Good Laboratory Practices Study Protocols for Effective Research Management
Supplemental materials providing detailed protocols for implementing Good Laboratory Practices (GLP) in research settings. The protocols cover GLP requirements, experimental design, reading regulatory sections, approval processes, amendments, circulation lists, and study plans. These materials aim t
0 views • 22 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
A Comparison of Hinduism and Buddhism in Ancient Indian Religions
Hinduism and Buddhism, two major religions originating in ancient India, share beliefs in concepts like moksha and reincarnation but differ in practices, gods, texts, and societal impacts. Hinduism's caste system influences all aspects of life, while Buddhism was founded by Siddhartha Gautama, the B
2 views • 11 slides
Effortless Printer Solutions: Your 24/7 Go-To for Printer Problems
The setup and configuration of HP printers is easy. \nA range of economically priced, high-quality printer types are available from HP. Advanced scanning and printing features are available for all HP models, including DeskJet, OfficeJet, LaserJet, and Envy. When you buy a new one, you have to know
1 views • 3 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Oklahoma School Safety Protocols Overview
Overview of the school safety protocols in Oklahoma, which define requirements based on COVID-19 alert levels per capita in each county. The protocols include instructions for different alert levels, mask recommendations, visitor limitations, and activity guidelines. Schools are expected to offer in
0 views • 9 slides
Overview of Alexander Pope's "An Essay on Criticism
Alexander Pope's "An Essay on Criticism" is divided into three parts discussing the principles of good criticism, offering solutions to critical problems, and identifying obstacles to good criticism. Part One delves into the challenges critics face due to partial judgments, false learning, and envy.
0 views • 17 slides
Retrieval Practice for Where the Mountain Meets the Moon
In this retrieval practice exercise based on the book "Where the Mountain Meets the Moon," students are quizzed on key aspects such as the symbolism of goldfish, the concept of dynasty, folktale definitions, characters connected to dynasties, and traits like impulsiveness in the story. The practice
0 views • 18 slides
Lessons from the Story of Joseph in Egypt
Explore the biblical story of Joseph in Egypt, focusing on themes of envy, gratitude, and interpreting dreams. Discover how envy can lead to destructive actions, and learn how gratitude can combat envy. Follow Joseph's journey from being sold by his brothers to interpreting Pharaoh's dreams and prep
0 views • 10 slides
Overcoming Barriers to Thankfulness: Lessons from Scripture
Exploring passages from the Bible, this content highlights various barriers to thankfulness such as anger, envy, anxiety, and discontentment. It emphasizes the importance of gaining a proper perspective, shifting focus towards gratitude, and finding value in different situations to cultivate a thank
0 views • 11 slides
Work Protocols and Safety Measures for Employees Returning to Work
In the wake of the COVID-19 pandemic, these work protocols emphasize roles, responsibilities, and mental wellbeing of employees. Pre-work precautions at home, personal measures, testing procedures, increasing awareness, and safe travel guidelines are highlighted to ensure a secure work environment.
0 views • 16 slides
Understanding Emergency Conditions in ERCOT Protocols
ERCOT has defined various levels and communication protocols for Emergency Conditions within the electrical grid system. This includes Emergency Notices, Energy Emergency Alerts, operating plans, outage coordination, and requirements related to voltage support for ensuring system safety and reliabil
6 views • 18 slides
Understanding Lock-Based Protocols in Database Concurrency Control
Lock-based protocols are essential mechanisms for controlling concurrent access to data items in a database system. This involves granting locks in exclusive (X) or shared (S) modes to ensure data integrity and prevent conflicts. Lock compatibility matrices and locking protocols play a crucial role
2 views • 69 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Analysis of "Annabel Lee" by Edgar Allan Poe
Explore the tragic love story of "Annabel Lee" by Edgar Allan Poe, delving into the poet's personal life, background, and the poem's themes. Discover the deep love between the speaker and Annabel Lee, the envy of angels, and the haunting influences Poe faced in his own life that shaped this poignant
0 views • 17 slides
Exploring the Essence of Love Through Virtues
Delve into the profound qualities of love as described in text. Love embodies patience, kindness, humility, and selflessness, while shunning envy, arrogance, rudeness, selfishness, provocation, and a record of wrongs. Instead, it rejoices in truth and morality, setting a high standard for interperso
0 views • 15 slides
Insights on Envious, Emerge, Reliable Week 10
Explore the concepts of envy through the narrations of Tuck Everlasting, alongside reflections on emergence and reliability from various perspectives. Delve into scenarios with Tulip and Glenn, pondering on feelings of envy, appearances, and the unfolding of events. Witness the interplay of emotions
0 views • 15 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Enhanced Cleaning Protocols for Classrooms and Common Areas
Spread through respiratory droplets, COVID-19 requires rigorous cleaning protocols in class and common areas. Key measures include mandatory mask-wearing, hand sanitizing, physical distancing, and regular surface cleaning using alcohol wipes and disinfectants. Classroom staff play a crucial role in
0 views • 5 slides
Trusting God's Timing in Turbulent Times
Encouragement from Psalm 31 and Genesis 26:1-14 on trusting God's sovereignty in difficult times and being fruitful even in famine by listening to His guidance and obeying His commands. The story of Isaac showcases how God's blessings follow obedience and faithfulness, leading to prosperity and envy
1 views • 26 slides
Understanding the Seven Deadly Sins and the Importance of SAMM
Delve into the concept of the Seven Deadly Sins - Lust, Gluttony, Greed, Sloth, Wrath, Envy, and Pride - and explore their impact on human behavior. Discover the significance of SAMM in ensuring the success of Application Security Projects. Uncover how these sins and SAMM relate to each other in var
0 views • 13 slides
Best Make Up Services in Blackbutt
If you want the Best Make Up Services in Blackbutt, visit Envy Beauty By Bree. They are your destination for award-winning advanced beauty treatments in Oak Flats. Their comprehensive services include Body Contouring, IPL, Ultrasound Product Infusion
1 views • 6 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Exploring True Wisdom: Insights from James and Psalms
Through verses from James and Psalms, we delve into the essence of wisdom, emphasizing its divine origin, characteristics, and the contrast between earthly and heavenly wisdom. The reflection on the fear of the LORD, the importance of humility, and the impact of envy and selfish ambition offers a pr
0 views • 14 slides
Understanding Fair Allocation in Theoretical Computer Science
Explore the concepts of fair allocation through algorithms and protocols in the realm of theoretical computer science. Delve into topics such as resource allocation, cake cutting problems, envy-free protocols, and more, with a focus on maximizing social welfare, fairness, and stability. Gain insight
0 views • 37 slides
Fair Cake-Cutting Methods for Envy-Free Allocations
Various fair cake-cutting methods for allocating divisible goods among multiple agents are explored in this content. These methods ensure that each agent receives a share proportionate to their preferences, without feeling envious of others' allocations. Techniques such as connected pieces, bounded-
0 views • 28 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Data Link Control and Protocols in Computer Networks
This chapter discusses various protocols for handling data link control in computer networks, focusing on noiseless and noisy channels. It covers protocols like Stop-and-Wait ARQ, Go-Back-N ARQ, and Selective Repeat ARQ, explaining how they ensure error-free transmission and flow control. The concep
0 views • 12 slides
Understanding Lock-Free and Wait-Free Algorithms in Concurrent Data Structures
Illustration of lock-free and wait-free algorithms compared to blocking algorithms, with insights on concurrent object execution, blocking vs. non-blocking algorithms, definitions, comparisons between locks, lock-free, and wait-free approaches, and explanations on making algorithms wait-free. Exampl
0 views • 23 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
The Destructive Power of Envy: Reflections from Proverbs & Psalms
Explore the corrosive nature of envy through verses from Proverbs and Psalm 73, diving into the inner turmoil it brings and the wisdom in overcoming this deadly sin. Delve into the importance of addressing envy to maintain peace and spiritual strength.
0 views • 25 slides
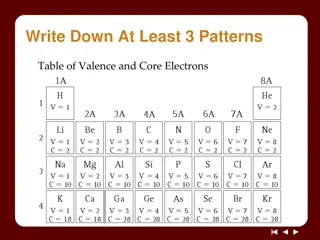
Understanding Ionic Bonds: Valence Electrons and Ion Formation
Exploring the concepts of valence and core electrons, Noble Gas Envy Ions, and the formation of ions through electron transfer between metal and nonmetal atoms. Learn about cations and anions, ion charges based on the periodic table, and the relationship between ion charge and valence electrons.
0 views • 13 slides
Wisdom from Proverbs and Psalms: Do Not Envy the World, Be Zealous for the Fear of the Lord
Encouragement from Proverbs and Psalms to avoid envy, seek wisdom, and be zealous in the fear of the Lord, with references to the hereafter and the assurance of hope.
0 views • 5 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides