redu
0 views • 39 slides
Understanding X-CAPM: An Extrapolative Capital Asset Pricing Model
This paper discusses the X-CAPM model proposed by Barberis et al., which addresses the challenges posed by investors with extrapolative expectations. The model analytically solves a heterogeneous agents consumption-based model, simulates it, and matches various moments. It explores how rational inve
0 views • 23 slides
Innovation and Social Entrepreneurship Initiatives in Higher Education
This project focuses on establishing a leading center for promoting innovation and social entrepreneurship within higher education institutions. It aims to encourage students and staff to develop creative solutions for community challenges, expand social involvement, and foster sustainable positive
0 views • 13 slides
Principles of Econometrics: Multiple Regression Model Overview
Explore the key concepts of the Multiple Regression Model, including model specification, parameter estimation, hypothesis testing, and goodness-of-fit measurements. Assumptions and properties of the model are discussed, highlighting the relationship between variables and the econometric model. Vari
0 views • 31 slides
Cognitive Model of Stereotype Change: Three Models Explored
The Cognitive Model of Stereotype Change, as researched by Hewstone & Johnston, delves into three key models for altering stereotypical beliefs: the bookkeeping model, the conversion model, and the subtyping model. These models suggest strategies such as adding or removing features to shift stereoty
0 views • 58 slides
Communication Steps for Parallel Query Processing: Insights from MPC Model
Revealing the intricacies of parallel query processing on big data, this content explores various computation models such as MapReduce, MUD, and MRC. It delves into the MPC model in detail, showcasing the tradeoffs between space exponent and computation rounds. The study uncovers lower bounds on spa
0 views • 25 slides
Secure Computation Lecture Recap and Solutions
Lectures 19-20 by Arpita Patra cover secure computation, with a focus on perfect MPC in a malicious setting, VSS, multiplication protocols, Yao's 2-party protocol, and solutions to identified problems for garbled circuits construction and evaluation.
0 views • 8 slides
Enhancing Federal Procurement Standards Through Past Performance Documentation
Proposal to add a FAR Subpart 42.15-like section to the MPC for recording Contractor Performance Information, in alignment with OMB guidance in 2 CFR Part 200. The history and importance of past performance evaluation in federal grants and agreements are highlighted, emphasizing the need for a struc
0 views • 13 slides