Real-World Evidence Analytics Market Poised for Staggering Growth
Data management & integration enhancements help improve the speed & quality of drug discovery and clinical trial processes. Artificial intelligence (AI) is employed in real-world data (RWD) to enhance data anomaly detection, standardization, and quality check at the pre-processing stage. AI is expec
1 views • 3 slides
SAFETY TRAINING FOR NEW RECRUITS
This detailed safety training course for new recruits covers a wide range of topics such as group vision, commitment, safety values, HSE risks, golden rules, anomaly reporting, and more. The course is divided into three sections: D1 & D2, D3 to D90, and D3 to D90 continued. Each section includes cla
1 views • 8 slides
Netdata - The Open Source Observability Platform: A Comprehensive Overview
Netdata is an open-source observability platform created by Costa Tsaousis. It enables real-time, high-resolution monitoring with auto-discovery of integrations, unsupervised machine learning for metrics, alerting, visualization, and anomaly detection. With easy installation on any system, Netdata p
1 views • 54 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Real-world Evidence (RWE) Analytics Market Worth $2.93 billion by 2029
Data management & integration enhancements help improve the speed & quality of drug discovery and clinical trial processes. Artificial intelligence (AI) is employed in real-world data (RWD) to enhance data anomaly detection, standardization, and quality check at the pre-processing stage. AI is expec
0 views • 2 slides
Understanding Similarity and Dissimilarity Measures in Data Mining
Similarity and dissimilarity measures play a crucial role in various data mining techniques like clustering, nearest neighbor classification, and anomaly detection. These measures help quantify how alike or different data objects are, facilitating efficient data analysis and decision-making processe
0 views • 51 slides
Guide to Implant Insertion and Removal
Essential steps and equipment required for the insertion of implants, including patient positioning, skin preparation, insertion techniques, and post-insertion care. Detailed instructions on how to handle potential complications during the insertion process and necessary follow-up steps for successf
1 views • 20 slides
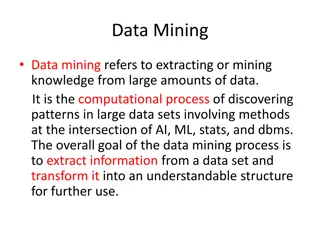
Understanding Data Mining: Processes and Applications
Data mining involves extracting knowledge from large data sets using computational methods at the intersection of AI, ML, stats, and DBMS. It aims to discover patterns and transform data into actionable insights for various applications such as predictive modeling and anomaly detection.
0 views • 11 slides
Microwave Filter Design: Understanding Insertion Loss Methods
Study microwave filter design focusing on insertion loss method for lossless filters. Explore transmission line connections, power loss ratio calculations, and insertion loss in designing filters for specific responses like low-pass. Learn about common filter types and approaches for designing vario
0 views • 35 slides
Understanding Transaction Management in DBMS
In this lecture, Mohammad Hammoud covers the key aspects of transaction management in database management systems (DBMS). Topics include locking protocols, anomaly avoidance, lock managers, and two-phase locking. The session delves into the rules, data structures, and processes involved in maintaini
1 views • 56 slides
Insights into Filter Design by Insertion Loss Method
Explore various aspects of filter design by insertion loss method including insertion loss, linear phase, maximally flat low-pass prototype, and more through informative images and descriptions. Delve into the intricacies of two prototypes and gain a deeper understanding of this important design met
0 views • 11 slides
Understanding Sorting Algorithms: Bubble Sort and Insertion Sort
Master the concepts of standard sorting algorithms through a detailed exploration of Bubble Sort and Insertion Sort. Learn how each algorithm functions step-by-step, gaining a practical understanding of sorting techniques in computational thinking and programming. Engage in hands-on activities to ap
1 views • 14 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Understanding Outlier Analysis in Data Mining
Outliers are data objects that deviate significantly from normal data, providing valuable insights in various applications like fraud detection and customer segmentation. Types of outliers include global, contextual, and collective outliers, each serving distinct purposes in anomaly detection. Chall
0 views • 44 slides
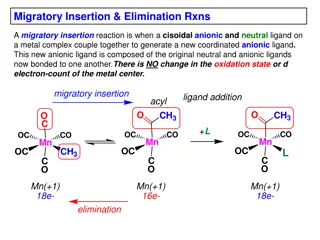
Insights into Migratory Insertion and Elimination Reactions in Metal Complexes
Migratory insertion in metal complexes involves the coupling of a cisoidal anionic and neutral ligand to form a new coordinated anionic ligand without changing the metal center's oxidation state or d-electron count. This process requires cisoidality between the reacting ligands and a vacant coordina
0 views • 19 slides
Efficient Anomaly Detection for Batch Systems Using Machine Learning
Explore a lightning talk session focusing on using Collectd metrics and job data in HTCondor batch systems for anomaly detection. Challenges with raw historical data are addressed through data collection, manipulation, and application of anomaly detection techniques using ML. Various algorithms such
0 views • 14 slides
Suprapubic Catheter Insertion Procedure Guidelines
Suprapubic catheter insertion is a procedure indicated for conditions such as urethral injury, obstruction, bladder neck masses, and benign prostatic hypertrophy. It involves proper patient positioning, analgesia, equipment preparation, and a step-by-step technique including bladder palpation, marki
1 views • 12 slides
An Overview of Evading Anomaly Detection using Variance Injection Attacks on PCA
This presentation discusses evading anomaly detection through variance injection attacks on Principal Component Analysis (PCA) in the context of security. It covers the background of machine learning and PCA, related work, motivation, main ideas, evaluation, conclusion, and future work. The content
1 views • 19 slides
Understanding Enamel Pearl Anomaly in Dentistry
Enamel Pearl is a developmental anomaly where small nodules of enamel form below the cemento enamel junction, mainly on permanent teeth. This anomaly, detected radiographically, can lead to bacterial accumulation, periodontal issues, and inflammation if left untreated. Dental hygienists play a cruci
0 views • 8 slides
Wavelet-based Scaleograms and CNN for Anomaly Detection in Nuclear Reactors
This study utilizes wavelet-based scaleograms and a convolutional neural network (CNN) for anomaly detection in nuclear reactors. By analyzing neutron flux signals from in-core and ex-core sensors, the proposed methodology aims to identify perturbations such as fuel assembly vibrations, synchronized
3 views • 11 slides
Priority Queues: Operations and Implementations
Priority queues are data structures that allow efficient insertion, deletion, and retrieval of elements based on their priority. This information-rich content covers various aspects of priority queues, including ideal times, binomial queues, Dijkstra's algorithm for single-source shortest paths, and
0 views • 11 slides
Advanced Techniques for Heavy Hitters Detection in Insertion Streams
Beating CountSketch algorithms, like those presented by David P. Woodruff and team, offer innovative solutions for identifying heavy hitters in insertion streams with minimal space complexity. Guarantees such as L1 and L2 outputs and the CountSketch approach are explored to achieve efficient heavy h
0 views • 18 slides
Lessons Learned from On-Orbit Anomaly Research
The On-Orbit Anomaly Research workshop held at the NASA IV&V Facility in 2013 focused on studying post-launch anomalies and enhancing IV&V processes. The presentations highlighted common themes like Pseudo-Software Command Scripts, Software and Hardware Interface issues, Communication Protocols, and
0 views • 55 slides
Troubleshooting Percutaneous Tube Insertion: Medical Insights by Dr. Dave Sawbridge
Explore troubleshooting aspects of percutaneous tube insertion as discussed by Gastroenterologist Dr. Dave Sawbridge from Mater Private Cork. Learn about practicalities, complications, who needs PEG/PEG-J/PEJ insertion, how the procedure is done, risks and benefits involved, and how to address poten
0 views • 9 slides
On-Orbit Anomaly Research at NASA: Causes and Solutions
On-Orbit Anomaly Research (OOAR) at NASA's IV&V Facility involves studying mishaps related to space missions, identifying anomalies, and improving IV&V processes. The research delves into the causes of anomalies, such as operating system faults, and proximate causes like software deficiencies. Detai
0 views • 20 slides
Adaptive Insertion Policies for High-Performance Caching
Explore the concept of adaptive insertion policies in high-performance caching systems, focusing on mitigating the issue of Dead on Arrival (DoA) lines by making simple changes to cache insertion policies. Understanding cache replacement components, victim selection, and insertion policy can signifi
0 views • 15 slides
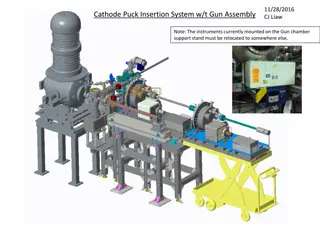
Development Status Update for Cathode Puck Insertion System
Update on the development status of the Cathode Puck Insertion System, including relocation of instruments, preparation table procurement, design and fabrication status of various components, stationary section details, welding requirements for manipulator and puck locking mechanism, mobile cart set
0 views • 14 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
LD-Sketch: Distributed Sketching Design for Anomaly Detection in Network Data Streams
LD-Sketch is a novel distributed sketching design for accurate and scalable anomaly detection in network data streams, addressing challenges such as tracking heavy keys in real-time across a vast key space. By combining high accuracy, speed, and low space complexity, LD-Sketch enables efficient heav
0 views • 25 slides
Overview of Sorting Algorithms and Quadratic Sorting - CS 330 Lecture Notes
Sorting algorithms play a crucial role in computer science and computing tasks, consuming a significant portion of computing power. Various algorithms such as Bubble Sort, Selection Sort, and Insertion Sort are discussed for sorting a list of values efficiently. Quadratic sorting algorithms like Sel
0 views • 30 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Anomaly Detection in Data Mining: Understanding Outliers and Importance
Anomaly detection is crucial in data mining to identify data points significantly different from the norm. This technique helps in recognizing rare occurrences like ozone depletion anomalies. Understanding the distinction between noise and anomalies is key, as anomalies can provide valuable insights
0 views • 35 slides
MVTX.C&S Review Homework for MVTX Group July 29-30, 2019
The homework review for the MVTX Group on July 29-30, 2019 includes questions regarding the insertion of MVTX and details about carbon fiber work at LBNL. It covers topics like the steps of insertion, drawings of the beam pipe, plans for testing with a mockup beam pipe, and evaluation of commercial
0 views • 12 slides
Anomaly Detection Using Process Behavior Charts
Explore the philosophy behind understanding variation and key principles in anomaly detection using process behavior charts. Learn about preparing data, creating SAS charts, running tests for special causes, and executing a plan for anomaly detection and reporting processes. The material draws heavi
0 views • 41 slides
Study on Ionospheric Perturbation Due to Solar and Geomagnetic Activity in Odessa Magnetic Anomaly
Research conducted in the area of the Odessa magnetic anomaly investigates ionospheric perturbations caused by solar and geomagnetic activity. The study utilizes radio astronomical and magnetometric observations from various observatories, highlighting the significance of the geomagnetic anomaly nea
0 views • 18 slides
Understanding AVL Trees: Operations, Insertion, and Deletion
AVL trees, a type of self-balancing binary search tree, require specific operations for finding, insertion, and deletion. Inserting a node involves checking for imbalance in four possible cases. Various rotations are used to maintain the tree's balance. Deletion can either be lazy or involve balanci
0 views • 13 slides
Detecting Performance Anomalies in Cellular Networks via Regression Analysis
The study focuses on detecting performance anomalies in cellular networks using regression analysis. It addresses challenges such as labeling, rare anomalies, and correlated factors. The tool CellPAD is introduced for anomaly detection, supporting various prediction algorithms and offering insights
0 views • 19 slides
Solving Cosmic Gamma Background Anomaly: Ekaterina Shlepkina's Research Insights
Explore the quest to find a solution for the cosmic gamma background anomaly in cosmic rays through Ekaterina Shlepkina's research presented at the XXII International Workshop. Learn about the investigations into cosmic rays fluxes, antiparticle studies, and possible interaction types of Dark Matter
0 views • 19 slides
Understanding Neural Network Watermarking Technologies
Neural networks are being deployed in various domains like autonomous systems, but protecting their integrity is crucial due to the costly nature of machine learning. Watermarking provides a solution to ensure traceability, integrity, and functionality of neural networks by allowing imperceptible da
0 views • 15 slides
Insertion Thermal Mass Flow Meter in India
LEOMI is a manufacturing venture founded by experienced professionals with over two decades in technology and automation. Specializing in industrial measurement solutions, particularly Insertion Thermal Mass Flow Meters, LEOMI aims to enhance operati
0 views • 10 slides