Evolution of IBM System/360 Architecture and Instruction Set Architectures
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing by offering forward and backward compatibility, a unified instruction set architecture (ISA), and a balance between scientific and business efficiency. The critical elements of this architecture
0 views • 18 slides
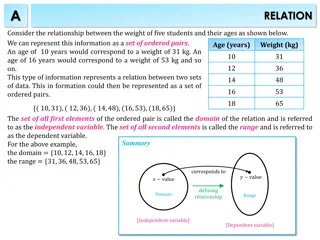
Understanding Domain and Range of Functions
Understanding functions involves exploring concepts such as domain, range, and algebraic inputs. This content covers topics like constructing functions, common functions like quadratic and trigonometric, and solving functions based on given domain and range. It also provides practice questions to te
1 views • 21 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs sharing one memory with a global address space, with challenges like the cache coherence problem. This summary delves into UMA and NUMA architectures, addressing issues like memory latency and bandwidth, as well as the bus-based UMA and NUMA shared m
0 views • 27 slides
Gradual Fine-Tuning for Low-Resource Domain Adaptation: Methods and Experiments
This study presents the effectiveness of gradual fine-tuning in low-resource domain adaptation, highlighting the benefits of gradually easing a model towards the target domain rather than abrupt shifts. Inspired by curriculum learning, the approach involves training the model on a mix of out-of-doma
0 views • 17 slides
Exploring Logical Agents and Architectures in Wumpus World
Explore the use of logical agents in the Wumpus World domain through three agent architectures: reflex agents, model-based agents, and goal-based agents. Understand how these agents operate in the challenging environment of the Wumpus World, where the task is to find the gold, return to starting pos
0 views • 21 slides
Understanding Domain Adaptation in Machine Learning
Domain adaptation in machine learning involves transferring knowledge from one domain to another. It addresses the challenge of different data distributions in training and testing sets, leading to improved model performance. Techniques like domain adversarial training and transfer learning play a k
0 views • 16 slides
Understanding Integrity Constraints in Relational Database Systems
Integrity constraints play a crucial role in maintaining the accuracy and integrity of data in a database. They include domain constraints, entity integrity, and referential integrity, each serving a specific purpose to ensure data consistency and reliability. Domain constraints ensure values in a c
0 views • 12 slides
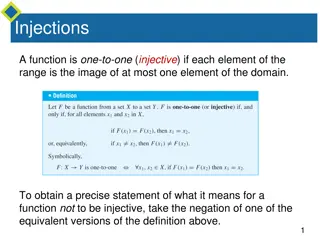
Understanding Injective and Surjective Functions
Injective functions map elements from the domain to the range uniquely, while surjective functions ensure every element in the co-domain has a corresponding element in the domain. The negation of injective means finding x1 and x2 in the domain with the same function value but not equal, whereas for
0 views • 26 slides
Introduction to PDDL Planning Domain
PDDL (Planning Domain Description Language) is a language based on STRIPS with various extensions originally defined by Drew McDermott. It is used in the International Planning Competition (IPC) series and offers a standard input for many planners. Tasks are specified using two files: domain file an
6 views • 13 slides
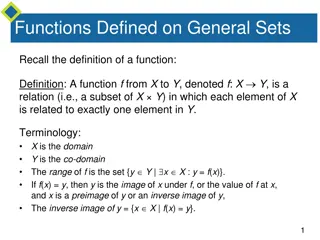
Understanding Functions: Definitions and Arrow Diagrams
Recall the definition of a function, where each element in the domain is related to exactly one element in the co-domain. Arrow diagrams can visually represent functions from finite sets X to Y. In this example, a function is defined from X = {a, b, c} to Y = {1, 2, 3, 4} using arrow diagrams, showc
7 views • 28 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs accessing a common memory, leading to challenges like the cache coherence problem. This article delves into different types of shared memory architectures, such as UMA and NUMA, and explores the cache coherence issue and protocols. It also highlights
2 views • 27 slides
Understanding Operating System Protection Principles
Explore the goals, principles, and implementation of protection in computer systems, including access matrix, domain structure, and capability-based systems. Learn how protection domains and access control are used to specify resource access, and delve into the concept of least privilege and dynamic
4 views • 21 slides
Understanding Relations and Functions in Mathematics
A relation is a correspondence between two sets where each element in the first set (domain) corresponds to at least one element in the second set (range). Functions are special relations where each element in the domain has a unique correspondence in the range. Surjective functions map the entire r
0 views • 12 slides
Understanding Domain Name Service (DNS) in Linux Network Administration
Domain Name Service (DNS) is a crucial scheme for resolving hostnames in a network, eliminating the need to record all hostnames in a local file. The Berkeley Internet Name Domain service (BIND) is a prominent DNS implementation providing efficient hostname resolution. DNS organizes hostnames in a h
0 views • 35 slides
Variations in Computer Architectures: RISC, CISC, and ISA Explained
Delve into the realm of computer architectures with a detailed exploration of Reduced Instruction Set Computing (RISC), Complex Instruction Set Computing (CISC), and Instruction Set Architecture (ISA) variations explained by Prof. Kavita Bala and Prof. Hakim Weatherspoon at Cornell University. Explo
0 views • 55 slides
Country Names in the Domain Name System (DNS)
The Domain Name System (DNS) plays a crucial role in attributing top-level and second-level domains to country names. This system is global and managed by ICANN, not national offices, allowing for unique attribution to one person. Examples of country names registered as second-level domains are prov
0 views • 7 slides
Research Insights on Future Internet Architectures
This survey explores key research topics in designing future internet architectures, focusing on innovations, content/data-oriented paradigms, mobility challenges, cloud-computing architectures, security considerations, and experimental testbeds. The study emphasizes the need for collaborative proje
0 views • 43 slides
Introduction to PDDL Planning Domain Language
PDDL (Planning Domain Description Language) is a language based on STRIPS with various extensions, widely used in the International Planning Competition. It allows for specifying tasks via domain and problem files, representing predicates, operators, objects, initial states, and goal states. Blackbo
0 views • 11 slides
Hierarchical Attention Transfer Network for Cross-domain Sentiment Classification
A study conducted by Zheng Li, Ying Wei, Yu Zhang, and Qiang Yang from the Hong Kong University of Science and Technology on utilizing a Hierarchical Attention Transfer Network for Cross-domain Sentiment Classification. The research focuses on sentiment classification testing data of books, training
0 views • 28 slides
Embedded Computer Architecture - Instruction Level Parallel Architectures Overview
This material provides an in-depth look into Instruction Level Parallel (ILP) architectures, covering topics such as hazards, out-of-order execution, branch prediction, and multiple issue architectures. It compares Single-Issue RISC with Superscalar and VLIW architectures, discussing their differenc
0 views • 49 slides
General Medical Imaging Dataset for Two-Stage Transfer Learning
This project aims to provide a comprehensive medical imaging dataset for two-stage transfer learning, facilitating the evaluation of architectures utilizing this approach. Transfer learning in medical imaging involves adapting pre-trained deep learning models for specific diagnostic tasks, enhancing
0 views • 16 slides
Developing MPI Programs with Domain Decomposition
Domain decomposition is a parallelization method used for developing MPI programs by partitioning the domain into portions and assigning them to different processes. Three common ways of partitioning are block, cyclic, and block-cyclic, each with its own communication requirements. Considerations fo
0 views • 19 slides
Understanding Cross-Domain Policies in Web Application Security
This content explores various aspects of cross-domain policies in web applications, including the Same-Origin Policy for JavaScript and Flash, their importance in protecting user data, potential risks of bypassing these policies, and the implications of trusting Flash content to read data from exter
0 views • 64 slides
Challenges in Establishing a Secure Inter-Domain Routing System
The daunting task of creating a secure and trusted inter-domain routing system poses significant challenges due to the decentralized nature of the internet. Addressing issues such as propagation of false routing information, ensuring correct reachability, and dealing with the lack of a clear truth m
0 views • 15 slides
Wyoming Eminent Domain Laws - Legal Updates and Negotiations
Wyoming Legislative Changes to Eminent Domain Laws outline the requirements for exercising eminent domain, including proof of public interest and necessity, diligent negotiations, and proper notification to property owners. The laws also emphasize the importance of good faith negotiations and fair c
0 views • 9 slides
Introduction to Ontology in Computer Science
Ontology is the study of existence, with applications in various fields like philosophy, linguistics, and computer science. In computer science, an ontology is an engineering artifact that defines a specific vocabulary to describe a domain, along with explicit assumptions about the vocabulary's inte
0 views • 33 slides
Important Update: Change of CORE Domain Code and Impacted Auction Information
An important update has been issued regarding a change in the CORE domain code, impacting auctions for the CORE region. The new domain code and its application date have been specified, along with details on affected auctions and files. Additionally, information on a test phase for long-term and sha
0 views • 4 slides
Understanding OpenMP Programming on NUMA Architectures
In NUMA architectures, data placement and thread binding significantly impact application performance. OpenMP plays a crucial role in managing thread creation/termination and variable sharing in parallel regions. Programmers must consider NUMA architecture when optimizing for performance. This invol
0 views • 18 slides
Understanding Computer Systems and Operating System Architectures
An exploration of computer systems and operating system architectures, covering topics such as CPU modes, monolithic and layered architectures, microkernel architecture, Linux and Windows kernel architectures, as well as devices and their terminology. The content delves into the roles, structures, a
0 views • 57 slides
Understanding Domain Names for Authoritative DNS Servers
Researchers need to accurately define the types of authoritative DNS servers they sample when measuring server properties. This study focuses on collecting domain names used for web servers to assess typical domain name characteristics, highlighting the importance of accurate data for research purpo
0 views • 7 slides
Understanding the Domain Name System (DNS) Structure
The Domain Name System (DNS) is a distributed data collection utilizing a delegation hierarchy to reflect the hierarchical structure of domain names. This system resolves DNS names by discovering information through iterative searches, starting from the root zone. The process involves querying serve
0 views • 25 slides
Exploring Efficient Hardware Architectures for Deep Neural Network Processing
Discover new hardware architectures designed for efficient deep neural network processing, including SCNN accelerators for compressed-sparse Convolutional Neural Networks. Learn about convolution operations, memory size versus access energy, dataflow decisions for reuse, and Planar Tiled-Input Stati
0 views • 23 slides
Securing Domain Control with BGP Attacks and Digital Certificates
Exploring the vulnerabilities of domain control verification in the context of BGP attacks and the role of digital certificates in ensuring security. The process of domain control verification, issuance of digital certificates by Certificate Authorities (CAs), and the significance of Public Key Infr
0 views • 53 slides
Exploring the Classic Blocks World Domain
Discover the classic blocks world domain, starting with the BW domain file and solving problems using planning domains. Learn about predicates, constants, and actions to manipulate objects effectively within the domain.
0 views • 10 slides
Open-Domain Question Answering Dataset WikiQA Overview
This content discusses the WikiQA dataset, a challenge dataset for open-domain question answering. It covers topics such as question answering with knowledge base, answer sentence selection, QA sentence dataset, issues with QA sentence dataset, and WikiQA dataset details. Various aspects of open-dom
0 views • 24 slides
Understanding the Role of CCNSO Study Group on Emoji in the Internet Community
The CCNSO Study Group on Emoji was established to address the use of emojis as second-level domains within the ccTLD community. This study group aims to provide a comprehensive overview of the associated issues and current practices, potentially advising on further actions. The group was initiated i
0 views • 18 slides
Ensuring Secure Internet Connections: Understanding Domain Verification
This content delves into the importance of verifying domain authenticity to safeguard against potential online scams and phishing attempts. It explores how organizations like the Commonwealth Bank of Australia use domain name certification processes, encryption techniques, and trusted third parties
0 views • 54 slides
Evolution of Domain Name System (DNS) Since 1983
Domain Name System (DNS) has played a crucial role in converting domain names to IP addresses since its inception in 1983. This system has revolutionized the way we navigate the internet, translating human-readable names into machine-readable IP addresses. The distributed and hierarchical nature of
0 views • 23 slides
Exploring Accelerators and Emerging Architectures in Specialized Computing
Delve into the world of accelerators and specialized computing architectures with a focus on application-specific designs like GPUs and FPGAs. Discover the challenges of performance efficiency and generality in the Iron Triangle paradigm, alongside innovative solutions presented in recent research p
0 views • 61 slides
Performance Comparison of 40G NFV Environments
This study compares the performance of 40G NFV environments focusing on packet processing architectures and virtual switches. It explores host architectures, NFV related work, evaluation of combinations of PM and VM architectures with different vswitches, and the impact of packet processing architec
0 views • 24 slides