Coordinated R-TWT Protection in Multi-BSS
The protection of Restricted Transmitting Using Time Window (R-TWT) service periods in a multi-BSS environment, where overlapping BSSs can affect the latency-sensitive traffic exchange. It proposes methods to coordinate R-TWT service periods and receive schedule information for neighboring BSSs.
3 views • 11 slides
Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
Multi-BSS Network Simulation in ns-3 with IEEE 802.11-23 Update
A status update on the WiFi module in ns-3 for IEEE 802.11-23 focusing on advancements like new protocol features, AI/ML integration, and runtime improvements for multi-BSS networks. The simulations cover throughput benchmarks, multi-BSS scenarios, interference parameters, and validation against ana
13 views • 33 slides
A Safety Expert’s Guide: How to Stack Pallets Safely
In the bustling world of warehouses, logistics, and manufacturing, the proper stacking of pallets is a critical aspect of maintaining a safe and organized workspace. As a safety expert, I\u2019ve seen firsthand the importance of implementing best practices to ensure the secure stacking of pallets. I
14 views • 2 slides
Enhancing Low Latency Channel Access in Legacy IEEE 802.11 Networks
This document discusses the impact of introducing a Low Latency (LL) channel access mechanism in legacy IEEE 802.11 networks. It addresses the use of High Priority EDCA (HiP EDCA) mechanisms, proposing solutions for improving tail latency in both isolated BSS and multi-BSS scenarios. Additionally, i
4 views • 10 slides
Piezoelectric Stack Actuator Market Analysis, Size, Share, Growth, Trends Foreca
The Global Piezoelectric Stack Actuator market stands at the forefront of technological driving advancements in various industries through its dynamic applications. These actuator systems harness the unique properties of piezoelectric materials, providing precision and versatility in a range of mech
0 views • 8 slides
Efficient Stack Emission Monitoring Procedure for Air Quality Control
Stack emission monitoring is crucial for industries to assess and reduce pollutants in exhaust air. This procedure involves tasks like measurement, testing, and analysis of flue gases. Sampling sites are selected strategically for accurate readings, and molecular weight and gas velocity are determin
1 views • 11 slides
IEEE 802.11-20/0668r1: EHT BSS Configuration Proposal
The document discusses the configuration of a 320 MHz BSS in the context of 6 GHz regulations, focusing on EHT operation elements such as channel width indication, CCFS principles, and BSS advertisement settings. It proposes design principles for managing legacy and EHT STA operations, emphasizing s
0 views • 14 slides
Bandwidth Indication for EHT BSS in IEEE 802.11-20/0680r0
This IEEE document discusses the proposal to use an Enhanced High Throughput (EHT) operation element to indicate operating bandwidth for EHT Basic Service Sets (BSS). It suggests methods for indicating channel configurations, punctured channels, and channel width for EHT stations. The goal is to ena
0 views • 15 slides
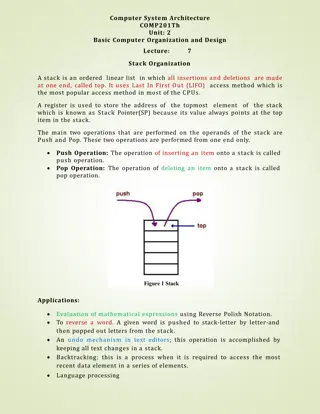
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
Understanding The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
IEEE 802.11-21/0036r0 BSS Parameter Update Clarification
This document delves into the IEEE 802.11-21/0036r0 standard, specifically focusing on the BSS parameter update procedure within TGbe D0.2. It details how an AP within an AP MLD transmits Change Sequence fields, Critical Update Flags, and other essential elements in Beacon and Probe Response frames.
1 views • 11 slides
Understanding Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
IEEE 802.11-21/1737r0 Beacon and Group Frames Information
An IEEE document from November 2021 discusses Beacon and group frames in wireless networks, focusing on out-of-band signaling to improve BSS range determination and frame reception by non-AP MLDs. It addresses the impact of frame types and MCS on BSS range and transmission rates, proposing solutions
3 views • 14 slides
IEEE 802.11-21/1737r0 Beacon and Group Frames Information
This document discusses the transmission of Beacon and group addressed frames in IEEE 802.11 networks, focusing on the impact of frame types and MCS on BSS range and transmission rate. It proposes out-of-band signaling to assist scanning STAs in determining BSS range and non-AP MLDs in selecting a l
0 views • 14 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
International Collaboration in Open Source Software: A Network Analysis Study
This research project delves into the realm of open source software (OSS) by using web scraping and network analysis to understand international collaboration dynamics. It explores the significance, scope, and impact of OSS, focusing on the structure of collaboration networks, contributions of diffe
1 views • 23 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
BSS Curriculum Committee Meeting Overview
The BSS Curriculum Committee Meeting discussed the need to update the curriculum process due to the increasing workload and impending retirement of key personnel. The meeting also compared curriculum processes in different divisions, highlighting the roles of faculty and staff in managing curriculum
0 views • 9 slides
Enhancing BSS Load Management in 802.11ax Networks
Proposed changes to address load balancing issues in dense 802.11ax scenarios by introducing a new information element for BSS Load. The new element considers OFDMA utilization, UL/DL MU-MIMO, and allows for future extensions to ensure efficient AP selection by unassociated STAs. Enhancements aim to
0 views • 14 slides
802.11aj 45 GHz Channel Access and BSS Operation Framework Proposal
This document outlines a proposal for channel operation and BSS operation in the 45 GHz frequency bands for 802.11aj in China. It includes details on channelization, spectrum allocation, maximum transmit power, and BSS configuration rules. The aim is to meet the functional requirements specified whi
0 views • 32 slides
Understanding Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
IEEE 802.11-20/0834r1: Recap of Association and Fast BSS Transition
The document presents insights into tentative (re)association for non-AP MLDs, focusing on addressing data delivery interruptions during roaming and association with new access points. It covers necessary actions before data transfer, open system authentication, association operations, and fast BSS
0 views • 17 slides
IEEE 802.11-24/0161r1 OBSS R-TWT Announcement in Multi-BSS
The document discusses the coordination of R-TWT schedules in Multi-BSS to enhance operation and protection. It covers how APs announce OBSS R-TWT schedules to associated STAs, ensuring efficient transmission of latency-sensitive traffic. Methods for announcing OBSS R-TWT schedules to EHT STAs and U
0 views • 13 slides
R-TWT Coordination Negotiation in Multi-BSS Networks
This document discusses the coordination negotiation process for R-TWT schedules in Multi-BSS networks to minimize interference between Access Points (APs). It outlines the overview, signaling methods, and importance of coordinated R-TWT schedules in improving network efficiency.
0 views • 16 slides
IEEE 802.11-23/1841r0 BSS Color Considerations for Multi-AP Networks
The document delves into the challenges of BSS color management in multi-AP setups, focusing on Joint Transmission techniques in IEEE 802.11 networks. It proposes solutions to avoid filtering PPDU transmissions due to mismatched BSS colors, potentially causing PHY preamble collisions.
1 views • 8 slides
IP Fabric Architecture for GRNET Datacenters: Automating the Future
GRNET is expanding its data center infrastructure to address existing problems, balance tested and innovative solutions, and enable VLAN stretching between data centers. The new architecture aims to enhance network efficiency and scalability by implementing an IP Fabric solution. Previous architectu
0 views • 19 slides
Announcement of OBSS R-TWT Coordination in Multi-BSS Environment
The document discusses the coordination of R-TWT service periods (SPs) in a Multi-BSS environment, focusing on addressing limitations in the exchange of latency-sensitive traffic in adjacent BSSs. It explores methods for coordinating R-TWT SPs among multiple APs to protect the intended SPs within ea
0 views • 9 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
BSS Division Council Meeting Highlights and Updates
The BSS Division Council met on November 16, 2023, discussing attendance, agenda items, and program reports. The meeting covered various topics including evaluations, annual planning, sabbaticals, and reports from different programs. It was noted that student survey results were delayed and self-eva
0 views • 14 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Building a Viable Business around Open Source Software (OSS)
Discover the opportunities and challenges of establishing a successful business model using Open Source Software (OSS) like dGB Earth Sciences did with OpendTect. Explore the benefits such as lower startup costs and a faster pace of innovation, alongside the strategies for commercializing OSS effect
0 views • 23 slides
Overview of Phaethon: LightPath Provisioning Adapter for LightSoft
Phaethon is a lightpath provisioning adapter designed for LightSoft, providing capabilities such as reconfigurable optical add-drop multiplexing and transponder filtering. It integrates with the GRNET OSS/BSS stack and facilitates operations like transforming CORBA calls to HTTP REST calls and manag
0 views • 25 slides