Active Directory Penetration Testing, cionsystems
The partner plan of AD Guardian is used by professional services which include penetration testing to test if your AD is secure from such threats. http:\/\/tinyurl.com\/4yzps5xv
1 views • 2 slides
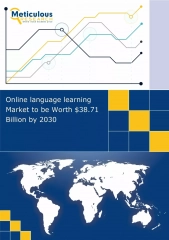
Global Online Language Learning Market to Surpass $38.7 Billion by 2030
The growth of this market is driven by globalization and the growing need for cross-border communication, the growing E-learning market, and the penetration of artificial intelligence in E-learning. The increasing expenditure on the education sector, rising internet and smartphone user base, and inc
3 views • 3 slides
India's EdTech Boom A 313 Billion Opportunity and the Challenges to Overcome
The global EdTech market is poised for exponential growth, projected to soar to USD 696.04 billion by 2028, with a robust compound annual growth rate (CAGR) of 15.22% from 2022 to 2028. This surge is fueled by a confluence of factors, including the escalating demand for education, expanding internet
3 views • 4 slides
Enhancing Interpersonal Communication Skills
Explore the dynamics of interpersonal communication in this chapter, covering topics such as social penetration theory, self-disclosure principles, intrapersonal communication, and self-concept understanding. Learn how to improve communication effectiveness and relationships through active listening
0 views • 13 slides
Energy Sector Updates and Reports Overview
The Operations Working Group and ERCOT have reported peaks in demand and renewable energy penetration for January. Updates on Texas Reliability Entity and NPRR developments including congestion mitigation strategies were discussed. The latest comments and proposed changes for NPRR 1198 and NOGRR 258
0 views • 8 slides
Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
Active Directory Penetration Testing, cionsytems.com
The partner plan of AD Guardian is used by professional services which include penetration testing to test if your AD is secure from such threats. \/\/rb.gy\/2f1rq2
4 views • 7 slides
The Case for Central Bank Digital Currency (CBDC) by G. Venkatesh
Central Bank Digital Currency (CBDC) offers numerous advantages such as scalability, safety, and potential for financial inclusion. India introduced its CBDC a year ago with goals of digitizing the economy and simplifying cross-border trade settlement. However, CBDC penetration is currently low, and
0 views • 22 slides
Active Directory Penetration Testing, cionsystems.com
The partner plan of AD Guardian is used by professional services which include penetration testing to test if your AD is secure from such threats. \/\/rb.gy\/m1wkb8
2 views • 2 slides
Luxury Safari Accommodation To Discover The Iconic Wildlife And The Natural Envi
Going on safari means stepping into a world where the heartbeat of nature echoes through the air. Every sound emanating from the foliage conceals a hidden mystery yearning to be discovered.\n\nFor more info visit: \/\/ \/kenya-safaris\/6-days-kenya-semi-luxury-safari
2 views • 6 slides
Production Technology for Ornamental Crops and Landscaping Overview
Explore the world of ornamental crops, medicinal plants, and landscaping with Dr. Mahendra Kr. Yadav's Production Technology course. Learn about different crop types, landscaping principles, flower production practices, and the importance of value addition. Delve into ornamental horticulture, floric
0 views • 15 slides
Penetration Testing and Incident Response Technologies Overview
Explore the world of penetration testing, incident response technologies, and ethical hacking in the context of CIS 6395 course at UCF. Learn about tools like Metasploitable 2 VM for vulnerability testing and techniques such as Ping Sweep and Ping. Discover essential concepts for testing and securin
0 views • 32 slides
Comprehensive Guide to Penetration Testing Execution Standard (PTES)
Penetration Testing Execution Standard (PTES) is a crucial methodology to simulate attackers' methods for compromising security controls and gaining access to systems. The PTES process involves phases such as Pre-Engagement, Intelligence Gathering, Threat Modeling, Vulnerability Analysis, Exploitati
3 views • 14 slides
Polymeric Controlled Drug Delivery Systems
Polymeric controlled drug delivery systems play a crucial role in regulating drug release through diffusion, solvent penetration, and chemical mechanisms. These systems include diffusion-controlled, solvent-controlled, and chemically-controlled devices, each operating based on specific principles. S
0 views • 33 slides
Understanding Cycas: A Detailed Look at the Morphology and Characteristics
Sixteen species of Cycas are distributed across tropical and sub-tropical regions, with India hosting six species. Cycas plants are evergreen and resemble palm trees, with unique root and stem structures. The plant body consists of an arborescent stem and distinctive leaf morphology. Cycas leaves ar
0 views • 26 slides
Disaster Recovery and Incident Response Concepts
This content covers the essential concepts of disaster recovery, incident response, penetration testing, vulnerability scanning, and business continuity planning in the context of cybersecurity. It explains the goals and steps involved in penetration testing, vulnerability scanning tasks, business c
2 views • 15 slides
Insights into the Nigerian Insurance Industry: Trends and Opportunities
The Nigerian insurance industry shows promising growth potential with low penetration rates but increasing awareness and regulatory support. Despite challenges, there has been significant growth in premiums and a shift towards a more diverse professional workforce. A comparison with similar economie
0 views • 10 slides
Shopper Insight Report - Northern Ireland Region Analysis
This Shopper Insight Report covers a 52-week period from 02/05/2016 to 30/04/2017, focusing on key performance indicators like sales growth, customer penetration, and customer loyalty. Recommendations include focusing on core stores with high demand, increasing penetration and repeat rate, and utili
0 views • 23 slides
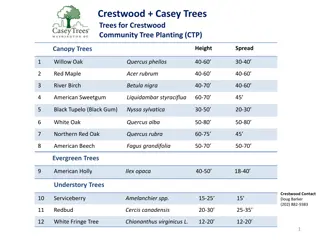
Crestwood Community Tree Planting - Tree Species Overview
Explore the diverse range of trees recommended for the Crestwood Community Tree Planting project. From majestic oaks to colorful maples, each species brings unique characteristics and benefits to the urban landscape. Learn about their heights, spreads, foliage colors, and preferred conditions to mak
1 views • 13 slides
Understanding Penetration Testing Tactics and Techniques
In the realm of secure software engineering, penetration testing plays a crucial role in proactively identifying vulnerabilities. This involves delving deep to exploit potential weaknesses and simulate real-world attack scenarios. Skilled testers, both in-house and external, use frameworks like MITR
0 views • 16 slides
Comprehensive Guide to Highbush Cranberry (Viburnum trilobum)
Highbush Cranberry, known scientifically as Viburnum trilobum, is a deciduous shrub that grows up to 12 feet tall. It features dark green leaves in summer and maroon foliage in fall, white flowers, and bright red or orange fruits that persist through winter. This plant thrives in moist and slightly
0 views • 7 slides
Honey Bee Exposure to Pesticides: Routes and Impacts
Analysis by the U.S. Environmental Protection Agency outlines various exposure routes of honey bees to pesticides, including contact with contaminated sources like foliage and soil, ingestion of contaminated pollen and nectar, and inhalation of chemical droplets. Different application types and age
2 views • 13 slides
The Influence of the West Wind on Nature: A Visual Journey
The poetic verses of "Ode to the West Wind" by Percy Bysshe Shelley vividly depict the disruptive and transformative impact of the West Wind on nature. Through captivating imagery, the poem portrays how the West Wind stirs the Mediterranean sea from its slumber, creates chasms in the Atlantic Ocean,
1 views • 20 slides
Raging Fire in the Forest: A Narrative Description
Smoke and flames engulf a forest in a vivid narrative, with verbs like festooned, stirred, and flaring bringing the scene to life. Readers witness the thrilling progression of fire through trees and foliage, evoking a sense of both danger and awe. The descriptive nouns and phrases enhance the imager
0 views • 4 slides
Study on EU Retail Sector: Drivers of Choice and Innovation
The study examines complaints of large retailers imposing detrimental conditions on food suppliers, affecting investment, choice, and innovation. Findings suggest that competition, economic environment, and bargaining power influence innovation, while private label penetration shows a negative corre
0 views • 8 slides
How to Boost Your Business with Effective Market Penetration
Market penetration is a strategy aimed at increasing a company\u2019s market share within existing markets. It involves selling more of the current products or services to existing customers and attracting competitors\u2019 customers.
0 views • 10 slides
Understanding Ultrasound Transducers: Applications and Functionality
Ultrasound transducers play a crucial role in medical imaging by converting electrical signals into ultrasonic energy for tissue penetration and image creation. This technology utilizes focused transducers to enhance resolution and penetration, while also managing beam intensity. The article delves
0 views • 24 slides
Herbicide Absorption and Translocation Mechanisms in Plants
Herbicides need to be effectively absorbed and translocated within plants to interfere with physiological and biochemical processes. Soil-applied herbicides are absorbed by roots, shoots, and seeds through different mechanisms, while foliage-applied herbicides enter through the cuticle, stomata, and
0 views • 7 slides
Comprehensive Guide to Intelligence Gathering and Penetration Testing Stages
Understanding the importance of intelligence gathering in security and the stages of penetration testing - information gathering, scanning, exploitation, and reporting. Delve into tools like nslookup for server information and leverage Google Dorks for database vulnerabilities. Safeguard your system
0 views • 4 slides
Enhancing Insurance Penetration in Ghana Through Digital Innovation
Dr. Gideon Amenyedor explores how digital insurance can enhance insurance penetration in Ghana by leveraging technology to improve existing insurance models and create new ones. The strategic application of digital technology aims to address the low insurance penetration rate in the country by consi
0 views • 18 slides
Internet Overview in the Arab Region by ARISPA
The Arab Internet & Telecom Union (ARISPA) provides a detailed overview of internet penetration rates in the Arab region, focusing on global and regional comparisons, as well as the future IPv4 situation. Founded in 2006, ARISPA works under the Arab Economic Union Council, with 20 members representi
0 views • 17 slides
Essentials of Penetration Testing: Expectations and Performance
This presentation delves into the realm of penetration testing, outlining the basic expectations and performance aspects. It emphasizes the importance of clear planning, client-side and auditor-side negotiations, and commencing the audit process diligently. With insights into the types of audits, sc
0 views • 32 slides
Late Blight Disease of Potato: Symptoms and Management
Late blight is a severe fungal disease affecting potatoes worldwide, causing foliage damage, reduced tuber yield, and decay. It is caused by Phytophthora infestans and manifests as brownish-black lesions on plant parts. The disease spreads rapidly under humid conditions, leading to blighting of foli
0 views • 8 slides
Flower Value Addition in Mamillapalli Thriveni
Value addition in flowers is a process that enhances the economic value and consumer appeal of floral commodities through genetic changes, processing, packaging diversification, and postharvest technology adoption. It not only boosts profitability but also serves as a rural development strategy, esp
0 views • 25 slides
Understanding Armitage and Metasploit for Penetration Testing
Explore the capabilities of Armitage and Metasploit in penetration testing, comparing their attack styles, advantages, and limitations. Learn how Armitage simplifies the process by providing a GUI front-end for Metasploit, making it user-friendly for conducting machine-gun style attacks. Discover th
0 views • 16 slides
Challenges in Transitioning Austrian Energy System to High Wind Energy Penetration
The transition of Austria's energy system to embrace high wind energy penetration requires consideration of various factors such as economic incentives, costs, social norms, individual values, and beliefs. Through the TransWind project, research questions are examined, including the techno-economica
0 views • 15 slides
Exploring Leaves: From FOLI to Unifoliate
Delve into the world of leaves, from the beautiful FOLIage of plants to the use of defoliants and folio in literature. Discover the significance of bifoliate orchids, the importance of folic acid, and the art of exfoliating leaves. Explore the diverse meanings and applications of leaves in various c
0 views • 11 slides
All About Sumac Trees: Features, Uses, and Care Tips
Sumac trees, known for their shrubs and small trees with clusters of reddish drupes, are commonly found in North America and Africa. These trees, comprising approximately 250 species, are used for landscaping but some species can cause skin irritation. With minimal care requirements, sumac trees can
0 views • 11 slides
Analysis of Multi-Wall Penetration Loss Model for HEW System-Level Simulation
In December 2014, a multi-wall penetration loss model for HEW system-level simulation was proposed by Kejun Zhao, Yunxiang Xu, and Xiaoyuan Lu from the National Engineering Research Center for Broadband Networks & Applications. The model provides more accurate calculations of penetration loss in ind
0 views • 11 slides
Improving Penetration Testing Through Enhanced Input Vector Identification
Enhance your penetration testing efforts by improving information gathering and response analysis. This comprehensive guide explores various aspects of penetration testing, including information gathering, attack generation, and response analysis, offering valuable insights and strategies to bolster
0 views • 23 slides