Mobile App Security What’s Your Contingency Plan Safeguard Your Users
In today\u2019s digital landscape, where mobile apps hold a treasure trove of personal information, mobile app security is no longer an afterthought; it\u2019s a paramount concern. As a leading provider of best mobile app creation services in Arizona, we at Net-Craft are committed to helping you nav
2 views • 3 slides
Mobile App Development service In Chennai - Webdads2U PRIVATE LIMITED
Looking for professional and reliable mobile app development services in Chennai? Look no further than Webdads2U. We are a top-rated mobile app development company dedicated to creating innovative and user-friendly mobile applications for businesses of all sizes.\n\nAt Webdads2U, we have a team of s
2 views • 6 slides
How Long Does It Really Take To Develop a Mobile App
Developing a successful mobile app is an exciting yet intricate process. By understanding the various factors at play and the development life cycle, you can gain a clearer picture of the timeframe involved. At Net-Craft.com, your trusted mobile app development partner in Arizona, we\u2019re here to
1 views • 3 slides
Latest Innovations in Mobile App Development Shaping the Future in Scottsdale
The mobile app development landscape is constantly evolving, driven by cutting-edge technologies and ever-changing user demands. Here at Net-Craft.com, a leading mobile app development company in Scottsdale Arizona, we stay at the forefront of these advancements, crafting future-proof apps that elev
2 views • 4 slides
Mobile Game Development Services - Osiz Technologies
In this presentation, Osiz unveils our top mobile game development services. We'll explore the future of mobile gaming and its exciting trends. Finally, discover the benefits of mobile gaming for players and businesses. Join us to unlock the potential of mobile gaming and bring your vision to life.\
3 views • 11 slides
Why Choose a Mobile App Development Company from Arizona for Your Business Needs
In today\u2019s digital age, having a mobile app can be a game-changer for businesses. It allows you to reach a wider audience, enhance customer engagement, and streamline operations. But with a plethora of mobile app development companies vying for your attention, choosing the right partner can be
1 views • 3 slides
B2B Mobile App Development
Travelopro is a top-notch b2b mobile app development company, building feature-packed and interactive b2b mobile applications for startups, medium and large enterprises. Our cutting-edge and out-of-the-box approach will deliver cost-effective b2b mobile app development solutions to turn your busines
2 views • 15 slides
Convenient Prepaid Recharges at Your Fingertips with payRup
Experience the convenience of prepaid recharges with payRup. Effortlessly recharge your Airtel prepaid plans, BSNL recharge, or Jio prepaid mobile recharge with just a few clicks. payRup offers seamless solutions for Airtel recharging, Jio recharge, and Vodafone Idea recharge, making mobile online r
0 views • 1 slides
Enhance Your Career with a Mobile Marketing Course in Delhi
If you're looking to advance your career in the ever-evolving digital landscape, enrolling in a Mobile Marketing Course in Delhi is a strategic move. The capital city hosts several prestigious Mobile Marketing Institutes in Delhi , offering comprehensive training programs designed to equip you with
0 views • 10 slides
5 Must-Have Features for Your Ecommerce Mobile App
Developing robust mobile apps can have a dramatic impact on a retailer\u2019s business if they are equipped with the right capabilities \u2013 leading to higher engagement and loyalty while retaining or improving the revenue, and greatly reducing the costs. But always keep the needs of your users in
1 views • 5 slides
Best service for Mobile Car Detailing in Orem
Robbins Car Detailing & Mobile Detailing provides the Best service for Mobile Car Detailing in Orem. They bring unparalleled attention to you and your vehicle, using specialized tools and products from around the globe to enhance your experience. Their mission is to change the way you think about ca
1 views • 6 slides
Best Mobile App Development Company Pune | Appristine Technologies
Appristine Technologies stands out as the best mobile app development company Pune. Our skilled developers create robust and user-friendly mobile applications tailored to your specific requirements. Experience top-notch mobile app development services that boost your business growth and engagement.
1 views • 2 slides
Best Mobile App Development Company Pune | Appristine Technologies
Appristine Technologies stands out as the best mobile app development company Pune. Our skilled developers create robust and user-friendly mobile applications tailored to your specific requirements. Experience top-notch mobile app development services that boost your business growth and engagement.
1 views • 2 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Understanding Mobile Communication and Networks in Physics
Utilizing mobile phones for communication has become essential in modern society. This article delves into the technology behind mobile communication, including network infrastructure, codes associated with mobile phones, and communication protocols. Explore how mobile devices connect wirelessly and
6 views • 19 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
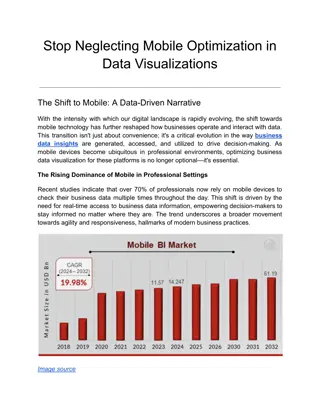
Stop Neglecting Mobile Optimization in Data Visualizations
Explore why mobile optimization is critical for your data visualizations in our latest blog. We delve into the transformative benefits of making your business data insights accessible and intuitive on mobile devices, enhancing decision-making and user engagement. Discover actionable strategies to br
0 views • 8 slides
COMET: Code Offload by Migrating Execution - OSDI'12 Summary
The research paper discusses COMET, a system for transparently offloading computation from mobile devices to network resources to improve performance. It outlines the goals of COMET, its design, and evaluation, focusing on distributed shared memory and bridging computation disparity through offloadi
0 views • 31 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Omnispace: Redefining Global Mobile Connectivity with 5G NTN Technology
Omnispace, launching in December 2022, introduces the world's first global hybrid mobile network using 5G NTN technology to revolutionize mobile connectivity for consumer, enterprise, government, and IoT users. The innovative 5G hybrid architecture combines global NGSO coverage and mobile network ro
0 views • 10 slides
Enhancing Mobile-Cloud Computing with Autonomous Agents Framework
Autonomous Agents-based Mobile-Cloud Computing (MCC) refers to moving computing tasks to powerful centralized platforms in the cloud, offering advantages like extending battery life and dynamic resource provisioning. However, an inflexible split of computation between mobile and cloud platforms lead
0 views • 22 slides
Enhancing Multi-Party Computation Efficiency Through ORAM Techniques
Explore the realm of efficient random access in multi-party computation through the reevaluation of classic schemes and the introduction of new approaches. Discover the potential of ORAM in improving performance and reducing costs in various computational tasks, such as secure multi-party computatio
0 views • 22 slides
Exploring Secure Computation in the Age of Information
Welcome to Secure Computation Lecture 1 by Arpita Patra. The course covers evaluation policies, projects, and references in the realm of secure computation. The content delves into the significance of information security across various sectors, emphasizing the importance of safeguarding sensitive d
0 views • 36 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
Introduction to Mobile Computing Principles and Designing Mobile Applications
Mobile computing systems involve computing capabilities that can be utilized while on the move, leveraging wireless connectivity, small size, and mobile-specific functionalities. The history of mobile computing traces back to military origins and has evolved with technologies like GPS and wireless t
0 views • 98 slides
Secure Computation Challenges and Solutions in Data Mining
Exploring the intersection of secure computation and data mining, this content uncovers key challenges such as improving algorithms, converting programs for secure computation, and addressing parallelizability issues. It highlights the importance of cryptography in ensuring data privacy and presents
0 views • 30 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Overview of Turing Machines: Introduction, Tape, and Computation
Turing Machines are fundamental in the theory of computation, capable of recognizing all computable languages. They consist of a Finite State Machine combined with an infinite tape. The tape is initialized with input on the left end, and a TM's computation can either halt by entering special accept
0 views • 29 slides
Computation for Real Estate Sector in Bangalore Branch of ICAI
Practical overview of GST computation for real estate transactions in Bangalore, with details on old rates with ITC and new rate regime effective from April 1, 2019. The content discusses different transactions, conditions for new rates without ITC, and provides insights on the 80:20 computation met
0 views • 39 slides
Fides: A System for Verifiable Computation Using Smart Contracts
Fides presents a system for verifiable computation using smart contracts, focusing on blockchain basics, Ethereum, smart contracts, and outsourcing computation. It explores key components of blockchain, Ethereum's decentralized computing platform, properties of smart contracts, and the concept of ve
0 views • 25 slides
Exploring the World of Mobile Computing
Delve into the realm of mobile computing through this comprehensive presentation outline. Discover what mobile computing is, its applications, challenges, and the future of this technology. Compare mobile networks to wired networks, understand why going mobile is essential, and explore various types
0 views • 106 slides
Guide to Mobile User Experience Design Choices & Platform Selection
Explore platform choices, deciding between responsive websites and native mobile apps, and rethinking mobile web concepts in this comprehensive guide to designing user experiences for mobile. Learn about the benefits of both responsive websites and native mobile apps, and understand the importance o
0 views • 9 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Overview of Income Computation and Disclosure Standards (ICDS)
The Income-tax Act, 1961 introduced Income Computation and Disclosure Standards (ICDS) to be followed by certain assesses for computation of income. ICDS applies to taxpayers using the mercantile system of accounting from the Assessment Year 2016-17 onwards. Non-compliance with ICDS can lead to Best
0 views • 49 slides
Blackbox Verifiable Computation Scheme Overview
This summarized content discusses the concept of blackbox verifiable computation, focusing on the challenges faced by clients and servers, the role of helper oracles, positive results utilizing homomorphic encryption, and background information on Random Self Reducible (RSR) functions. The protocol
0 views • 20 slides
Parallel Computation for Matrix Multiplication
Matrix multiplication is a fundamental operation with diverse applications across scientific research. Parallel computation for matrix multiplication involves distributing the computational workload over multiple processors, improving efficiency. Different algorithms have been developed for multiply
0 views • 36 slides
Advanced Techniques in Multi-Party Computation
Explore cutting-edge methods in Multi-Party Computation (MPC), including leveraging Fully Homomorphic Encryption (FHE) for minimal round complexity, constructing MPC directly via FHE techniques, and simplifying multi-key FHE constructions for efficient decryption. Learn about key concepts such as di
0 views • 17 slides