Automated Mobile App QoE Diagnosis with Cross-layer Analysis
This work presents the QoE Doctor, a solution for accurate and repeatable QoE measurements and analysis in mobile apps. By introducing UI automation, it enables the replay of user behavior to measure UI layer QoE metrics without modifying app source code. The QoE Doctor also supports multi-layer dia
3 views • 28 slides
Proposed Approach for MAC Address Assignment in IEEE 802.11
IEEE 802.1CQ is working on a mechanism to assign local MAC address blocks to end nodes specifically related to IEEE 802.11 standards. The current draft lacks a pre-association mechanism for IEEE 802.11 stations to obtain a local MAC address before association. The proposed remedy suggests specifying
8 views • 7 slides
NASA Platform Layer Updates for the CAELUM (7.0) Release
The National Aeronautics and Space Administration (NASA) discusses platform layer updates for the CAELUM (7.0) release of the Core Flight System in the 2021 Flight Software Workshop. The platform layer consists of the Operating System Abstraction Layer (OSAL) and Platform Support Package (PSP), whic
1 views • 20 slides
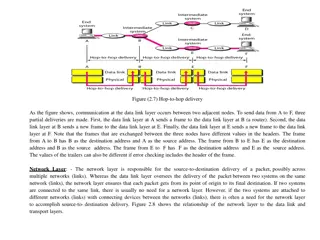
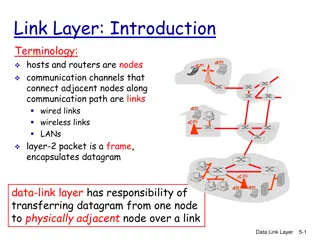
Communication Layers in Computer Networks
Communication in computer networks is facilitated through different layers such as the data link, network, and transport layers. Each layer has specific responsibilities in ensuring data delivery from one point to another. The data link layer handles communication between adjacent nodes, the network
3 views • 7 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
The OSI Model and Layered Tasks in Networking
The content highlights the OSI model and layered tasks in networking, explaining the functions of each layer in the OSI model such as Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. It also discusses the interaction between l
2 views • 41 slides
Enhancing Privacy with Randomized MAC Addresses in 802.11 Networks
This presentation discusses the use of randomized MAC addresses as a privacy-enhancing measure in 802.11 networks. Passive observation of MAC addresses poses privacy risks, and the proposal suggests assigning random MAC addresses to portable devices to mitigate tracking risks. By periodically changi
0 views • 10 slides
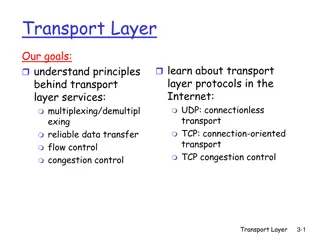
Internet Transport Layer Services and Protocols
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Privacy Issues in IEEE 802.11 Networks: Tracking and MAC Randomization
This presentation delves into the privacy concerns surrounding 802.11 networks, focusing on tracking vulnerabilities and the limitations of MAC randomization in preventing tracking. It discusses the ease of tracking devices, the risk of passive tracking due to MAC addresses being visible in frames,
1 views • 27 slides
IEEE802.15-14-0110-01-0mag MAC Timing Discussion Points for IEEE 802.15.4 Revision
Initial discussion document submitted by Benjamin A. Rolfe from Blind Creek Associates addressing MAC timing issues in the IEEE 802.15.4 standard revision. The document identifies potential problems, provides a list of questions for consideration, and outlines areas for improvement. It includes stat
0 views • 8 slides
ZFS: Structure and Operations
Explore the comprehensive structure and operations of ZFS, covering aspects like MOS layer, object-set layer, Dnode, Block Pointer, and TRIM operations. Learn about the meta-object set (MOS), dataset and snapshot layer (DSL), and storage pool allocator (SPA) modules within ZFS. Understand how ZVOLs,
0 views • 10 slides
Summary of MAC Address Policy Contribution to IEEE 802.11
This document outlines the contribution of MAC address policy to IEEE 802.11, focusing on defining ANQP and Beacon elements to convey information about addressing types supported by the network. It details how specific bits in the ANQP element represent support for various MAC address types includin
0 views • 5 slides
The Planetary Boundary Layer in Atmospheric Science
The Planetary Boundary Layer (PBL) plays a crucial role in atmospheric dynamics, divided into surface, mixed, stable, and residual layers. During the day, the mixed layer experiences convective motions due to surface heating, while the stable layer dominates during the night. Understanding these lay
0 views • 18 slides
Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
This content delves into the concepts of Transport Layer Security (TLS) and Secure Sockets Layer (SSL), exploring their origins, application in web security, and protocol stack integration. It covers the TLS/SSL handshake process, key derivation, data transfer mechanisms, and the significance of the
1 views • 26 slides
Implications of IEEE 802.11 State Machine and MAC Randomization
The document discusses the state machine transitions in IEEE 802.11, focusing on MAC address handling and implications for STA connectivity within an ESS. It explains the scenarios where a STA can use different MAC addresses, emphasizing the binding of state to specific address configurations and th
0 views • 11 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
How to Record Your Voice: A Comprehensive Guide for Windows, Mac, and Smartphones
Learn how to record your voice for ePoster, MP3, or podcasts using Windows 10, Mac, Android, or iPhone/iPad devices. Find step-by-step instructions for recording on different platforms, including using Windows Voice Recorder on a Windows 10 computer and QuickTime Player on a Mac. Discover tips for a
2 views • 10 slides
Mac OS & VoiceOver: A Comprehensive Guide with Belinda Rudinger
Dive into the world of Mac OS and VoiceOver with expert Belinda Rudinger in this detailed tutorial. Learn about screen readers, VoiceOver commands, built-in features, interaction tools, customization options, and useful utilities. Discover how to navigate the Mac ecosystem seamlessly using VoiceOver
0 views • 20 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
1 views • 25 slides
The Migration Advisory Committee Review and Findings
The Migration Advisory Committee (MAC) is an independent advisory body formed in 2007 to provide recommendations to the government on migration issues. The MAC does not create or implement policy but advises through research and analysis in various areas like economics, education, and stakeholder en
0 views • 13 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage, providing structured approaches through the Structured Local Address Plan (SLAP) in different regions of the local MAC address space. Local MAC addresses are not globally unique, and the assignment is within local administration's sc
0 views • 9 slides
ARP, ICMP, and DHCP in TCP/IP Protocol Stack
ARP (Address Resolution Protocol) plays a crucial role in bridging the Layer 2/Layer 3 addressing boundary in the TCP/IP protocol stack, allowing IP to be agnostic about layer 2 addressing while still using layer 2 for packet delivery. Machines ARP for MAC addresses within their local network, where
0 views • 39 slides
Caseous Mitral Valve Calcification (C-MAC) and Stroke: Overview and Management
Caseous Mitral Valve Calcification (C-MAC) is a rare condition characterized by spectrum liquefaction necrosis of the mitral annular calcification (MAC), potentially leading to cardiovascular complications like strokes and emboli. This article discusses the features, diagnostic aspects, and treatmen
0 views • 7 slides
Enhancing MAC Header Protection in IEEE 802.11 Networks
This document discusses the need for improved protection of MAC headers in IEEE 802.11 networks to address security concerns related to certain fields that are currently not adequately protected. It emphasizes the importance of safeguarding vital information in MAC headers to prevent potential attac
0 views • 12 slides
The Link Layer in Computer Communication and Networks
The link layer, an essential component in computer networks, is implemented at every host through adapters like NICs or Ethernet/802.11 cards. It handles tasks such as frame encapsulation, error checking, and flow control to ensure reliable data transmission between nodes. Link layer services includ
0 views • 64 slides
Link Layer in Computer Networking
The link layer, also known as the data link layer, plays a crucial role in transferring data between adjacent nodes over communication links. This layer is responsible for framing, access control, reliable delivery, error detection and correction, flow control, and more. It is implemented in network
0 views • 34 slides
IEEE 802.11-22/0424r1 - MAAD MAC Protocol Overview
The document discusses the MAAD MAC protocol, where the AP assigns a MAAD MAC address to the STA during association. Key differences from other schemes are highlighted, emphasizing the use of MAAD MAC addresses as identification. Details on support indication, address allocation, and recognition mec
0 views • 7 slides
IEEE 802.11-22/0955r0 TGbh Pre-association Schemes Exploration
The document explores the pre-association schemes NGID, MAAD, and IRM within the IEEE 802.11-22 standard. It discusses how the schemes operate, comparing RRCM to MAAD and IRM, and addresses the use of Probes and MAC addresses in pre-association scenarios. The presentation clarifies the allocation of
0 views • 15 slides
Network Security Part 2: Link Layer and ARP
Exploring the vulnerabilities in simple network topologies with hubs and the need for examining the link layer to prevent eavesdropping. Dive into MAC addresses, ARP (Address Resolution Protocol), and how machines translate IP addresses to physical Ethernet addresses. Learn about ARP tables, the tra
0 views • 61 slides
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
Layer 3 Switches: Functionality and Configuration
Layer 3 switches combine the features of Ethernet switches and routers, allowing them to process both MAC and IP headers. By configuring VLANs, trunking, and management interfaces, these switches can handle data forwarding across different subnets efficiently. This guide explains the basic principle
0 views • 19 slides
IEEE 802.11-23/0421r1: Understanding the IRM Scheme for MAC Address Privacy
The document discusses the use of the Same MAC Address (SMA) scheme in IEEE 802.11-23/0421r1 and introduces the Improved Randomized MAC (IRM) scheme as a privacy-enhancing solution. It explores the implementation and benefits of IRM over SMA, addressing issues like privacy requirements, device ident
0 views • 7 slides
Enhancement of Rule-based Random and Changing MAC Proposal in IEEE 802.11-22/1802r0
This document details the enhancements proposed for the Rule-based Random and Changing MAC (RRCM) in IEEE 802.11-22/1802r0. The RRCM concept involves generating Random MAC (RMA) addresses locally to increase security and prevent trackability in wireless networks. Key aspects include RMA generation,
0 views • 12 slides
MAC Address Randomization in IEEE 802.11: Privacy Concerns and Solutions
The document discusses the rise of MAC randomization in IEEE 802.11 networks, addressing motivations, benefits, concerns over privacy implications, and real-life scenarios highlighting the risks associated with passive observation of MAC addresses. It emphasizes the importance of safeguarding privac
0 views • 14 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage and specifies different assignment approaches in four regions of the local MAC address space. Local MAC addresses are not globally unique and can be changed within local administration scope. The SLAP Quadrants and addressing policies
0 views • 9 slides
Atmospheric Boundary Layer Dynamics and Evolution
The atmospheric boundary layer undergoes transformations from a residual layer to a stable boundary layer through the night, impacting wind behavior and turbulence levels. The virtual potential temperature profile provides insights into these changes.
0 views • 8 slides
Chapter 5: DataLink Layer
In the world of computer communication and networks, the DataLink Layer plays a crucial role in ensuring reliable data transfer. This layer deals with link protocols like Ethernet, frame relay, and 802.11, each offering different services and implementations. The link layer is present in every host,
3 views • 59 slides
L4S Support in IEEE 802.11bn Proposal
This proposal aims to enhance IEEE 802.11bn by incorporating Low Latency, Low Loss, and Scalable throughput (L4S) support. The focus is on improving end-to-end latency and ensuring optimal performance through dual-queue Active Queue Management (AQM) at the MAC layer for both stations and access poin
0 views • 7 slides
Medium Access Control (MAC)
Medium Access Control (MAC) in networking focuses on broadcast channels where multiple sources contend for access. The MAC layer manages collision resolution and channel access fairness, impacting throughput and delay. Protocols like ALOHA and CSMA improve channel utilization through methods like ra
0 views • 67 slides