Overcoming the UX Challenges Faced by FIDO Credentials in the Faced by FIDO Credentials in the Consumer Space
Many websites are vulnerable to phishing attacks due to traditional authentication methods. To address this, the utilization of cryptographic authentication, such as key pairs, is recommended to enhance security and prevent MITM attacks.
0 views • 17 slides
Cryptographic Reductions and Learning in Computational Complexity
This lecture explores the connection between computational complexity and cryptography, focusing on topics like pseudorandom functions, public-key cryptography, and learning from Gaussians. It delves into the implications of cryptographic reductions, lower bounds for learning MLPs, and the existence
0 views • 22 slides
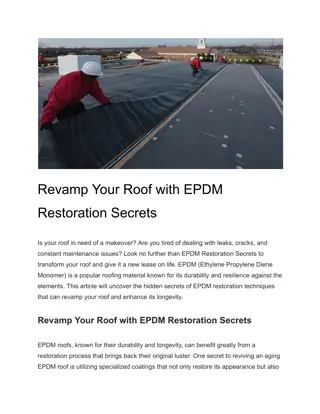
Revamp Your Roof with EPDM Restoration Secrets
Is your roof in need of a makeover? Are you tired of dealing with leaks, cracks, and constant maintenance issues? Look no further than EPDM Restoration Secrets to transform your roof and give it a new lease on life. EPDM (Ethylene Propylene Diene Monomer) is a popular roofing material known for its
0 views • 5 slides
Revamp Your Roof with EPDM Restoration Secrets
Is your roof in need of a makeover? Are you tired of dealing with leaks, cracks, and constant maintenance issues? Look no further than EPDM Restoration Secrets to transform your roof and give it a new lease on life. EPDM (Ethylene Propylene Diene Monomer) is a popular roofing material known for its
0 views • 5 slides
Understanding E-commerce Data Collection and Legal Frameworks
Explore the implications of collecting data in e-commerce activities, legal status of electronic transactions, and electronic signatures in this informative module. Learn about analyzing data, regulatory environments, and cryptographic codes.
0 views • 8 slides
5 Secrets You Should Know About Cannabis Terpene Testing
Terpenes, the aromatic compounds found in cannabis, play a significant role in shaping its effects, flavors, and therapeutic benefits. As the cannabis industry continues to evolve, terpene testing has become increasingly important for understanding and maximizing the potential of different cannabis
0 views • 3 slides
Challenges in Standard QUIC Protocol Implementation
The content discusses the challenges and shortcomings of the standard QUIC protocol implementation, focusing on the use of TLS 1.3 for cryptographic handshake. It highlights issues such as complexity in implementation and state machine, lack of a full security proof, and the risk of ossification due
0 views • 108 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
1 views • 41 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Exploring Secrets and Friendship Through Stories in PSHE Lesson
In this PSHE lesson for Year 5 pupils, the focus is on discussing feelings about secrets and friendship through stories. The lesson aims to help children understand the impact of secrets, recognize when to seek help, consider how their actions affect others, and address problems compassionately. Thr
0 views • 13 slides
Overview of the Official Secrets Act, 1923 in India
The Official Secrets Act, 1923 in India focuses on protecting official records of the Central and State Governments, safeguarding information privacy, and imposing penalties for activities prejudicial to the State's interests. Rooted in the British colonial era, the Act aims to maintain national sec
2 views • 12 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Understanding the Importance of Web Cryptography API and Its Application
The Web Cryptography API is a vital tool that enables end-to-end encryption and authentication in browsers. This API allows secure handling of cryptographic algorithms, providing access to native crypto libraries. While JavaScript is faster, the native code is more secure and battle-tested, making i
0 views • 111 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Post-Quantum Cryptography in IEEE 802.11 - Current State and Future Concerns
Submission discusses the potential impact of post-quantum algorithms on IEEE 802.11 networks, highlighting the necessity to prepare for a post-quantum future. It explores the risks posed by quantum computing to existing cryptographic systems and emphasizes the importance of adopting post-quantum sol
0 views • 19 slides
EU Trade Secrets Directive: Misappropriation and Legal Framework Overview
The European Union Trade Secrets Directive sets out rules and harmonization for misappropriation of trade secrets across member states, allowing room for more extensive protection by individual countries. This directive addresses unlawful acquisition, use, and disclosure of trade secrets, along with
0 views • 28 slides
Enhancing Cryptographic Key Generation with High-Quality Randomness
This presentation discusses the critical aspect of ensuring high-quality randomness in cryptographic key generation processes. It explores key vulnerabilities and common failure modes, emphasizing the importance of incorporating strong randomness. The content delves into various methods and issues r
0 views • 45 slides
Exploring Friendship, Secrets, and Supportive People in Year 1
Dive into a journey exploring feelings about friends, handling negative behaviors, dealing with secrets, and seeking help in the Year 1 curriculum. Engage in activities like choosing new friends, discussing good and bad secrets, and identifying supportive individuals. Discover the dynamics of friend
0 views • 11 slides
Study Group Secrets How to Maximize Your College Study Sessions
This article will delve into the secrets of creating productive and successful college study groups and how Explain Learning can further elevate your study experience. Know more \/\/explainlearning.com\/blog\/college-study-group-secrets\/
1 views • 3 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
Understanding Trade Secrets in Arkansas
Explore the dos and don'ts of Trade Secrets as defined by the Arkansas Trade Secret Act and APC&EC Rules. Learn about the key factors, evaluation criteria, and protection measures related to trade secrets, essential for businesses to safeguard their valuable information effectively.
0 views • 26 slides
Enhancing Security for XMSS and SPHINCS+ Using Machine-Checked Methods
Advanced cryptographic techniques such as XMSS and SPHINCS+ are critical for ensuring secure digital signatures in a post-quantum world. This project focuses on improving the security and verification processes of XMSS and SPHINCS+ using machine-checked methods, aiming to enhance trust in these cruc
1 views • 17 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Franco-Japanese Cybersecurity Workshop Highlights and Future Plans
The 5th Franco-Japanese Cybersecurity Workshop concluded with insightful discussions on key areas such as IoT security, AI, hardware security, and supply chain security. The steering committee members shared plans for the 6th workshop in France, emphasizing policy discussions and cross-cutting issue
0 views • 18 slides
Understanding the Defend Trade Secrets Act (DTSA) - Key Points and Implications
The Defend Trade Secrets Act (DTSA) is a federal law that provides important protections for trade secrets. This law covers various aspects such as the definition of a trade secret, reasonable efforts requirement, types of misappropriation, injunctions, damages, and more. The DTSA also includes prov
0 views • 8 slides
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computing utilizes the principles of quantum mechanics to process information exponentially faster than classical computers. This advancement poses a significant threat to current cryptographic systems, especially those reliant on factors like RSA and Diffie-Hellman key exchange. If large-sc
0 views • 25 slides
Exploring the Role of Blockchain as a Trusted Third Party in Decentralized Systems
Blockchain technology serves as a decentralized and cryptographic Trusted Third Party (TTP) by enhancing trust, immutability, and censorship resistance in transactions. By distributing trust and utilizing cryptographic protocols, blockchain mitigates the need for a centralized authority, offering a
0 views • 30 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Faster Implementation of Modular Exponentiation in JavaScript
Development of a cryptographic authentication toolkit for web application developers. Discusses modular exponentiation, digital signatures, elliptic curve cryptography, and the importance of DSA in providing secure authentication. Aims to offer both classical and elliptic curve cryptographic solutio
0 views • 22 slides
Post-Quantum Cryptography: Safeguarding Secrets in the Digital Age
Delve into the realm of post-quantum cryptography and learn about the evolving landscape of secure communication. Explore topics such as Supersingular Isogeny Graphs, Ring-Learning With Errors, and the significance of key exchange in maintaining confidentiality. Discover the foundations of public ke
0 views • 39 slides
Best Practices to Prevent Theft of Trade Secrets
This presentation discusses best practices to prevent theft of trade secrets, including identifying when to panic, triage steps to differentiate smoke from fire, defining wins upfront, recognizing trade secrets, restrictive covenants, evidence preservation, forensic analysis, smartphone evidence con
0 views • 66 slides
Understanding the Importance of Cryptographic Safety Valves in Legislation
Legislation regarding cryptographic safety valves is impending, with potential implications on privacy and security. Matt Tait discusses the need to analyze risks and consequences, emphasizing the importance of transparent and secure safety valves. The debate surrounds decryption requirements for da
0 views • 17 slides
Zeroizing Attacks on Cryptographic Multilinear Maps: Overview and Applications
Cryptographic multilinear maps (MMAPs) enable computations on encoded secret data, offering similarities to fully homomorphic encryption (FHE) while providing distinct features. MMAPs find applications in identity-based encryption, non-interactive zero-knowledge proofs, and more. The evolution of MM
0 views • 45 slides
Understanding Trade Secrets and Confidential Information Laws
Trade secrets and confidential information play a crucial role in business success. Learn what trade secrets are, how to share and protect them, and how to enforce against their misuse. Explore the legal definitions of trade secrets, their protection under the law, and the criteria that classify inf
0 views • 31 slides
Understanding Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
0 views • 28 slides
In-Process Isolation with Memory Protection Keys
Secure and efficient in-process isolation with memory protection keys is crucial in preventing security vulnerabilities and bugs, such as the Heartbleed bug. By implementing techniques like language and runtime isolation, cryptographic secrets can be securely managed from native libraries, safeguard
0 views • 56 slides
Overview of Trade Secrets and Legal Framework in the United States
Understanding trade secrets, their definition, protection, and examples is crucial for businesses operating in the United States. This content provides insights into the laws, including the Uniform Trade Secrets Act and the Economic Espionage Act, governing trade secrets at both state and federal le
0 views • 39 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Scalable Cryptographic Authentication for High Performance Computing
This work discusses the scalable cryptographic authentication approach developed by Andrew Prout and team for high-performance computing. The LLGrid system architecture, challenges with interactive supercomputing, and utilization of LLGrid for various computing tasks are explored, highlighting the i
0 views • 34 slides