Understanding IDS/IPS: Enhancing Security with SecurityGen's Advanced Solutions
In the realm of cybersecurity, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play pivotal roles in safeguarding networks against evolving threats. SecurityGen's IDS IPS solutions are designed to monitor network traffic, detect suspicious activities, and prevent potential i
4 views • 1 slides
Progress in Prevention and Health Inequalities - Annual Report 2023-24
The Prevention and Health Inequalities Team at BOB ICB is dedicated to enhancing prevention efforts and reducing health inequalities across their population and communities. Key achievements include setting up inpatient and maternity tobacco dependency treatment services, establishing prevention net
0 views • 14 slides
Understanding Suicide Risk and Prevention During the COVID-19 Pandemic
The COVID-19 pandemic has raised concerns about potential increases in suicide rates due to its economic impacts and social disruptions. While there is a focus on suicide prevention efforts, the exact effect of the pandemic on suicide rates remains unclear. Initiatives such as Suicide Prevention Act
1 views • 10 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Understanding Disability Prevention and Levels of Prevention
Disability prevention involves efforts to eliminate or reduce the causes and severity of disabilities. It can be achieved through primary, secondary, and tertiary prevention strategies, aiming to prevent risk factors that cause impairment and promote overall well-being. Primary prevention focuses on
2 views • 21 slides
Deception Game on Decoy Systems and Honeypots
Deception Game on Decoy Systems and Honeypots explores the use of deception technologies in computer security, focusing on decoy systems like honeypots. It delves into how attackers are lured into fake objects and the monitoring of their behavior to mitigate intrusion. The concept of fake honeypots,
4 views • 25 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Semantics-Aware Intrusion Detection for Industrial Control Systems by Mer Yksel
Mer Yksel, a PhD candidate at Eindhoven University of Technology, specializes in intrusion detection and data analytics with a focus on industrial control systems. His research covers targeted attacks, threat modeling, protection of ICS networks, and innovative anomaly-based approaches for cybersecu
0 views • 31 slides
Yale Intrusion Alarm System Overview
Yale, a global leader in security solutions, offers the Yale Intrusion Alarm system designed to secure homes and personal belongings. This system features the HSA-6403-PS and HSA-6404-GSM panels with various security elements like sensors, sirens, keypad, and more. Users can easily program and test
0 views • 24 slides
Comprehensive Student Support Program for Mental Health and Wellness
Providing a wide range of no-cost services to students and families, the program focuses on drug/alcohol prevention, suicide prevention, character building, bullying prevention, and more. Through initiatives like teaching Botvin Life Skills, implementing suicide prevention curriculum, and offering s
1 views • 5 slides
Comprehensive Overview of Distributed Intrusion Detection System (DIDS)
Explore the Distributed Intrusion Detection System (DIDS) introduced by Mohammad Hossein Salehi and Kiumars Talaee. Learn about the significance, working, and different types of IDS within DIDS like HIDS, NIDS, and agent-based IDS. Understand the division, information sources, and roles of client-ba
0 views • 25 slides
A Hybrid Intrusion Detection System Approach for IEEE 802.11 Wireless Networks
This research project explores the development of a hybrid intrusion detection system for IEEE 802.11 wireless networks. The study includes research objectives, background information, experimental results, evaluation, and comparison of existing systems, HWIDS design, conclusions, future work, and r
0 views • 73 slides
POLLUTION PREVENTION: A Closer Look at Environmental Initiatives in Oklahoma
Explore the evolution and implementation of pollution prevention measures in Oklahoma, focusing on statutory directives, recent activities, recycling efforts, tax credits, and more. The Pollution Prevention Act of 1990 plays a crucial role in reducing environmental hazards through the reduction of p
0 views • 31 slides
Prevention and Care of Airborne Infections in TB/HIV Settings
In this session, participants will learn the importance of infection prevention and control in TB/HIV care, levels of prevention in airborne infections, strategies to prevent TB transmission in healthcare settings, and patient management steps to prevent TB transmission. The spread of TB, risks of t
0 views • 20 slides
Youth Substance Abuse Prevention Funding in California
California utilizes Substance Abuse Prevention and Treatment Block Grant (SABG) funding to support primary prevention services for youth. Approximately $40 million is distributed annually to 58 counties for strategic prevention planning based on local needs assessments. Initiatives like the Strategi
0 views • 18 slides
Effective Strategies for Virtualizing Intrusion Detection Systems
Explore the benefits of virtualizing intrusion detection systems through microservices, addressing the limitations of traditional monolithic IDS setups. Learn how this approach improves scalability, efficiency, and customization for enhanced security measures in network environments.
0 views • 25 slides
Mastering Intrusion Detection with Snort: A Comprehensive Guide
Dive into the world of network security with Snort, the powerful intrusion detection system. Learn how to analyze network traffic in real time, create custom configuration files, and defend against zero-day attacks. Explore Snort's versatility, portability, and configurability, and discover advanced
0 views • 5 slides
Understanding IDS and IPS for Network Security
Enhance the security of your network with IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) by monitoring traffic, inspecting data packets, and detecting malicious activities based on known signatures. Learn about different types like HIDS and NIDS, their functions, and tools us
0 views • 7 slides
Understanding Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are software pieces that monitor computer systems to detect unauthorized intrusions and misuse, responding by logging activity, notifying authorities, and taking appropriate countermeasures. IDS help address security challenges, aiming to find and fix serious securi
0 views • 40 slides
Root Causes of Intrusion Detection False Negatives: Methodology and Case Study
This study, presented at IEEE MILCOM 2019 by Eric Ficke, Kristin M. Schweitzer, Raymond M. Bateman, and Shouhuai Xu, delves into the analysis of root causes of intrusion detection false negatives. The researchers explore methodologies and present a case study to illustrate their findings.
0 views • 24 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
Understanding Intrusion Detection and Prevention Systems
Learn about the components and implementation options of intrusion detection and prevention systems, as well as the goals and role of an IDPS in network defense. Discover the capabilities of IDPS, such as assessing network traffic, detecting unauthorized access, and responding to threats. Explore an
0 views • 57 slides
Comprehensive Overview of HIV Prevention Strategies and Interventions
This synthesis covers the importance of monitoring progress in HIV prevention through data cascades, the need for standardized frameworks, promoting effective HIV prevention programs in diverse social contexts, and the key pillars of combination HIV prevention strategies. It also outlines various HI
0 views • 40 slides
Football Field Complex Remedy Project Overview
The project involves remedial measures for the football field complex at Elmira High School, focusing on soil removal, groundwater monitoring, and vapor intrusion prevention. Excavation, disposal of hazardous waste, and construction of institutional controls are key components. Plans for interim rem
0 views • 15 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
Dive into the world of hacking techniques, intrusion detection, and network protocols with expert Ali Al-Shemery. Learn about host discovery, port scanning, packet crafting, and more using tools like Nmap. Explore the importance of network protocols like TCP, UDP, ICMP, and ARP. Discover the art of
0 views • 50 slides
Understanding Radon and Chemical Soil Gas Vapor Intrusion
This presentation at the 2019 International Radon Symposium in Denver, Colorado explores the association between radon, chemical soil gas, and vapor intrusion. It discusses the challenges in testing, analyzing differences, and the need for supplemental measurements like radon to validate models. The
0 views • 19 slides
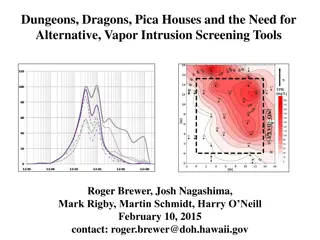
Alternative Vapor Intrusion Screening Tools for Environmental Investigations
Estimation of subslab attenuation factors for vapor intrusion investigations is crucial in assessing indoor air quality. This study reviews EPA methods, emphasizing the importance of vapor attenuation in screening indoor air for contaminants. Various experts contributed insights, leading to the deve
0 views • 35 slides
Effective Strategies for Injury Prevention in Trauma Centers
Organized and data-driven injury prevention activities are crucial in trauma centers. Community partnerships, evidence-based reviews, designated injury prevention coordinators, and involvement of trauma personnel are key elements for successful injury prevention. Targeting contributing factors like
0 views • 20 slides
Prevention Subcommittee Update - July 26, 2023 Review
The Prevention Subcommittee Update held on July 26, 2023, highlighted key topics including an introduction, strategic plan prioritization, insights from subject matter experts, and discussions on the Prevention Center and workshops. The subcommittee comprises talented preventionist commissioners and
0 views • 6 slides
Assessment of HIV Prevention Programme Needs and Barriers in Ghana
Conduct a data-driven assessment of HIV prevention programme needs and barriers in Ghana based on the Ghana Road Map Baseline Survey components. Evaluate the country's preparedness in addressing HIV epidemic patterns and prevention response analysis. Identify key barriers hindering HIV prevention ef
0 views • 11 slides
Understanding Client-Side Attacks and Intrusion Detection
Explore client-side attacks, their methodology, and defense strategies in Ali Al-Shemery's comprehensive guide. Discover the evolving challenges of network security and the importance of staying ahead with effective intrusion detection techniques.
0 views • 65 slides
Understanding Intrusion Detection and Security Tools
Explore the world of intrusion detection, access control, and security tools through terminology, systems, classifications, and methods. Learn about intrusion detection systems (IDSs), their terminology, alert systems, classification methods like signature-based and statistical anomaly-based approac
0 views • 39 slides
Understanding Situational Crime Prevention Strategies
Situational crime prevention strategies aim to reduce crime by altering environmental conditions, influencing offender decisions, and targeting crime opportunities. Primary prevention focuses on modifying physical and social environments, while secondary prevention aims to identify potential offende
1 views • 31 slides
Comprehensive Guide to Hacking Techniques and Intrusion Detection
This guide by Ali Al-Shemery provides insights into hacking techniques, intrusion detection, fingerprinting, external and internal footprinting, passive reconnaissance, WHOIS lookups, and various online tools for intelligence gathering during penetration tests. It covers identifying customer externa
0 views • 29 slides
California's Family First Prevention Services Program
California's Family First Prevention Services Program, established under the Family First Prevention Services Act of 2018, aims to provide evidence-based prevention and trauma-informed services to children and youth at risk of entering foster care. The program leverages a comprehensive plan that inc
0 views • 21 slides
Kentucky Injury Prevention and Research Center - Promoting Safe Communities
The Kentucky Injury Prevention and Research Center (KIPRC) at the University of Kentucky focuses on reducing the burden of injuries across the state. Founded in 1994, KIPRC works on surveillance, data analysis, and prevention of injuries related to falls, poisonings, fires, motor vehicles, and viole
0 views • 21 slides
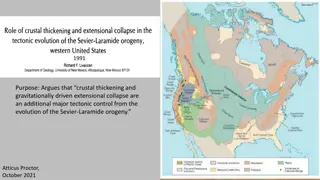
Tectonic Controls of the Sevier-Laramide Orogeny
The Sevier-Laramide orogeny was influenced by crustal thickening and gravitational extensional collapse. The tectonic model proposed suggests that conductive heating from subduction weakened the crust, leading to compression, uplift, and lateral growth. Deformation persisted from the Cretaceous to t
0 views • 8 slides
Suicide Prevention Advisory Group Meeting - April 23, 2024
The Suicide Prevention Advisory Group held its monthly meeting on April 23, 2024, discussing critical research priorities and key areas of focus for suicide prevention efforts. The meeting agenda included reviewing priority setting processes, analyzing survey results, and determining key research ar
0 views • 22 slides
Analysis of Tropospheric Intrusion Evolution in START08 Field Campaign
The study presents the analysis of tropospheric intrusion evolution during the START08 Field Campaign using models such as WACCM and GFS. The primary goals include comparing model output with observations, verifying dynamical transport features, and studying the spatial and temporal evolution of mid
0 views • 26 slides