Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
6 views • 46 slides
Adversarial Machine Learning in Cybersecurity
Adversarial Machine Learning (AML) is a critical aspect of cybersecurity, addressing the complexity of evolving cyber threats. Security analysts and adversaries engage in a perpetual battle, with adversaries constantly innovating to evade defenses. Machine Learning models offer promise in combating
1 views • 43 slides
Gradual Fine-Tuning for Low-Resource Domain Adaptation: Methods and Experiments
This study presents the effectiveness of gradual fine-tuning in low-resource domain adaptation, highlighting the benefits of gradually easing a model towards the target domain rather than abrupt shifts. Inspired by curriculum learning, the approach involves training the model on a mix of out-of-doma
3 views • 17 slides
Domain Adaptation in Machine Learning
Domain adaptation in machine learning involves transferring knowledge from one domain to another. It addresses the challenge of different data distributions in training and testing sets, leading to improved model performance. Techniques like domain adversarial training and transfer learning play a k
10 views • 16 slides
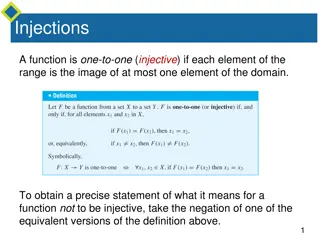
Injective and Surjective Functions
Injective functions map elements from the domain to the range uniquely, while surjective functions ensure every element in the co-domain has a corresponding element in the domain. The negation of injective means finding x1 and x2 in the domain with the same function value but not equal, whereas for
7 views • 26 slides
Adversarial Attacks in Machine Learning
Adversarial attacks in machine learning aim to investigate the robustness and fault tolerance of models, introduced by Aleksander Madry in ICML 2018. This defensive topic contrasts with offensive adversarial examples, which seek to misclassify ML models. Techniques like Deep-Fool are recognized for
4 views • 29 slides
Adversarial Machine Learning Attacks
Adversarial Machine Learning (AML) involves attacks on machine learning models by manipulating input data to deceive the model into making incorrect predictions. This includes creating adversarial examples, understanding attack algorithms, distance metrics, and optimization problems like L-BFGS. Var
2 views • 88 slides
Adversarial Threats in Machine Learning
This document explores the world of adversarial threats in machine learning, covering topics such as attack nomenclature, dimensions in adversarial learning, influence dimension, causative and exploratory approaches in attacks, and more. It delves into how adversaries manipulate data or models to co
5 views • 10 slides
Limitations of Deep Learning in Adversarial Settings
Deep learning, particularly deep neural networks (DNNs), has revolutionized machine learning with its high accuracy rates. However, in adversarial settings, adversaries can manipulate DNNs by crafting adversarial samples to force misclassification. Such attacks pose risks in various applications, in
1 views • 38 slides
Adversarial Learning in ML: Combatting Internet Abuse & Spam
Explore the realm of adversarial learning in ML through combating internet abuse and spam. Delve into the motivations of abusers, closed-loop approaches, risks of training on test data, and tactics used by spammers. Understand the challenges and strategies involved in filtering out malicious content
2 views • 13 slides
Distillation as a Defense Against Adversarial Perturbations in Deep Neural Networks
Deep Learning has shown great performance in various machine learning tasks, especially classification. However, adversarial samples can manipulate neural networks into misclassifying inputs, posing serious risks such as autonomous vehicle accidents. Distillation, a training technique, is proposed a
8 views • 31 slides
Robustness to Adversarial Examples in Machine Learning
Explore the vulnerability of machine learning models to adversarial examples, including speculative explanations and the importance of linear behavior. Learn about fast gradient sign methods, adversarial training of deep networks, and overcoming vulnerabilities. Discover how linear perturbations imp
3 views • 37 slides
Country Names in the Domain Name System (DNS)
The Domain Name System (DNS) plays a crucial role in attributing top-level and second-level domains to country names. This system is global and managed by ICANN, not national offices, allowing for unique attribution to one person. Examples of country names registered as second-level domains are prov
4 views • 7 slides
Hierarchical Attention Transfer Network for Cross-domain Sentiment Classification
A study conducted by Zheng Li, Ying Wei, Yu Zhang, and Qiang Yang from the Hong Kong University of Science and Technology on utilizing a Hierarchical Attention Transfer Network for Cross-domain Sentiment Classification. The research focuses on sentiment classification testing data of books, training
1 views • 28 slides
Developing MPI Programs with Domain Decomposition
Domain decomposition is a parallelization method used for developing MPI programs by partitioning the domain into portions and assigning them to different processes. Three common ways of partitioning are block, cyclic, and block-cyclic, each with its own communication requirements. Considerations fo
3 views • 19 slides
Understanding Zero-Shot Adversarial Robustness for Large-Scale Models
Pretrained large-scale vision-language models like CLIP show strong generalization on unseen tasks but are vulnerable to imperceptible adversarial perturbations. This work delves into adapting these models for zero-shot transferability in adversarial robustness, even without specific training on unk
4 views • 18 slides
Cross-Domain Policies in Web Application Security
This content explores various aspects of cross-domain policies in web applications, including the Same-Origin Policy for JavaScript and Flash, their importance in protecting user data, potential risks of bypassing these policies, and the implications of trusting Flash content to read data from exter
4 views • 64 slides
Wyoming Eminent Domain Laws - Legal Updates and Negotiations
Wyoming Legislative Changes to Eminent Domain Laws outline the requirements for exercising eminent domain, including proof of public interest and necessity, diligent negotiations, and proper notification to property owners. The laws also emphasize the importance of good faith negotiations and fair c
0 views • 9 slides
Domain Names for Authoritative DNS Servers
Researchers need to accurately define the types of authoritative DNS servers they sample when measuring server properties. This study focuses on collecting domain names used for web servers to assess typical domain name characteristics, highlighting the importance of accurate data for research purpo
1 views • 7 slides
Securing Domain Control with BGP Attacks and Digital Certificates
Exploring the vulnerabilities of domain control verification in the context of BGP attacks and the role of digital certificates in ensuring security. The process of domain control verification, issuance of digital certificates by Certificate Authorities (CAs), and the significance of Public Key Infr
4 views • 53 slides
Evolution of Domain Name System (DNS) Since 1983
Domain Name System (DNS) has played a crucial role in converting domain names to IP addresses since its inception in 1983. This system has revolutionized the way we navigate the internet, translating human-readable names into machine-readable IP addresses. The distributed and hierarchical nature of
0 views • 23 slides
Efficient Image Compression Model to Defend Adversarial Examples
ComDefend presents an innovative approach in the field of computer vision with its efficient image compression model aimed at defending against adversarial examples. By employing an end-to-end image compression model, ComDefend extracts and downscales features to enhance the robustness of neural net
1 views • 16 slides
Defense Against Adversarial Images using Web-Scale Nearest-Neighbor Search
This study explores a method to defend against adversarial images by approximating their projection onto the image manifold through nearest-neighbor search. The approach involves finding the nearest neighbors in a web-scale image database to classify and mitigate the impact of adversarial perturbati
4 views • 15 slides
Intelligent Information Processing Lab – Seminar Insights
The Intelligent Information Processing Lab seminar delved into advanced techniques such as deep learning approaches, geometric transformations, color space transformations, and adversarial training. With a focus on plant image data augmentation, the lab showcased innovative methodologies such as GAN
0 views • 8 slides
Spectral Normalization for Generative Adversarial Networks
Spectral normalization is a technique used in Generative Adversarial Networks (GANs) to address issues like non-convergence, mode collapse, and gradient problems. By normalizing the spectral norm of weight matrices, SN helps stabilize training and improve quality. Explore the benefits and applicatio
2 views • 22 slides
Automatic Modulation Recognition Using Generative Adversarial Networks
In the realm of spectrum sensing, the demand for automatic modulation recognition (AMR) has intensified due to the scarcity of spectrum resources. This study delves into the utilization of Generative Adversarial Networks (GAN) to automate AMR, a departure from manual methods. By employing GAN's gene
2 views • 13 slides
Generative Adversarial Networks
In this informative content, explore the concepts of generative adversarial networks, synthetic data, hand shapes, 3D hand orientation, hand pose estimation applications, and labeling data for hand pose. Discover how synthetic data is used in training, the flexibility of hand shapes, the impact of 3
0 views • 60 slides
Adversarial Examples in Neural Networks
Adversarial examples in neural networks refer to inputs intentionally modified to cause misclassification. This phenomenon occurs due to the sensitivity of deep neural networks to perturbations, making them vulnerable to attacks. By understanding the generation and impact of adversarial examples, re
1 views • 14 slides
Workshop on Adversarial Machine Learning and Voice Assistant Vulnerabilities
Explore the innovative discussions at the AIMCOM2 Workshop on Adversarial Machine Learning and Voice Assistant Vulnerabilities, featuring insights from Ananthram Swami and Yingying Chen on critical topics in network protocols and edge computing. Discover the latest advancements in detecting and defe
0 views • 4 slides
Domain Name System (DNS) and Content Delivery Networks (CDNs)
Explore the fundamentals of DNS and CDNs in computer networks, covering topics such as domain organization, address conversion protocols, the importance of domain names, and the process of translating domain names to IP addresses. Discover the challenges and complexities involved in navigating, cach
5 views • 59 slides
Adversarial Machine Learning Attacks and Defenses
Learn about the challenges posed by adversarial machine learning attacks such as poisoning and evasion, and explore offensive and defensive strategies to protect machine learning models. Discover how attackers manipulate training data to misclassify inputs and how defenders can counter such attacks
6 views • 9 slides
Adversarial Search in Competitive Environments: A Deep Dive
Delve into the world of adversarial search in competitive environments where agents strategize against each other, focusing on zero-sum games like chess. Explore game setup, minimax strategy, and the challenges of decision-making in adversarial settings.
2 views • 21 slides
Powerful Generative Adversarial Networks in Medical Imaging
Discover the power of Generative Adversarial Networks (GANs) in medical imaging, where two neural networks collaborate to generate realistic images and handle domain shifts. Explore challenges, popular GAN models like CycleGAN and ProGAN, and potential solutions for diverse image synthesis across do
0 views • 8 slides
Neural Network Robustness from a Probabilistic Perspective
Explore the intriguing behavior of neural networks, the discovery of adversarial examples, challenges in training robust networks, and the shift towards non-adversarial robustness considerations. Learn about local and global robustness specifications and the probabilistic view on maintaining neural
2 views • 12 slides
Solving Problems in Classic Blocks World Domain
Explore the Classic Blocks World domain starting with BW domain file, solving problems using planning domains, and extending the domain with predicates and constants. Learn about basic add and delete effects in actions, defining predicates and actions, and executing pick-up, put-down, stack, and uns
2 views • 11 slides
Julia Machine Learning: Adversarial Algorithms & Practical Applications
Discover the world of adversarial machine learning in Julia, including the intricacies of adversarial algorithms, distance metrics, and practical applications such as malware detection. Learn why Julia is a preferred language for machine learning tasks and how it excels in optimization challenges. U
0 views • 9 slides
Adversarial Learning in ML: Internet Abuse & Spam
Explore the complexities of adversarial learning in machine learning, focusing on combating internet abuse and spam. Discover the motivations behind online abuse, the closed-loop approach to filter spam, risks of training on test data, and tactics used by spammers. Gain insights into the challenges
0 views • 13 slides
Mitigating Attacks in Machine Learning Models with Defensive Strategies
Explore the challenges of adversarial attacks in machine learning, such as poisoning and evasion attacks, and learn about offensive and defensive strategies to safeguard models against malicious manipulation. Discover how to identify and counteract adversarial inputs, protect against backdoor attack
12 views • 9 slides
Adversarial Examples for Reading Comprehension Evaluation
Dive into the world of adversarial examples used to evaluate reading comprehension systems, with a focus on understanding language and human performance. Explore how models like BiDAF Ensemble are tested with adversarial questions and see the impact of adding grammatical sentences to improve system
1 views • 70 slides
Understanding Domain Name System (DNS) Hierarchy and Structure
Explore the hierarchical structure of the Domain Name System (DNS) through detailed explanations and visual representations. Learn about top-level domains, fully qualified domain names, namespace organization, and resource records. Enhance your understanding of how DNS translates domain names to IP
1 views • 44 slides