Understanding Hash Maps: A Common Data Structure
In this module, learn about Hash Maps, a common data structure used in various programming languages like Java, C#, C++, Python, and PHP. Hash Maps allow you to store key-value pairs without duplicate keys, making it efficient for mapping relationships between data elements. Explore how to declare,
6 views • 16 slides
Quick Hash Delivery in Ottawa Canafast.ca
Craving premium hashish in Ottawa? Look no further. Our service offers prompt and discreet hash delivery right to your doorstep in Ottawa. Indulge in the finest hash products without leaving the comfort of your home.
3 views • 6 slides
Understanding Hash Join Algorithm in Database Management Systems
In this lecture, Mohammad Hammoud explores the Hash Join algorithm, a fundamental concept in DBMS query optimization. The algorithm involves partitioning and probing phases, utilizing hash functions to efficiently join relations based on a common attribute. By understanding the intricacies of Hash J
1 views • 41 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
3 views • 41 slides
Understanding Energy Transfer in Collisions
Exploring what happens to energy when objects collide, this lesson focuses on energy transfer through collisions using engaging models and investigations. Key science ideas such as the relationship between an object's speed and energy are examined, with a detailed analysis of energy movement before,
0 views • 13 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Understanding Vehicle Collisions: Causes, Types, and Injuries
Vehicle collisions involve various types such as front impacts, side impacts, and rear-end collisions, resulting in different injuries like back and head injuries, neck injuries, soft tissue damage, broken bones, and internal injuries. Understanding the causes and effects of collisions can help prev
0 views • 14 slides
Shifting Bloom Filters at Peking University, China
Explore the innovative research on Shifting Bloom Filters conducted at Peking University, China, featuring evaluations, conclusions, background information, and insights on membership, association, and multiplicity queries. The study delves into hash functions, theoretical results, and the Shifting
1 views • 25 slides
Exploring Heavy-Ion Collisions at CERN LHC: ALICE Experiment Overview
Unveiling insights into heavy-ion collisions at CERN's Large Hadron Collider (LHC) through the ALICE experiment. Delving into the status, performance, and initial results, ALICE aims to characterize the medium formed during collisions. With a collaboration of around 1000 members from 31 countries an
0 views • 29 slides
Experimental Reconstruction of Primary Hot Fragment in Heavy Ion Collisions
Investigation into primary hot fragment reconstruction at Fermi energy heavy ion collisions, utilizing experimental data and simulations to reconstruct excitation energy, mass, and charge of primary fragments. Techniques like kinematical focusing and isotope identification were employed, with a focu
0 views • 36 slides
Insights into Quarkonium Production in Nuclear Collisions by Dhruv Dixit
Quarkonium mesons, such as Charmonium and Bottomonium, provide crucial information in understanding the effects of nuclear matter on their production in proton-nucleus collisions. These mesons, composed of quark-antiquark pairs, exhibit different behaviors in hot mediums, making them valuable probes
0 views • 11 slides
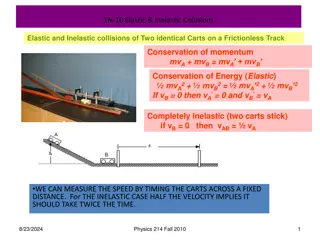
Understanding Elastic and Inelastic Collisions in Physics
Exploring the concepts of elastic and inelastic collisions, momentum, impulse, and energy conservation in physics. Topics include measuring speed, advantages of airbags, impact of catching objects, and understanding forces in collisions. Images and explanations demonstrate key principles in physics.
1 views • 25 slides
Buy Playboy Hash Online - globaldrugsstore.com
Buy Playboy Hash Online is an Indica dominant hash that originated from Morocco where it is widely known to produce some of the best hash in the world. This hash is quite potent but very easy on the throat. It smokes incredibly smooth and has a sweet
1 views • 3 slides
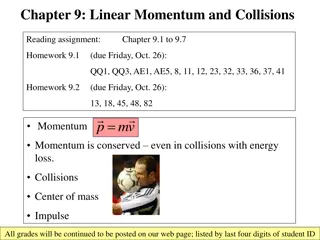
Understanding Linear Momentum and Collisions in Physics
Exploring the concepts of linear momentum, collisions, and conservation of energy in physics, this content covers topics such as momentum definition, conservation laws, impulse, types of collisions, and examples of perfectly inelastic and elastic collisions. It also includes a practical blackboard e
0 views • 17 slides
Understanding Momentum and Collisions in Physics
Momentum plays a crucial role in analyzing collisions, where objects exert forces on each other over short time intervals. Conservation of momentum, following Newton's laws, allows predicting outcomes in collisions by redistributing momentum among objects. The concept is illustrated through examples
0 views • 25 slides
Understanding Distributed Hash Tables in Peer-to-Peer Systems
Distributed Hash Tables (DHTs) are a fundamental component in organizing nodes in peer-to-peer networks. By using hash functions to assign keys to peers, DHTs enable efficient storage and retrieval of objects. Peers in a DHT are responsible for storing and managing key-value pairs, with each key bei
0 views • 31 slides
CSE 373 - Hashing Concepts and Exam Preparation
Introduction to hashing in CSE 373, covering basic concepts, hash functions, collision resolution, and runtimes. Exam details for Friday's practice exam include topics on Stacks, Queues, BigO Notation, Heaps, Trees, Design Tradeoffs, and exam format with emphasis on theoretical understanding. Lectur
0 views • 38 slides
Kompetisi Fungsi Hash NIST (SHA-3): Proses Pemilihan Finalis dan Detail Desain
Seperti sejarah AES, National Institute of Standards and Technology (NIST) menyelenggarakan kompetisi terbuka untuk mengembangkan fungsi hash baru yang disebut SHA-3. Kompetisi ini diadakan dari tahun 2007 hingga Oktober 2012. Proses pemilihan terdiri dari 2 putaran dan babak final dengan total 64 s
0 views • 17 slides
Post-Quantum Security of Hash Functions Explained
Explore the intricacies of post-quantum secure hash functions, their properties, surprises, and implications in quantum settings. Delve into collision resistance, pseudo-random generators, efficient signatures, and more, presented by Dominique Unruh from the University of Tartu.
0 views • 23 slides
Comparison of ALOHA, Slotted ALOHA, and CSMA Protocols
ALOHA is a basic protocol where stations can transmit at any time, which leads to collisions. Slotted ALOHA organizes time into slots to reduce collisions and increase efficiency. CSMA uses carrier sensing to avoid collisions. Each protocol has its advantages and limitations in handling network traf
0 views • 17 slides
Understanding Momentum, Impulse, and Collisions in Physics
Learn about momentum, impulse, and collisions in Chapter 8 of physics. Understand how linear momentum, impulse, and the Impulse-Momentum theorem are crucial in analyzing collisions and conservation of momentum. Explore real-world applications in sports and scenarios like a child driving a bumper car
0 views • 19 slides
Understanding Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
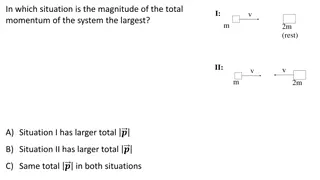
Momentum and Collisions Explained Through Illustrations
Explore various scenarios involving momentum, collisions, and elastic interactions through illustrated examples. Understand concepts such as total momentum in different situations, speeds of masses after collisions, momentum conservation in 1-D and 2-D collisions, and changes in momentum direction.
0 views • 28 slides
Understanding Distributed Hash Table (DHT) in Distributed Systems
In this lecture, Mohammad Hammoud discusses the concept of Distributed Hash Tables (DHT) in distributed systems, focusing on key aspects such as classes of naming, Chord DHT, node entities, key resolution algorithms, and the key resolution process in Chord. The session covers various components of D
0 views • 35 slides
Overview of Peer-to-Peer Systems and Distributed Hash Tables
The lecture discusses Peer-to-Peer (P2P) systems and Distributed Hash Tables, exploring their architecture, benefits, adoption in various areas, and examples such as BitTorrent. It covers the decentralized nature of P2P systems, the challenges they address, and the advantages they offer including hi
0 views • 56 slides
Evolution of Peer-to-Peer Networks and Distributed Hash Tables
Peer-to-peer networks and distributed hash tables have evolved significantly over the years, from the early days of ARPANET to the emergence of decentralized systems like Chord, Kelips, and Dynamo. This evolution has brought about a shift towards greater decentralization, improved scalability, and e
0 views • 39 slides
Understanding Overlay Networks and Distributed Hash Tables
Overlay networks are logical networks built on top of lower-layer networks, allowing for efficient data lookup and reliable communication. They come in unstructured and structured forms, with examples like Gnutella and BitTorrent. Distributed Hash Tables (DHTs) are used in real-world applications li
0 views • 45 slides
Quarkonium in Medium and Transport in Heavy-Ion Collisions
Discussing the properties and behavior of quarkonium in medium and its transport in heavy-ion collisions. Topics include heavy-quark potential, confinement, quarkonia at finite temperature, quarkonium transport, and quarkonia in heavy-ion collisions. Insightful details about in-medium potential and
0 views • 30 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
Understanding Hash Functions in Data Structures
Hash functions are crucial in storing data efficiently by converting a sized amount of data into a single integer. They are used to generate hash values, hash codes, or hash sums, which serve as indexes in arrays. The hash function should be quick to compute and distribute hash addresses uniformly t
0 views • 200 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Exploring Parton and Nucleon Interactions in Hadronic Collisions
Discussions at the GDR QCD workshop covered a range of topics from double parton scattering to coherent processes on nuclei, emphasizing the importance of understanding parton interactions in both proton-proton and heavy ion collisions. Theoretical frameworks such as DPS, SPS, GPDs, and TMDs were ex
0 views • 12 slides
Understanding the Relationship between Decisional Second-Preimage Resistance and Preimage Resistance in Cryptographic Hash Functions
This work delves into the subtle question of when Decisional Second-Preimage Resistance (SPR) implies Preimage Resistance (PRE) in hash functions. It presents a tool for enabling tight security proofs for hash-based signatures by exploring the success probability of adversaries against collision res
0 views • 25 slides
Foundations of Cryptography: Digital Signatures and Collision-Resistant Hash Functions
Foundations of Cryptography explores the construction of digital signature schemes and collision-resistant hash function families using one-way functions and safe primes. The content delves into the concept of collision-resistant hash functions and their construction from the discrete logarithm prob
0 views • 31 slides
Foundations of Cryptography: Lecture 12 - Digital Signatures and Collision-Resistant Hash Functions
The lecture covers the construction of collision-resistant hash functions from discrete log, the security behind it, and the implications for digital signature schemes. It delves into the theoretical foundations of cryptography, showcasing the interplay between one-way functions, hash functions, and
0 views • 25 slides
Understanding Hash Tables and Handling Collisions
This content covers the concepts of hash tables, handling collisions, and efficient implementation of dictionary operations. It explores methods like direct-access tables, converting keys to non-negative integers, and using functions to work with non-integer keys. The discussion includes approaches
0 views • 32 slides
Physics Practice Problems: Collisions and Conservation of Momentum
In this physics practice set, various scenarios of collisions involving objects of different masses and velocities are presented. The problems explore concepts such as momentum conservation and the calculation of final velocities after collisions. Each scenario provides a detailed explanation and so
0 views • 33 slides
Quarkonia Suppression in High Energy Heavy Ion Collisions by Roland Katz
Investigating the phenomenon of Quarkonia suppression in high energy heavy ion collisions, Roland Katz explores the properties of Quark Gluon Plasma and the behavior of quarks and gluons under extreme conditions. The study delves into the dynamics using the Schrödinger-Langevin equation, highlighti
0 views • 23 slides
Understanding Hash Tables and Hashing Concepts in Computer Algorithms
This content delves into the concept of Hash Tables, covering topics such as the support for dictionary operations, achieving constant time through direct address tables, case studies in web server maintenance, and an exploration of hashing functions and collision avoidance. It also touches upon key
0 views • 40 slides