Public key encryption, Digital signature and authentication
Understand the concept of public key encryption, asymmetric encryption, and the widely used RSA algorithm. Explore how public key cryptography revolutionized the field of encryption and its applications in confidentiality, authentication, and key distribution.
4 views • 12 slides
Understanding Memory Allocation in Operating Systems
Memory allocation in operating systems involves fair distribution of physical memory among running processes. The memory management subsystem ensures each process gets its fair share. Shared virtual memory and the efficient use of resources like dynamic libraries contribute to better memory utilizat
1 views • 233 slides
Understanding Memory Organization in Computers
The memory unit is crucial in any digital computer for storing programs and data. It comprises main memory, auxiliary memory, and cache memory, each serving different roles in data storage and retrieval. Main memory directly communicates with the CPU, while cache memory enhances processing speed by
1 views • 37 slides
Understanding Memory Organization in Computers
Delve into the intricate world of memory organization within computer systems, exploring the vital role of memory units, cache memory, main memory, auxiliary memory, and the memory hierarchy. Learn about the different types of memory, such as sequential access memory and random access memory, and ho
0 views • 45 slides
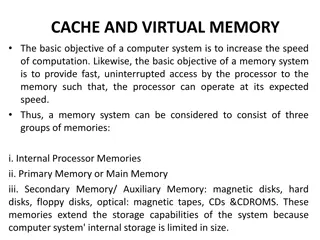
Understanding Cache and Virtual Memory in Computer Systems
A computer's memory system is crucial for ensuring fast and uninterrupted access to data by the processor. This system comprises internal processor memories, primary memory, and secondary memory such as hard drives. The utilization of cache memory helps bridge the speed gap between the CPU and main
1 views • 47 slides
Understanding AES Encryption Algorithm and Its Implementation
Learn about the Advanced Encryption Standard (AES) algorithm - a NSA-approved NIST standard encryption method. Explore how AES works, its key rounds, SubBytes, ShiftRows, MixColumns operations, and its optimization for embedded systems and small memory devices. Discover the importance of secure cryp
0 views • 14 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Dynamic Memory Allocation in Computer Systems: An Overview
Dynamic memory allocation in computer systems involves the acquisition of virtual memory at runtime for data structures whose size is only known at runtime. This process is managed by dynamic memory allocators, such as malloc, to handle memory invisible to user code, application kernels, and virtual
0 views • 70 slides
Understanding Memory Management in Operating Systems
Dive into the world of memory management in operating systems, covering topics such as virtual memory, page replacement algorithms, memory allocation, and more. Explore concepts like memory partitions, fixed partitions, memory allocation mechanisms, base and limit registers, and the trade-offs betwe
1 views • 110 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs accessing a common memory, leading to challenges like the cache coherence problem. This article delves into different types of shared memory architectures, such as UMA and NUMA, and explores the cache coherence issue and protocols. It also highlights
2 views • 27 slides
Understanding Memory Management and Swapping Techniques
Memory management involves techniques like swapping, memory allocation changes, memory compaction, and memory management with bitmaps. Swapping refers to bringing each process into memory entirely, running it for a while, then putting it back on the disk. Memory allocation can change as processes en
0 views • 17 slides
Security with Functional Re-Encryption in Cryptography
Exploring the concept of functional re-encryption from the perspective of security in encryption schemes lies between CPA and CCA security levels. The work done by Yevgeniy Dodis, Shai Halevi, and Daniel Wichs delves into how functional re-encryption can enhance the security and privacy of encrypted
0 views • 12 slides
Probabilistic Public Key Encryption with Equality Test Overview
An exploration of Probabilistic Public Key Encryption with Equality Test (PKE-ET), discussing its concept, applications, security levels, and comparisons with other encryption schemes such as PKE with Keyword Search and Deterministic PKE. The PKE-ET allows for perfect consistency and soundness in en
3 views • 17 slides
Overview of SMX Algorithm and AES Encryption Standard
The SMX Algorithm presents a fresh approach to the avalanche effect in the Advanced Encryption Standard (AES). Initially developed to overcome the limitations of the Data Encryption Standard (DES), AES boasts improved security and efficiency, supporting key lengths of 128, 192, and 256 bits. The AES
3 views • 19 slides
Understanding Memory Encoding and Retention Processes
Memory is the persistence of learning over time, involving encoding, storage, and retrieval of information. Measures of memory retention include recall, recognition, and relearning. Ebbinghaus' retention curve illustrates the relationship between practice and relearning. Psychologists use memory mod
0 views • 22 slides
The Vital Role of Encryption in Safeguarding the Digital Economy
Encryption plays a crucial role in protecting the digital economy by providing secure communication channels. Professor Peter Swire from Ohio State University emphasizes the need for strong encryption over weak cybersecurity measures. He discusses the history of wiretaps, the shift to strong cryptog
0 views • 15 slides
Improved Encryption Technique for Phase Change Memory (PCM)
Bit flips in Phase Change Memory (PCM) can adversely impact performance, power consumption, and system lifespan. To address this, a write-efficient encryption scheme called DEUCE was developed, which reduced bit flips by 50% and improved speed by 27%. By re-encrypting only modified data, the scheme
0 views • 41 slides
Understanding Encryption: Keys, Algorithms, and Applications
Encryption plays a crucial role in securing data transmission and storage. It involves using keys and algorithms to convert plaintext information into a cipher that can only be deciphered with the correct key. This article explores different encryption methods, such as private and public key encrypt
0 views • 62 slides
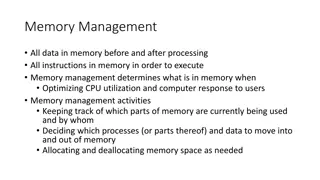
Understanding Memory Management in Computer Systems
Memory management in computer systems involves optimizing CPU utilization, managing data in memory before and after processing, allocating memory space efficiently, and keeping track of memory usage. It determines what is in memory, moves data in and out as needed, and involves caching at various le
1 views • 21 slides
Homomorphic Encryption Overview
Homomorphic encryption allows computation on encrypted data without revealing the underlying information. It enables secure delegation of data processing to a server while maintaining privacy. The process involves key generation, encryption, decryption, and evaluation of functions on encrypted data.
0 views • 40 slides
Bootstrapping in Fully Homomorphic Encryption
Fully Homomorphic Encryption (FHE) allows evaluation of unbounded-depth circuits without being limited by specific parameters. Bootstrapping is a critical technique to achieve full homomorphism by refreshing ciphertexts, enabling decryption functionalities within the encryption scheme. This process
0 views • 38 slides
Dynamic Memory Management Overview
Understanding dynamic memory management is crucial in programming to efficiently allocate and deallocate memory during runtime. The memory is divided into the stack and the heap, each serving specific purposes in storing local and dynamic data. Dynamic memory allocators organize the heap for efficie
0 views • 31 slides
Homomorphic Encryption and RLWE Schemes Overview
Homomorphic encryption allows computation on encrypted data, enabling privacy in outsourced computing services and applications like spam filters for encrypted mail. The Ring Learning With Errors (RLWE) scheme and its properties are discussed, along with symmetric encryption from RLWE and fully homo
0 views • 16 slides
Understanding Unidirectional Updatable Encryption and Proxy Re-Encryption
Unidirectional updatable encryption and proxy re-encryption are key concepts in secure cryptography deployments. Key management and rotation are essential for secure encryption schemes such as Proxy Re-Encryption (PRE) and Updatable Encryption (UE). PRE allows delegation of decryption abilities, whi
0 views • 16 slides
Understanding Memory Basics in Digital Systems
Dive into the world of digital memory systems with a focus on Random Access Memory (RAM), memory capacities, SI prefixes, logical models of memory, and example memory symbols. Learn about word sizes, addresses, data transfer, and capacity calculations to gain a comprehensive understanding of memory
1 views • 12 slides
Understanding Different Types of Memory Technologies in Computer Systems
Explore the realm of memory technologies with an overview of ROM, RAM, non-volatile memories, and programmable memory options. Delve into the intricacies of read-only memory, volatile vs. non-volatile memory, and the various types of memory dimensions. Gain insights into the workings of ROM, includi
0 views • 45 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
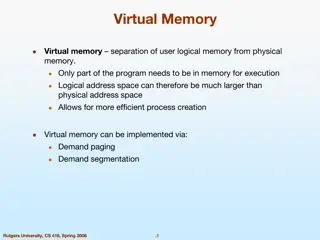
Understanding Virtual Memory Concepts and Benefits
Virtual Memory, instructed by Shmuel Wimer, separates logical memory from physical memory, enabling efficient utilization of memory resources. By using virtual memory, programs can run partially in memory, reducing constraints imposed by physical memory limitations. This also enhances CPU utilizatio
0 views • 41 slides
Understanding Virtual Memory and its Implementation
Virtual memory allows for the separation of user logical memory from physical memory, enabling efficient process creation and effective memory management. It helps overcome memory shortage issues by utilizing demand paging and segmentation techniques. Virtual memory mapping ensures only required par
0 views • 20 slides
Understanding Memory: Challenges and Improvement
Delve into the intricacies of memory with discussions on earliest and favorite memories, a memory challenge, how memory works, stages of memory, and tips to enhance memory recall. Explore the significance of memory and practical exercises for memory improvement.
0 views • 16 slides
Understanding RSA Public-key Cryptography in Data Encryption
Exploring the foundational concepts of RSA public-key cryptography and its applications in data encryption. Learn how messages can be encoded, transmitted securely, and decoded using encryption and decryption functions. Discover the significance of picking large primes and understanding the bijectio
1 views • 12 slides
Understanding RSA Encryption for Secure Communication
Encryption plays a vital role in securing information, and RSA encryption, developed by Rivest, Shamir, and Adleman in 1977, uses public and private keys to safeguard data. Learn about the process, challenges with other encryption methods, prime numbers, and how RSA encryption works step by step.
0 views • 24 slides
Memory Management Principles in Operating Systems
Memory management in operating systems involves the allocation of memory resources among competing processes to optimize performance with minimal overhead. Techniques such as partitioning, paging, and segmentation are utilized, along with page table management and virtual memory tricks. The concept
0 views • 29 slides
Ensuring Orthogonal Security in Data Encryption Processes
Addressing the challenge of data confidentiality in untrusted server environments through the use of encryption techniques such as deterministic and non-deterministic encryption. The goal is to achieve full functionality independently of data encryption, allowing for secure processing of data querie
0 views • 21 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides
Enhancing Memory Bandwidth with Transparent Memory Compression
This research focuses on enabling transparent memory compression for commodity memory systems to address the growing demand for memory bandwidth. By implementing hardware compression without relying on operating system support, the goal is to optimize memory capacity and bandwidth efficiently. The a
0 views • 34 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides
Locality-Aware Caching Policies for Hybrid Memories
Different memory technologies present unique strengths, and a hybrid memory system combining DRAM and PCM aims to leverage the best of both worlds. This research explores the challenge of data placement between these diverse memory devices, highlighting the use of row buffer locality as a key criter
0 views • 34 slides