Understanding the Significance of IDAHOBiT Day and Pride Flags
International Day Against Homophobia, Transphobia, and Biphobia (IDAHOBiT) is observed on May 17th to raise awareness about discrimination faced by the LGBTQ+ community. Flying the rainbow flag symbolizes acceptance and solidarity. Learn about the history of Pride flags, including the evolution of t
0 views • 14 slides
Honoring the United States Flag: Etiquette and Protocol
This content provides a detailed guide on how to honor the United States flag according to the U.S. Flag Code Title 4 Chapter 1. It covers topics such as saluting the flag, displaying the flag, and the proper etiquette during ceremonies involving the flag, such as the National Anthem and Pledge of A
0 views • 19 slides
Understanding the FLAGS Register in Assembly Language
An exploration of the FLAGS register in assembly language, highlighting the key status flags such as Carry Flag (CF), Parity Flag (PF), Auxiliary Carry Flag (AF), Zero Flag (ZF), Sign Flag (SF), and Overflow Flag (OF). These flags play a crucial role in reflecting the outcome of operations within th
0 views • 24 slides
Understanding Flag Registers in Microprocessor 8086
This content discusses the flag registers in the Microprocessor 8086, covering conditional flags such as Carry Flag (CF), Auxiliary Flag (AF), Parity Flag (PF), Zero Flag (ZF), Sign Flag (SF), and Overflow Flag (OF), as well as control flags including Trap Flag (TP), Interrupt Flag (IF), and Directi
1 views • 23 slides
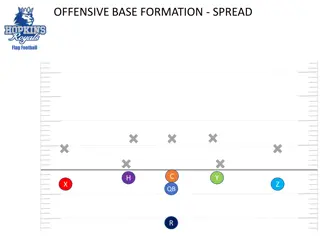
Flag Football Formations and Templates Collection
Explore a comprehensive collection of flag football formations, offensive and defensive templates, and playbook strategies through detailed images and descriptions. From spread formations to defensive setups, this resource provides insights for enhancing your flag football game. Dive into the world
0 views • 9 slides
Roadmap for DNS Load Balancing Service at CERN - HEPiX Autumn 2020 Workshop
This roadmap presented by Kristian Kouros on behalf of the DNS Load Balancing Team at CERN outlines the introduction, implementation, and upgrades associated with the DNS Load Balancing Service. It covers topics such as system architecture, LBClient metrics, and the overall structure of the service.
3 views • 29 slides
Overview of 8086 Assembly Language Arithmetic Operations
The 8086 assembly language provides instructions for arithmetic operations such as addition, subtraction, and comparison. These operations are essential for manipulating data in memory and registers. The instructions support various operand types, including registers, memory locations, and immediate
0 views • 24 slides
Understanding Domain Name Service (DNS) in Linux Network Administration
Domain Name Service (DNS) is a crucial scheme for resolving hostnames in a network, eliminating the need to record all hostnames in a local file. The Berkeley Internet Name Domain service (BIND) is a prominent DNS implementation providing efficient hostname resolution. DNS organizes hostnames in a h
0 views • 35 slides
DNS Research Federation: Advancing Understanding of Cybersecurity Impact
The DNS Research Federation, a UK non-profit organization, aims to advance the understanding of the Domain Name System's impact on cybersecurity, policy, and technical standards through education, research, and improved data access. Motivated by the need to measure resolver capabilities, they have d
0 views • 17 slides
Understanding DNS Firewall Architecture at Virginia Tech
Virginia Tech implements Response Policy Zone (RPZ) as a mechanism in the DNS system to protect clients from malicious domains. The RPZ allows recursive resolvers to customize responses for specific zones, enhancing security against malware callbacks. Working with campus partners, the RPZ database a
0 views • 11 slides
Understanding BIND DNS Security Vulnerabilities and Configuration
Dive into the world of BIND DNS with a focus on security vulnerabilities, zone transfer restrictions, rate limiting, and essential configuration options. Explore key topics such as ISC mailing lists, CVE announcements, and best practices for setting up BIND DNS servers.
0 views • 16 slides
Understanding DNS Replication with BIND9
Explore the intricacies of DNS replication using BIND9, including the role of authoritative name servers, the importance of serial numbers, and the process of data transfer between master and slave servers. Discover insights on maintaining consistency in zone data to ensure smooth DNS operations.
2 views • 39 slides
Automating DNS Maintenance with Catalog Zones: A New Approach
Explore a fresh method for automating maintenance in DNS servers through catalog zones, focusing on dynamic configuration data. Learn about generating includes for various DNS daemons and enhancing zone management efficiency. Discover how to streamline provisioning and loading processes with Python,
0 views • 12 slides
Celebrating Republic Day of India: History, Importance, and Traditions
The Republic Day of India, celebrated on January 26th, marks the adoption of the Indian Constitution in 1950. It signifies the transition from a British Dominion to a republic. Dr. B.R. Ambedkar played a pivotal role in drafting the constitution. The day is commemorated with flag hoisting, parades,
0 views • 10 slides
Flag Display Guidelines in Parades
Understand the guidelines for displaying flags in parades, focusing on the U.S. flag's positioning and respect. Learn about the U.S. flag, the Maryland flag, the Adventist Youth flag, and the Christian flag, each with its unique design and symbolism.
0 views • 13 slides
United States Flag Etiquette and Naval Traditions
Explore the traditional meanings of the colors on the U.S. flag, the history behind the Don't Tread on Me flag, proper procedures for disposing of a worn U.S. Ensign, guidelines for raising and lowering the National Ensign at half-mast, the history of colors in naval practices, the origin of Bravo Z
1 views • 14 slides
Understanding Domain Name System (DNS) and Content Distribution Networks (CDNs)
This lecture delves into the fundamentals of the Domain Name System (DNS), highlighting the differences between DNS hostname and IP address, the various uses of DNS, the original design challenges of DNS, its goals and non-goals, and the hierarchical structure of the DNS. It also covers the role of
0 views • 60 slides
DNS Forensics & Protection: Analyzing and Securing Network Traffic
DNS Forensics involves using DNS traffic to analyze network health, detect anomalous behavior, and combat malicious activities. By understanding DNS activity on systems and implementing defense strategies, users and network providers can enhance security and privacy.
0 views • 16 slides
Unveiling IBDNS: The Intentionally Broken DNS Server
Uncover the unique server, IBDNS, intentionally designed to simulate faulty DNS scenarios for testing. Explore its unconventional testing tools, coverage of RFCs, and architecture focusing on file zones and bit-flip examples. Delve into testing methodologies and response simulations tailored for dia
0 views • 17 slides
Understanding DNS Performance and Issues in Information-Centric Networks
DNS (Domain Name System) plays a crucial role in the Internet and web infrastructure, impacting scalability and content delivery. This content delves into DNS issues, comparing ISP DNS with Google DNS and OpenDNS in terms of latency, caching, and performance with CDNs. It explores how caching, third
0 views • 12 slides
Understanding DNS Flag Day and EDNS: A Comprehensive Overview
DNS Flag Day marks a coordinated effort to remove workarounds in DNS implementations, impacting domains in various ccTLDs like .CL, .CZ, .SE, .NU, and .NZ. Enhanced DNS (EDNS) provides a mechanism for supporting new options, but issues arise from poor DNS implementations causing delays and hindering
0 views • 20 slides
DNS Testing and Signatures Rollover Analysis
In this content, Geoff Huston from APNIC discusses DNS testing and transport considerations, focusing on the rolling roots process. The discussion includes insights on rolling root keys, KSK repositories in the US and Amsterdam, and a step-by-step guide on how to perform a Key Signing Key (KSK) roll
0 views • 39 slides
Understanding X86 ISA Flags in System Security
This article delves into the details of various flags in the X86 ISA architecture, such as CF (Carry Flag), PF (Parity Flag), AF (Auxiliary Flag), ZF (Zero Flag), SF (Sign Flag), TF (Trace Flag), IF (Interrupt Flag), DF (Direction Flag), OF (Overflow Flag), and IOPL (Input Output Privilege Level). T
0 views • 16 slides
Improving DNS Security with KINDNS Best Practices
Best practices for improving DNS resilience and security are crucial for protecting billions of Internet users. Initiatives like KINDNS aim to establish global norms to enhance DNS security by codifying these practices. The KINDNS group focuses on practices for authoritative and recursive nameserver
0 views • 17 slides
Understanding Domain Names for Authoritative DNS Servers
Researchers need to accurately define the types of authoritative DNS servers they sample when measuring server properties. This study focuses on collecting domain names used for web servers to assess typical domain name characteristics, highlighting the importance of accurate data for research purpo
0 views • 7 slides
Understanding DNS Centrality: The Internet's Core Challenge
Delve into the critical issue of DNS centrality on the Internet, its impact on competition and innovation, and the consolidation trends shaping service provision. Explore the implications of a single entity controlling the DNS and its broader influence on the online ecosystem in just 20 minutes. Unc
0 views • 50 slides
Challenges of DNS Centrality in Internet Infrastructure
The presentation discusses the issue of centrality in the DNS and its impact on the Internet. It explores the implications of concentration of control, economic considerations, and the history of consolidation in DNS services. The importance of competition, innovation, and consumer benefits are high
0 views • 47 slides
Understanding Factors in Country Names and DNS Confusion
This content explores the intricacies of country names in the Domain Name System (DNS), covering long-form, short-form, colloquial/native names, and more. It delves into the case of Switzerland as an example, detailing its various official and colloquial names. Additionally, the text discusses facto
0 views • 4 slides
Understanding the Domain Name System (DNS) Structure
The Domain Name System (DNS) is a distributed data collection utilizing a delegation hierarchy to reflect the hierarchical structure of domain names. This system resolves DNS names by discovering information through iterative searches, starting from the root zone. The process involves querying serve
0 views • 25 slides
Proactive Network Protection Through DNS Security Insights
Exploring proactive network protection methods using DNS, security challenges, botnet threats, firewall management, malware controls, and DNS-based malware control. Discussions on DNS security vulnerabilities, DNSSEC, threat intelligence, machine learning, and best practices like RPZ for DNS protect
0 views • 29 slides
Understanding Network Security Fundamentals
Explore the critical components of network security focusing on DNS, BGP, and RPKI. Learn about the importance of trust on the Internet, potential attacks, and measures to secure DNS and BGP protocols. Delve into naming hierarchy, DNS structure, hierarchical administration, and DNS server functions.
0 views • 70 slides
Understanding DNS Security Mechanisms
Various DNS security mechanisms like DNSSEC, DNS Cookies, CAA, SPF, DMARC, and more are crucial in protecting against security threats targeting the DNS ecosystem. This analysis delves into the prevalence and effectiveness of these mechanisms in countering vulnerabilities such as cache poisoning, am
0 views • 29 slides
Understanding DNSSEC: Adding Digital Signatures to DNS Responses
DNSSEC (Domain Name System Security Extensions) allows for the addition of digital signatures to DNS responses, ensuring the authenticity, completeness, and currentness of the data received by a client. By validating the digital signature, clients can trust the response received is genuine and unalt
0 views • 27 slides
Understanding DNS Registration: Importance and Process Explained
DNS registration is crucial for establishing online presence. It involves registering domain names like web pages and email addresses. HEAnet delegates to hosting providers, like IEDR, who ensure quality service and support customers. Timing is key - think about DNS registration at the project's sta
0 views • 7 slides
Evolution of Domain Name System (DNS) Since 1983
Domain Name System (DNS) has played a crucial role in converting domain names to IP addresses since its inception in 1983. This system has revolutionized the way we navigate the internet, translating human-readable names into machine-readable IP addresses. The distributed and hierarchical nature of
0 views • 23 slides
Exploring Our National Flag: A Lesson on Patriotism and Identity
Understanding the significance of national flags, this lesson focuses on the pride and symbolism associated with Bangladesh's flag. Through this exploration, students learn about the history, importance, and rituals surrounding the flag, promoting a sense of national identity and respect for freedom
0 views • 17 slides
Understanding DNS and Network Address Translation
DNS, or Domain Name System, is a vital component of the internet that translates domain names into IP addresses. This essential system allows users to easily navigate the web using familiar names instead of complex numbers. Explore the importance of DNS, its structure, and how it functions within co
0 views • 41 slides
Internet Society Armenia's Role in Managing and Enhancing Armenia's DNS Infrastructure
Internet Society Armenia (ISOC.AM) actively manages Armenia's country code top-level domain (ccTLD) and plays a crucial role in ensuring the stability, resilience, and security of the country's DNS servers. Through partnerships with organizations like ICANN and RIPE NCC, ISOC.AM oversees the operati
0 views • 23 slides
Enhancing Privacy in DNS Zone Exchanges
This work presents a privacy-aware schema for efficient distribution of Authoritative DNS Server zones to Recursive DNS Servers or scrubbing services. By utilizing probabilistic data structures like Cuckoo Filters, the system ensures efficient zone mapping, compatibility with existing DNS infrastruc
0 views • 17 slides
DNS Query Behavior Analysis: Understanding Queries for Non-Existent Names
Exploring the unexpected high number of DNS queries for non-existent names and the factors contributing to this behavior, including Happy Eyeballs and client query patterns. Revealing insights into the complexities of DNS resolution processes.
0 views • 27 slides