The English language test for healthcare professionals
OET assesses English language skills for healthcare professionals. It replicates skills needed for effective communication in healthcare, covering speaking, listening, reading, and writing. Designed to simulate workplace tasks, it's taken by various healthcare professionals like doctors, nurses, den
3 views • 14 slides
How to Protect Your On-Demand App from Cyberattacks and Data Breaches
On-demand app development solutions provide convenient services but also carry cybersecurity risks like hacking, malware, and data breaches. This comprehensive guide explores best practices to secure on-demand apps and protect sensitive user data. Learn how encryption, multifactor authentication, ac
0 views • 4 slides
The Impact of Telehealth on Healthcare Delivery
Telehealth, the delivery of healthcare services remotely through technology, is gaining significance in the healthcare industry. With the increasing demand for accessible and affordable care, telehealth offers innovative solutions to improve patient outcomes, reduce costs, and enhance convenience. I
1 views • 23 slides
Data Guardianship_ Securing Sensitive Documents
The modern day digital world deals with data breaches and cyber threats, that\u2019s why the importance of secure document management in Los Angeles, cannot be overstated. Whether you\u2019re a small business owner, a healthcare professional, or an individual handling personal information, ensuring
9 views • 6 slides
MedLink Healthcare Job Posting pdf
\"MedLink is a groundbreaking platform dedicated to connecting healthcare professionals and institutions, transforming healthcare hiring. Our exclusive job platform serves as the ultimate bridge between jobseekers and a wide range of healthcare institutions, including hospitals, clinics, and provide
0 views • 8 slides
Privacy Breach Management Guide by Health PEI
Understanding, Preventing, and Managing Privacy Breaches in Healthcare: Learn about what constitutes a privacy breach, how to prevent breaches, steps to determine and manage breaches effectively, including containment, investigation, and notification processes.
0 views • 10 slides
Understanding Data Use Agreements (DUAs) in Sponsored Projects Office
Data Use Agreements (DUAs) are contractual agreements between data providers and recipients, ensuring proper handling of non-public data, especially data subject to restrictions like HIPAA. DUAs address data use limitations, liability, publication, exchange, storage, and protection protocols. HIPAA
6 views • 19 slides
Cyber Data Breach Review_ A Comprehensive Insight with LDM Global in the USA
In today's digital landscape, cyber data breaches pose significant threats to organizations of all sizes. A cyber data breach can result in severe financial losses, reputational damage, and legal ramifications. To navigate these challenges effectively, companies turn to expert services like those pr
1 views • 13 slides
Importance of Philanthropy in Healthcare
Philanthropy plays a crucial role in healthcare, fostering partnerships between medical staff and grateful patients. Grateful patients and families contribute significantly to healthcare philanthropy, driving donations that support medical institutions and patient care. As healthcare costs rise and
3 views • 16 slides
Lessons from Recent Data Breaches: Insights and Strategies
This presentation covers the landscape of data breaches, leading causes, and steps to take when facing a cyber incident. It discusses the impact of large-scale cyber attacks by external threat actors, outlines key considerations for response, and provides tips for notifying affected individuals to m
2 views • 20 slides
Ransomware and Data Breaches in Public Libraries Analysis
Delve into the world of ransomware and data breaches in public libraries, exploring the definitions of ransomware and data breaches, the potential impacts on libraries, the financial losses incurred, and the value of library records. Understand the risks, implications, and consequences associated wi
0 views • 21 slides
Enhancing University Information and Records Management for Strategic Advancement
The University's continuous improvement strategy for 2020 focuses on managing information and records effectively to mitigate risks associated with data processing. Information is deemed a critical asset, and risks range from data breaches to operational disruptions. To address these challenges, an
1 views • 21 slides
Data Protection Incidents and Fines: Lessons Learned
Learn from real-life data protection scenarios that led to fines and breaches, such as improper data handling with USB devices, confidential files ending up in public recycling, misdirected emails of sensitive data, and unsecured mobile devices leading to theft. Understand the consequences and best
0 views • 9 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Special Audit Report on Caribbean Maritime University (CMU) - December 2019
The special audit report on Caribbean Maritime University revealed unsatisfactory HR practices, poor governance, deficiencies in oversight, procurement breaches, and mismanagement of contracts. Issues included inconsistent HR practices, unapproved emoluments, infrequent council meetings, and inadequ
0 views • 12 slides
Understanding Response Patterns to Data Breaches in Firm IT Investment
This research explores how firms reallocate internal IT resources in response to security breaches and the impact of these allocation patterns on future firm performance. It delves into the allocation of IT budgets, changes in IT staffing, and examines antecedents and consequences of security breach
0 views • 47 slides
Understanding the EU General Data Protection Regulation (GDPR)
This session focuses on the key elements of the GDPR, preparing for the UK's Data Protection Act implementation, the scope of GDPR, principles, individual rights, accountability, breaches, and top tips for action planning. GDPR is a crucial part of global data protection, especially for UK organizat
3 views • 156 slides
Essential Steps for Personal Data Breach Management
Detect, identify, and respond effectively to personal data breaches by containing the breach, assessing risks, notifying relevant authorities and affected individuals, and implementing measures to prevent future occurrences. Debunk common myths surrounding breach reporting and focus on mitigating ne
0 views • 5 slides
Challenges and Opportunities in Women's Healthcare Access in Georgia
The presentation to the Senate Women's Adequate Healthcare Study Committee by Dr. Catherine Bonk sheds light on the crucial aspects of women's healthcare in Georgia. It addresses daily healthcare dilemmas for women across generations, the role of OBGYNs, chronic health issues, access challenges, and
0 views • 18 slides
Louisiana Coastal Flooding Litigation Overview
The content discusses various aspects related to the Katrina Canal breaches consolidated litigation in Louisiana, focusing on the legal implications, failures in flood control measures, geology of coastal Louisiana, coastal elevations, and the impact of canal breaches on flooding in the region. It a
1 views • 30 slides
Privacy Breach Response and Reporting under the Health Information Act
Understanding privacy breaches under the Health Information Act (HIA) is crucial for organizations dealing with health data. This document outlines what constitutes a breach, mandatory notification requirements, factors to consider in determining risk of harm, and potential offences and penalties fo
0 views • 21 slides
Importance of Privacy & Data Security Training in Healthcare
Privacy and data security training in healthcare is crucial due to the interconnected nature of the industry, putting patient information at risk. Breaches have resulted in significant financial losses, emphasizing the need for mandatory training to safeguard patient privacy. Understanding responsib
0 views • 27 slides
HIPAA and Research Data Security Training for Researchers at BU Charles River Campus
This training provides essential information on how HIPAA impacts human subject research, the importance of protecting health data, reporting breaches, and utilizing BU resources. It also covers implications of HIPAA in research, national standards, consequences of breaches, and scenarios where HIPA
0 views • 37 slides
NHS Sussex Conflicts of Interest Breach Register Summary May 2024
NHS Sussex manages conflicts of interest breaches by recording and publishing them on their website. Breaches are documented with details of the nature of the breach and actions taken. In May 2024, no breaches were reported. Previous months had breaches due to late declarations of interest. Staff we
0 views • 5 slides
Privacy and Data Protection in the Digital Age
Bart van der Sloot, a Senior Researcher at Tilburg Institute for Law, Technology, and Society, specializes in Privacy and Big Data, focusing on issues such as internet intermediary liability, data protection, and internet regulation. With expertise in the General Data Protection Regulation, internat
0 views • 89 slides
Integrated Healthcare Waste Management and WASH in Healthcare Facilities
National Workshop on Integrated Healthcare Waste Management (IHCWM) and Water Sanitation & Hygiene (WASH) in Healthcare Facilities highlighted the importance of following national standards, guidelines, and strategies for effective management of healthcare waste and ensuring proper water, sanitation
0 views • 32 slides
Best Practices for Remote GBV Services - Documentation and Data Protection
This guidance focuses on phone-based case management and hotlines for remote GBV services. It covers key considerations related to documentation, data storage, and confidentiality in phone-based GBV case management and hotline services. The importance of protecting survivor information, avoiding dat
0 views • 10 slides
Data Protection Best Practices for Secure Storage and File Encryption
Safeguarding data is crucial to prevent potential risks such as lost or stolen laptops, data breaches, and unauthorized access. This involves strategies like secure storage, encryption of file systems, and sharing encrypted files with authorized users. Implementing strong password-based file encrypt
0 views • 24 slides
Anonymization Techniques in Data Privacy
Anonymizing data is crucial to safeguard privacy, prevent data breaches, and enable sharing for various use cases, such as statistics, data science, and data release. Techniques like K-anonymity aim to protect individual identities by grouping data into subsets with shared characteristics. However,
0 views • 24 slides
The Potential of AI in Healthcare and Its Implementation Challenges
AI has the potential to revolutionize healthcare by utilizing vast amounts of data for analysis and improving key healthcare activities like disease diagnosis. However, existing AI solutions are sparsely implemented due to limitations in task focus, integration into clinical processes, and electroni
0 views • 32 slides
Healthcare Utilization in Quebec Immigrants and Non-Immigrants with Chronic Hepatitis C Infection
This study, supervised by Dr. Christina Greenaway, aims to estimate and compare healthcare utilization in Quebec immigrants and non-immigrants diagnosed with chronic Hepatitis C infection. The research seeks to identify predictors of all-cause and liver-related healthcare utilization. With rising he
0 views • 25 slides
VAST: A Unified Platform for Interactive Network Forensics
VAST is a comprehensive platform designed for interactive network forensics, addressing the increasing frequency of security incidents and large-scale data breaches. It aims to provide solutions for detecting, analyzing, and preventing breaches efficiently, with features like data exploration, query
0 views • 17 slides
Data Breaches and Privacy Concerns: An Overview
Privacy expert Marilyn Prosch, Ph.D., sheds light on the significant issue of privacy, emphasizing recent data breaches in various institutions and outlining some alarming cases where sensitive information was compromised. The incidents range from stolen laptops and office break-ins to mishandling o
0 views • 34 slides
Understanding General Data Protection Regulation (GDPR)
GDPR is a legal framework implemented in May 2018 to enhance data protection rights and increase obligations for data controllers and processors. It requires compliance in processing personal data and imposes strict rules on handling data breaches. Key definitions, including personal data categories
0 views • 5 slides
Overview of OET: English Language Test for Healthcare Professionals
OET is an English language test tailored for healthcare professionals aiming to practice in English-speaking environments. It evaluates skills in speaking, listening, reading, and writing, replicating scenarios encountered in healthcare settings. Designed to assess abilities in a workplace context,
0 views • 14 slides
Understanding Ethics and Data Governance in Data Science
Evolution of data ecosystem, importance of data ethics for data scientists, and understanding data governance framework are crucial aspects covered in this content. Examples of data breaches highlight the need for ethical data collection practices, while implementing a data governance framework ensu
0 views • 77 slides
Understanding Healthcare Data Standards
Exploring the importance of protecting healthcare information, the challenges in implementing standardized protocols like HL7, and the risks associated with data breaches in the healthcare sector. The content also touches on the roles of penetration testers in ensuring the security of healthcare sys
0 views • 38 slides
Understanding Medical Law and Ethics in the Healthcare Industry
Delve into the intricate world of medical law and ethics with insights on the distinctions between laws and ethics, the significance of HIPAA regulations, and real-world examples of breaches of patient privacy. Explore the implications of non-compliance and the importance of maintaining confidential
0 views • 15 slides
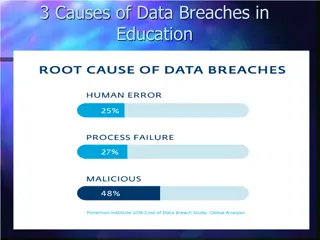
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides
Legal Issues in Data Breaches and Confidentiality Violations
The content covers various scenarios related to breach of confidence, liability of businesses in safeguarding data, and legal causes of action in case of data breaches. It discusses real-life analogies and legal principles concerning the mishandling of confidential information, including a case stud
1 views • 23 slides