Computer Organization and Architecture
A computer system is a programmable digital electronics device that processes data as per program instructions to provide meaningful output. It comprises hardware and software components, with hardware being the physical parts and software essential for driving the hardware. Computer organization fo
15 views • 71 slides
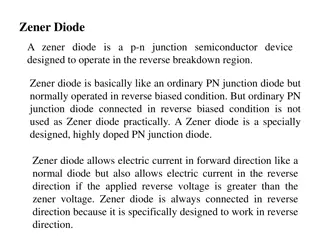
Zener Diodes: Breakdown Mechanisms and Symbol
A Zener diode is a specialized semiconductor device designed to operate in the reverse breakdown region, with two types of breakdown - avalanche and Zener. Avalanche breakdown occurs at high reverse voltages in both normal and Zener diodes, while Zener breakdown is specific to heavily doped P-N junc
9 views • 19 slides
Hip Hop Jewelry: The Sparkling Symbol Of Hip Hop Culture
Hip-Hop culture is renowned for its striking fashion choices, and no element is more emblematic of this than Hip-Hop Jewelry. Featuring everything from expansive chains to pendants laden with diamonds, Hip-Hop Jewelry stands as a potent symbol of sel
1 views • 5 slides
Evolution of IBM System/360 Architecture and Instruction Set Architectures
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing by offering forward and backward compatibility, a unified instruction set architecture (ISA), and a balance between scientific and business efficiency. The critical elements of this architecture
3 views • 18 slides
P&IDs and Symbols in Process Engineering
An insightful primer on P&IDs and symbols for students unfamiliar with EMEC125 and EMEC130 courses. The article delves into the definition of P&IDs as schematic diagrams illustrating the relationship between instruments, controllers, piping, and equipment. It explores the widely understood acronym "
1 views • 32 slides
MIPS CPU Design Using Verilog and Instruction Set Architecture Overview
Explore the world of MIPS CPU design using Verilog with a deep dive into Instruction Set Architecture (ISA), SPIM instruction formats, addressing modes, and more. Learn about the key components such as Program Counter (PC), Instruction Memory (IM), Register Files (RF), Arithmetic Logic Unit (ALU), D
1 views • 29 slides
Mastering Symbol Substitution in Mathematical Operations
In the realm of mathematical operations, understanding symbol substitution is key to solving questions efficiently. Learn how to interchange mathematical signs and symbols to find the correct answer. With examples and guidance, grasp the concept of symbol substitution and excel in tackling such ques
0 views • 25 slides
Texas Senate Bill 792: Disabled Parking Requirements and Penalties
Texas Senate Bill 792, effective January 1, 2022, outlines the requirements for parking in disabled spaces, including the need for a disabled person license plate or a placard featuring the International Symbol of Access (ISA). Veterans with Disabled Veteran plates must also meet specific criteria t
1 views • 10 slides
Instruction Set Architecture and Data Types in Computer Systems
In computer architecture, the Instruction Set Architecture (ISA) level is crucial in defining how a processor executes instructions. This includes the formal defining documents, memory models, registers, and various data types that can be supported. The ISA level specifies the capabilities of a proc
3 views • 13 slides
IBM System/360 Architecture Evolution
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing with its forward and backward compatibility, ISA family concept, and efficient integration of scientific and business applications. The critical elements, including compatibility design consider
0 views • 18 slides
MC-OOK Symbol Design for IEEE 802.11 - March 2018
Introducing MC-OOK waveforms with low peak-to-average power ratio for IEEE 802.11, utilizing 256-QAM modulation and 4 MHz bandwidth. The design methodology involves generating time-domain waveforms, transforming to frequency domain, and proposing symbols with and without DC subcarriers. Detailed sym
0 views • 20 slides
Uncovering Business Models for Linked Government Data
Delve into the exploration of business models for linked government data through a comprehensive study under the European Commission's ISA Programme. Discover key stakeholders, methodologies like the Business Model Canvas, case studies, and the potential value of Linked Open Government Data. Uncover
0 views • 19 slides
Miracles of Prophets: Divine Wonders and Prophetic Signs
Explore the profound significance of miracles in Islam, showcasing the extraordinary events granted by Allah to His Prophets as a testament to their truthfulness and divine approval. Delve into the greatest miracle, the Holy Quran, which offers unparalleled knowledge and insight into the miraculous
2 views • 36 slides
RISC, CISC, and ISA Variations in Computer Science
Explore the differences between RISC and CISC architectures, along with variations in Instruction Set Architecture (ISA). Dive into the intricacies of processor design, performance factors, and assembly languages. Get insights into the concepts of control units, memory units, pipelines, and datapath
0 views • 37 slides
Variations in Computer Architectures: RISC, CISC, and ISA Explained
Delve into the realm of computer architectures with a detailed exploration of Reduced Instruction Set Computing (RISC), Complex Instruction Set Computing (CISC), and Instruction Set Architecture (ISA) variations explained by Prof. Kavita Bala and Prof. Hakim Weatherspoon at Cornell University. Explo
1 views • 55 slides
Symbol Table Management in Program Compilation
Symbol table management is crucial in program compilation as it involves gathering information about names and constants, constructing storage structures, and aiding different phases like lexical and syntactic analysis, semantic analysis, code generation, and error handling. The symbol table serves
0 views • 22 slides
The Story of the Baguette: From Revolution to UNESCO Heritage
The baguette, a famous French stick, has a rich history dating back to the French Revolution. Originating from Vienna, it became a symbol of equality and was even chosen by Napoleon for his soldiers. Today, the baguette remains an iconic part of French cuisine, with millions sold globally each year.
0 views • 5 slides
Practical Implementation of Embedded Shadow Page Tables for Cross-ISA System Virtual Machines
This research focuses on the practical implementation and efficient management of embedded shadow page tables for cross-ISA system virtual machines. It discusses the framework, evaluation, and conclusions regarding system virtualization, particularly addressing memory virtualization overhead and opt
0 views • 33 slides
Contrast and Development in "Men Should Weep" Act Three
Act Three of "Men Should Weep" by Ena Lamont Stewart portrays a contrast in atmosphere from the start of the act, characterized by a cheerier and more positive ambiance. It delves into complex family dynamics, plot strands, and character developments that culminate in a climactic resolution, offerin
0 views • 39 slides
The Golden Temple: A Symbol of Sikh Sovereignty and Universal Culture
Mutual contacts in Sikh history have left monuments of bigotry, yet the Golden Temple stands as a symbol of universal culture and a meeting ground for all. Grounded in Sikh doctrine, it represents a stance against absolutism and serves as the hub of the Sikh world, embodying the principles of respec
0 views • 11 slides
Introduction to Y86 Instruction Set Architecture
Y86 Instruction Set Architecture is a simplified pseudo-language based on x86 (IA-32) architecture. It involves implementing the Fetch-Decode-Execute cycle, where instructions are fetched from memory, decoded, and executed. The Y86 ISA offers a simpler set of instructions and formats compared to x86
0 views • 25 slides
Computer Organization: Instruction Set Architecture and Interrupts
Explore the critical concepts of Computer Organization focusing on Instruction Set Architecture (ISA) and Interrupts. ISA serves as the interface between hardware and software, enabling programmers to write machine language programs effectively. Learn about Application Binary Interface (ABI), interr
0 views • 26 slides
Literary Devices in Frankenstein: Analysing Simile, Metaphor, Symbol, Motif, and Allusion
Explore the intricate use of simile, metaphor, symbol, motif, and allusion in Frankenstein through excerpts from Letter 1-4 and Chapters 1-12. Dive into the vivid comparisons, symbolic representations, and layered meanings embedded in Mary Shelley's classic novel.
0 views • 11 slides
Chemistry Revision: Atomic Structure and the Periodic Table - AQA Trilogy
Explore key concepts in Chemistry Revision for AQA Trilogy including atomic structure, periodic table organization, separation techniques, symbol equations, electron structures, isotopes, and more. Learn about burning magnesium, crystallization, chromatography, fractional distillation, and propertie
0 views • 10 slides
X86 ISA Flags in System Security
This article delves into the details of various flags in the X86 ISA architecture, such as CF (Carry Flag), PF (Parity Flag), AF (Auxiliary Flag), ZF (Zero Flag), SF (Sign Flag), TF (Trace Flag), IF (Interrupt Flag), DF (Direction Flag), OF (Overflow Flag), and IOPL (Input Output Privilege Level). T
0 views • 16 slides
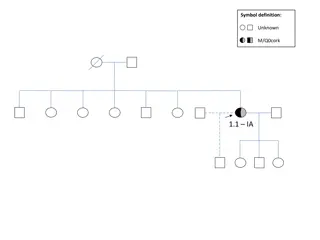
Unveiling Symbol Definitions Across Various Regions
Discover the enigmatic symbol definitions from unknown realms such as Perugia, Brescia, Torino, Cosenza, Pordenone, Lampedusa, and Dublin. Unravel the mysteries behind these symbols through intriguing images and descriptions, each representing a unique identity and significance.
0 views • 8 slides
Specific Parameters for DL Interruptions in 5G Network Testing
Detailed discussion and guidelines for verifying symbol-level DL interruptions in 5G network testing scenarios such as switching between LTE and NR carriers, inter-band ENDC TDD configuration, and FDD-TDD CA (SA) TDD configuration. The document covers specific parameters, test options, and symbol ve
0 views • 6 slides
IEEE 802.11-15/0099 Payload Symbol Size for 11ax Study
The document dated January 2015 discusses the payload symbol size for 11ax in IEEE 802.11 standards. It includes contributions from various authors representing companies like Broadcom, Intel, Samsung, Marvell, and NTT. The study addresses technical aspects related to wireless communication technolo
0 views • 33 slides
Real-Time Digital Signal Processing Lab: Digital Pulse Amplitude Modulation (PAM)
Introduction to Digital Pulse Amplitude Modulation (PAM) in the context of Real-Time Digital Signal Processing Lab. Topics covered include pulse shaping, symbol mapping, baseband PAM transmission, and more. The content delves into bit-to-symbol conversion, symbol amplitude mapping, symbol period det
0 views • 18 slides
Scopes and Symbol Tables in Compiler Construction
Scopes and symbol tables play a crucial role in programming languages by regulating the visibility of identifiers and establishing the relationship between binding and applied occurrences. Language issues such as single vs. multiple-pass compilation further impact the implementation of compilers, as
0 views • 26 slides
Implementation of RISC-V in Protium: Overview and Analysis
RISC-V, a royalty-free open-source Instruction Set Architecture (ISA), has gained popularity since its inception in 2010. This article delves into the historical background, extensions, integer registers, and the Pulp platform's RISC-V cores. The implementation of RISC-V in Protium is discussed, pro
0 views • 13 slides
Instrument Air Quality Standards in Industrial Applications
TESCORP, based in Tulsa, Oklahoma, specializes in distributing, fabricating, and servicing compression systems globally. Instrument air quality standards are crucial for pneumatic instruments in various industries. ANSI/ISA 7.0.0.1996 sets the standard for instrument air quality, focusing on pressur
0 views • 17 slides
The Characters and Themes in "Men Should Weep" by Ena Lamont Stewart
The introduction to the play "Men Should Weep" by Ena Lamont Stewart sets the stage for a tumultuous story as Alec and Isa arrive to stay with John and Maggie after a tragic event. The dynamics between the characters, particularly Alec, Jenny, and the rest of the family, reveal layers of complex rel
0 views • 7 slides
The Life of Sayyidatuna Maryam (alayhassalam) in Islam
Sayyidatuna Maryam (alayhassalam) is renowned in Islam for her piety, purity, and devotion to Allah. Born into the noble family of `Imran, she was granted the honor of being the mother of Prophet `Isa (Jesus). Her miraculous birth and upbringing under Prophet Zakariyyah (alayhissalam) highlight her
0 views • 10 slides
Analysis on Impact of Blank Guard Interval to Inter-Symbol Interference
Performance gain was observed with Blank GI in coping with Inter-Symbol Interference (ISI). However, Intra-Symbol Interference still remains. Three Waveform Coding Designs were evaluated for their effectiveness. The study analyzed the effects of Blank GI on ISI and Intra-Symbol Interference to enhan
0 views • 14 slides
Pipelining in Computer Organization
Explore the intricate process of pipelining in computer organization and assembly language programming. Delve into the fetch-decode-execute cycle, toy ISA instructions, defining pipeline behavior, and the pipeline steps for different instructions. Gain insights into how instructions progress through
0 views • 37 slides
Advanced Computer Architecture in Parallel Computing
Covering topics like Instruction-Set Architecture (ISA), 5-stage pipeline, and Pipelined instructions, this course delves into the intricacies of advanced computer architecture, with a focus on achieving high performance by optimizing data flow to execution units. The course provides insights into t
0 views • 12 slides
Overview of Single-Cycle Implementation in Computer Organization
Today's lecture discussed the single-cycle implementation of processors, focusing on executing instructions in hardware based on the ISA. The process involves different cycles such as instruction fetch, decode, execution, memory access, and write-back. The presentation highlighted the functions of a
0 views • 24 slides
Concept of Ying Yang and Opposites in Nature
The Yin Yang symbol represents the balance of opposite energies in nature, where complementary forces can work together harmoniously. This article delves into the significance of opposites, showcases different Ying Yang designs, encourages creativity in designing your own symbol, and explores the co
0 views • 7 slides
Instruction Set Architectures (ISAs) in Computer Science
Explore the concepts of RISC, CISC, and ISA variations in computer architecture. Dive into the differences between MIPS, ARM, X86, and other ISAs, focusing on load/store, arithmetic, control flow, and more. Gain insights into the evolution and variations of ISAs, and discover the alternatives beyond
0 views • 37 slides