In-Depth Look at Breaking HTTP Servers, Proxies, and Load Balancers
Explore the world of disrupting HTTP technology with authors Ben Kallus and Prashant Anantharaman. Delve into vulnerabilities, DARPA-funded projects, and the interesting exploits in HTTP implementations. Witness the journey that involves discovering multiple vulnerabilities, receiving grants for res
2 views • 51 slides
Role of AI in Threat Detection and Zero-day Attacks
Cybercrime has been on the rise, especially with the surge in zero-day attacks targeting various industries. State-sponsored actors, like Chinese groups, dominate zero-day exploits, challenging traditional detection methods. Incorporating AI, machine learning, and deep learning is vital in enhancing
0 views • 9 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Memory-unsafe languages like C and C++ are prone to Use-After-Free (UAF) vulnerabilities. PUMM introduces execution unit partitioning to efficiently tackle this issue. By segregating and managing execution units, PUMM aims to prevent UAF exploits and enhance software security.
0 views • 31 slides
Understanding Phase Contrast Microscopy: A Revolutionary Tool in Cell Observation
Phase contrast microscopy, invented by Frits Zernike, revolutionized cell observation by utilizing tiny phase changes in light rays to create contrast in living cells. This technique exploits differences in refractive indices to enhance visibility without staining cells, offering a new perspective i
0 views • 27 slides
15-213 Recitation: Bomb Lab Overview and Tips
This content covers the Bomb Lab exercise in x86-64 assembly code and GDB debugging techniques. It explains the purpose of Bomb Lab, downloading the bomb, detonating the bomb, hints for solving phases, and x86-64 Linux register usage. The material emphasizes the importance of using GDB for efficient
0 views • 42 slides
Mythical Tales of Cú Chulainn and His Extraordinary Exploits
Delve into the captivating mythology surrounding Cú Chulainn, the legendary hero of Ulster. From his miraculous birth and childhood feats to his extraordinary adventures, battles, and mystical encounters, the story of Cú Chulainn is a tapestry of magic and valor intertwined with prophecies, curses
0 views • 10 slides
Exploring Web Application Vulnerabilities and JavaScript Worms
Web applications face pervasive vulnerabilities, with Cross-site Scripting (XSS) leading the threats. The domination of XSS and buffer overruns has enabled the propagation of JavaScript worms, exemplified by infamous cases like Samy's MySpace outbreak. These exploits, marked by obfuscation and polym
1 views • 20 slides
Understanding Web Security Fundamentals in Networking
This lecture delves into the intricate layers of web security, focusing on vulnerabilities by year, CSRF attacks, and defensive strategies. Topics covered include the application layer, networking stack, HTTP protocols, and common security threats like XSS and SQL injection. Various defense mechanis
0 views • 27 slides
Notorious Criminals: Al Capone and Pablo Escobar
Al Capone and Pablo Escobar were infamous criminals who ran violent empires in Chicago and Colombia, involved in bootlegging, drug trafficking, and other illegal activities. Capone's reign led to the St. Valentine's Day Massacre, while Escobar's ruthless methods made him the "King of Coke." Their cr
0 views • 16 slides
Understanding Exploit Development Fundamentals
Explore key concepts in exploit development, including vulnerabilities, exploits, 0days, memory management, instructions vs. data, and program address space. Learn about stack manipulation and how to take advantage of system flaws effectively.
0 views • 46 slides
Understanding Computer System Exploits and Prevention
Exploring program exploitation, stack buffer overflows, vulnerability analysis, and exploit prevention strategies in computer systems. Learn about setting the stage for exploits, exploiting stack buffer overflows, and the challenges faced in executing shellcode attacks. Dive into the world of cyber
0 views • 36 slides
Understanding Buffer Overflows and Exploits in C Programs
Explore the concepts of buffer overflows and exploits in C programming, covering memory layout, program details, and examples of stack smashing and implicit casting bugs. Learn how attackers manipulate code sequences and take control through vulnerabilities like the misuse of functions like memcpy.
0 views • 39 slides
Understanding Software Weaknesses and Exploits
Discover the vulnerabilities present in software such as buffer overflows and format string vulnerabilities, and how these weaknesses can be exploited to cause security issues. Learn about the technical aspects of weaknesses, stack frames, memory organization, and the potential consequences of stack
0 views • 57 slides
African American Veterans in World War I: The Harlem Hellfighters and Corporal Freddie Stowers
African American veterans played a significant role in World War I, exemplified by the exploits of the renowned Harlem Hellfighters and Corporal Freddie Stowers. The Hellfighters, part of the 369th Infantry, fought bravely in France, earning respect and accolades despite facing racism upon returning
0 views • 5 slides
Understanding Buffer Overflow in Computer Programming
This content delves into the intricacies of buffer overflow vulnerabilities in computer programming, showcasing real-world examples such as the Internet Worm and IM War incidents. It covers topics like stack buffer overflow exploits, Unix function implementations prone to buffer overflow, and the re
0 views • 35 slides
Safeguarding Against Predatory Publishing Practices
Predatory publishing exploits authors through counterfeit journals, lacking transparency and integrity. Researchers must prioritize reputation, visibility, quality recognition, and peer review in academic publishing. Stay vigilant using tools like Incites and Beall's list, and adhere to ethical guid
0 views • 14 slides
Addressing Software Security, Economic, and Liability Issues
In the realm of software security, economic considerations often lead to negligence in addressing vulnerabilities, resulting in billions of dollars wasted annually due to exploits by hackers. The focus is on the prevalence of vulnerabilities, limited sources of security issues, and the need for a sh
0 views • 37 slides
Understanding Memory Snapshotting by Vinod Ganapathy
Explore the concept of memory snapshotting through images and insights shared by Vinod Ganapathy at the EECS Symposium. Delve into topics like malware detection, the layer-below principle, and the risks of OS infections due to exploits and social engineering attacks.
0 views • 42 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Web Security Threats and Vulnerabilities: An Overview
Understanding the risks associated with web security, including issues like IP hijacking, cache poisoning, and transparent proxies. Explore how existing approaches fall short in protecting against malicious attacks and potential exploits, with observed vulnerabilities highlighting the importance of
0 views • 17 slides
Understanding DLL Hijacking in Windows
Dynamic-Link Libraries (DLLs) are a mechanism in Windows for sharing code and data, making it easier to design and build applications. By loading DLLs either statically at compile time or dynamically at runtime, programs can enhance memory management and user experience. However, DLL hijacking, a co
0 views • 13 slides
Social engineering: A threat to even well-engineered networks
Despite robust technical defenses, organizations remain vulnerable to cyber espionage and social engineering attacks. This is exemplified through scenarios where sensitive information is targeted through deceptive tactics rather than technical breaches. Social engineering exploits human vulnerabilit
0 views • 15 slides
Exploring the Shipwreck of S.S. American Star
Uncover the captivating history of the S.S. American Star, a cruise liner turned hotel project that met a watery fate in 2008. Dive into discussions on adventure, writing tasks, and the pros and cons of daring exploits, all while marveling at images of the ship's remains on Fuerteventura's shores.
0 views • 12 slides
Hunting Cross-Site Scripting Attacks in the Network
Detect suspicious URLs and prevent XSS attacks with xHunter, a tool by Elias Athanasopoulos and team at FORTH-ICS, Greece. Explore the motivation, current status, targets, and orchestration of XSS incidents. Learn about the anatomy of XSS exploits and the operation of xHunter in identifying JavaScri
0 views • 48 slides
The Military Conquest of Wales and Scotland by Edward I
Edward I's military exploits in the Welsh and Scottish wars overshadow his other achievements, forming a significant part of his legacy. This includes key events such as the Welsh Building Project, Treaties of Salisbury and Birgham, and the strategic castles built during his reign, like Caernarfon C
0 views • 12 slides
Understanding Control Hijacking Attacks in Computer Systems
Explore the concept of control hijacking attacks in computer systems, including buffer overflows, format string vulnerabilities, and use-after-free exploits. Learn about the attacker's goal, examples of attacks, and the importance of understanding C functions, the stack, and the heap. Delve into sys
0 views • 39 slides
Strategies Against Malware Attacks
Learn effective defenses against malware including preventing exploits, utilizing non-executable memory, combating return-oriented programming, implementing ASLR, and more to enhance your system's security against cyber threats.
0 views • 42 slides
Understanding Heap Exploitation Techniques in CSE 545 Fall 2020
This collection of images covers various heap exploitation techniques discussed in CSE 545 Fall 2020, such as fastbin use-after-free vulnerabilities, tcache poisoning, double-free exploits, metadata manipulation, and more. The images depict scenarios involving tcache, fast bins, unsorted bins, and f
0 views • 72 slides
N-Variant Execution for Improved Security Measures
N-Variant Execution (NVX) is a technique used to enhance security measures by running diversified program variants in parallel and comparing their outputs for transparency. NVX systems can protect against attacks relying on knowledge of virtual address spaces but have limitations against attacks bas
0 views • 48 slides
Understanding Weak Points in Web Application Architecture
Information collected during the reconnaissance process can unveil critical aspects of a web application's architecture, including technologies used, API endpoints, functionality, domains, configurations, and authentication systems. Vulnerabilities in web applications often stem from poorly designed
4 views • 13 slides
Enhancing Cybersecurity in Modern Linux Systems
Explore the evolving landscape of cybersecurity in Linux systems as discussed in Professor Ken Birman's CS4414 lecture series at Cornell University. The focus is on protection features, defense strategies, code reviews, and continuous efforts to secure Linux platforms against exploits and vulnerabil
0 views • 55 slides
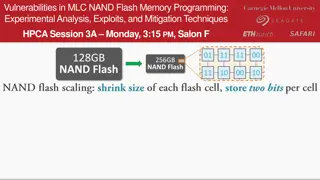
Experimental Analysis of Vulnerabilities in MLC NAND Flash Memory Programming
This session at HPCA explores the experimental analysis, exploits, and mitigation techniques related to vulnerabilities in MLC NAND flash memory programming. The presentation delves into the risks associated with NAND flash memory, such as data corruption and errors during read operations. It discus
0 views • 10 slides
Understanding Cross-Site Scripting (XSS) Attacks and Prevention Measures
Cross-Site Scripting (XSS) is a prevalent security vulnerability in web applications that allows attackers to inject malicious scripts, potentially leading to unauthorized data access or manipulation. The content covers types of XSS attacks, finding vulnerable websites, testing exploits, and legal i
0 views • 10 slides