Public key encryption, Digital signature and authentication
Understand the concept of public key encryption, asymmetric encryption, and the widely used RSA algorithm. Explore how public key cryptography revolutionized the field of encryption and its applications in confidentiality, authentication, and key distribution.
4 views • 12 slides
Améliorer la planification des transplantations hépatiques avis d'experts d'éminents chirurgiens en Inde
\ud83d\udc68\u200d\u2695\ud83d\udc89\ud83d\udc8a\ud83e\ude7a Le pays a connu des d\u00e9veloppements significatifs dans le domaine de la transplantation h\u00e9patique, avec des installations m\u00e9dicales de classe mondiale et des professionnels qualifi\u00e9s obtenant des r\u00e9sultats remarquab
3 views • 9 slides
Understanding Security Threats and Public-Key Cryptosystems
Explore the world of security threats, passive and active attacks, and the importance of asymmetric encryption through the terminology related to asymmetric encryption, public-key cryptosystems, and public-key cryptography. Learn about the key components of public-key encryption schemes and the proc
0 views • 46 slides
Understanding AES Encryption Algorithm and Its Implementation
Learn about the Advanced Encryption Standard (AES) algorithm - a NSA-approved NIST standard encryption method. Explore how AES works, its key rounds, SubBytes, ShiftRows, MixColumns operations, and its optimization for embedded systems and small memory devices. Discover the importance of secure cryp
0 views • 14 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
2 views • 37 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
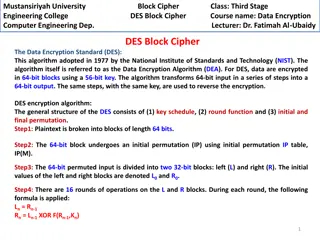
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
Deep Eutectic Solvents: Classification, Synthesis, and Applications
Deep Eutectic Solvents (DES) are versatile solvents formed by mixing specific acids and bases. These solvents exhibit unique hydrogen bonding properties, resulting in a lower melting point compared to individual components. DES can be classified into hydrophobic and hydrophilic types, each with dist
3 views • 7 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Exploring Cloud Cryptography for Secure Data Processing
Cloud cryptography is a vital aspect of data security in cloud computing, allowing data to be encrypted and processed securely. This presentation delves into the concepts of cloud cryptography, homomorphic encryption, and the two types of homomorphic encryption - hybrid and partial. It discusses the
8 views • 17 slides
Utilisation du Pack PowerPoint pour Intégrer des Cartes dans Vos Présentations
Ce pack de PowerPoint fournit des cartes simples et personnalisables que vous pouvez intégrer dans vos présentations et rapports en ajoutant vos propres données. Il inclut des outils tels que des symboles, des légendes et des étiquettes que vous pouvez facilement copier et coller. Sélectionnez
0 views • 16 slides
Security with Functional Re-Encryption in Cryptography
Exploring the concept of functional re-encryption from the perspective of security in encryption schemes lies between CPA and CCA security levels. The work done by Yevgeniy Dodis, Shai Halevi, and Daniel Wichs delves into how functional re-encryption can enhance the security and privacy of encrypted
0 views • 12 slides
Probabilistic Public Key Encryption with Equality Test Overview
An exploration of Probabilistic Public Key Encryption with Equality Test (PKE-ET), discussing its concept, applications, security levels, and comparisons with other encryption schemes such as PKE with Keyword Search and Deterministic PKE. The PKE-ET allows for perfect consistency and soundness in en
3 views • 17 slides
Overview of SMX Algorithm and AES Encryption Standard
The SMX Algorithm presents a fresh approach to the avalanche effect in the Advanced Encryption Standard (AES). Initially developed to overcome the limitations of the Data Encryption Standard (DES), AES boasts improved security and efficiency, supporting key lengths of 128, 192, and 256 bits. The AES
3 views • 19 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
The Vital Role of Encryption in Safeguarding the Digital Economy
Encryption plays a crucial role in protecting the digital economy by providing secure communication channels. Professor Peter Swire from Ohio State University emphasizes the need for strong encryption over weak cybersecurity measures. He discusses the history of wiretaps, the shift to strong cryptog
0 views • 15 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Cryptography Concepts and Encryption Methods Overview
Exploring elementary cryptography concepts such as encryption, cryptanalysis, symmetric and asymmetric encryption algorithms like DES, AES, and RSA. Delve into key exchange protocols, digital signatures, cryptographic hash functions, and the process of encryption and decryption in a cryptosystem.
0 views • 23 slides
Understanding Encryption: Keys, Algorithms, and Applications
Encryption plays a crucial role in securing data transmission and storage. It involves using keys and algorithms to convert plaintext information into a cipher that can only be deciphered with the correct key. This article explores different encryption methods, such as private and public key encrypt
0 views • 62 slides
Homomorphic Encryption Overview
Homomorphic encryption allows computation on encrypted data without revealing the underlying information. It enables secure delegation of data processing to a server while maintaining privacy. The process involves key generation, encryption, decryption, and evaluation of functions on encrypted data.
0 views • 40 slides
Bootstrapping in Fully Homomorphic Encryption
Fully Homomorphic Encryption (FHE) allows evaluation of unbounded-depth circuits without being limited by specific parameters. Bootstrapping is a critical technique to achieve full homomorphism by refreshing ciphertexts, enabling decryption functionalities within the encryption scheme. This process
0 views • 38 slides
Homomorphic Encryption and RLWE Schemes Overview
Homomorphic encryption allows computation on encrypted data, enabling privacy in outsourced computing services and applications like spam filters for encrypted mail. The Ring Learning With Errors (RLWE) scheme and its properties are discussed, along with symmetric encryption from RLWE and fully homo
0 views • 16 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Understanding Data Encryption and File Security
Exploring data encryption and file security, covering topics such as scenarios for encryption, file encryption methods, limitations, and secure file deletion techniques. Highlighting the challenges of balancing security, usability, and reliability in computer systems.
0 views • 29 slides
Understanding Unidirectional Updatable Encryption and Proxy Re-Encryption
Unidirectional updatable encryption and proxy re-encryption are key concepts in secure cryptography deployments. Key management and rotation are essential for secure encryption schemes such as Proxy Re-Encryption (PRE) and Updatable Encryption (UE). PRE allows delegation of decryption abilities, whi
0 views • 16 slides
Implementing Informix Encryption at Rest
Discover how to implement Encryption At Rest (EAR) in Informix, providing disk-level encryption for dbspaces within your instance. Learn about use cases, setting up EAR for new and existing instances, preparing the environment, and configuring disk encryption options like keystore and stash file nam
0 views • 18 slides
Email Security and Encryption Technologies Overview
Email security is crucial in today's digital world. This content discusses various email security measures, including PGP and S/MIME systems, and their utilization in business and personal communications. It also explores the history of PGP encryption, the role of Philip R. Zimmermann, and the chara
0 views • 10 slides
Data Encryption and File Security Overview
Explore the complexities and challenges of encrypting stored data, file encryption, and ensuring secure systems. Learn about the scenarios where data encryption is crucial, the limitations of file encryption, and the importance of secure data wiping practices for maintaining confidentiality. Delve i
0 views • 30 slides
Understanding RSA Public-key Cryptography in Data Encryption
Exploring the foundational concepts of RSA public-key cryptography and its applications in data encryption. Learn how messages can be encoded, transmitted securely, and decoded using encryption and decryption functions. Discover the significance of picking large primes and understanding the bijectio
1 views • 12 slides
Understanding RSA Encryption for Secure Communication
Encryption plays a vital role in securing information, and RSA encryption, developed by Rivest, Shamir, and Adleman in 1977, uses public and private keys to safeguard data. Learn about the process, challenges with other encryption methods, prime numbers, and how RSA encryption works step by step.
0 views • 24 slides
Understanding Encryption and its Importance in Everyday Life
Encryption is a crucial process that transforms messages into secret codes, ensuring only intended recipients can decipher them. This review delves into the significance of encryption for online activities, cracking different cipher methods, and recognizing security flaws. Discover how computational
0 views • 9 slides
Overview of Public Key Encryption Schemes by Dan Boneh
This content provides insights into public key encryption schemes such as Diffie-Hellman and ElGamal, as presented by cryptography expert Dan Boneh. Topics covered include key exchange, secure email, encryption applications, constructions, and a review of the Diffie-Hellman protocol. The material de
0 views • 41 slides
Ensuring Orthogonal Security in Data Encryption Processes
Addressing the challenge of data confidentiality in untrusted server environments through the use of encryption techniques such as deterministic and non-deterministic encryption. The goal is to achieve full functionality independently of data encryption, allowing for secure processing of data querie
0 views • 21 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides
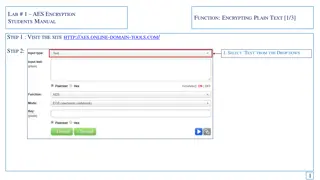
Guide to AES Encryption for Students - Encrypting and Decrypting Text
This manual provides a step-by-step guide on AES encryption for students. Learn how to encrypt plain text using a secure key, generate cipher text, and then decrypt it back to the original message. Follow the instructions on a specific website, enter your text, select encryption options, and save th
0 views • 6 slides