Identity Theft Prevention Program
Ensure staff understand their responsibility to protect sensitive information and know the steps to prevent, detect, and respond to identity theft. This training is required as part of the Montana Tech Identity Theft Prevention Program.
1 views • 31 slides
Prevent Identity Theft: Tips and Actions
Understand identity theft, learn how to protect against it by safeguarding your information and spotting signs early on, and know the steps to take if it happens to you. Start a conversation and report any fraud promptly. Get informed at ftc.gov/PassItOn.
0 views • 10 slides
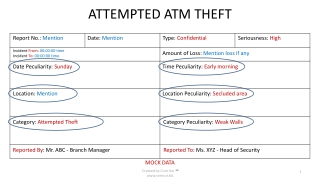
Attempted ATM Theft Incident Report
An attempted theft at an ATM located in a bank branch was unsuccessful but resulted in significant damage. Quick action by bank staff, including retrieving screenshots from backup, aided in the apprehension of the perpetrators. Recommendations were made to enhance security measures at ATM locations.
0 views • 4 slides
Global Mobility and Legal Identity Strategy Presentation
Explore the significance of legal identity and global mobility in the context of migration and border management as presented by Mme. Mariama Mohamed Cisse, Director at IOM Special Liaison Office to the AU and ECA. The presentation addresses frameworks, principles, and strategies for ensuring legal
3 views • 14 slides
Global Identity Verification Market Size & Analysis _ BIS Research
The Global Identity Verification Market has witnessed exponential growth in recent years, driven by factors such as increasing instances of identity theft, regulatory compliance requirements, and the growing adoption of digital platforms. According to BIS market research the global identity verifica
10 views • 4 slides
United Nations Legal Identity Agenda and Civil Registration Guidelines
The United Nations Legal Identity Agenda aims to ensure legal recognition for all individuals through civil registration systems. This initiative, aligned with the 2030 Agenda for Sustainable Development, emphasizes birth registration and legal identity as fundamental rights. The agenda encompasses
1 views • 10 slides
Understanding Cyber Crimes and Remedies in Gangtok by Himanshu Dhawan
Explore the world of cyber crimes and available remedies as presented by Advocate Himanshu Dhawan. Learn about different categories of cyber crimes, examples of financial and non-financial cyber crimes, data theft, and relevant sections of the IT Act, 2000. Gain insights into unauthorized access, da
1 views • 9 slides
Protecting Against Financial Scams: Insights & Prevention
Learn how to safeguard your finances from scams and identity theft. Discover the impact of scams on US citizens in 2019, the age group most affected by identity theft, the state with the highest identity theft reports, and the common delivery methods of scams. Gain valuable insights to protect yours
0 views • 27 slides
Understanding White-Collar Crimes and Theft Offenses
Exploring the world of white-collar crimes and theft offenses, including common examples like embezzlement and fraud. Learn about larceny, robbery, burglary, and more, with insights on criminal acts, required state of mind, and motives behind such offenses.
0 views • 23 slides
Understanding the Red Flags Rule for Identity Theft Prevention
Learn how the Red Flags Rule aims to detect, prevent, and mitigate identity theft. Explore the goals of this training, identify red flags of potential fraud, and understand the application of the rule to financial institutions and creditors. Discover what covered accounts are and how to create unit-
2 views • 15 slides
United Nations Legal Identity Agenda: Achieving SDG 16.9
The United Nations Legal Identity Expert Group (LIEG) aims to close the global legal identity gap by over 300 million within four years. The group focuses on implementing a life-cycle approach to legal identity, starting from birth, to ensure no one is left behind. The structure and strategy of LIEG
0 views • 10 slides
Understanding Section 390 of the Indian Penal Code on Robbery
Section 390 of the Indian Penal Code discusses the concept of robbery and its elements of theft and extortion. It outlines that robbery involves imminent danger or the use of violence, and the offender voluntarily causes harm or induces fear to commit the crime. The section also provides explanation
0 views • 7 slides
Organizational and Managerial Issues in Logistics
This chapter delves into various organizational and managerial issues in logistics, covering topics such as organizational structure, productivity, quality, theft management, logistics social responsibility, reverse logistics, and programs to counter terrorism impact on logistics. Key terms and conc
0 views • 37 slides
If truly stolen crypto can be recovered in some way, can someone share the steps
1. Identify the Theft\n\nThe first step in recovering stolen cryptocurrency is to accurately identify and document the theft. This involves:\n\nNoticing unauthorized transactions in your wallet or exchange account.\nRecording all relevant transaction IDs, wallet addresses, and timestamps.\nCollectin
0 views • 15 slides
Protect Yourself from Identity Theft: Tips and Information
Learn about identity theft, how to spot it, major credit bureaus, keeping personal information secure, identity monitoring services, and ways to protect yourself from becoming a victim of identity theft.
0 views • 8 slides
The Importance of Digital Identity in Modern Society
Digital identity plays a crucial role in modern society by enabling secure online services and verification processes. Identity management forms the foundation for moving services online, providing a means to verify individuals in a completely digital environment. The Pan-Canadian Trust Framework fo
0 views • 16 slides
Police Report: Theft of Amazing Robot
Mr. Silvester reported the theft of his 12-speed metallic blue Trek mountain bike, detailing the circumstances and security measures taken prior to the incident. The locked garage was found forced open with the missing bike bearing a security tag. The police investigation uncovered evidence suggesti
0 views • 10 slides
Understanding and Preventing Identity Theft in Daily Life
Learn how to safeguard your personal info and prevent identity theft with practical, everyday tips.\n
2 views • 5 slides
Challenges and Impact of Stock Theft in Kenya: Lessons and Future Directions
Agricultural crime, particularly stock theft in Kenya, poses significant challenges affecting rural communities and the national economy. Livestock theft, a prevalent form of agricultural crime, not only results in financial losses but also undermines rural livelihoods and community cohesion. Despit
2 views • 15 slides
Safeguarding Against Identity Theft: Prevention and Remediation
Identity theft is a serious threat where personal information is stolen for malicious purposes like setting up accounts or accessing funds in your name. This guide explains what identity theft is, why you should be concerned, how thieves obtain information, signs of being a victim, and preventive me
0 views • 22 slides
Protect Yourself: Identity Theft and Consumer Protection Insights
Explore the realms of identity theft, consumer protection laws, and fraud prevention strategies. Learn about consumer rights and responsibilities, ways to avoid financial scams, and agencies providing assistance. Discover the importance of safeguarding personal information to prevent fraud and ident
0 views • 21 slides
Redefining Irish Identity in a Globalized World
Exploring the complexities of Irish identity in a post-colonial, globalized society through the lenses of cultural fragmentation, intercultural exchange, and the evolving narratives of contemporary Irish playwrights. The discourse delves into the challenges of maintaining a distinct Irish identity w
2 views • 15 slides
Understanding Theft Offences: Elements and Case Law
Theft offences, including theft and robbery, are defined under the Theft Act 1968. A person is guilty of theft if they dishonestly appropriate property belonging to another with the intention to permanently deprive them of it. The elements of theft involve actus reus (appropriation) and mens rea (di
0 views • 26 slides
Understanding Digital Identity in the Modern Age
Exploring the concept of digital identity, this content delves into the various forms it takes, such as personal information and online behaviors. It discusses the learning outcomes related to digital identity in educational settings, including analyzing bias in digital texts and understanding emplo
0 views • 7 slides
Insights into Identity Theft Trends in Michigan
Explore the complex world of identity theft through a lens focused on Michigan. Discover the tactics and methods used by thieves to exploit personal information for financial gain. Learn about the rise of stolen identity markets and the impact on individuals and authorities. Delve into cases reveali
0 views • 23 slides
Safeguarding Against Fraud and Identity Theft: Essential Tips
Learn how to protect your private information and prevent fraud and identity theft with insights from Pete Begin, VP Senior Security Officer at Mascoma Bank. Discover crucial precautions to reduce the risk of NPPI exposure and understand how identity thieves exploit vulnerabilities like unlocked com
0 views • 25 slides
Understanding Robbery: Elements, Definition, and Distinctions
Robbery, defined under Section 8 of the Theft Act 1968, involves the act of stealing with the use of force or threat of force. This offense carries serious consequences, including a potential life imprisonment sentence. The key elements of robbery include the actus reus of theft and force, along wit
0 views • 11 slides
Protect Yourself from Identity Theft and Financial Crimes
Learn about identity theft, how it occurs, and steps you can take to protect yourself. Discover common methods used by fraudsters and the Equifax data breach incident. Find out what to do if you've been impacted by identity theft. Enroll in the TrustedID Premier credit monitoring service for free.
0 views • 23 slides
Addressing Vehicle Theft Crisis: Compulsory Engine Immobilisers in Queensland
Australia faces a significant vehicle theft issue, with Queensland being particularly affected. The societal and individual impacts are vast, highlighting the urgent need for implementing compulsory installation of engine immobilisers in passenger vehicles to combat theft, reduce crime rates, and pr
0 views • 21 slides
Understanding Cybercrime: Types, Signs, and Prevention
Cybercrime involves various criminal activities targeting computers and networks, aiming to generate profit or cause harm. Types include website spoofing, ransomware, malware, IoT hacking, identity theft, and online scams. Signs of identity theft can manifest in credit, tax, child, medical, and crim
0 views • 6 slides
Understanding Wage Theft: A Closer Look at Violations and Consequences
Wage theft, a prevalent issue in the labor market, encompasses various violations such as not paying minimum wage, altering breaks, and misclassifying employees. The Fair Labor Standards Act of 1938 addresses these offenses with penalties, including imprisonment for repeat offenders. Studies indicat
0 views • 15 slides
Protect Yourself from Identity Theft: Tips and Actions to Take
Learn how to spot and respond to identity theft by checking your statements, credit reports, and taking immediate action if it happens. Protect your personal information and act swiftly to prevent further damage.
0 views • 11 slides
Understanding Identity Theft: Risks for Teens and How to Protect Yourself
Explore the world of identity theft and its potential impact on teenagers. Learn what identity theft entails, why teens are at risk, and the evolving tactics used by criminals. Discover how stolen identities are misused and ways to prevent falling victim to such crimes.
0 views • 41 slides
Importance of Gender Identity Data Collection in Health Surveys
Gender identity data collection is crucial for identifying health disparities among marginalized groups. National Center for Health Statistics (NCHS) emphasizes the need to include questions on sexual orientation and gender identity in surveys to address health equity. Initiatives like the NCHS Heal
0 views • 20 slides
Exploring Cultural Identity and Well-being Among Indigenous Australians
This study delves into the intricate relationship between cultural identity and well-being among Māori and Aboriginal/Torres Strait Islander Australians. It examines the impact of colonialism on identity, emphasizing the importance of connections to land, family, and kinship systems in shaping iden
0 views • 13 slides
Identity and Community Exploration in School: TLN Identity Pack Lesson
Engage students in exploring identity, diversity, uniqueness, and community with the TLN Identity Pack Lesson series. Through discussions and activities, students reflect on the meaningful people in their lives and how interactions shape identity. Utilize resources and prompts to facilitate insightf
0 views • 15 slides
Unveiling the Power of Identity in Christ
Explore the multifaceted aspects of identity and its significance from personal beliefs to finding true fulfillment in Christ. Delve into the essence of living in the fullness of a divine identity versus falling prey to identity theft, emphasizing the transformative power of God's word in shaping be
0 views • 22 slides
Combating and Preventing Organised Vehicle Crime in Belgium
The project in Belgium aims to combat and prevent organised vehicle crime through the development of a barrier model funded by the European Union. Despite a steady decline in motor vehicle theft in Belgium, challenges persist with the absence of specific expertise in law enforcement agencies and hot
4 views • 17 slides
Understanding Human Authentication and Digital Identity
Explore the complexities of human authentication, classes of countermeasures, principles, personal and digital identity, and aspects of digital identity. Dive into the philosophical problem of personal identity, different types of identities, attributes, identifiers, verifiers, and the process of id
0 views • 33 slides
Understanding Robbery: Elements and Distinctions
Robbery, as defined in Section 8 of the Theft Act 1968, involves the act of stealing accompanied by the use of force or the threat of force to instill fear in order to commit the theft. This offense is considered more serious than theft and can lead to a life imprisonment sentence. The key elements
0 views • 11 slides