Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
TEAM SWOT ANALYSIS
This comprehensive presentation template guides individuals or small groups through conducting a SWOT analysis to identify strengths, weaknesses, opportunities, and threats for a business. It includes questions to assess strengths, weaknesses, opportunities, and threats, a discussion section to dete
1 views • 8 slides
Artificial Intelligence in Cyber Security: Enhancing Threat Detection and Response
Artificial Intelligence (AI) is revolutionizing cyber security by enhancing threat detection, response, and prevention capabilities. By leveraging machine learning algorithms, AI enables organizations to identify cyber threats, analyze behavioral patterns, automate incident response, adapt to evolvi
1 views • 33 slides
Comprehensive Digital Risk Assessment Guide for Businesses
Conducting a digital risk assessment is vital for securing your business against threats like viruses, malware, hackers, and human errors. This guide outlines key areas to focus on, such as identifying critical assets, assessing potential impacts of breaches, prioritizing threats, utilizing tools li
3 views • 4 slides
Health Statistics Update and CDC Priorities
The National Center for Health Statistics (NCHS) is undergoing reorganization to better address public health threats, with an emphasis on disease control and prevention. Key changes include the establishment of the Office of Public Health Surveillance, Data, and Technology. The new CDC Director, Ma
4 views • 16 slides
Understanding Threats in Distribution Integrity Management Program
Distribution Integrity Management Program (DIMP) focuses on ensuring the integrity of pipelines by understanding and managing various threats. Operators are responsible for identifying, categorizing, and addressing potential threats such as corrosion, natural forces, excavation damage, and more to p
1 views • 39 slides
Healthcare Executive's Guide to Ransomware Threats
This comprehensive guide covers essential information on ransomware threats in healthcare, including the definition of ransomware, how it works, email and network threats, and statistics. Gain insights from Troy Ament, a seasoned CISO in the healthcare sector, to safeguard your organization against
0 views • 17 slides
Cyber Threats and Security Controls Analysis for Urban Air Mobility Environments
The Urban Air Mobility (UAM) environment, with its service-oriented architecture, faces various cyber threats related to end-users, cyber-physical systems, cloud services, and on-premise computing. Threats include unauthorized interception of data, phishing attacks, and Denial of Service (DoS) incid
1 views • 9 slides
Understanding Hybrid Threats and Resilience through Civil Preparedness
Exploring the concept of hybrid threats that combine external threats and internal vulnerabilities, this academic viewpoint by Ramon Loik emphasizes the importance of civil preparedness in building resilience against crises. It delves into aspects such as target selection, active influencing, and th
0 views • 11 slides
Common Framework on Public Health Protection and Health Security in the UK
The Common Framework on Public Health Protection and Health Security in the UK is a structured approach towards ensuring health safety across geographical regions. Originating from EU regulations, the framework addresses infectious diseases, environmental hazards, and more. It involves collaboration
0 views • 5 slides
Understanding Adversarial Threats in Machine Learning
This document explores the world of adversarial threats in machine learning, covering topics such as attack nomenclature, dimensions in adversarial learning, influence dimension, causative and exploratory approaches in attacks, and more. It delves into how adversaries manipulate data or models to co
0 views • 10 slides
Understanding Cyber Threats and the Role of Defenders in Organizations
Explore the world of cyber threats, including phishing, malware, and data breaches, and understand the importance of being a defender in your organization. Learn about key security mechanics, evolving threats, and the essential role of human vigilance in cybersecurity.
0 views • 17 slides
Essential Tips for Protecting Your Computer from Cyber Threats
Protecting your computer from cyber threats is crucial in today's interconnected world. By installing and regularly updating antivirus software, you can enhance your computer's security and safeguard your data from malicious attacks. Choose the right antivirus software based on recommendations, feat
0 views • 28 slides
Conservation Efforts and Threats to Biodiversity at Nolde Forest
Nolde Forest State Park, established by hosiery baron Jacob Nolde in the early 1900s, is a lush coniferous forest now dedicated to environmental education. The park faces threats to biodiversity such as natural disasters, invasive species, and human activity. Hurricane Sandy's impact in 2012 and the
2 views • 13 slides
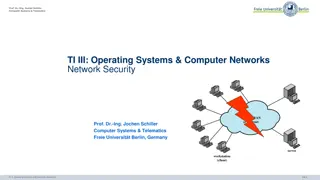
Understanding Network Security Threats and Goals in Computer Systems
Explore the concept of threats in communication networks, including examples of attacks such as hacking and data disclosure. Learn about key security goals like confidentiality, data integrity, accountability, availability, and controlled access. Discover technically defined threats like masquerade,
0 views • 32 slides
Understanding Internet Threat Landscape and Countermeasures
Delve into the complexities of identifying and mitigating threats in cyberspace at scale. Explore the challenges of detecting malicious activities, the need for broad-based blocklists, and the importance of tracking provider abuse percentages. Learn about the Pwnage Cycle, ICANN's efforts in measuri
0 views • 32 slides
Coastal Challenges: Threats and Uses Analysis
The Year 9 Geography homework booklet focuses on the topic of coasts, emphasizing grid references and mapping skills. Students are tasked with identifying grid references for shapes, drawing specific shapes on grids, and demonstrating understanding of 4 and 6 figure grid references. Additionally, in
0 views • 13 slides
Understanding Security Threats and Countermeasures
Explore the diverse threats posed by attackers in the information security landscape, ranging from employee sabotage to hacking incidents. Learn about fundamental security terminology, types of security compromises, and countermeasure strategies to prevent, detect, and correct security breaches. Gai
0 views • 32 slides
Enhancing One Health Leadership Skills and Competencies for Emerging Pandemic Threats
This collection of images and competency matrix highlights the essential skills and competencies required for effective leadership in One Health, particularly in the context of the Emerging Pandemic Threats Program. It emphasizes the importance of predicting, responding to, preventing, and identifyi
0 views • 7 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
IPv6 Security and Threats Workshop Summary
David Kelsey from STFC-RAL presented on IPv6 security and threats at the IPv6 workshop pre-GDB at CERN in June 2016. The workshop covered topics such as IPv6 protocol attacks, issues for site network security teams and sys admins, new features of IPv6, security pros and cons, immediate IPv6 concerns
0 views • 29 slides
Mobile Issues and Cyber Threats in Nigeria - Presentation by Dr. J.O. Atoyebi, NCC
Evolution of GSM in Nigeria, the impact of mobile phone deregulation, and the rise of cyber threats highlighted in a presentation by Dr. J.O. Atoyebi of the Nigerian Communications Commission. The report reveals Nigeria's position in global internet security threats and the challenges faced by the c
0 views • 7 slides
Understanding Computer Threats and Security Measures
Computer threats are constantly evolving, posing risks such as unauthorized access, data manipulation, and cyber-attacks. This chapter discusses various types of threats to users, hardware, and data security measures to mitigate these risks. Learn about identity theft, malware, cyber terrorism, and
0 views • 21 slides
Nuclear Security and Regulatory Oversight in the Slovak Republic
The Nuclear Regulatory Authority of the Slovak Republic is addressing new challenges in nuclear security, including threats such as drones and cyber attacks. They are working on updating legislation and implementing countermeasures to safeguard nuclear facilities. The focus is on enhancing cyber sec
0 views • 17 slides
Recognizing and Preventing Insider Threats in National Security
Insider threats pose a significant risk to national security and industry, involving individuals using authorized access to carry out harmful actions. This content covers the definition of insider threats, indicators, consequences, and ways to recognize and report suspicious behaviors. It emphasizes
0 views • 15 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Understanding Cloud Security Threats and Vulnerabilities
Explore the world of cloud security through the eyes of Dr. Liang Zhao, focusing on mobile security, WLAN security, and cloud threats. Learn about threat modeling, mitigating cloud vulnerabilities, and common threats such as data leakage, insecure interfaces, and more. Discover practical threat anal
0 views • 18 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Comprehensive Guide to SWOT Analysis in Business
SWOT analysis is a strategic planning tool used to evaluate the Strengths, Weaknesses, Opportunities, and Threats of an organization or a business. It helps in identifying key issues, building on strengths, minimizing weaknesses, seizing opportunities, and counteracting threats. By focusing on turni
0 views • 18 slides
Challenges and Threats in E-Commerce: Ghana's Perspective
E-commerce in Ghana faces significant barriers including technical, financial, logistical, human, and policy/regulatory factors. Cyber threats are rampant, with Ghana being vulnerable to internet fraud and cyber-crime. The country struggles with a lack of infrastructure, financial investment, litera
0 views • 11 slides
Understanding Cyber Threats in Today's Digital Landscape
Cyberspace is a vast realm encompassing the Internet, where we engage in various activities ranging from communication to entertainment. With the majority of children exposed to the online world, cybersecurity awareness is crucial to tackle the rising cyber threats. These threats include job frauds,
0 views • 33 slides
National Security Challenges and the Road Ahead
General Barry R. McCaffrey, a retired four-star General, discusses long-term international security challenges including Chinese naval and air power in the South China Sea, North Korean threats, Iranian threats, Russian border expansion, cyber-threats, nuclear proliferation, international terrorism,
0 views • 13 slides
Understanding Computer System Security Threats and Malware Types at Eshan College of Engineering
Explore the world of computer system security threats and malware at Eshan College of Engineering through insightful presentations prepared by Associate Professor H.K. Sharma from the CS Department. Learn about security threats like intrusion, phishing, spyware, spam, and malware categories such as
0 views • 13 slides
Safeguard Your Business from Digital Threats
Protecting yourself and your business from digital threats is crucial in today's cyber landscape. Learn how to control your information, recognize security threats like malware and phishing, and take proactive measures to enhance your online security defenses. By following these guidelines, you can
0 views • 5 slides
Understanding Experiments and Threats to Validity
Explore the world of experimental research, internal and external validity, threats to validity, and the importance of proper study design in ensuring the credibility of research results. Learn about confounding variables, threats to internal validity such as environmental factors and group comparis
0 views • 15 slides
EU4Health Programme: Transforming Public Health in Europe
The EU's financial strategy and priorities in the health domain are highlighted through the EU4Health programme, aiming to enhance public health in Europe. The HaDEA is actively involved in improving health in the Union, protecting against cross-border health threats, ensuring availability of afford
0 views • 11 slides
Navigating Current and Emerging Cyber Threats: Leadership Insights
Delve into the realm of current and emerging cyber threats with a focus on leadership considerations. Understand the evolving landscape of cyber risks, the importance of cyber expertise in leadership planning, and the essential role of cybersecurity in today's digital world. Explore the various thre
0 views • 16 slides
Understanding Threats and Attacks in Information Systems
Threats and attacks pose risks to information systems through vulnerabilities that can be exploited, leading to data loss, system unavailability, and compromised security. Four primary classes of threats include unstructured threats from inexperienced individuals, structured threats from skilled hac
0 views • 21 slides
Comparison of Traditional and Cyber Threat Assessment Methodologies
In the digital age, understanding cyber threats alongside traditional threats is crucial. Cyber adversaries operate globally and are hard to identify, posing challenges for intelligence agencies. The ease of acquiring cyber skills and resources makes cyber threats dynamic and dangerous. Classical cy
0 views • 17 slides
Safeguarding Information Assets from Cyber Threats
Explore the world of protecting information assets with insights on various types of threats and computer crimes, understanding attackers, attack methods, persistent electronic threats, DDoS attacks, bot-net concepts, and utilizing reCAPTCHA for input validation. Gain knowledge on safeguarding again
0 views • 33 slides