Pest control in Kolkata
Are you looking for professional pest control services in Kolkata? Socspl.com is here to provide the most reliable and efficient pest control services in Kolkata. We have extensive knowledge and experience in handling all kinds of pest infestations such as termite control, cockroach control, ant con
1 views • 8 slides
Understanding Organizational Control in Business Management
Exploring the concept of control in a business setting, this module delves into the methods, processes, and importance of implementing organizational control. It covers the need for control, different types of control, benefits, and disadvantages, shedding light on how control mechanisms help organi
1 views • 38 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Swing Barrier Gate Entrance Automatic
A swing barrier gate entrance is a type of entrance control system commonly used in areas where security and access control are important, such as office buildings, residential complexes, and public transportation stations. These gates consist of a series of horizontal bars or panels that swing open
0 views • 1 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Mushroom Culture: Preparation of Culture Medium and Edible Mushroom Examples
Mushroom culture involves the preparation of culture medium for cultivating various edible mushrooms. This process includes the systematic classification, structure, and examples of edible mushrooms. The medium preparation methods and materials are essential for successful mushroom cultivation. The
0 views • 24 slides
Understanding Plant Tissue Culture Media and Their Importance in In Vitro Growth
Plant tissue culture media play a crucial role in the in vitro growth and morphogenesis of plant tissues. The composition of culture media depends on the specific plant species and the type of material used for culture. Various types of media, such as White's medium, MS medium, B5 medium, N6 medium,
0 views • 6 slides
Processor Control Unit and ALU Implementation Overview
In Chapter 4, the processor's control unit and ALU are detailed in a simple implementation scheme. The ALU performs operations based on opcode values, while the control unit provides signals for various functions such as load/store, compare, and branch. Decoding techniques and control signal generat
1 views • 21 slides
Asian Pest Control - Professional Pest Management Services in Dhaka
Asian Pest Control offers top-quality pest control services in Dhaka, with a mission to be recognized as the best in the industry. Their highly trained professionals prioritize safety and environmental care while providing services like cockroach control, rodent control, snake repellent, lizard cont
1 views • 16 slides
Basic Computer Organization and Design - Timing and Control
The timing of all registers in a basic computer is governed by a master clock generator, with clock pulses controlling the flip-flops and registers in the system. Two main types of control organization are Hardwired Control and Micro-programmed Control. The former uses digital circuitry like gates a
1 views • 4 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
IEEE 802.11-23/1980r1 Coordinated AP-assisted Medium Synchronization Recovery
This document from December 2023 discusses medium synchronization recovery leveraging multi-AP coordination for multi-link devices. It covers features such as Multi-link device (MLD), Multi-link operation (MLO), and Ultra High Reliability (UHR) capability defined in P802.11bn for improvements in rat
0 views • 8 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
Database Security Measures and Controls
Database security is crucial to protect against threats like loss of integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption are important for safeguarding databases. Access control involves creating user accounts and pass
0 views • 35 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Understanding Marketing Control and Its Importance in Business
Marketing control is a crucial process for firms to evaluate the impact of their marketing strategies and initiatives, making necessary adjustments for better outcomes. It involves various aspects such as annual plan control, profitability control, efficiency control, and strategic control. The proc
0 views • 20 slides
Coordinated AP-Assisted Medium Synchronization Recovery in IEEE 802.11-23/1980r0
This document discusses the proposal for medium synchronization recovery leveraging multi-AP coordination for multi-link devices in IEEE 802.11be EHT networks. It introduces the concept of AP-assisted medium synchronization recovery to assist non-AP STAs in transmitting frames without causing collis
0 views • 7 slides
Understanding Control Plans in Process Management
A Control Plan is vital in controlling risks identified in the FMEA process, focusing on process and product characteristics, customer requirements, and establishing reaction plans for out-of-control conditions. It serves as a central document for communicating control methods and includes key infor
1 views • 20 slides
Medium Turns Flight Training Manual Section 9
Learn how to execute medium turns in flight training, changing direction through 360 degrees at a constant rate while maintaining altitude and balance. Understand the principles of lift, adverse yaw, and overbanking performance involved in medium turns, along with techniques to reduce adverse yaw an
0 views • 25 slides
Best Medium Psychic in Brunswick
Karla Gwendoline - The Happy Medium serves the Best Medium Psychic in Brunswick. Transform confusion into clarity, turn your aspirations for change into tangible reality, and craft the life you were meant to live. This is where your path to a persona
0 views • 6 slides
Collaborative Access Control in Webdamlog System Analysis
In the WebdamLog system, Serge Abiteboul delves into collaborative access control, loss of user control over data, and the need for a Distributed Knowledge Base. Discussing rule-based language, contradictions in data, and Webdamlog+Proba for access control and data management, this exploration sheds
0 views • 28 slides
Understanding Sound: Energy, Pitch, Transmission, and Speed
Sound is a form of energy that travels through a medium by vibrations. It carries intensity and pitch, with frequency determining pitch. Sound requires a medium to travel, unlike light. Elasticity and temperature of the medium affect the speed of sound transmission. Understanding how sound waves pro
0 views • 12 slides
Recombination in Jet Showers: Status and Discussion
This document discusses the status and ongoing research on recombination in jet showers, particularly focusing on the JET Collaboration Meeting at UC Davis in June 2014. Topics covered include in-medium hadronization, jet recombination formalism, application to in-medium shower Monte Carlos, challen
1 views • 24 slides
Achieving Secure and Scalable Data Access Control in Cloud Computing
Cloud computing enables remote data storage and application utilization without local hardware and software management. This paper addresses challenges related to data security and access control in cloud environments, emphasizing the need for fine-grained data access control. It discusses the compl
0 views • 32 slides
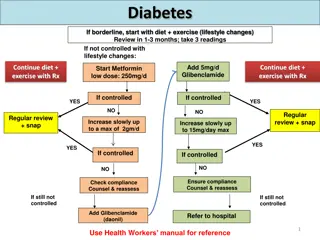
Managing Diabetes, Hypertension, and Cholesterol: Overview of Treatment Guidelines
The guidelines outline step-by-step management strategies for borderline diabetes, hypertension, and cholesterol. For diabetes, lifestyle changes are first recommended, followed by medication if necessary. Hypertension management starts with diet and exercise, then progresses to medication if needed
0 views • 7 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Quarkonium in Medium and Transport in Heavy-Ion Collisions
Discussing the properties and behavior of quarkonium in medium and its transport in heavy-ion collisions. Topics include heavy-quark potential, confinement, quarkonia at finite temperature, quarkonium transport, and quarkonia in heavy-ion collisions. Insightful details about in-medium potential and
0 views • 30 slides
Ultra-Reliable PHY Elements: Optimized Building Blocks for Low Latency and Efficiency
The document presents a deep dive into ultra-reliable PHY elements, focusing on achieving low latency, reduced collision, and energy efficiency. It proposes optimized universal building blocks to address these goals effectively, especially in scenarios where many devices may not receive transmission
0 views • 17 slides
Enhancing Medium Access Efficiency in IEEE 802.11 Networks
This presentation discusses the utilization of chirp signals for Ultra High Rate (UHR) STAs to access the medium efficiently, transmit reliably at reduced power levels, and handle interference challenges in IEEE 802.11 networks. It explores the concept of chirps, their differentiation from other pro
0 views • 20 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Coordinated Medium Access for Multi-AP Deployments in IEEE 802.11 Networks
The document discusses a solution to reduce latency, increase throughput, and improve reliability in networks with latency-sensitive traffic by introducing coordination between access points (APs). This involves leveraging mechanisms like Restricted TWT (rTWT) and Coordinated rTWT (C-rTWT) to facili
0 views • 12 slides
Plant Tissue Culture Techniques: Isolation and Growth
Plant tissue culture involves preparing a suitable nutrient medium, selecting healthy plant explants, sterilizing them, inoculating on solid medium, incubating under controlled conditions, inducing regeneration, and hardening before transferring to greenhouse or field. Various types of cultures can
0 views • 20 slides
Understanding Start Time Sync Procedures in IEEE 802.11-21/1679r0
In the document authored by Ronny Yongho Kim et al., the focus is on start time sync PPDU medium access considering internal collision in IEEE 802.11-21/1679r0. It discusses the importance of defining a clear rule to resolve internal collision cases during medium access procedures. Specific attentio
0 views • 9 slides
Database Access Control & Privacy: A Common Ground Explored
Exploring the intersection of database access control and data privacy, this paper delves into the implications of data privacy concerns on Database Management Systems (DBMS). It discusses the need for more than just access control mechanisms and highlights the evolving landscape of data publishing,
0 views • 29 slides
Effective Regulation of Active Power in Renewable Energy Sources
The balance between generation and load is crucial in power systems operation. Various control levels ensure this balance, from frequency control to power station planning. DER units may lack control means, but specific configurations allow for frequency and voltage control. Performance indicators a
0 views • 51 slides
Understanding Control Plans in Process Management
Control plans are essential tools for managing process risks and ensuring quality control. They focus on controlling process and product characteristics, meeting customer requirements, and having reaction plans in place. A control plan contains key information such as control factors, specifications
0 views • 20 slides