Master GB0-372 Ace H3C Advanced Routing & Switching Technology 1 Exam
Elevate your career with success in the GB0-372 exam. Master H3C Advanced Routing and Switching Technology 1 with our comprehensive study materials, practice tests, and expert guidance. Prepare effectively for the H3C GB0-372 exam and gain the skills and knowledge necessary to excel in advanced rout
2 views • 8 slides
Understanding Routing Methods in Hydrologic Engineering Center (HEC-ResSim)
Explore the differences between hydrologic and hydraulic routing, learn about open channel flow processes, and delve into channel routing within HEC-ResSim. Discover various reach routing methods, parameter estimation techniques, and calibration approaches. Dive into the Muskingum method and its app
6 views • 29 slides
Guidelines for Upholding Rights of LGBTQ
In light of evolving societal norms and the imperative to safeguard the rights and dignity of LGBTQ individuals and inter-faith\/inter-caste couples, the Supreme Court has given guidelines for the handling of habeas corpus petitions and petitions for police protection.\nBackground:\nRecent instance
9 views • 4 slides
Gradual Fine-Tuning for Low-Resource Domain Adaptation: Methods and Experiments
This study presents the effectiveness of gradual fine-tuning in low-resource domain adaptation, highlighting the benefits of gradually easing a model towards the target domain rather than abrupt shifts. Inspired by curriculum learning, the approach involves training the model on a mix of out-of-doma
0 views • 17 slides
Inter-Cluster Coordination and Information Management in Humanitarian Emergencies
Inter-Cluster Coordination and Information Management play vital roles in humanitarian emergencies. The coordination mechanism involves regular meetings convened by the RC/HC and coordinated by OCHA, providing opportunities for clusters to collaborate on shared planning, needs assessments, and poole
3 views • 13 slides
Understanding Domain Adaptation in Machine Learning
Domain adaptation in machine learning involves transferring knowledge from one domain to another. It addresses the challenge of different data distributions in training and testing sets, leading to improved model performance. Techniques like domain adversarial training and transfer learning play a k
0 views • 16 slides
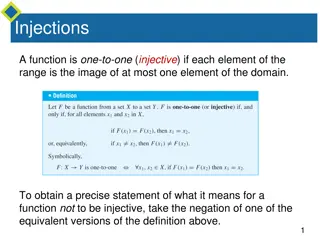
Understanding Injective and Surjective Functions
Injective functions map elements from the domain to the range uniquely, while surjective functions ensure every element in the co-domain has a corresponding element in the domain. The negation of injective means finding x1 and x2 in the domain with the same function value but not equal, whereas for
1 views • 26 slides
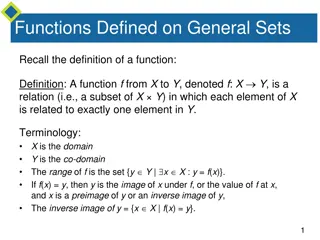
Understanding Functions: Definitions and Arrow Diagrams
Recall the definition of a function, where each element in the domain is related to exactly one element in the co-domain. Arrow diagrams can visually represent functions from finite sets X to Y. In this example, a function is defined from X = {a, b, c} to Y = {1, 2, 3, 4} using arrow diagrams, showc
8 views • 28 slides
Understanding Operating System Protection Principles
Explore the goals, principles, and implementation of protection in computer systems, including access matrix, domain structure, and capability-based systems. Learn how protection domains and access control are used to specify resource access, and delve into the concept of least privilege and dynamic
4 views • 21 slides
Understanding EIGRP: A Comprehensive Overview
Enhanced Interior Gateway Routing Protocol (EIGRP) is a dynamic routing protocol providing various advantages to network administrators. It is a classless routing protocol supporting VLSM and is considered an Interior Gateway Protocol (IGP). EIGRP uses advanced distance vector routing and is known f
1 views • 5 slides
Decoy Routing: A Tool Against Internet Censorship
Modern censorship resistance tools like decoy routing provide a new approach against web censorship at a nation-state level. Decoy routing involves placing a proxy in the middle of paths to hide user packets from detection by adversaries. The use of decoys helps in avoiding the enumeration of censor
0 views • 20 slides
Direct Routing with Teams: Opportunity or Threat?
Microsoft's shift in cloud architecture for voice services opens up new possibilities for enterprises and carriers with Teams Direct Routing. This allows seamless integration of PSTN services directly to the cloud, offering flexibility in maintaining existing contracts while transitioning to Teams a
0 views • 10 slides
Geometric Routing Concepts and Byzantine Fault Tolerance
Geometric Routing enables routing without overhead, where each node knows its global coordinates and forwards messages based on proximity to the destination. Byzantine Faults pose challenges with arbitrary node behavior, but a Byzantine-Robust Geometric Routing algorithm addresses this in a 3-connec
2 views • 33 slides
Understanding Static Routing in Network Infrastructure Workshops
Explore the concepts of static routing in networking workshops, covering Unix and Cisco network interface configurations, static routes, default routes, and advantages and disadvantages of static routing. Learn about IP routing configuration, assignment of IPv4 addresses, and FreeBSD network interfa
4 views • 37 slides
Understanding Networking Principles and Routing Algorithms in Distributed Systems
Delve into the intricacies of networking principles and routing algorithms in distributed systems. Explore the four layers studied, including the network layer that handles routing. Discover the role of routers in forwarding packets between networks and the challenges of designing routing algorithms
1 views • 23 slides
Understanding Internet Routing Protocols
Explore the intricacies of routing protocols in the context of the Internet's large federated network. Delve into the concepts of reachability, message exchange, algorithm design, and the challenges posed by running an autonomous system. Gain insights into the Border Gateway Protocol (BGP) and inter
1 views • 26 slides
Country Names in the Domain Name System (DNS)
The Domain Name System (DNS) plays a crucial role in attributing top-level and second-level domains to country names. This system is global and managed by ICANN, not national offices, allowing for unique attribution to one person. Examples of country names registered as second-level domains are prov
0 views • 7 slides
Trust-Based Anonymous Communication Models and Routing Algorithms
This research paper discusses trust-based anonymous communication models and routing algorithms in the context of onion routing, emphasizing the importance of trust in mitigating security risks from adversaries with resources. The paper presents a model of trust and proposes trust-based routing algo
0 views • 65 slides
Hierarchical Attention Transfer Network for Cross-domain Sentiment Classification
A study conducted by Zheng Li, Ying Wei, Yu Zhang, and Qiang Yang from the Hong Kong University of Science and Technology on utilizing a Hierarchical Attention Transfer Network for Cross-domain Sentiment Classification. The research focuses on sentiment classification testing data of books, training
0 views • 28 slides
Developing MPI Programs with Domain Decomposition
Domain decomposition is a parallelization method used for developing MPI programs by partitioning the domain into portions and assigning them to different processes. Three common ways of partitioning are block, cyclic, and block-cyclic, each with its own communication requirements. Considerations fo
0 views • 19 slides
Understanding Greedy Distributed Spanning Tree Routing in Wireless Sensor Networks
Wireless sensor networks play a critical role in various applications, and the Greedy Distributed Spanning Tree Routing (GDSTR) protocol, developed by Matthew Hendricks, offers an efficient routing approach. This protocol addresses challenges such as scalability, dynamic topologies, and sensor node
0 views • 34 slides
Understanding Dynamic Routing on Fast Data Plane with VPP and BIRD
Explore the concept of dynamic routing on a fast data plane featuring VPP (Vector Packet Processing) and BIRD (Internet Routing Daemon). Learn how packets traverse a graph, routing mechanisms like BGP, RIP, OSPF, and how sockets and plugins interact to forward traffic efficiently. Discover how VPP a
0 views • 12 slides
Understanding Cross-Domain Policies in Web Application Security
This content explores various aspects of cross-domain policies in web applications, including the Same-Origin Policy for JavaScript and Flash, their importance in protecting user data, potential risks of bypassing these policies, and the implications of trusting Flash content to read data from exter
0 views • 64 slides
Challenges in Establishing a Secure Inter-Domain Routing System
The daunting task of creating a secure and trusted inter-domain routing system poses significant challenges due to the decentralized nature of the internet. Addressing issues such as propagation of false routing information, ensuring correct reachability, and dealing with the lack of a clear truth m
0 views • 15 slides
Understanding Routing Protocols in Network Layer
Routing protocols in the network layer dictate how data packets are routed through a network. This lecture delves into key concepts such as reachability, routing protocol components, and the workings of Distance Vector (DV) algorithms. It explains how updates propagate in networks efficiently with D
0 views • 31 slides
Wyoming Eminent Domain Laws - Legal Updates and Negotiations
Wyoming Legislative Changes to Eminent Domain Laws outline the requirements for exercising eminent domain, including proof of public interest and necessity, diligent negotiations, and proper notification to property owners. The laws also emphasize the importance of good faith negotiations and fair c
0 views • 9 slides
Understanding Hyper-Specific Prefixes in Internet Routing
Delve into the world of Hyper-Specific Prefixes (HSPs) in Internet routing as authors analyze the prevalence, visibility, and consistency of these unique routing elements. Exploring BGP best practices, related work, and methodological approaches, the study uncovers the nuances of HSPs' presence and
0 views • 31 slides
Adaptive Resilient Routing via Preorders in SDN
This research paper discusses the challenges of path-based routing in modern networks and introduces a novel approach called Adaptive Resilient Routing via Preorders in Software-Defined Networking (SDN). The authors emphasize the limitations of traditional routing schemes, the importance of resilien
0 views • 42 slides
Understanding Domain Names for Authoritative DNS Servers
Researchers need to accurately define the types of authoritative DNS servers they sample when measuring server properties. This study focuses on collecting domain names used for web servers to assess typical domain name characteristics, highlighting the importance of accurate data for research purpo
0 views • 7 slides
Understanding IP Routing and Switching in Computer Networks
In the world of computer networking, IP routing and switching play crucial roles in ensuring efficient data transmission. Switches make decisions based on MAC addresses, while routers route based on IP information. By managing routing tables and using static or dynamic routing protocols, networks ca
0 views • 13 slides
Updates and Changes in SPA/SPAC Processes
Changes and updates to SPA/SPAC processes include new team members, carryforward form submission instructions, Kuali Research routing adjustments, and a new routing process for proposals. These updates aim to streamline procedures and improve efficiency in award management. Routing process changes w
0 views • 31 slides
Understanding the Domain Name System (DNS) Structure
The Domain Name System (DNS) is a distributed data collection utilizing a delegation hierarchy to reflect the hierarchical structure of domain names. This system resolves DNS names by discovering information through iterative searches, starting from the root zone. The process involves querying serve
0 views • 25 slides
New IDT/ICT Form: Streamlining Inter-Departmental and Inter-Company Transactions
Streamline inter-departmental and inter-company transactions with the new IDT/ICT form. Easily transfer funds between different departments within the same company and across different companies. Two identical forms cater to Foundation and Philanthropic accounts, enhancing efficiency in financial pr
0 views • 13 slides
Securing Domain Control with BGP Attacks and Digital Certificates
Exploring the vulnerabilities of domain control verification in the context of BGP attacks and the role of digital certificates in ensuring security. The process of domain control verification, issuance of digital certificates by Certificate Authorities (CAs), and the significance of Public Key Infr
0 views • 53 slides
Evolution of BGP: Expectations vs. Reality in Protocol Development
BGP has evolved over 30 years from its origins as an advancement of EGP in the 1980s to address issues like routing explosion, IPv6 integration, and imperfections such as session insecurity and protocol instability. Despite challenges, BGP remains a critical component of inter-domain routing, adapti
0 views • 10 slides
Understanding BGP Basics and Routing Security
Border Gateway Protocol (BGP) is a crucial protocol used by routers to exchange routing information and make routing decisions. This protocol plays a key role in how the Internet functions, with over 76,000 Autonomous Systems and millions of routes being advertised. Research and Education (R&E) netw
0 views • 33 slides
Exploring the Classic Blocks World Domain
Discover the classic blocks world domain, starting with the BW domain file and solving problems using planning domains. Learn about predicates, constants, and actions to manipulate objects effectively within the domain.
0 views • 10 slides
Understanding Non-Optimal Routing and 32-Bit ASN Compatibility
Explore the challenges caused by the incompatibility of 32-bit ASN with old router software, leading to non-optimal routing issues. Learn about Autonomous Systems, AS Numbers, BGP asymmetric routing, and the importance of routing software supporting 32-bit ASN. Discover how outdated software replace
0 views • 8 slides
Evolution of Domain Name System (DNS) Since 1983
Domain Name System (DNS) has played a crucial role in converting domain names to IP addresses since its inception in 1983. This system has revolutionized the way we navigate the internet, translating human-readable names into machine-readable IP addresses. The distributed and hierarchical nature of
0 views • 23 slides
Understanding Domain Name System (DNS) Fundamentals
The Domain Name System (DNS) is a crucial component of the Internet, facilitating the conversion of human-readable domain names into IP addresses. This session covers the basics of DNS, the need for names in computing, challenges of the old HOSTS.TXT system, the distributed nature of DNS, its hierar
0 views • 29 slides