Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
Understanding Inference and Vyapti in Logic
Inference, known as Anumana in Sanskrit, is the process of deriving knowledge based on existing information or observations. It can be used for personal understanding or to demonstrate truths to others. An inference may be SvArtha (for oneself) or ParArtha (for others). Vyapti, the invariable concom
1 views • 14 slides
Understanding Inference in Indian Philosophy
In Indian philosophy, inference is considered one of the six ways to attain true knowledge. It involves three constituents: Hetu (middle term), Sadhya (major term), and Paksha (minor term). The steps of inference include apprehension of the middle term, recollection of the relation between middle an
11 views • 8 slides
Understanding Resolution in Logical Inference
Resolution is a crucial inference procedure in first-order logic, allowing for sound and complete reasoning in handling propositional logic, common normal forms for knowledge bases, resolution in first-order logic, proof trees, and refutation. Key concepts include deriving resolvents, detecting cont
2 views • 12 slides
Understanding the Scope of Inference in Statistical Studies
Statistical studies require careful consideration of the scope of inference to draw valid conclusions. Researchers need to determine if the study design allows generalization to the population or establishes cause and effect relationships. For example, a study on the effects of cartoons on children'
1 views • 15 slides
DNN Inference Optimization Challenge Overview
The DNN Inference Optimization Challenge, organized by Liya Yuan from ZTE, focuses on optimizing deep neural network (DNN) models for efficient inference on-device, at the edge, and in the cloud. The challenge addresses the need for high accuracy while minimizing data center consumption and inferenc
0 views • 13 slides
Understanding the Difference Between Observation and Inference
Learn to differentiate between observation (direct facts or occurrences) and inference (interpretations based on existing knowledge or experience) through examples such as the Sun producing heat and light (observation) and a dry, itchy skin leading to the inference that it is dry. The distinction be
2 views • 14 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Navigating Statistical Inference Challenges in Small Samples
In small samples, understanding the sampling distribution of estimators is crucial for valid inference, even when assumptions are violated. This involves careful consideration of normality assumptions, handling non-linear hypotheses, and computing standard errors for various statistics. As demonstra
0 views • 19 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Understanding Rules of Inference in Logic
Dive into the world of logic with this detailed exploration of rules of inference. Learn about different types of arguments, such as Modus Ponens and Modus Tollens, and understand how to determine the validity of an argument. Discover the purpose of rules of inference and unravel the logic behind co
0 views • 17 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
Understanding Expert Systems and Knowledge Inference
Expert Systems (ES) act as synthetic experts in specialized domains, emulating human expertise for decision-making. They can aid users in safety, training, or decision support roles. Inference rules and knowledge rules play key roles in ES, helping in problem-solving by storing facts and guiding act
0 views • 63 slides
Understanding Knowledge-Based Agents: Inference, Soundness, and Completeness
Inference, soundness, and completeness are crucial concepts in knowledge-based agents. First-order logic allows for expressive statements and has sound and complete inference procedures. Soundness ensures derived sentences are true, while completeness guarantees all entailed sentences are derived. A
0 views • 6 slides
Fast High-Dimensional Filtering and Inference in Fully-Connected CRF
This work discusses fast high-dimensional filtering techniques in Fully-Connected Conditional Random Fields (CRF) through methods like Gaussian filtering, bilateral filtering, and the use of permutohedral lattice. It explores efficient inference in CRFs with Gaussian edge potentials and accelerated
0 views • 25 slides
Probabilistic Graphical Models Part 2: Inference and Learning
This segment delves into various types of inferences in probabilistic graphical models, including marginal inference, posterior inference, and maximum a posteriori inference. It also covers methods like variable elimination, belief propagation, and junction tree for exact inference, along with appro
0 views • 33 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Optimizing Inference Time by Utilizing External Memory on STM32Cube for AI Applications
The user is exploring ways to reduce inference time by storing initial weight and bias tables in external Q-SPI flash memory and transferring them to SDRAM for AI applications on STM32Cube. They have questions regarding the performance differences between internal flash memory and external memory, r
0 views • 4 slides
Typed Assembly Language and Type Inference in Program Compilation
The provided content discusses the significance of typed assembly languages, certifying compilers, and the role of type inference in program compilation. It emphasizes the importance of preserving type information for memory safety and vulnerability prevention. The effectiveness of type inference me
0 views • 17 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding TCP Sequence Numbers and Attacks
Explore the fundamental concepts of TCP sequence numbers and inference attacks, along with the design, implementation, and impact analysis of TCP attacks. Delve into the significance of TCP fields, the three-way handshake process, as well as sequence and acknowledgment numbers to gain a comprehensiv
0 views • 35 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Rules of Inference Exercise Solutions in Discrete Math
This content provides solutions to exercises involving rules of inference in discrete mathematics. The solutions explain how conclusions are drawn from given premises using specific inference rules. Examples include identifying whether someone is clever or lucky based on given statements and determi
0 views • 4 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Modern Likelihood-Frequentist Inference: A Brief Overview
The presentation by Donald A. Pierce and Ruggero Bellio delves into Modern Likelihood-Frequentist Inference, discussing its significance as an advancement in statistical theory and methods. They highlight the shift towards likelihood and sufficiency, complementing Neyman-Pearson theory. The talk cov
0 views • 22 slides
Sequential Approximate Inference with Limited Resolution Measurements
Delve into the world of sequential approximate inference through sequential measurements of likelihoods, accounting for Hick's Law. Explore optimal inference strategies implemented by Bayes rule and tackle the challenges of limited resolution measurements. Discover the central question of refining a
0 views • 29 slides
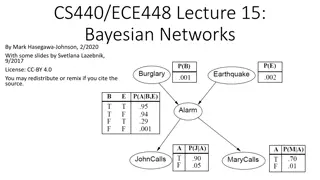
Understanding Bayesian Networks for Efficient Probabilistic Inference
Bayesian networks, also known as graphical models, provide a compact and efficient way to represent complex joint probability distributions involving hidden variables. By depicting conditional independence relationships between random variables in a graph, Bayesian networks facilitate Bayesian infer
0 views • 33 slides
Understanding DDoS Attacks: Simulation, Analysis & Defense
Delve into the world of Distributed Denial of Service (DDoS) attacks with this comprehensive study covering the architecture, advantages, bot installation phases, attack methods, defenses, and simulation. Learn about the detrimental impact of DDoS attacks on servers, their multi-tiered structure, an
0 views • 20 slides
Overview of DoS and DDoS Attacks in Cybersecurity
This content provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks in cybersecurity. It covers the types of attacks, including volumetric, reflected, and stealthy, along with detailed explanations and examples. Additionally, it discusses how DoS at
0 views • 8 slides
Dynamic Crowd Simulation Using Deep Reinforcement Learning and Bayesian Inference
This paper introduces a novel method for simulating crowd movements by combining deep reinforcement learning (DRL) with Bayesian inference. By leveraging neural networks to capture complex crowd behaviors, the proposed approach incorporates rewards for natural movements and a position-based dynamics
0 views • 15 slides