An Easy Method To Resolve QuickBooks Backup Failed Issue
Businesses that depend on QuickBooks accounting software may find it alarming when they receive a \"QuickBooks Backup Failed\" warning. Network problems, corrupted data files, and inadequate storage are examples of potential causes. Take immediate action to resolve these problems by making sure ther
5 views • 7 slides
Direct Lender Short Term Loans UK Get the Money with Just a Simple Qualification
Easy requirements like being eighteen years old, a permanent resident of the United Kingdom, employed full-time with a steady income, and having an open checking account are sufficient to easily obtain additional cash using short term loans UK direct lender.\nhttps:\/\/paydayquid.co.uk\/\n
2 views • 1 slides
Unlocking the Secrets to Finding the Best Car Service Near me
Full car service encompasses a comprehensive inspection and maintenance routine for your vehicle. From checking fluid levels to inspecting crucial components like brakes and suspension, a full car service leaves no stone unturned in ensuring your vehicle's optimal functioning.
1 views • 1 slides
Impact of Fact-Checking on Credibility Among Older Adults
Analyzing the impact of fact-checking on news credibility among older adults reveals that age is a key factor in information credibility. Older adults tend to give more credibility to various kinds of information, leading to potential challenges in discerning between true facts and false news. Fact-
5 views • 31 slides
BTR: Binary Token Representations for Efficient Retrieval Augmented Language Models
Retrieval-augmented language models like BTR address issues such as hallucination by providing efficient solutions for encoding input passages and queries. By utilizing cacheable binary token representations, BTR offers a unique approach to decomposing and binarizing passage encoding to improve runt
0 views • 9 slides
Exploring 'Checking Out Me History' - A Poem Analysis Quiz
Unravel the layers of "Checking Out Me History" through a 10-question quiz delving into themes of identity, historical figures, and the narrator's sentiments towards education and heritage. Discover the hidden messages and insights within this powerful poem.
0 views • 12 slides
Understanding Mood and Modality in Morphosyntax with Prof. John Corbett
Today's session with Prof. John Corbett explores the final three sets of grammatical categories related to verbs: mood (fact or non-fact), modality (speaker's stance), and voice (subject's role). The session delves into the present-day English mood system, differentiating between various realization
1 views • 24 slides
Understanding the Distinction Between Findings of Fact and Conclusions of Law
The distinction between findings of fact and conclusions of law is explored through various legal opinions and cases. The complexity and importance of this distinction are highlighted, with instances where findings are deemed as conclusions and vice versa. Scholars and legal experts have pondered ov
0 views • 24 slides
Understanding Fact Finding Techniques in System Analysis and Design
Fact finding techniques play a crucial role in collecting essential data and information for system analysis and design. Techniques include sampling existing documentation, research, observation, questionnaires, interviews, prototyping, and joint requirements planning. Extracting facts accurately is
1 views • 8 slides
Exploring Addition and Subtraction Fact Families Warm-Up
Engage in a series of activities to discover and practice addition and subtraction fact families. These exercises will help strengthen numerical skills and foster a deeper understanding of mathematical operations. Dive into the world of numbers and boost your math proficiency through interactive lea
1 views • 7 slides
Enhancing Data Analysis for Clemson University's Fact Book
Exploring the implementation of Tableau Server for presenting Clemson University's Interactive Fact Book, including considerations for data accuracy, design consistency, and improved navigation. The report covers insights on data preparation, retention, graduation, and the importance of communicatio
0 views • 13 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Quality Improvement Cycle: Plan, Do, Check, Act (PDCA)
The Quality Improvement Cycle follows the PDCA framework, involving planning, implementing, checking, and acting to continuously enhance processes. It begins with defining customer requirements, implementing processes effectively, checking for issues, and taking action to resolve any problems. The c
1 views • 6 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
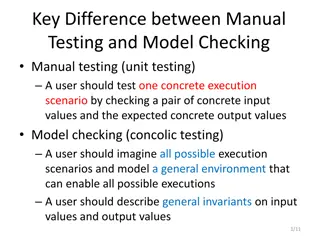
Difference Between Manual Testing and Model Checking
Manual testing focuses on testing specific scenarios with concrete inputs and outputs, while model checking involves imagining all possible scenarios to create a general environment for testing. In manual testing, users test specific execution scenarios, whereas in model checking, users envision and
2 views • 4 slides
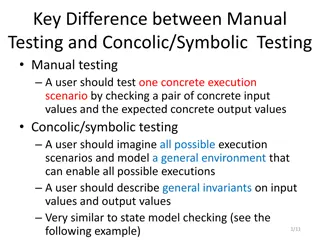
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
Best Practices for Absentee Voting Programs
Explore key terminology, absentee logistics, inherent tradeoffs, and best-practice recommendations for absentee ballot programs. Learn about different types of absentee voting, ballot request and submission processes, voter validation requirements, and the challenges and benefits associated with abs
0 views • 5 slides
Unveiling the Power of Data in Journalism
Exploring the crucial role of data in journalism, this content guides on utilizing data for story ideas, focus, context, and fact-checking. Learn the significance of approaching data with an open mind, conducting initial exploration, and finding compelling story ideas. Discover how to analyze and in
0 views • 9 slides
Data Journalism Projects and Best Practices: A Comprehensive Guide
Dive into the world of data journalism with insights on idea generation, fact-checking, campaign finance data in Argentina, researching effectively, and verifying information. Discover how to approach data journalism projects with a critical eye and attention to detail.
0 views • 31 slides
Unveiling the Truth: A Deep Dive into Fake News Phenomenon
Delve into the intricate web of fake news with a comprehensive course funded by the Erasmus+ Programme. Explore the history, definitions, and dangers of fake news alongside the new teaching fields for the next generation of journalists. Meet the author Marian Popovici, a PhD student in Communication
0 views • 39 slides
Context-Aware Identification of Check-worthy Claims in Political Discussions
This work explores the intersection of man and machine in countering malicious communication in social networks, focusing on fact-checking in political discussions. The research investigates the need for technology to verify the accuracy of public figures' statements, considering the thriving field
0 views • 21 slides
Understanding Time: 60 Minutes in One Hour
Explore the concept that there are 60 minutes in one hour through engaging activities like fact-checking, counting by 5s, and calculating minutes traveled by the minute hand. Learn key vocabulary related to time, clocks, and minute hands while reinforcing the fundamental idea that there are 60 minut
0 views • 11 slides
Understanding COVID-19 Vaccination: Myths, Facts, and Global Impact
Learn about the Phase One Inoculation Webinar, dispel vaccine myths and misinformation, understand the relationship between 5G and viruses, compare COVID-19 cases and deaths globally, and discover the importance of vaccination in saving lives. The content emphasizes the distinction between myths and
0 views • 8 slides
Exploring Architecture and Challenges of Proof Assistants
Explore the architecture of proof assistants, discussing the use of tactics, formal proofs, and the difficulty in utilizing these tools. Discover the contribution of a new architecture for proof assistants, addressing extensibility and error checking, with a focus on soundness guarantees. Delve into
0 views • 41 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
Essential Guide to Opening and Managing a Checking Account
Learn the importance of opening a checking account, the process of choosing a bank, criteria to consider, and the steps to open an account. Understand the different services offered by banks and the key factors to keep in mind when selecting a financial institution. Discover the benefits and require
0 views • 39 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Divide & Conquer Approach to Model Checking
Addressing the state space explosion issue in model checking, this work by Canh Minh Do, Yati Phyo, and Kazuhiro Ogata introduces a divide & conquer approach focusing on until and until stable properties. The research extends techniques to handle these properties effectively, emphasizing mitigation
2 views • 17 slides
Understanding the Decision-Making Process of Checking Behaviors Among Doctors and Patients
Recent research by Ido Erev from Technion and University of Warwick, along with Alvin E. Roth and others, explores the coexistence of insufficient and over-checking behaviors among individuals, including doctors and patients. The study delves into the factors influencing checking decisions, highligh
0 views • 24 slides
Inferential Statistics Solutions for Challenging Problems in Section B
The provided statistical problems in Section B involve calculating the expected number of shoppers spending specific durations at a furniture shop and reasons for not checking the weight of each packet when filling corn flakes. Solutions include determining the shoppers expected to spend more than 4
0 views • 25 slides
Math Fact Practice for Multiplication and Division
Enhance your multiplication and division skills with this interactive fact practice session. Test your knowledge with various problems and receive instant feedback on your progress. Improve your math abilities in an engaging way!
0 views • 73 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
0 views • 27 slides
Conflict Checking Process in Heraldry: Armory 104 Overview
Delve into the intricacies of conflict checking using the ordinary in heraldry with Armory 104. Explore prerequisites, review key concepts, understand where SCA-registered armory is located, and learn the process of identifying and analyzing charge groups to ensure uniqueness in designs. Avoid commo
0 views • 28 slides
Utilizing the Family and Children's Trust Fund (FACT) Research Portal for Program Needs Identification and Targeting
Explore how the Family and Children's Trust Fund (FACT) in Virginia supports the prevention and treatment of family violence through data management and strategic goals. Learn about managing by data, FACT's initiatives, and the significance of prevention in addressing family violence issues.
0 views • 25 slides
Subtyping and Type Checking in Programming Language Design
In the realm of programming language design, subtyping and type checking play crucial roles. This content delves into how syntax-directed rule systems evolve when dealing with subtyping, presenting the challenges and the solutions through a recursive algorithm approach. The discussion includes the t
0 views • 40 slides
Orthogonal Vectors Conjecture and Sparse Graph Properties Workshop
Exploring the computational complexity of low-polynomial-time problems, this workshop delves into the Orthogonal Vectors Problem and its conjectures. It introduces concepts like the Sparse OV Problem, first-order graph properties, and model checking in graphs. Discussing the hardness of problems rel
2 views • 22 slides
Streamlining Technical Processing for Library Services
In the technical processing workflow of a library, utilizing tools like copy cataloging macros can significantly improve efficiency and accuracy. This involves checking for copy cataloging status, running fix routines, and updating catalog records. While these macros offer benefits such as saving ti
0 views • 17 slides
Communication Complexity in Byzantine Agreement Research
The presentation discusses communication complexity in Byzantine Agreement, emphasizing a lower bound of (f/2) when After the Fact removal is considered. It explores two major contributions - the communication lower bound in randomized protocols and near-optimal subquadratic Byzantine Agreement. The
0 views • 9 slides
Comprehensive Overview of ECV Data Sourcing and Fact Sheet Creation Process
Detailed insights into the ECV data sourcing procedures, criteria for selection, and the development of fact sheets, as outlined by the GCOS Secretariat and WMO representative Valentin Aich. The content covers requirements tables, product definitions, data sources compilation steps, and the importan
0 views • 15 slides