Azure IoT Edge
Seamlessly move cloud and custom workloads to the edge securely. Deploy AI and advanced analytics with ease. Monitor and update from the cloud. Azure IoT Edge provides a secure and scalable solution from chipset to the cloud.
0 views • 16 slides
School Crossing Guard Training Course
The School Crossing Guard Training Course! This course aims to provide standardized training to new and seasoned crossing guards, helping them understand their roles, learn relevant laws, practice proper crossing techniques, and foster safe environments.
2 views • 58 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Parsimoni – the European IoT/Edge OS. Secure, efficient, flexible.
Revolutionizing IoT/Edge computing with secure, efficient, and flexible technology, Parsimoni aims to set new standards in the industry. Led by CEO Miklos Tomka, the company leverages European open-source technology to create a secure-by-design OS for IoT/Edge applications. Seeking partners for cons
1 views • 5 slides
Leveraging EXO Edge, The Benefits of Outsourcing Property Accounting
In the realm of property accounting, offshore operations have become a strategic avenue for businesses to optimize resources and enhance efficiency. With the advent of advanced technological solutions like EXO Edge, managing property accounting offshore has evolved into a streamlined process, offeri
11 views • 8 slides
Mastering Property Management Accounting with EXO Edge
In the dynamic world of property management, maintaining a seamless financial operation is paramount. From rental income to maintenance expenses, every penny needs careful tracking and management. Enter EXO Edge, the revolutionary solution empowering property managers with cutting-edge accounting ca
11 views • 8 slides
Unlocking Excellence in Property Accounting Services with Exo Edge
In conclusion, Exo Edge offers unparalleled property accounting services tailored to meet diverse needs. With a commitment to client success, cutting-edge technology, and expert resources, they provide the financial clarity and confidence essential for property managers and investors to thrive. Part
1 views • 17 slides
Protect Your Roof with Solar Panel Critter Guards and Squirrel Guards
Installing solar panel critter guards and squirrel guards for your roof ensures protection from pests. These guards prevent critters from damaging your solar panels and wiring, maintaining their efficiency and longevity. Invest in a reliable guard to
0 views • 3 slides
Machine Shop Safety and Best Practices for Precision Machining
Safety is paramount in the machine shop. Ensure proper safety measures like wearing safety glasses, appropriate clothing, and using guards on machines. Precision measuring tools must be calibrated and used correctly for accurate results. Machine setups require rigidity and proper tools for efficient
0 views • 14 slides
Understanding Fordyce Granules and Linea Alba in Oral Health
Fordyce granules and linea alba are common variations found on the surface of the lips and cheeks. Fordyce spots are enlarged oil glands that appear as white or yellow bumps, while linea alba is a white ridge of calloused tissue. These conditions are harmless but may cause concerns. Cheek biting and
0 views • 6 slides
Transforming Buildings with EDGE Certification
Discover how EDGE certification revolutionizes the way buildings are designed and constructed for a smarter, greener world. EDGE provides a comprehensive solution that makes building green faster, easier, and more affordable. Learn about the EDGE standard's focus on resource efficiency, materials, e
1 views • 17 slides
Analysis of "Borders" by Thomas King
In "Borders" by Thomas King, the story revolves around Laetitia, her mother, and their interaction with border guards. The characters exhibit different traits, with Laetitia displaying courage and curiosity, while the border guards represent discrimination. The conflict arises from the unfair treatm
0 views • 15 slides
Explore the World of Knights: Armor and Protection
Delve into the realm of knights and their armor with a closer look at the essential components such as helmets, throat guards, shoulder guards, breastplates, and chainmail. Discover the significance of each piece in providing protection during battles and tournaments. Engage in fun activities like i
0 views • 16 slides
Understanding the Compilation Toolchain in Software Development
Delve into the world of the Compilation Toolchain, from pre-processing to dynamic linking and loading. Explore the functionalities of the preprocessor, compiler, and include guards in C programming. Discover the significance of header files, #define directives, and preprocessor macros in converting
0 views • 40 slides
General Lab Safety Rules and Guidelines
Ensure 100% accuracy in identifying and adhering to general lab safety rules. Key points include reporting all injuries, wearing eye protection, maintaining safety zones around machines, disposing of combustible materials properly, obtaining permission before using equipment, and recognizing broken
0 views • 12 slides
Importance of Dental Mouth Guards in Wrestling
Dental mouth guards play a crucial role in protecting athletes, especially wrestlers, from preventable injuries such as dislodged teeth, concussions, broken teeth, and more. This article discusses the necessity of wearing mouth guards during sports activities to safeguard the teeth, mouth, and head
3 views • 7 slides
Analysis of IoT Band Edge Performance Against FCC Regulations in 3GPP TSG-RAN-WG4 Meeting
This document discusses the band edge requirements for NB-IoT devices, specifically focusing on FCC specifications. It addresses the complexities of band edge regulations, proposes further analysis and simulations, and suggests options for network signaling release. The references provide insight in
0 views • 4 slides
Guide to Setting Up a Computer Forensics Lab
Explore the essential aspects of creating a computer forensics lab, including where to establish it, tools needed, forensic software, storing evidence, access controls, chain of custody, and recording details about forensic images. Learn about the differences between criminal and civil investigation
0 views • 36 slides
One of the Best service for Gutter Cleaning in Yangebup
FloPro Gutter Guards serves the Best service for Gutter Cleaning in Yangebup. To discuss how they can help protect your home from the elements. Ensure your home is protected with their superior gutter solutions. Their dedicated team is committed to d
1 views • 6 slides
The Importance of Professionalism in Security Services
Highlighting the significance of appearance, attitude, integrity, and reliability in maintaining professionalism for security guards. Emphasizes the impact of a professional demeanor on how guards are perceived and respected by others.
2 views • 23 slides
Tone and Mood in Various Literary Texts
This content discusses the role of inmates taking on the position of prisoner guards, Elie's experiences in a camp, changes within Elie, incidents with children among guards, and behavioral changes mirrored by Franek due to brutality normalization. It also analyzes the tone and mood in different lit
0 views • 13 slides
Enhancing Service Function Chaining in Edge Data Networks
Introduction of new interfaces and capabilities in 3GPP standards such as Rel-13 and TR 23.718 for improved service function chaining support in Edge Data Networks. Requirements for service functions and controllers in edge environments, considerations for cloud-based and edge-located SFs/SFCs, and
0 views • 18 slides
Food Safety Practices in Service Industry
This chapter focuses on the essential food safety practices in the service industry, covering topics such as time and temperature requirements for holding food, ways to prevent time-temperature abuse and cross-contamination, minimizing bare-hand contact with food, preventing staff and customers from
0 views • 26 slides
Insights into Elizabethan Beliefs in Shakespeare's "Hamlet
Act 1, Scene 1 of "Hamlet" introduces characters and Elizabethan beliefs like ghostly encounters, the power of Latin to exorcise spirits, and the constraints of ghosts. Horatio's skepticism evolves, validating ghostly apparitions for the audience. The scene contrasts superstitions, hierarchy, and ed
0 views • 8 slides
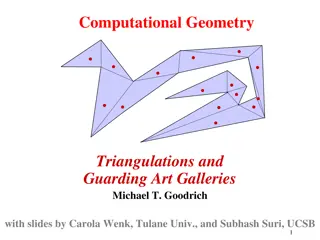
Understanding Computational Geometry: Triangulations and Art Gallery Guarding
Explore the concepts of triangulations and guarding art galleries in computational geometry. Learn about the problem of placing cameras or guards strategically in an art gallery to ensure every point is visible. Discover how polygons are defined, the variations in guarding strategies, and the use of
0 views • 31 slides
Understanding the Stanford Prison Experiment
Explore the infamous Stanford Prison Experiment conducted by Phil Zimbardo, where college students were assigned roles of prisoners and guards in a simulated prison environment. Witness the rapid deterioration of behaviors and mental states, leading to the premature halt of the study. Delve into the
0 views • 16 slides
Insights on Hidden Edge Guards and Guard Varieties
Explore various studies and findings on hidden edge guards with a focus on Victor Klee's Art Gallery Problem, the restriction of guards not seeing each other by Thomas Shermer, and different guard varieties. Discover the challenges and solutions associated with guarding polygons in different configu
0 views • 16 slides
Intelligent Task Allocation in Edge Computing for IoT Devices
This study explores the utilization of in-network decision-making intelligence for task allocation in edge computing, focusing on challenges like latency and data migration. Techniques such as tasks allocation at the edge and autonomous tasks processing are discussed. The aim is to enable efficient
0 views • 25 slides
Duties and Responsibilities of Guards in Military Operations
Explore the various types of guards including Police Guard, Grand Guard, and Provost Guard along with their specific duties and responsibilities in maintaining order, security, and protection within military camps and operations. Understand the roles of sentinels, pickets, and the importance of coun
0 views • 24 slides
Secure Your Angular App Using JWT and GraphQL
Ankit Sharma presents an insightful talk on securing Angular applications using JWT and GraphQL. He discusses the technology stack involving .NET, Angular, and GraphQL to create a secure API system with route guards. The talk explains the significance of JWT and when to use it, detailing its structu
0 views • 21 slides
3rd-4th Grade 9-Man Offensive Playbook with I-Backfield Formation Plays
Explore the offensive playbook designed for 3rd-4th grade 9-man football teams featuring various I-backfield formation plays like the 52 Dive, 152 Dive, 62 Dive, 162 Dive, 63 Dive, 163 Dive, 74 Reverse, 174 Reverse, 53 Power, 153 Power, 63 Power, and 163 Power. Each play is detailed with the positio
0 views • 47 slides
Partners and Resources for Disaster Risk Management (DRM)
In Module 6, trainees learn about local partners like police, home guards, and health centers who provide immediate assistance post-disaster. The module emphasizes the importance of incorporating various partners at local, national, regional, and international levels in a DRM plan to enhance respons
0 views • 13 slides
Understanding Edge Computing for Optimizing Internet Devices
Edge computing brings computing closer to the data source, minimizing communication distances between client and server for reduced latency and bandwidth usage. Distributed in device nodes, edge computing optimizes processing in smart devices instead of centralized cloud environments, enhancing data
0 views • 32 slides
Understanding Edge Detection in Image Processing
Edge detection is a fundamental operation in image processing, crucial for identifying object boundaries based on rapid changes in brightness. This process involves detecting areas of discontinuity in gray-level values to locate edges, which hold significant information about objects in an image. Co
0 views • 12 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
The Legal Battle Between eBay and Bidder's Edge
The legal dispute between eBay and Bidder's Edge revolves around Bidder's Edge utilizing software robots to aggregate listings from multiple auction sites, including eBay. eBay revoked Bidder's Edge's access, citing unauthorized activity and offering to license their actions. The underlying business
0 views • 19 slides
Maximize Storage with Boltless Racking, Durable Shelving, & Rack Guards
LSRACK is a boltless racking system that provides a multipurpose, effective method of storage aimed at making your warehouse management easy. It is designed for this purpose to bear different load capacities without the need for bolts. Having pallet
3 views • 4 slides
PT100 Guard Patrol System Overview
The PT100 Guard Patrol System is a comprehensive management solution designed for security, attendance, and logistics companies. This system utilizes fingerprint authentication to track the time and attendance of guards, ensuring they follow designated routes at specified intervals. With features li
0 views • 13 slides
Aeroplane Stalling Factors: Trailing Edge Flaps and Leading Edge Devices
Explore the factors contributing to aeroplane stalling, including the impact of trailing edge flaps and leading edge devices. Discover how stalling speed is affected and gain insight into the mechanisms behind aeroplane stalls.
0 views • 40 slides
Autonomous Underwater Detection of Smuggling Containers for Maritime Security
Innovative project led by Thomas Vonach of Subdron focusing on enhancing underwater detection capabilities to protect maritime areas and sea harbors. Utilizing Autonomous Underwater Vehicles (AUVs), the project aims to autonomously detect illegal obstacles such as cylindrical containers attached und
0 views • 4 slides