Departmental Security Administrator (DSA) Training Overview
The roles and responsibilities of a Departmental Security Administrator (DSA) and how to become one. Discover how DSAs assist new employees with self-registration and access to core data systems.
1 views • 38 slides
C1000-176 Preparation Guide: IBM Cloud Advanced Architect Certification
Start here---https:\/\/bit.ly\/3ONFty4---Get complete detail on C1000-176 exam guide to crack IBM Cloud - Cloud Solutions. You can collect all information on C1000-176 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on IBM Cloud - Cloud Solutions and
4 views • 16 slides
IBM C1000-137 Study Guide: Crack Exam Easily
Start here---https:\/\/bit.ly\/3UXr2v8---Get complete detail on C1000-137 exam guide to crack IBM Systems - Storage Software. You can collect all information on C1000-137 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on IBM Systems - Storage Softwa
2 views • 16 slides
Preparation Guide: IBM C1000-127 Certification | Crack Exam | Sample Questions
Begin your journey to success with the C1000-127 certification! Click here to start: \ud83e\udc0a https:\/\/bit.ly\/3T8LTcm \ud83e\udc08\n\nDiscover comprehensive details to master the IBM Security Guardium v11.x Administrator certification. Gather all the essential information on C1000-127 tutorial
3 views • 16 slides
Elevate Success S2000-018 IBM Cloud for VMware v1 Specialty Exam Mastery
The S2000-018 exam with confidence. Master the IBM Cloud for VMware v1 Specialty certification with comprehensive study materials, practice tests, and expert guidance. Gain the skills and knowledge needed to excel in cloud computing with VMware technologies. Our resources will help you navigate thro
2 views • 6 slides
Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
Maximize Success S2000-013 IBM Cloud Satellite v1 Specialty Mastery
Elevate your career with success in the S2000-013 exam. Master the IBM Cloud Satellite v1 Specialty with comprehensive study materials, practice tests, and expert guidance. Prepare effectively for the IBM Cloud Satellite v1 Specialty exam and gain the skills and knowledge necessary to excel in cloud
1 views • 6 slides
Unlock Success S2000-012 IBM Cloud Security Engineer v1 Specialty Exam Mastery
Prepare for the S2000-012 exam with confidence. Master the IBM Cloud Security Engineer v1 Specialty certification with comprehensive study materials, practice tests, and expert guidance. Gain the skills and knowledge needed to excel in cloud security engineering. Our resources will help you navigate
2 views • 6 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Dominate 156-215.81 Exam Master Check Point Certified Security Administrator R81.20
Prepare effectively for the 156-215.81 Check Point Certified Security Administrator R81.20 exam with top-notch study materials, expert guidance, and practice tests. Dominate the certification journey with proven strategies and ensure your success in securing networks with Check Point solutions.\n\/\
1 views • 4 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Introduction to IBM Watson Explorer in Business Intelligence: University of Rome La Sapienza Course
The course at University of Rome La Sapienza introduces students to IBM Watson Explorer for Business Intelligence. It covers practical use cases, advanced BI topics, and familiarization with real software used in organizations. The schedule includes sessions on Watson Explorer features, conducting B
0 views • 34 slides
Real IBM C1000-155 Exam Questions Analysis and Answers Explained
Begin Your Journey Here: \/\/bit.ly\/3xeWMSw - Access comprehensive details on the C1000-155 exam guide to excel in IBM Cloud - Management and Platform certification. Gather all necessary information on C1000-155 tutorials, practice tests, books, study materials, exam questions, and syllabus. Streng
0 views • 16 slides
Fortinet FCP_FWB_AD-7.4 Sample Questions | Syllabus
Start Here--- \/\/bit.ly\/3WBtDfc ---Get complete detail on FCP_FWB_AD-7.4 exam guide to crack Fortinet FCP - FortiWeb 7.4 Administrator. You can collect all information on FCP_FWB_AD-7.4 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Fortinet FC
2 views • 17 slides
Evolution of Operating Systems: From Mainframe Computers to Unix
Before the 1950s, users interacted directly with mainframe computers without an operating system, debugging using control panels. The transition to writing programs in symbolic languages led to the need for specific drivers. Run queues and operator-assisted job submissions marked this era. The first
0 views • 41 slides
Introduction to Decision Trees in IBM SPSS Modeler 14.2
Learn about decision trees in IBM SPSS Modeler 14.2, a powerful data mining concept for classification and prediction. Decision trees help in dividing records based on simple decision rules, making them a popular tool for data exploration and model building. Explore examples and understand the impor
1 views • 28 slides
Evolution of IBM System/360 Architecture and Instruction Set Architectures
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing by offering forward and backward compatibility, a unified instruction set architecture (ISA), and a balance between scientific and business efficiency. The critical elements of this architecture
1 views • 18 slides
Step-by-Step Guide to Host On-Demand Installation on IBM Z/OS
Comprehensive instructions for installing Host On-Demand on IBM Z/OS platform, including prerequisites, configuring in administrative mode, using Installation Manager, setting up repositories, and launching IBM Installation Manager in console mode.
0 views • 26 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
IBM System/360 Architecture Evolution
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing with its forward and backward compatibility, ISA family concept, and efficient integration of scientific and business applications. The critical elements, including compatibility design consider
0 views • 18 slides
PowerPC Architecture Overview and Evolution
PowerPC is a RISC instruction set architecture developed by IBM in collaboration with Apple and Motorola in the early 1990s. It is based on IBM's POWER architecture, offering both 32-bit and 64-bit processors popular in embedded systems. The architecture emphasizes a reduced set of pipelined instruc
2 views • 13 slides
Introduction to Neural Networks in IBM SPSS Modeler 14.2
This presentation provides an introduction to neural networks in IBM SPSS Modeler 14.2. It covers the concepts of directed data mining using neural networks, the structure of neural networks, terms associated with neural networks, and the process of inputs and outputs in neural network models. The d
0 views • 18 slides
Understanding IBM SPSS for Statistical Analysis
IBM SPSS, formerly known as Statistical Package for the Social Sciences, is a powerful software package for statistical analysis used by researchers across various industries. Developed in the late 1960s, SPSS offers features for data management, statistical analysis, and data documentation. It simp
1 views • 13 slides
APL - A Functional Language with Array Paradigms
APL, named after the book "A Programming Language Paradigms," is a functional language with a focus on array manipulation. Developed in the 1960s by Kenneth E. Iverson, it has had a significant impact on the development of spreadsheets and computer math packages. APL operates with chains of monadic
0 views • 11 slides
IBM Certified WebSphere Application Server 8.5 Administrator - Administrative Tools Overview
Learn about the various administrative tools available for managing IBM Certified WebSphere Application Server 8.5. Explore ways to administer through admin consoles, command line utilities, scripting, and JMX programs. Understand the importance of admin consoles, different types available, and how
1 views • 26 slides
Enhancing Enterprise Security and Efficiency with IBM Endpoint Manager - BigFix
Discover the benefits of using IBM Endpoint Manager - BigFix, such as reducing operational overhead, managing patches efficiently, enhancing security, ensuring audit compliance, and centrally managing IT configurations. With features like quick patch deployment, machine inventory, customization opti
0 views • 18 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
0 views • 41 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
Introduction to IBM SPSS Modeler: Association Analysis and Market Basket Analysis
Understanding Association Analysis in IBM SPSS Modeler 14.2, also known as Affinity Analysis or Market Basket Analysis. Learn about identifying patterns in data without specific targets, exploring data mining in an unsupervised manner. Discover the uses of Association Rules, including insights into
0 views • 18 slides
Helpful IBM i Tips and Techniques Presented by Laura and Community Members
A collection of helpful tips and techniques for IBM i users, shared by Laura and other community members. The tips cover topics such as managing disk utilization, utilizing the QADBIFLD file for system information, and a command created by Greg Shefferly to find source code efficiently. Includes pra
0 views • 33 slides
IBM Spectrum Scale Software Support Update and Problem Avoidance Overview
Expanding support team in China, improving time zone coverage, enhancing problem classification, and implementing best practices in problem avoidance are key focuses of IBM Spectrum Scale Software Support. With a dedicated team in Beijing, response times for production outages have decreased, leadin
0 views • 36 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Streamlining Operational Risk Management with IBM OpenPages
Partnering with ITech GRC, a Premier IBM OpenPages Partner, ensures that your business can implement, customize, and support this powerful tool effectively. Our team can help you put the \u201c4 Ps\u201d into action, keeping your business proactive,
2 views • 1 slides
Introduction to IBM SPSS Modeler 14.2 Data Mining Concepts
The article provides an overview of data mining concepts using IBM SPSS Modeler 14.2, including modules, definitions, reasons for data mining in customer-centric organizations, and the current importance of data mining. Data mining is explained as the process of discovering correlations and patterns
0 views • 14 slides
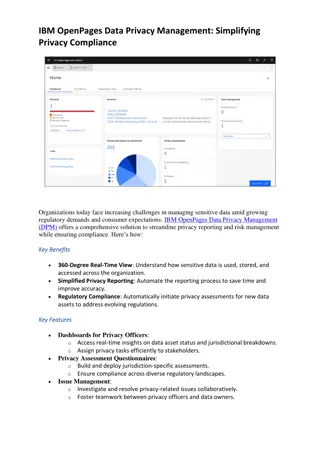
IBM OpenPages Data Privacy Management
Organizations today face increasing challenges in managing sensitive data amid growing regulatory demands and consumer expectations. IBM OpenPages Data Privacy Management (DPM) offers a comprehensive solution to streamline privacy reporting and risk
4 views • 2 slides
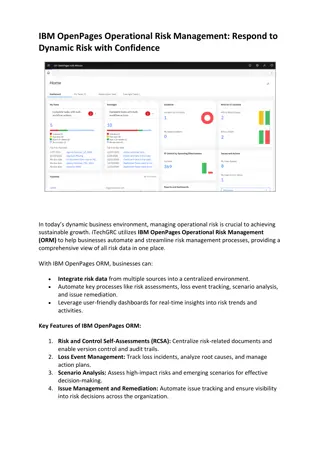
IBM OpenPages Operational Risk Management
Discover how iTechGRC leverages IBM OpenPages Operational Risk Management (ORM) to automate risk identification, monitoring, and analysis. Get a consolidated view of your risk data and streamline decision-making with key features like RCSA, loss even
0 views • 2 slides