H3C GB0-192 Certification: A Comprehensive Study Plan
Start Here--- https:\/\/bit.ly\/3HCewZV ---Get complete detail on GB0-192 exam guide to crack H3C Certified Network Engineer for Routing & Switching Plus (H3CNE-RS ). You can collect all information on GB0-192 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your kn
5 views • 17 slides
H3C GB0-392 Success Blueprint: Your Journey's Finale
Start Here--- https:\/\/bit.ly\/3SBX6Sg ---Get complete detail on GB0-392 exam guide to crack H3C Certified Senior Engineer for Routing & Switching Plus (H3CSE-RS ). You can collect all information on GB0-392 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your kno
1 views • 17 slides
H3C GB0-713 Exam All You Need To Know
Start Here--- https:\/\/bit.ly\/49yIgna ---Get complete detail on GB0-713 exam guide to crack H3C Certified Network Engineer for Cloud (H3CNE-Cloud). You can collect all information on GB0-713 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on H3C Ce
4 views • 19 slides
GB0-510 Exam Prep: A Comprehensive Study Plan | Sample Questions
Start Here --- https:\/\/bit.ly\/3wDbi6i --- Unlock the secrets to acing the H3C GB0-510 exam and becoming a certified Security Network Engineer! This PDF is your ultimate guide to mastering the H3CNE-Security certification, focusing on the planning, design, configuration, and maintenance of securit
4 views • 16 slides
H3C GB0-601 Exam Preparation: What You Need to Know
Begin your preparation journey here--- https:\/\/bit.ly\/4c6E4N5 \ud83d\ude80. Access all the essential details to ace the H3C Certified Network Engineer for Server (H3CNE-Server) exam. Gather all the necessary information, including tutorials, practice tests, books, study materials, exam questions,
5 views • 19 slides
H3C GB0-372 Exam Preparation Study Guide
Begin your journey towards success in the H3C Certified Senior Engineer for Routing & Switching Plus (H3CSE-RS ) exam by accessing comprehensive details at https:\/\/bit.ly\/49Lxgmp. Obtain a thorough understanding of the GB0-372 exam with valuable insights into tutorials, practice tests, recommende
2 views • 17 slides
Master GB0-372 Ace H3C Advanced Routing & Switching Technology 1 Exam
Elevate your career with success in the GB0-372 exam. Master H3C Advanced Routing and Switching Technology 1 with our comprehensive study materials, practice tests, and expert guidance. Prepare effectively for the H3C GB0-372 exam and gain the skills and knowledge necessary to excel in advanced rout
2 views • 8 slides
H3C GB0-382: Essential Study Plan and Resources
Begin Here--- \/\/bit.ly\/3wWcmTa ---Access comprehensive details on the GB0-382 exam guide to excel in the H3C Certified Senior Engineer for Routing & Switching Plus (H3CSE-RS ) certification. Gather all the necessary information on GB0-382 tutorials, practice tests, books, study materials, exam qu
2 views • 17 slides
H3C GB0-382: Essential Study Plan and Resources
Begin Here--- \/\/bit.ly\/3wWcmTa ---Access comprehensive details on the GB0-382 exam guide to excel in the H3C Certified Senior Engineer for Routing & Switching Plus (H3CSE-RS ) certification. Gather all the necessary information on GB0-382 tutorials, practice tests, books, study materials, exam qu
0 views • 17 slides
Understanding Cloud-Optimized HDF5 Files for Efficient Data Access
Explore the benefits and features of Cloud-Optimized HDF5 files, such as minimal reformatting, fast content scanning, and efficient data access for both cloud-native and conventional applications. Learn about chunk sizes, variable-length datatypes, internal file metadata, and best practices for opti
3 views • 25 slides
Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
Pedagogical Shift in Physical Science: Constructing Knowledge Through Learner-Centered Experiences
There is a significant pedagogical shift in physical science education from viewing science as a fixed body of knowledge to emphasizing the process of constructing knowledge. Learners are now placed at the center stage, engaging in inquiry-based learning, critical thinking, and collaborative interac
3 views • 21 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
Your Ultimate Guide to Constructing Windows
Windows are vital in home design, offering natural light, ventilation, and aesthetic appeal. This guide delves into the essential aspects of constructing windows, including types, materials, and design considerations. It highlights the importance of
1 views • 7 slides
Understanding Yes/No Questions in English Grammar
Yes/No questions in English grammar are essential for communication. These questions have two basic types - Yes/No questions and Wh-questions. Yes/No questions, also known as closed questions, have only two possible responses - Yes or No. To form a Yes/No question, verbs like BE, DO, HAVE, or modal
0 views • 9 slides
Understanding Rock Correlation Through Facies and Biostratigraphy
Explore the correlation of rocks using facies and biostratigraphy in Activity 3 of EOSC 326. Learn about constructing biozones, correlating stratigraphic logs, and interpreting paleoenvironments. Discover the significance of fossils B and F in correlation and apply techniques like seriation in const
5 views • 19 slides
Constructing Perpendiculars: Shortest Distance to a Point
Learn how to find the shortest distance from a point to a line, ensuring the path taken is efficient and direct. By constructing a perpendicular from the point to the line, you guarantee the shortest possible route, creating a right angle with the line. Explore the process of constructing perpendicu
2 views • 17 slides
Understanding Internet Connections and Services
Explore the world of internet connections and services, from local area networks (LANs) to wide area networks (WANs). Learn about the hardware and software required to connect devices, the purpose of WANs, and examples of WAN implementations in banks and the global internet.
0 views • 19 slides
Exploring Methods of Constructing Index Numbers
Various methods of constructing index numbers, such as un-weighted index, simple aggregate method, and simple average of price relatives method, are explained in detail. These methods play a crucial role in analyzing price changes over time and comparing different economic indicators. Each method of
0 views • 6 slides
Cloud-Optimized HDF5 Files Overview
Explore the concept of cloud-optimized HDF5 files, including Cloud-Optimized Storage Format, Cloud Native Storage Format, and the benefits of using HDF5 in cloud environments. Learn about key strategies like Paged Aggregation, chunk size optimization, and variable-length datatypes considerations to
1 views • 25 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Evolution of Proofs in Cryptography
Cryptography has evolved from classical proofs to interactive and probabilistically checkable proofs, enabling the development of applications like Non-Malleable and Chosen-Ciphertext Secure Encryption Schemes. Non-Malleability protects against active attacks like malleability and chosen-ciphertext
0 views • 29 slides
Efficient Cross-Engine Transactions in Skeena
Skeena presents efficient and consistent cross-engine transactions, offering solutions to challenges faced by traditional database engines. By utilizing memory-optimized database engines and a multi-engine DBMS approach, Skeena addresses issues such as high costs and compatibility concerns associate
2 views • 21 slides
Exploring Source-Routed Forwarding in SDN-Based WANs
Software-Defined Networking (SDN) in Wide Area Networks (WANs) utilizes source routing methods to address performance concerns related to network convergence time. Challenges such as latency constraints and controller placement impact performance, highlighting the need for efficient path computation
0 views • 24 slides
Understanding Local Area Networks (LAN) and IEEE Project 802
A Local Area Network (LAN) is a computer network designed for limited geographic areas, often interconnected with wide area networks (WANs) or the Internet. IEEE Project 802 established standards for LAN protocols, focusing on the physical and data link layers. Ethernet emerged as the dominant LAN t
0 views • 27 slides
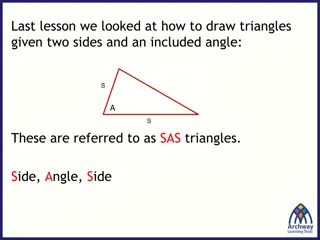
Constructing SSS Triangles: A Geometric Exercise
Explore the construction of Side-Side-Side (SSS) triangles step-by-step, using compass and straightedge techniques to draw triangles given specific side lengths. Understand the process of constructing triangles without angle information and enhance your geometric skills with practical examples.
0 views • 13 slides
Computer Networks and WANs: Week Four Overview
This week's session covers VMware View Client commands, traffic flow device configurations, Asynchronous Transfer Mode (ATM), Quality of Service (QoS), and more. Explore hands-on activities in MIMIC Virtual Lab CCNA and learn essential commands for networking tasks like configuring interfaces, debug
0 views • 70 slides
Insights on Constructing Geopolitical Risk Audit
Details on constructing the audit for the paper "Measuring Geopolitical Risk" by Dario Caldara and Matteo Iacoviello are outlined. It covers the process of building the GPR index, designing the audit sample, and coding articles to identify geopolitical risks discussed in newspapers. The methodology
0 views • 17 slides
Detailed Notes on Constructing the Audit for Measuring Geopolitical Risk
The notes provide insights into constructing the audit for measuring geopolitical risk as outlined in the paper by Dario Caldara and Matteo Iacoviello. It covers the construction of the index, design of the audit sample, reading articles, and coding them based on geopolitical risk references. The pr
0 views • 20 slides
Geometry Constructions Revision Solutions Section A
This chapter provides step-by-step instructions and solutions for constructing different geometric shapes like triangles and rectangles. Detailed guidelines are given to construct triangles with specific side lengths and angle measurements, as well as an equilateral triangle. The content also covers
0 views • 19 slides
Towards a More Programmable and Performance-Optimized Virtual Switch @ EuroP4 '21
This presentation discusses the development of a more programmable and performance-optimized virtual switch at EuroP4 '21. It covers topics such as P4 with OVS, challenges in OVS hardware offload, P4 enhanced Open vSwitch, P4 components in OVS, stacked pipelines, and various control and data planes
0 views • 10 slides
Ultra-Reliable PHY Elements: Optimized Building Blocks for Low Latency and Efficiency
The document presents a deep dive into ultra-reliable PHY elements, focusing on achieving low latency, reduced collision, and energy efficiency. It proposes optimized universal building blocks to address these goals effectively, especially in scenarios where many devices may not receive transmission
0 views • 17 slides
Optimized Content Transfer in Mesh Networks Using Bandwidth-Aware Chunking
This presentation by Gurdev Singh from Samsung addresses a technique for optimized content transfer in mesh networks by splitting content into file chunks based on the bandwidth of the channel. By considering the bandwidth or link quality of destination nodes, the content is divided so that lower ba
0 views • 20 slides
Constructing Price Index: General Procedure and Aggregation
The process of constructing a price index involves various steps such as computation of price relatives, aggregation at different levels, selection of base period, and designing data collection methods. Weighted arithmetic mean and simple ratio calculations are used in aggregating price indices. A t
0 views • 31 slides
Understanding Spatial Error in Photogrammetry
Reprojection error in photogrammetry refers to the discrepancy between a known point in a scene and its projected position on an image. Photometric error, on the other hand, involves errors related to pixel intensity values. To minimize reprojection error, parameters such as camera intrinsics, extri
0 views • 5 slides
Constructing Authentic Assessment Items: A Guide in 4 Steps
Constructing authentic assessment items involves four steps: identifying standards, selecting an authentic task, defining criteria, and creating a rubric. Standards are specific skills and knowledge students should gain. Tasks should reflect these standards. Criteria measure student mastery. Rubrics
0 views • 25 slides
Simulation Results for LC-Optimized PHY Proposal in July 2019
The document presents simulation results for an LC-optimized PHY proposal for TGbb based on G.9991 PHY. It includes details on the simulation setup, frame detection results, header modulation, coding simulation results, payload modulation, and coding simulation results. The setup involved various re
0 views • 18 slides
Optimizing Queries and Constructing Percentage Cube in Business Intelligence
Presented at ENSMA, this paper introduces optimized strategies for constructing a percentage cube to enhance processing of complex queries in modern business intelligence. It discusses challenges, comparison between percentage queries and percentage cube, and showcases a data cube analysis of car sa
0 views • 21 slides
Understanding Point-to-Point Protocol (PPP) and Serial Communications in WANs
This content explores the Point-to-Point Protocol (PPP), outlining its components, establishment of sessions, authentication protocols, and configuration. It also delves into WAN connection options, serial and parallel ports communication, and serial communication standards for LAN-to-WAN connection
0 views • 31 slides