Cryptographic Reductions and Learning in Computational Complexity
This lecture explores the connection between computational complexity and cryptography, focusing on topics like pseudorandom functions, public-key cryptography, and learning from Gaussians. It delves into the implications of cryptographic reductions, lower bounds for learning MLPs, and the existence
0 views • 22 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
3 views • 41 slides
Socio-technical Energy Transition Modelling: The TEMPEST Model
A simulation model, TEMPEST, incorporating societal and political factors, evaluates UK energy transition under three global SSPs. It analyzes the importance of political capital and societal preferences in adopting mitigation measures. The model's results are compared to the IMAGE model, suggesting
1 views • 5 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Budget Presentation: FY2018-19 Tentative Budget Overview
The FY2018-19 Tentative Budget was presented by Mark Mathers, CFO, and Mike Schroeder, Budget Director. The presentation covered updates on the General Fund, structural deficits, budget recommendations, and required actions to address the deficit. Base budget reductions have reduced the deficit to $
3 views • 50 slides
Proposed Changes to School Aid in the 2024-25 Executive Budget
The 2024-25 Executive Budget proposes significant changes to School Aid, including adjustments to Foundation Aid calculations. The budget aims to increase total School Aid by $824 million, with reductions in Foundation Aid for some districts. These changes are justified by concerns about sustainabil
4 views • 25 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Santa Monica College Proposed Budget Summary 2021-2022
Santa Monica College's presentation of the 2021-2022 proposed adopted budget to the Board of Trustees on September 14, 2021, includes details on revenue, expenditure, budget reductions, and financial highlights from the 2019-2020 and 2020-2021 fiscal years. The budget outlines various actions taken
1 views • 31 slides
Maximizing Savings Through Appliance Standards
Appliance and equipment standards have led to significant reductions in energy consumption for refrigerators, clothes washers, and dishwashers over the years. These standards not only save consumers money but also contribute to CO2 reductions. By updating existing standards, there are further opport
0 views • 14 slides
Emissions Reductions Beyond the Clean Smokestacks Act (CSA) Overview
Emissions Reductions Beyond the Clean Smokestacks Act (CSA) is a comprehensive program aimed at improving air quality by imposing limits on pollutant emissions from coal-burning facilities. The act has successfully achieved significant reductions in nitrogen oxide (NOx) and sulfur dioxide (SO2) emis
1 views • 12 slides
Innovative CPC Futures Contract Program for Agribusiness Sustainability
The Commodity Plus Carbon (CPC) Futures Contract Program integrates agricultural commodity prices with carbon valuation to incentivize good agricultural practices and reduce carbon footprint. By combining ag commodity prices with carbon reductions, CPC contracts offer hedging opportunities and incen
0 views • 8 slides
Exploring Post-Quantum Cryptography and Constructive Reductions
Delve into the realm of post-quantum cryptography through an insightful journey of constructive reductions, rethinking cryptography assumptions, and the relationship between classical and post-quantum regimes. Discover the challenges, advancements, and goals in the quest for durable cryptographic al
1 views • 21 slides
Analysis of SCE Summer Discount Plan 2015 Impact Estimates
The SCE Summer Discount Plan (SDP) for 2015 involved over 305,000 residential participants and 11,000 commercial participants, offering various cycling strategies to curtail air conditioning usage. Impact estimates were developed using matched control groups and a difference-in-differences approach.
0 views • 16 slides
Enhancing Cryptographic Key Generation with High-Quality Randomness
This presentation discusses the critical aspect of ensuring high-quality randomness in cryptographic key generation processes. It explores key vulnerabilities and common failure modes, emphasizing the importance of incorporating strong randomness. The content delves into various methods and issues r
0 views • 45 slides
Overview of Personnel Workshop and Budget Challenges in Marion County Schools
Marion County Schools faces challenges with personnel overages, budget impacts, and the drying up of ESSERF funding. The school employs more personnel than state-funded positions, leading to budget shortfalls and potential reductions. Factors like increased BRIM premiums, pay raises, and PEIA insura
0 views • 17 slides
Zero Emission Vehicles: Forecasting Fleet Scenarios & Emissions Implications
This research project, conducted by Louis Berger U.S. Inc. & Sonoma Technology Inc., explores the implications of adopting zero emission vehicles through forecasting fleet scenarios and estimating emissions reductions. The study assesses the potential increase in zero emission vehicle population, em
0 views • 42 slides
Understanding NP-Completeness and Reductions in Computer Science
Dive into the concept of NP-completeness and reductions in computer science, exploring topics such as 3SAT, E3SAT, EU3SAT, 1-in-EU3SAT, and SUBSETSUM. Learn about weak and strong NP-hardness, witness concepts, and the review of past lectures touching on NP, problems easy to verify, and more.
0 views • 27 slides
Understanding Signatures, Commitments, and Zero-Knowledge in Lattice Problems
Explore the intricacies of lattice problems such as Learning With Errors (LWE) and Short Integer Solution (SIS), and their relation to the Knapsack Problem. Delve into the hardness of these problems and their applications in building secure cryptographic schemes based on polynomial rings and lattice
0 views • 44 slides
Understanding Reductions in Decidability and Tractability
Exploring the concepts of reductions, particularly many-one reductions, in the context of decidability and tractability. The lecture delves into the relationship between decidable and undecidable problems, highlighting examples like Rice's Theorem. It explains the definitions and implications of red
0 views • 20 slides
Understanding Reductions in Theoretical Computer Science
Explore the concept of reductions in theoretical computer science, where problems are converted into others allowing solutions to one to solve the other. Learn how reductions can prove languages to be undecidable using examples like ATM and HALTTM. Follow along as we discuss the application of reduc
0 views • 38 slides
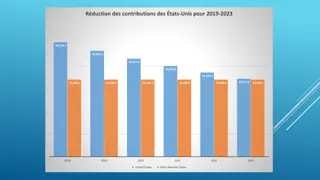
Financial Overview of Reductions and Contributions in the United States (2019-2023)
The data highlights reductions in the contributions of the United States from 2019 to 2023, along with the total quota income of other member states. It also includes projected expenses and budgetary reductions applied annually, categorized into personnel and non-personnel. The information provides
0 views • 5 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
Undecidability Proofs and Reductions in Theory of Computation
Explore undecidability proofs and reductions in the context of Theory of Computation through examples and explanations. Understand how problems are reduced to show undecidability, with demonstrations involving Turing Machines and languages. Gain insights into proving statements like the undecidabili
0 views • 21 slides
Enhancing Security for XMSS and SPHINCS+ Using Machine-Checked Methods
Advanced cryptographic techniques such as XMSS and SPHINCS+ are critical for ensuring secure digital signatures in a post-quantum world. This project focuses on improving the security and verification processes of XMSS and SPHINCS+ using machine-checked methods, aiming to enhance trust in these cruc
1 views • 17 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Franco-Japanese Cybersecurity Workshop Highlights and Future Plans
The 5th Franco-Japanese Cybersecurity Workshop concluded with insightful discussions on key areas such as IoT security, AI, hardware security, and supply chain security. The steering committee members shared plans for the 6th workshop in France, emphasizing policy discussions and cross-cutting issue
0 views • 18 slides
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computing utilizes the principles of quantum mechanics to process information exponentially faster than classical computers. This advancement poses a significant threat to current cryptographic systems, especially those reliant on factors like RSA and Diffie-Hellman key exchange. If large-sc
0 views • 25 slides
Exploring the Role of Blockchain as a Trusted Third Party in Decentralized Systems
Blockchain technology serves as a decentralized and cryptographic Trusted Third Party (TTP) by enhancing trust, immutability, and censorship resistance in transactions. By distributing trust and utilizing cryptographic protocols, blockchain mitigates the need for a centralized authority, offering a
0 views • 30 slides
Understanding Complexity Theory: Decidability, Undecidability, and Reductions
Explore the concepts of decidability and undecidability in complexity theory, discussing the proof of undecidability for various languages. Learn about the acceptance problem and reductions, including mapping reductions, to relate and solve different computational problems effectively.
0 views • 14 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Faster Implementation of Modular Exponentiation in JavaScript
Development of a cryptographic authentication toolkit for web application developers. Discusses modular exponentiation, digital signatures, elliptic curve cryptography, and the importance of DSA in providing secure authentication. Aims to offer both classical and elliptic curve cryptographic solutio
0 views • 22 slides
Understanding the Relationship between Decisional Second-Preimage Resistance and Preimage Resistance in Cryptographic Hash Functions
This work delves into the subtle question of when Decisional Second-Preimage Resistance (SPR) implies Preimage Resistance (PRE) in hash functions. It presents a tool for enabling tight security proofs for hash-based signatures by exploring the success probability of adversaries against collision res
0 views • 25 slides
Understanding the Importance of Cryptographic Safety Valves in Legislation
Legislation regarding cryptographic safety valves is impending, with potential implications on privacy and security. Matt Tait discusses the need to analyze risks and consequences, emphasizing the importance of transparent and secure safety valves. The debate surrounds decryption requirements for da
0 views • 17 slides
Effective Strategies for Church Staff Reductions: Involuntary and Voluntary Options
Explore effective strategies for church staff reductions, including involuntary reductions in force and voluntary employee exit programs. Learn about salary freezes, attrition reductions, and reduced work schedules/furloughs to navigate challenging situations while ensuring compliance with employmen
0 views • 36 slides
Zeroizing Attacks on Cryptographic Multilinear Maps: Overview and Applications
Cryptographic multilinear maps (MMAPs) enable computations on encoded secret data, offering similarities to fully homomorphic encryption (FHE) while providing distinct features. MMAPs find applications in identity-based encryption, non-interactive zero-knowledge proofs, and more. The evolution of MM
0 views • 45 slides
Understanding Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
0 views • 28 slides
Challenges and Solutions in Implementing PCT Fee Reductions for Universities
Implementing fee reductions for universities under the PCT system involves defining eligibility, counting reductions, claiming reductions, ensuring consistency across Receiving Offices, and monitoring quota usage. Challenges include defining university eligibility, handling multiple applicants, and
0 views • 8 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Scalable Cryptographic Authentication for High Performance Computing
This work discusses the scalable cryptographic authentication approach developed by Andrew Prout and team for high-performance computing. The LLGrid system architecture, challenges with interactive supercomputing, and utilization of LLGrid for various computing tasks are explored, highlighting the i
0 views • 34 slides
Undecidable Problems in Theory of Computation
Explore the concept of undecidable problems in the theory of computation, focusing on non-SD reductions and undecidable problems not involving Turing Machines. Learn about proving languages are not SD, using examples like AanBn and creating reductions to show non-SD properties. Work through reductio
0 views • 31 slides