Brigade Calista Bangalore
Brigade Calista is a brand-new, modern residential condominium complex located on one of Bangalore's most sought-after sites. Living in Bangalore's fast growing Old Madras Budigere Cross neighborhood lets you experience the tranquility of lush surroundings every day.
1 views • 2 slides
Threads is a new app by Instagram that lets people share photos, videos, and messages with just their close friends
Threads is a new app by Instagram that lets people share photos, videos, and messages with just their close friends. This makes it different from the regular Instagram app, which is more public-facing. Because Threads is all about close connections, it can be a great tool for marketers to connect wi
6 views • 7 slides
Beach Bliss_ Unveiling the Latest Bikinis and Beachwear at Marlei
For boho babes, crochet swimwear is having a moment. This nostalgic 70s trend is\nrevamped for today. Crochet Biknis Swimwear has intricate openwork stitching. Adding\ntexture and dimension. Crochet swimsuits offer the right coverage yet breathability. The\nopen fabric lets the skin breathe. The loo
1 views • 4 slides
Best Place To Buy Verified PAYEER Accounts 2024
Best Place To Buy Verified PAYEER Accounts 2024\nBuy Verified PAYEER Account\nA verified PAYEER account is critical if you have an online business. A verified PAYEER account lets you send and receive money worldwide quickly and safely. \nIf you any problem please contact me fast 24 Hours Reply\/Cont
0 views • 11 slides
Journey of a Lifetime Chandigarh to Spiti Valley Expedition
Prepare yourself for an adventure like never before in the captivating Spiti Valley. This Spiti Valley tour package takes you through stunning landscapes and lets you explore some of the region's most remarkable sites, including Komik and Hikkim. To learn more , visit \/\/wanderon.in\/trip\/chandiga
7 views • 1 slides
Best Place To Buy Verified PAYEER Accounts 2024
Best Place To Buy Verified PAYEER Accounts 2024\nBuy Verified PAYEER Account\nA verified PAYEER account is critical if you have an online business. A verified PAYEER account lets you send and receive money worldwide quickly and safely.\n24 Hours Reply\/Contact\nEmail: reviewinsta38@gmail.com\nTelegr
0 views • 11 slides
Zipaworld Express Delivery | Fast, Reliable, and Efficient Shipping Solutions
Get your packages delivered quickly and reliably with Zipaworld Express Delivery. We offer fast shipping services that ensure your items arrive on time, every time. Our advanced tracking technology lets you know exactly where your package is always,
2 views • 1 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
2 views • 37 slides
Understanding Sub-Letting in Rental Properties
Assured tenancies come with a statutory prohibition on sub-letting under the Housing Act 1988. If a tenant sub-lets, they breach their contract with the landlord, potentially leading to possession orders. The sub-tenants have a legal status, but the contractual relationship for paying rent lies with
0 views • 18 slides
Alabama State Advisory Group on Juvenile Justice and Delinquency Prevention Orientation
This presentation serves as an orientation for members of the Alabama State Advisory Group on Juvenile Justice and Delinquency Prevention, providing an overview of the group's role in implementing the ADECA LETS Title II Part B Formula Grant Program. Key terms related to juvenile justice are explain
0 views • 19 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Commodities Allowed in Air Freight_ A Comprehensive Overview
Air cargo tracking lets you monitor your air shipment's journey from start to finish. By using a unique tracking number, you can easily see where your package is at any given time, whether it\u2019s in transit, at customs, or has been delivered. This
0 views • 2 slides
Enhancing Supply Chain Efficiency with Advanced Air Waybill Tracking
Tracking lets you monitor the progress of your shipment in real-time. It provides updates on where your package is, whether it\u2019s in transit, at customs, or has been delivered. Air waybill tracking helps you stay informed about the status of your
2 views • 1 slides
Ndutu Migration Calving Safari Adventure
Embark on our 6 Days Ndutu Migration Calving Safari to witness nature's spectacle as thousands of wildebeest and other wildlife give birth. This once-in-a-lifetime experience lets you observe the circle of life in action amid Tanzania's stunning land
2 views • 5 slides
Introduction to Cryptography and Its Applications in Computer Science
Cryptography is the study of methods for sending and receiving secret messages. In this lecture, we explore the design and application of cryptosystems, such as the RSA cryptosystem and Turing's Code. The goal is to securely encrypt and decrypt messages using number theory to protect communication f
1 views • 53 slides
Understanding UserForm in Visual Basic for Applications (VBA)
UserForm in VBA allows customization of user interfaces using standard Windows controls, providing a form similar to a standard Windows form. This tool lets you design forms on a blank canvas by selecting and placing controls from the Toolbox window. Properties of the form, its events, and methods c
0 views • 37 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
Understanding Secure Information Transmission in Cryptography
Explore the concepts of secure information confidentiality, integrity, and authenticity in the realm of cryptography, including digital signatures, signcryption, and the challenges faced in ensuring secure communication. Delve into the attempts to encrypt, authenticate, and solve issues like non-rep
0 views • 23 slides
Crack the Code: A Journey into Transposition Ciphers
Mathematicians play a crucial role in industries like telecommunications and internet companies by condensing data and ensuring error detection. Transposition ciphers, like the Scytale used by Romans, offer a challenging way to encrypt messages. Test your skills with code-breaking challenges and exp
0 views • 4 slides
Client Privacy Preservation through Secured DNS - Feisty Forwarders
Feisty Forwarders, led by Dr. Amrita Mishra, is a team dedicated to client privacy preservation via secured DNS. They focus on developing protocols that hide IP addresses and encrypt all incoming and outgoing traffic to protect users from potential spies on the internet. With expertise in programmin
0 views • 11 slides
Work Opportunities Through Spousal Sponsorship in Canada
If you\u2019re in a loving relationship with a Canadian citizen or permanent resident, spousal sponsorship opens up exciting work opportunities for you. This program lets you live in Canada and apply for an open work permit, which means you can work
0 views • 8 slides
Understanding Virtual Functions and Visitor Pattern in C++
Virtual functions in C++ allow for dynamic polymorphism by defining a set of functions in base classes that can be overridden in derived classes. The visitor pattern is a design pattern that lets you define a new operation without changing the classes of the elements on which it operates. This patte
1 views • 12 slides
How Much Does It Cost To Hire A Full-Time Chef
The cost of hiring a chef depends upon the cost of living. In this blog lets discuss how much does it cost to hire a full-time chef.\n
0 views • 6 slides
Lettings Waltham Forest - Landlord Offer October 2020
Lettings Waltham Forest is a council-based lettings agency established in 2012, with over 40 years of experience in the team. They offer the Market Rent Product, working with landlords to provide quality accommodation to key workers in the borough. Their services include comprehensive credit checks,
0 views • 11 slides
Golden Exchange Are The Oldest And Best Online Sports Betting Site In India
Golden Exchange is your all-time platform or a marketplace that lets you play and place bets on sports cricket, soccer, tennis, live-card, slot-games more games, and other or betting games sport or event to bet on, and place your bet using your uniqu
1 views • 3 slides
PA Dutch 101 - Command Forms
PA Dutch 101 Video 37 covers Command Forms in Pennsylvania Dutch. There are three command forms: Singular, Plural, and Lets. The choice of form depends on the number of people being addressed. The Singular Form is used for one person, the Plural Form for multiple people, and the Lets Form when sugge
0 views • 8 slides
Best Guide to Canada’s Sponsorship Program
Canada\u2019s Family Sponsorship program lets Canadian citizens and permanent residents bring their family members to Canada. If you want to sponsor a spouse, child, parent, or grandparent, this program can help. This guide will explain who can apply
0 views • 8 slides
Benefits of Free SSL with Let's Encrypt for Website Security
Explore the advantages of implementing free SSL with Let's Encrypt for your website security needs. Discover why SSL/TLS encryption is essential to prevent insecure warnings in browsers, enhance search engine rankings, and comply with Apple's secure app requirements. Learn about the pain points asso
0 views • 25 slides
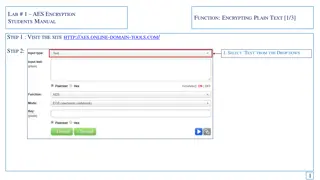
Guide to AES Encryption for Students - Encrypting and Decrypting Text
This manual provides a step-by-step guide on AES encryption for students. Learn how to encrypt plain text using a secure key, generate cipher text, and then decrypt it back to the original message. Follow the instructions on a specific website, enter your text, select encryption options, and save th
0 views • 6 slides
What Your Dream Wedding in Goa Lets Make It Happen with Goa Darling
What Your Dream Wedding in Goa Lets Make It Happen with Goa Darling
0 views • 4 slides
Understanding Loops and ASCII Values in Python
Learn about while loops, fencepost loops, and sentinel loops in Python programming. Explore how ASCII values are assigned to characters and how to manipulate them. Practice a Caesar cipher program to encrypt messages and discover common pitfalls in loop structures. Gain insights into the importance
1 views • 22 slides