Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
Laredo College Dual Enrollment Program Information
Laredo College Dual Enrollment Program offers High School Students the opportunity to take College Courses through various programs like Dual Credit, Early College, and Early Enrollment. Students must meet specific criteria for enrollment, including TSI standards, course placement requirements, and
1 views • 13 slides
Understanding Dual Enrollment Program for High School Students
Dual Enrollment is a challenging acceleration program that allows high school students to earn college credits simultaneously. Students can reduce time to complete a college degree, save money, increase chances of graduation, and even pursue industry certifications. Eligibility criteria include enro
1 views • 13 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
A Safety Expert’s Guide: How to Stack Pallets Safely
In the bustling world of warehouses, logistics, and manufacturing, the proper stacking of pallets is a critical aspect of maintaining a safe and organized workspace. As a safety expert, I\u2019ve seen firsthand the importance of implementing best practices to ensure the secure stacking of pallets. I
14 views • 2 slides
Dual Credit Options at Champion High School
Champion High School offers Advanced Placement (AP) and Dual Credit programs in partnership with various institutions like Northwest Vista College, Angelo State University, UT On-Ramps, and Tarleton Today. Students can earn college credit by meeting testing requirements, with some classes being free
1 views • 14 slides
430548-001 HPE NC373m PCI-E Dual Port Multifunction Gigabit Server Adapter
New | HPE 430548-001 | NC373m PCI-E Dual Port Multifunction Gigabit Server Adapter | \u2713 FREE and FAST Ground Shipping across the U.S. | Best Price Guaranteed\n\nProduct Link: \/\/ \/430548-001-hpe-nc373m-pci-e-dual-port-multifunction-gigabit-server-adapter\/
0 views • 1 slides
Piezoelectric Stack Actuator Market Analysis, Size, Share, Growth, Trends Foreca
The Global Piezoelectric Stack Actuator market stands at the forefront of technological driving advancements in various industries through its dynamic applications. These actuator systems harness the unique properties of piezoelectric materials, providing precision and versatility in a range of mech
0 views • 8 slides
Exploring Quantum Black Holes: Dual Dynamics and Brane Evaporation
Exploring the dual dynamics of quantum black holes reveals new perspectives on black hole evaporation. By placing black holes on branes, we can study their classical picture in higher dimensions. This approach provides insights that were previously unattainable, leading to a better understanding of
1 views • 28 slides
Efficient Stack Emission Monitoring Procedure for Air Quality Control
Stack emission monitoring is crucial for industries to assess and reduce pollutants in exhaust air. This procedure involves tasks like measurement, testing, and analysis of flue gases. Sampling sites are selected strategically for accurate readings, and molecular weight and gas velocity are determin
1 views • 11 slides
Understanding Artificial Neural Networks From Scratch
Learn how to build artificial neural networks from scratch, focusing on multi-level feedforward networks like multi-level perceptrons. Discover how neural networks function, including training large networks in parallel and distributed systems, and grasp concepts such as learning non-linear function
1 views • 33 slides
Understanding Dual Credit Programs for High School Students
Dual credit programs offer high school students the opportunity to earn college credits while still in high school. This program, offered to junior and senior students at MFHS, allows enrollment in college courses through CTC and/or Sul Ross. Successful completion earns credits towards both high sch
1 views • 11 slides
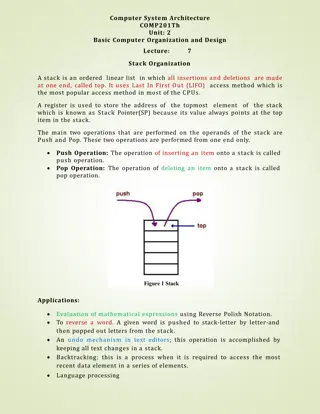
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
Understanding The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
Understanding Dual Enrollment and Concurrent Enrollment
At the state level, there is no formal distinction between Dual Enrollment and Concurrent Enrollment. Special admit students refer to high school students taking college courses. Courses under CCAP agreements aim to make dual enrollment accessible to all students. Regulations for CCAP students inclu
1 views • 16 slides
Understanding Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Dual Credit Reporting Guidelines for College Courses
Dual Credit Reporting provides definitions, guidelines, and validation rules for reporting college courses that allow students to earn both high school and college credit. Key elements covered include credit indicators, college credit hours, course sequencing, and validation rules to avoid overrepor
0 views • 6 slides
Exploring Dual Credits and Cooperative Education Programs
Dual credit programs offer high school students the opportunity to earn college credits while completing their secondary education, potentially leading to a post-secondary diploma or Certificate of Apprenticeship. These programs aim to support students facing challenges in meeting graduation require
0 views • 7 slides
Evolution and Implementation of Dual Fuel ECDIS in Maritime Navigation
Delve into the advancements in Dual Fuel ECDIS technology, exploring its principles, operational aspects, and stakeholder collaborations. Learn about the governance framework, content suggestions, and the integration of S-100 standards in ECDIS systems. Discover how Dual Fuel ECDIS bridges the gap b
3 views • 11 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Introduction to Neural Networks in IBM SPSS Modeler 14.2
This presentation provides an introduction to neural networks in IBM SPSS Modeler 14.2. It covers the concepts of directed data mining using neural networks, the structure of neural networks, terms associated with neural networks, and the process of inputs and outputs in neural network models. The d
0 views • 18 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Rare Case Report of Dual Thyroid Ectopia in a Young Female
An 18-year-old female presented with a large cystic swelling in the anterior aspect of her neck, leading to the diagnosis of dual thyroid ectopia. Imaging studies, including ultrasound and CT scan, revealed ectopic lingual thyroid and a complex thyroglossal cyst. The patient underwent thyroglossal c
1 views • 8 slides
Feasibility of Care Coordination for Dual Eligibles: Characteristics and Opportunities
The Pacific Health Policy Group's report discusses the feasibility of care coordination for dual eligibles, individuals eligible for both Medicaid and Medicare with high rates of complex health conditions. Characteristics include having low incomes, chronic physical and mental health conditions, and
4 views • 52 slides
Understanding Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
Understanding Dual Enrollment Program at SJR State
Dual Enrollment at SJR State is an acceleration program allowing eligible high school students to earn college credits while progressing towards high school completion. Students must maintain a 3.0 GPA, manage course loads carefully, and take ownership of their academic responsibilities. The program
0 views • 19 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Dual Career Counseling Best Practices in Sport Clubs
Explore good practices in dual careers in sport, focusing on counseling for life after sports in Sport Clubs. Learn about experiences from European countries, examples in other sports, and personal stories related to dual careers. Discover best practices in Austria, Bulgaria, Greece, North Macedonia
0 views • 23 slides
Approximating Steiner Forest and GW Primal-Dual Approach
The GW primal-dual approach for solving Steiner forest problems involves minimizing costs while ensuring certain connectivity constraints are met. Violated sets, primal and dual formulations, and increasing dual values play key roles in this approximation algorithm.
0 views • 15 slides
St. Johns River State College Dual Enrollment Information
Explore the opportunities and benefits of the Dual Enrollment program at St. Johns River State College. High school students can earn college credits while still in high school, saving time and money towards a college degree. With various programs offered, eligibility criteria, placement testing, an
0 views • 13 slides
Evolving Computer Communication and Networks: P2P Networking, Media Streaming, CDN
Delve into the continuously evolving landscape of computer communication and networks, focusing on P2P networking, media streaming, and CDN technologies. Explore topics such as overlays, P2P applications, multimedia streaming advancements, and the interplay between internet, data processing, and dis
0 views • 63 slides